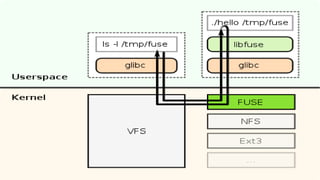
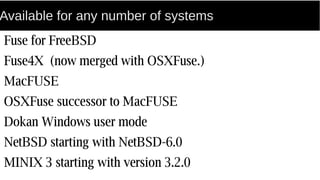
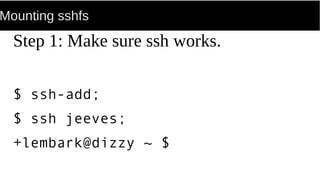
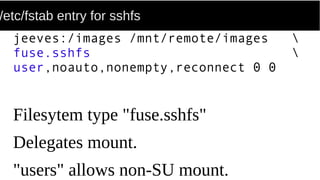
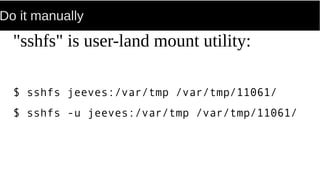
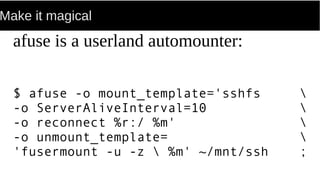
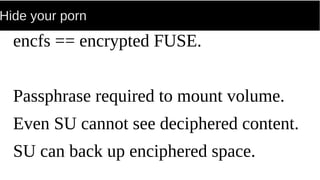
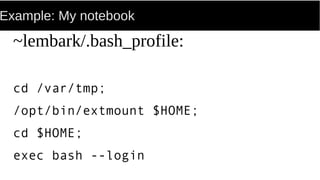
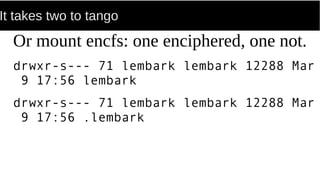
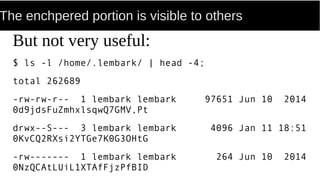
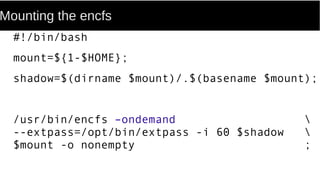
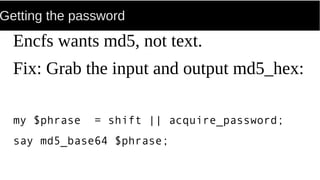
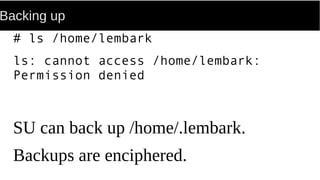
FUSE allows processes to mount their own private filesystems without requiring root privileges. Some examples of FUSE filesystems include encrypted volumes using encfs and remote filesystems mounted over SSH using sshfs. These filesystems can be mounted automatically and only be visible to the mounting process, providing security and privacy for personal data even from the root user.