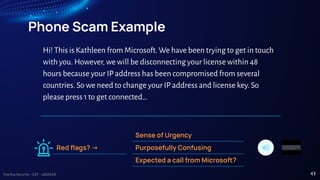
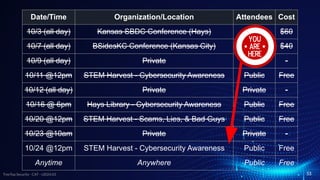
The document presents cybersecurity awareness tips from Treetop Security, emphasizing the importance of protecting personal and business data. Key advice includes maintaining strong, unique passwords, implementing two-factor authentication, and regularly backing up data while staying vigilant against phishing and malware threats. It underscores that effective cybersecurity relies not only on technology but also on the awareness and actions of individuals.


















![TreeTop Security - CAT - v2024.03
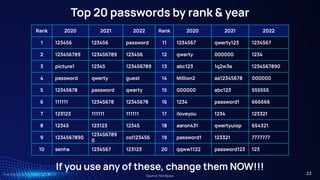
Passphrases, not passwords
● Useful when passwords must be typed in
○ Computer login
● Should not be easy to guess
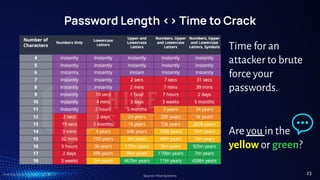
○ At least 12 characters, but 15 or more is far better
○ Length better than “complexity” - upper, lower, number, & special
characters (~!@#$%^&*_-+=`|(){}[]:;"'<>,.?/)
○ Bad password (8): P@ssw0rd
○ Great password (25): MysonwasbornNovember1995!
○ Wireless <- no phone numbers!
Why are most passwords exactly 8 characters?
21](https://image.slidesharecdn.com/cybersecurity-awareness-training-presentation-v202404-240417145139-8c2c1599/85/Cybersecurity-Awareness-Training-Presentation-v2024-03-21-320.jpg)