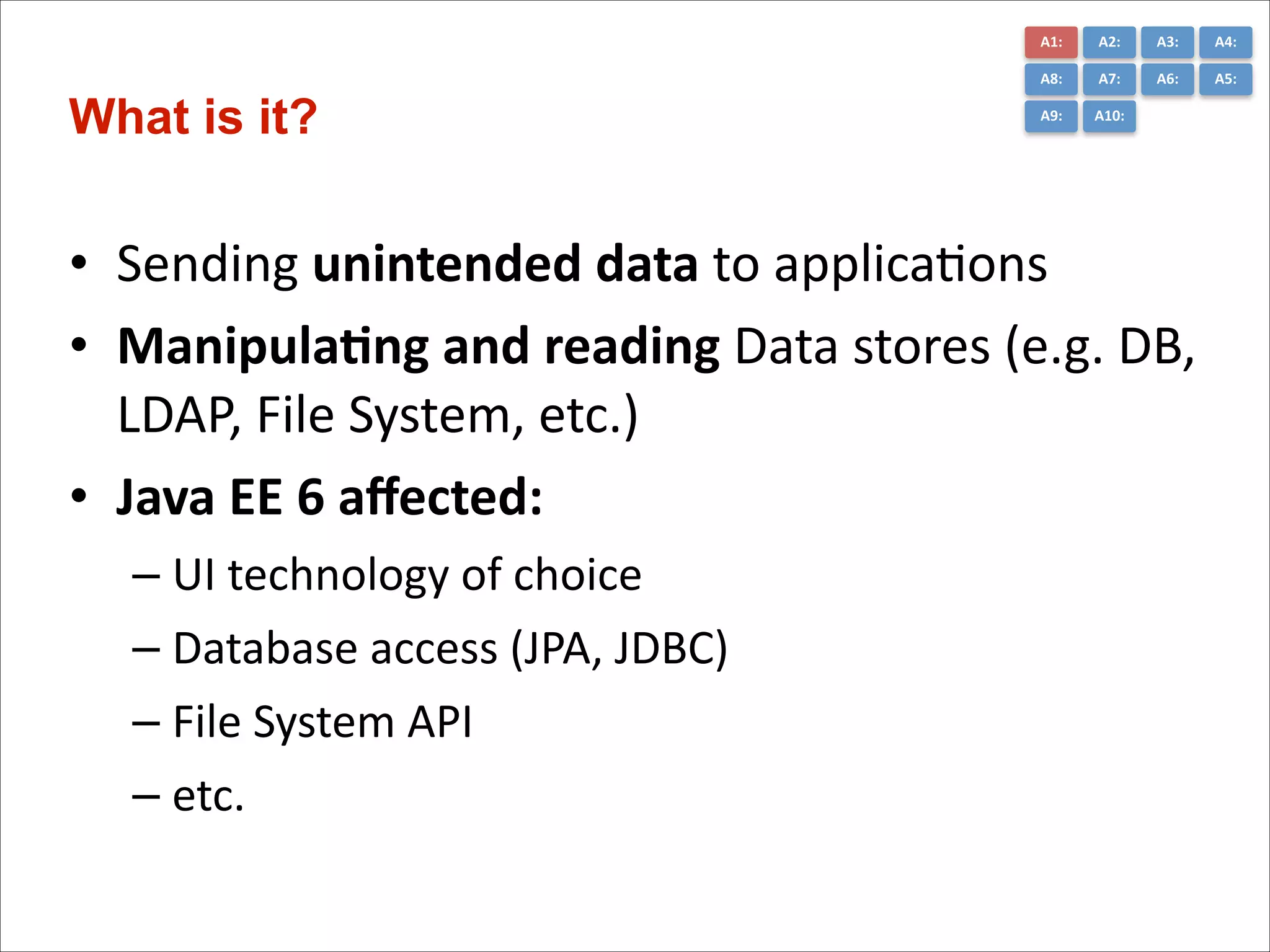
