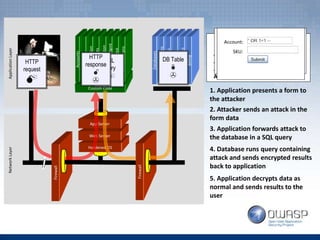
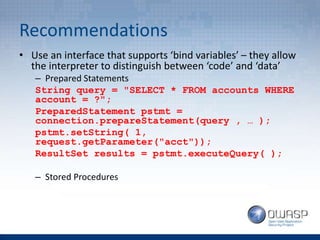
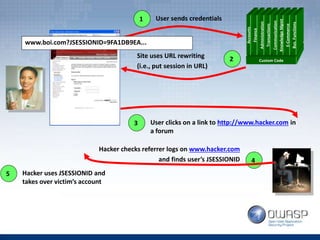
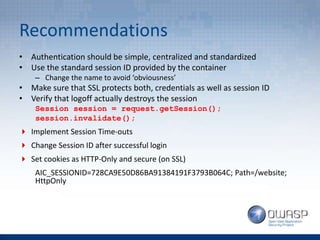
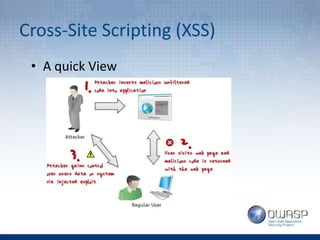
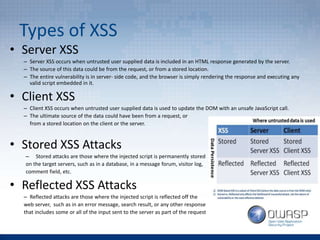
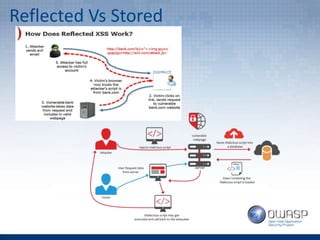
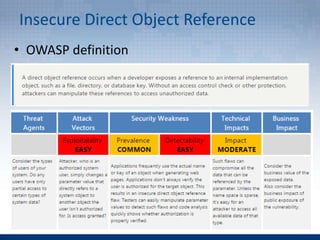
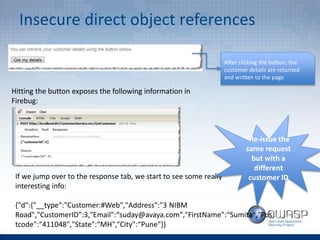
The document provides an overview of the top 5 vulnerabilities according to the OWASP Top 10 list - Injection, Broken Authentication and Session Management, Cross-Site Scripting (XSS), Insecure Direct Object References, and Security Misconfiguration. For each vulnerability, the document defines the vulnerability, provides examples, and lists recommendations for mitigating the risk.