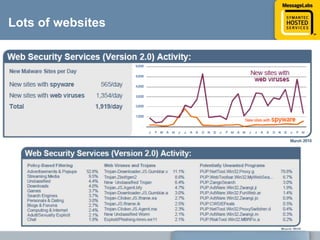
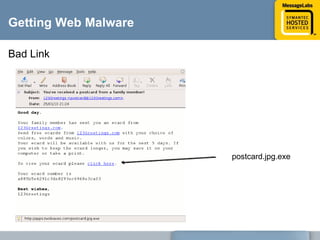
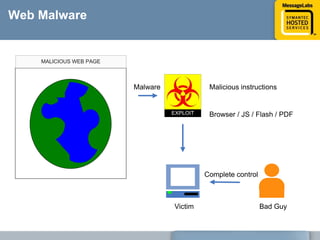
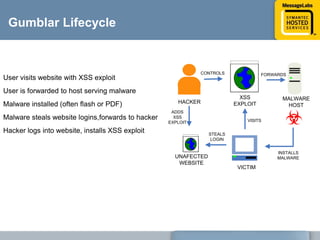
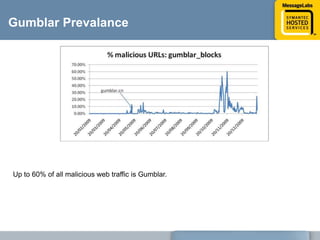
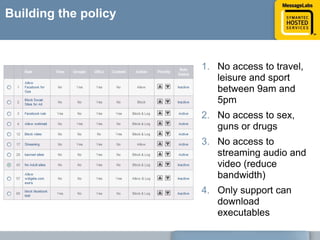
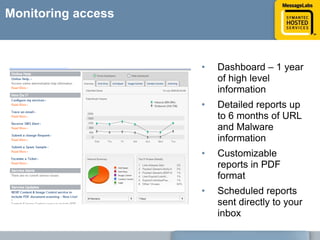
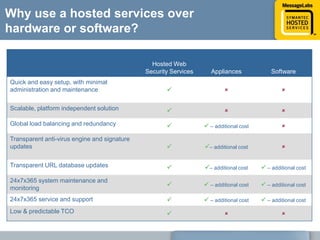
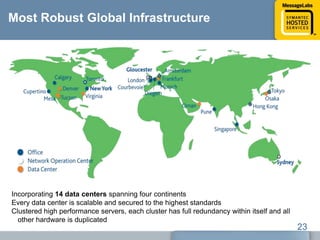
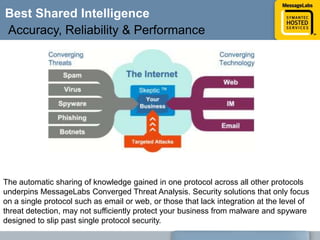
This document discusses common web attacks that companies face and how to protect against them. It outlines how malware spreads through bad links, advertising, and cross-site scripting (XSS) attacks. XSS can be used to redirect users to malicious sites or install malware through iframes. Up to 60% of malicious web traffic involves "Gumblar" attacks, which install malware to steal user credentials and data. The document recommends controlling web access through policy, monitoring usage, and using malware protection and a hosted security service for the best protection. It highlights the services, infrastructure, service level agreements and shared intelligence of MessageLabs to protect against web threats.