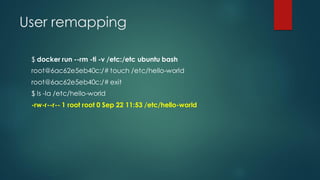
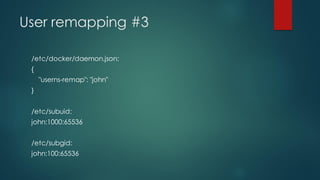
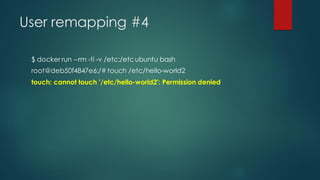
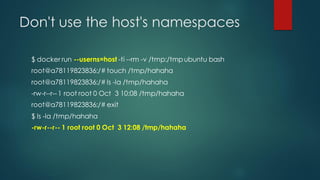
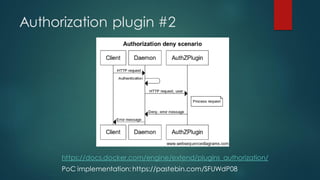
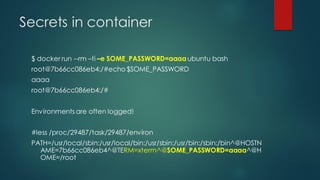
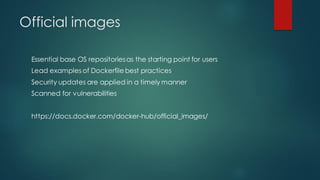
Docker images can pose security risks if not properly secured. Key steps to improve Docker security include:
1) Carefully curate official images and scan all images for vulnerabilities;
2) Implement Docker Content Trust (DCT) to verify image integrity and publisher;
3) Restrict container access to resources and capabilities to only what is necessary.














![[INFO] 2 - Docker daemon configuration
[PASS] 2.1 - Ensure network traffic is restricted between containers on the
default bridge
[PASS] 2.2 - Ensure the logging level is set to 'info'
[PASS] 2.3 - Ensure Docker is allowed to make changes to iptables
[PASS] 2.4 - Ensure insecure registries are not used
[PASS] 2.5 - Ensure aufs storage driver is not used
[INFO] 2.6 - Ensure TLS authentication for Docker daemon is configured
[INFO] * Docker daemon not listening on TCP
[INFO] 2.7 - Ensure the default ulimit is configured appropriately
[INFO] * Default ulimit doesn't appear to be set](https://image.slidesharecdn.com/docker-security-191012104818/85/Docker-security-21-320.jpg)




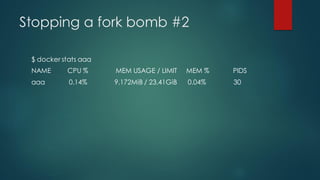
![Stopping a fork bomb
$ docker run --rm --name aaa --pids-limit 30 ubuntu
bash -c ":() { : | : & }; :; while [[ true ]]; do sleep 1; done"
environment: fork: retry: Resource temporarily unavailable
environment: fork: retry: Resource temporarily unavailable
...
bash: fork: retry: Resource temporarily unavailable
environment: fork: retry: Resource temporarily unavailable
environment: fork: retry: Resource temporarily unavailable
environment: fork: Resource temporarily unavailable
bash: fork: Interrupted system call](https://image.slidesharecdn.com/docker-security-191012104818/85/Docker-security-27-320.jpg)

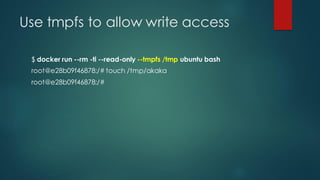
![Remove all capabilities ...
$ docker run --rm --cap-drop=ALL nginx
2019/09/22 09:37:45 [emerg] 1#1:
chown("/var/cache/nginx/client_temp", 101) failed (1: Operation not
permitted)
nginx: [emerg] chown("/var/cache/nginx/client_temp", 101) failed (1:
Operation not permitted)
man 7 capabilities](https://image.slidesharecdn.com/docker-security-191012104818/85/Docker-security-31-320.jpg)
![… add only what's required
$ docker run --rm --cap-add=chown --cap-drop=ALL nginx
2019/09/22 09:39:28 [emerg] 1#1: bind() to 0.0.0.0:80 failed (13:
Permission denied)
nginx: [emerg] bind() to 0.0.0.0:80 failed (13: Permission denied)](https://image.slidesharecdn.com/docker-security-191012104818/85/Docker-security-32-320.jpg)
![… add only what's required #2
$ docker run --rm --cap-add=chown --cap-add=net_bind_service --
cap-drop=ALL nginx
2019/09/22 09:43:22 [emerg] 6#6: setgid(101)failed (1: Operation not
permitted)
2019/09/22 09:43:22 [alert] 1#1: workerprocess 6 exitedwithfatal code
2 and cannot be respawned](https://image.slidesharecdn.com/docker-security-191012104818/85/Docker-security-33-320.jpg)
![… add only what's required #3
$ docker run --rm --cap-add=chown --cap-add=net_bind_service --
cap-add=setgid --cap-drop=ALL nginx
2019/09/22 09:43:54 [emerg] 6#6: setuid(101)failed (1: Operation not
permitted)
2019/09/22 09:43:54 [alert] 1#1: workerprocess 6 exitedwithfatal code
2 and cannot be respawned](https://image.slidesharecdn.com/docker-security-191012104818/85/Docker-security-34-320.jpg)