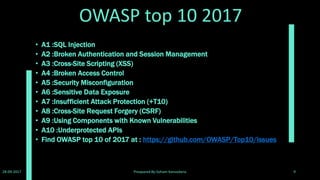
The document provides an overview and instructions for installing and using the Damn Vulnerable Web Application (DVWA). DVWA is a PHP/MySQL web application designed to be vulnerable for testing security skills. It contains vulnerabilities like SQL injection, XSS, file inclusion, and more. The document outlines how to install DVWA using XAMPP, describes the different security levels and vulnerabilities, and provides instructions for accessing the vulnerabilities and practicing attacks. It emphasizes that DVWA should only be used on localhost for legal and safe security testing.







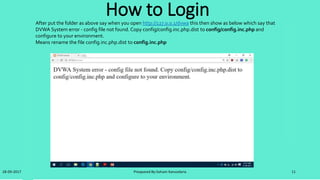
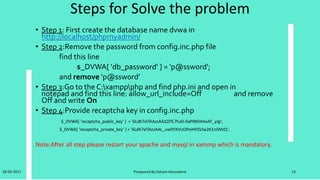
![Steps for Solve the problem
• Step 1: First create the database name dvwa in
http://localhost/phpmyadmin/
• Step 2:Remove the password from config.inc.php file
find this line
$_DVWA[ 'db_password' ] = 'p@ssword';
and remove ‘p@ssword’
• Step 3:Go to the C:xamppphp and find php.ini and open in
notepad and find this line: allow_url_include=Off and remove
Off and write On
• Step 4:Provide recaptcha key in config.inc.php
$_DVWA[ 'recaptcha_public_key' ] = '6LdK7xITAAzzAAJQTfL7fu6I-0aPl8KHHieAT_yJg';
$_DVWA[ 'recaptcha_private_key' ] = '6LdK7xITAzzAAL_uw9YXVUOPoIHPZLfw2K1n5NVQ';
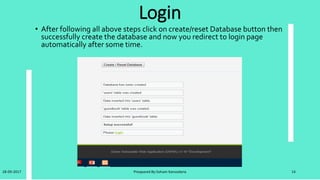
Note:After all step please restart your apache and mysql in xammp which is mandatory.
28-09-2017 Preapared By:Soham Kansodaria 12](https://image.slidesharecdn.com/dvwa1-170928124221/85/DVWA-Damn-Vulnerabilities-Web-Application-12-320.jpg)