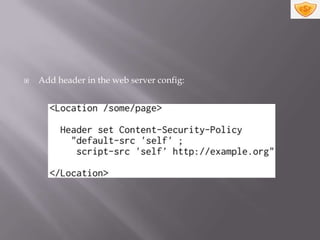
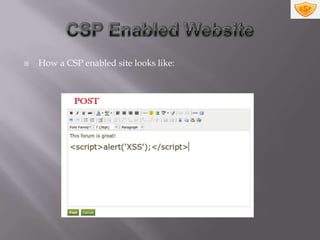
Content Security Policy (CSP) is a security policy that helps mitigate cross-site scripting attacks by whitelisting approved sources of executable content on a web page. An extra HTTP header instructs browsers to enforce the policy by blocking or warning about resources loaded from disallowed origins. CSP adoption involves deciding which policy directives to apply and configuring web servers to send the CSP HTTP header with resources.
















![ Facebook has started using [x-webkit-csp]](https://image.slidesharecdn.com/contentsecuritypolicy-130407101639-phpapp02/85/Content-security-policy-19-320.jpg)