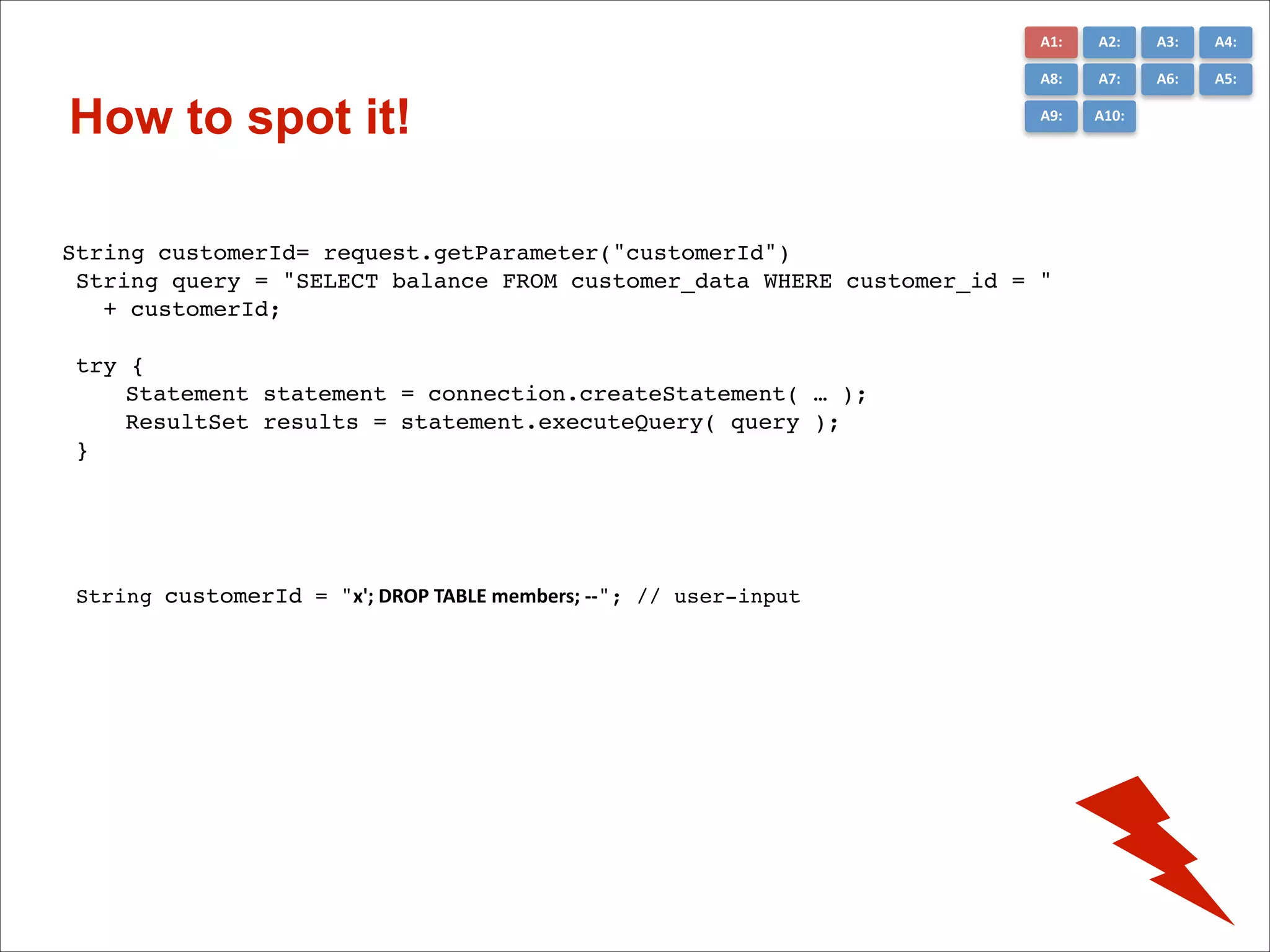
