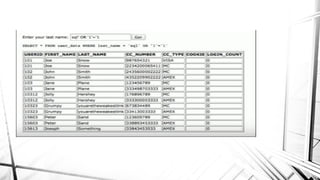
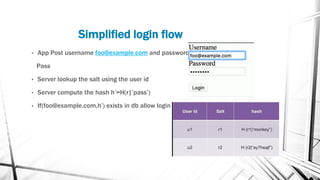
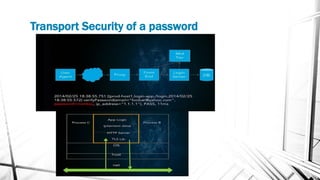
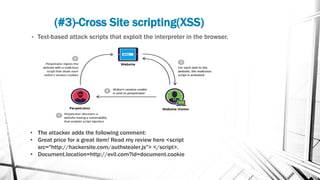
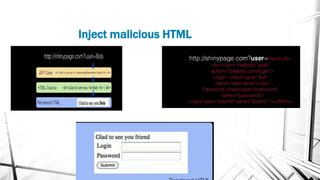
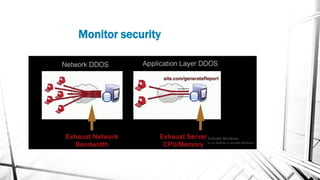
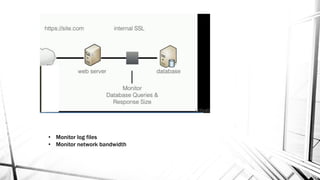
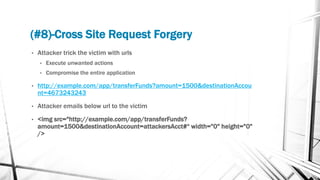
This document discusses web security and the OWASP organization. It provides an overview of the OWASP top 10 vulnerabilities, including injection, broken authentication, cross-site scripting, and insecure APIs. It also outlines techniques for preventing these vulnerabilities, such as input validation, encryption, access control, and keeping components up to date. Testing tools mentioned include OWASP ZAP and SQLMap.