This document is a hands-on introduction to Docker security, aimed at beginners. It covers the basic components of Docker, commands for interacting with Docker containers, and insights into Docker's security aspects such as container communication and privileged access. The presentation emphasizes the importance of proper Docker management for effective security and operational efficiency.






![Docker Commands
docker run [options] image:version [command]
Run a container from an image
“-d”: detached mode
“-t”: TTY
“-i”: interactive
“--name”: set a name for the container.
“-P”: Expose the default ports needed for this container.
“-p”: Expose specified ports to this container. Syntax: <host-interface>:<host-
port>:<container-port>
“-v”: Mount the specified volume on the container. Syntax:
/host/volume:/container/volume
“--readonly”: Mount the container's root filesystem as read only.
“--rm”: Automatically remove the container when it exits.](https://image.slidesharecdn.com/hands-onintroductiontodockersecurityfordockernewbies-170627105002/75/Hands-on-introduction-to-docker-security-for-docker-newbies-10-2048.jpg)
![Docker Commands
docker pull image:version
pull an image from the registry
docker exec [options] container-name [command]
execute a command on an active container
docker attach container-name
attach to a running container](https://image.slidesharecdn.com/hands-onintroductiontodockersecurityfordockernewbies-170627105002/75/Hands-on-introduction-to-docker-security-for-docker-newbies-11-2048.jpg)



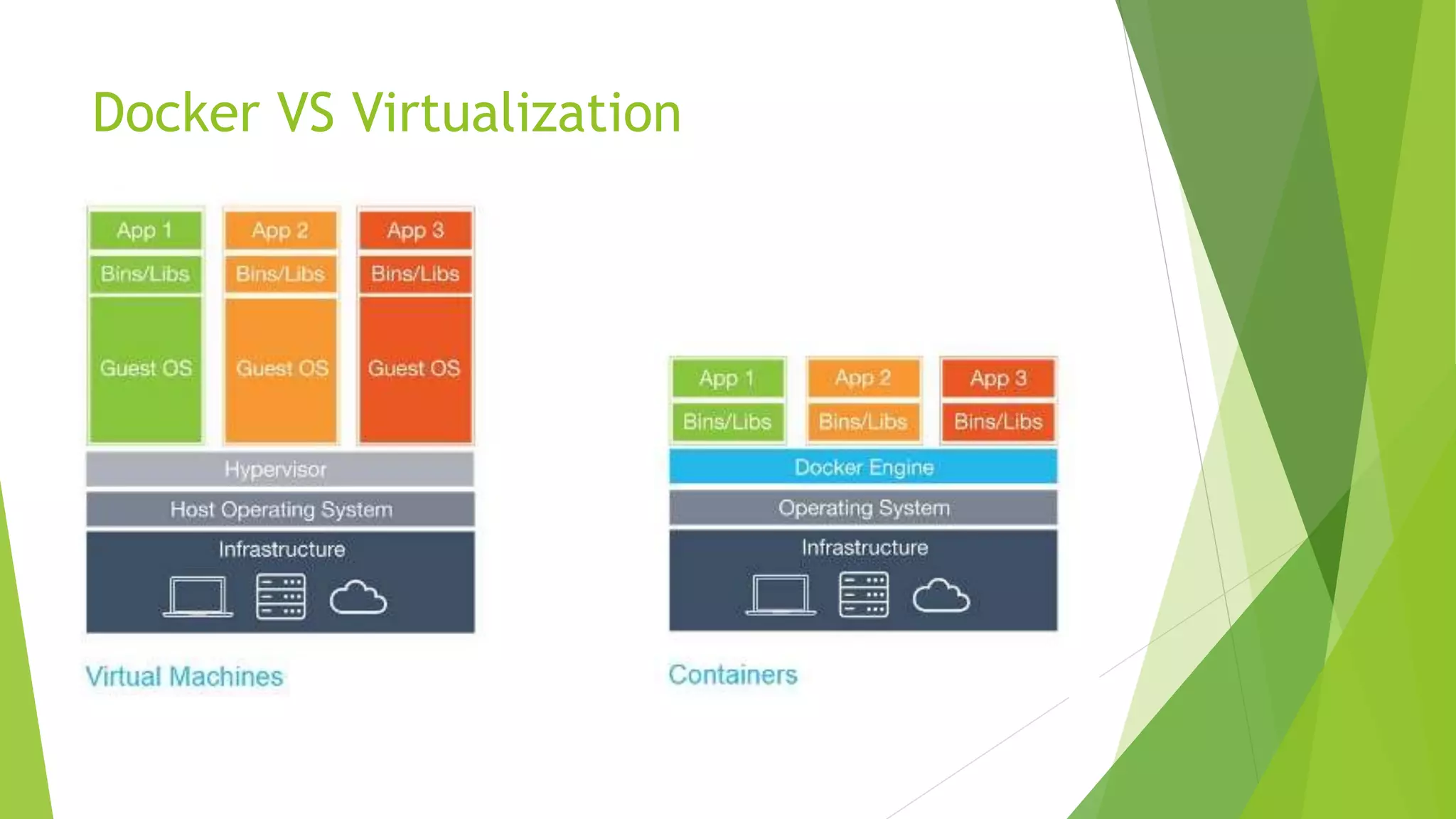




![So, security?
Privileged containers
From the Docker Host to connect to a non-privileged container and run:
docker exec –it [container-name] /bin/bash
ls /dev
Now to create a privileged container and run the same command:
docker run -it --privileged --name priv1 –h priv1 centos /bin/bash
ls /dev
As we can see, the privileged container can access a lot more hardware than
the non-privileged container](https://image.slidesharecdn.com/hands-onintroductiontodockersecurityfordockernewbies-170627105002/75/Hands-on-introduction-to-docker-security-for-docker-newbies-22-2048.jpg)