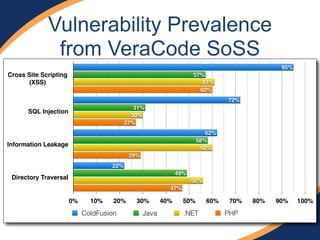
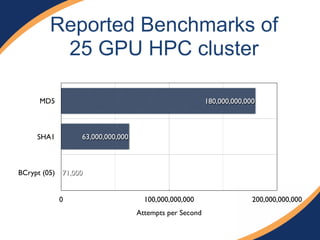
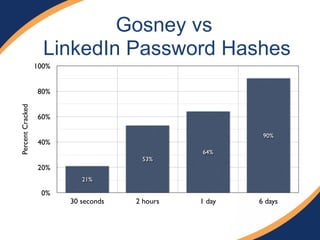
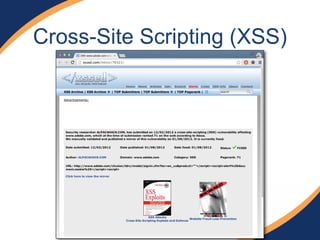
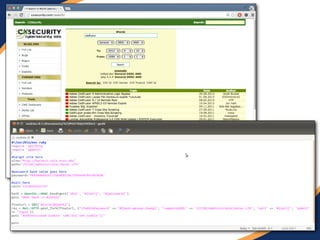
The document provides an overview of a presentation on web penetration testing and hacking tools. It discusses what will and will not be covered, including demonstrations of tools like sqlmap, BeEF, and Metasploit used against vulnerable web apps. It also summarizes recent security events like Heartbleed and Shellshock, the OWASP top 10 vulnerabilities, and techniques for SQL injection, XSS attacks, and exploiting vulnerabilities like those in ColdFusion.