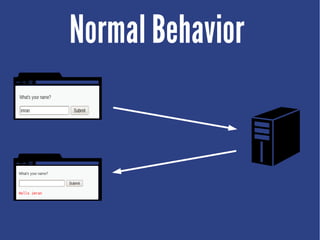
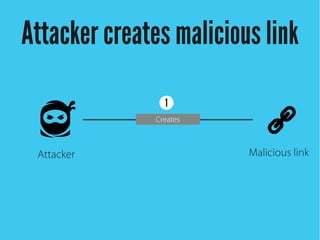
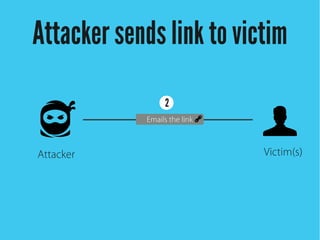
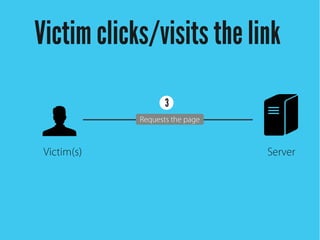
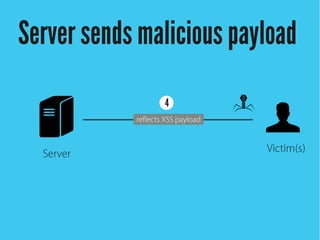
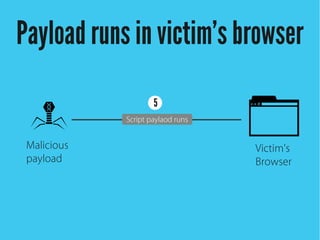
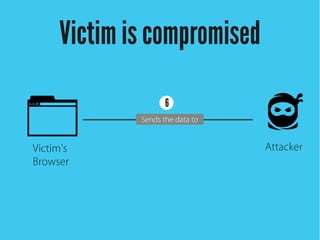
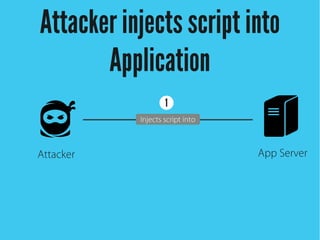
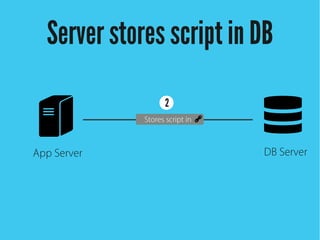
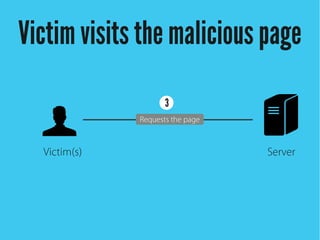
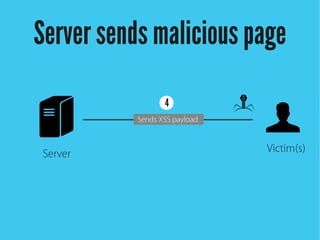
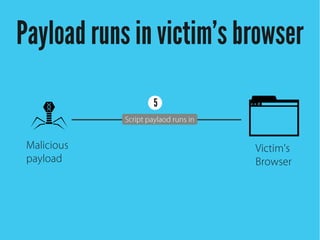
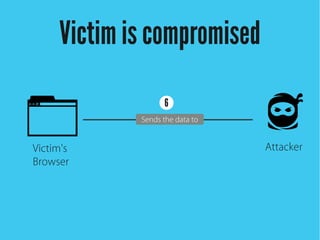
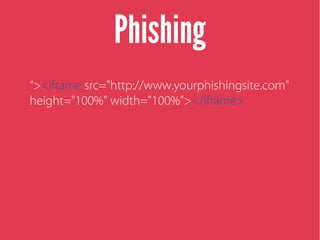
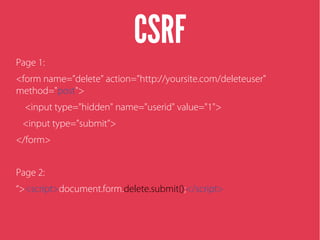
Cross-site scripting (XSS) is an injection attack where malicious scripts are injected into otherwise trusted sites. There are three main types of XSS attacks: reflected XSS occurs via URLs, stored XSS occurs when scripts are stored in a database and delivered to users, and DOM-based XSS modifies the DOM environment. XSS attacks can lead to issues like session hijacking, phishing, and port scanning. Developers can prevent XSS by validating and encoding untrusted data, and using HTTP-only and secure flags for cookies.