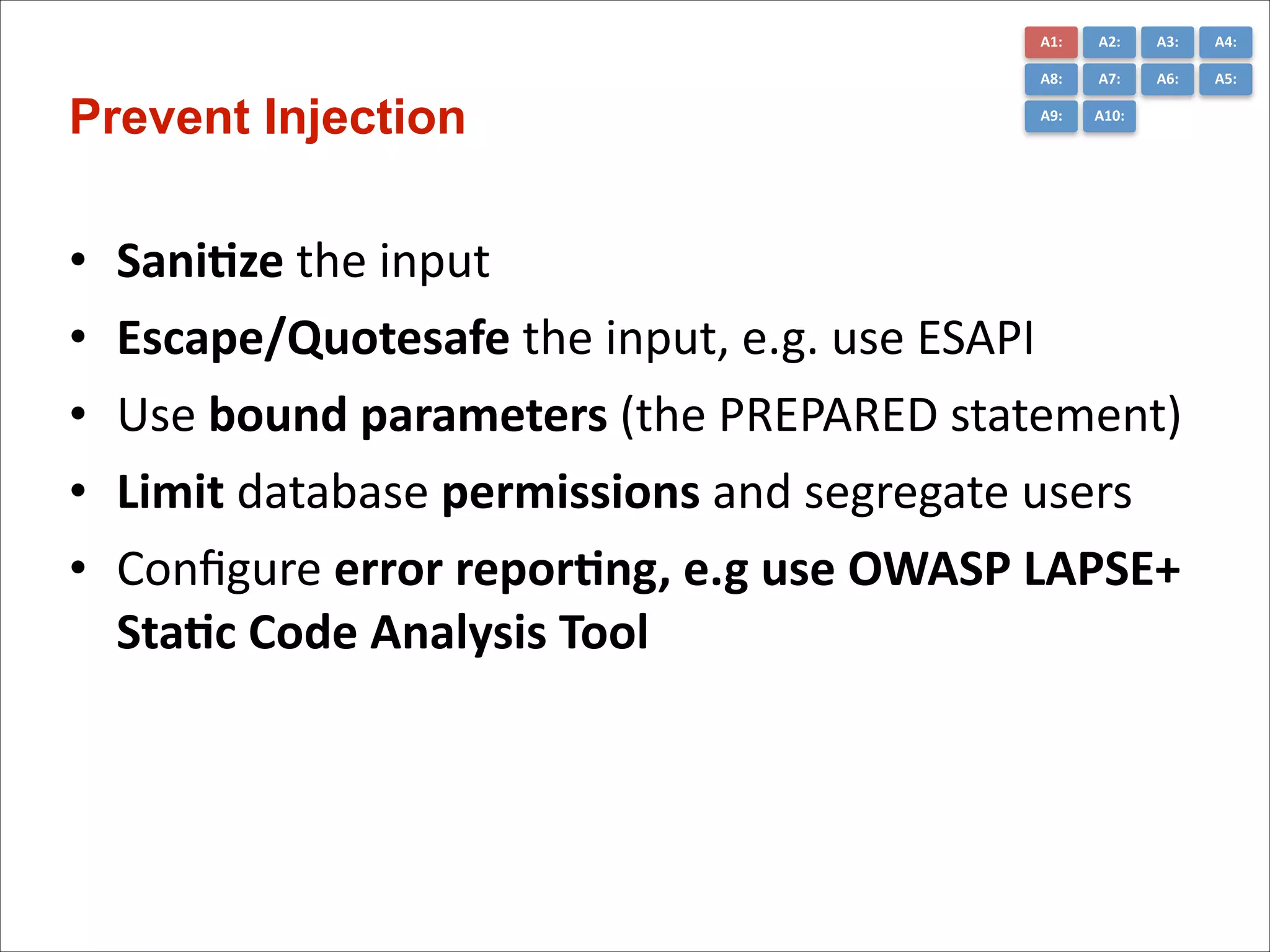
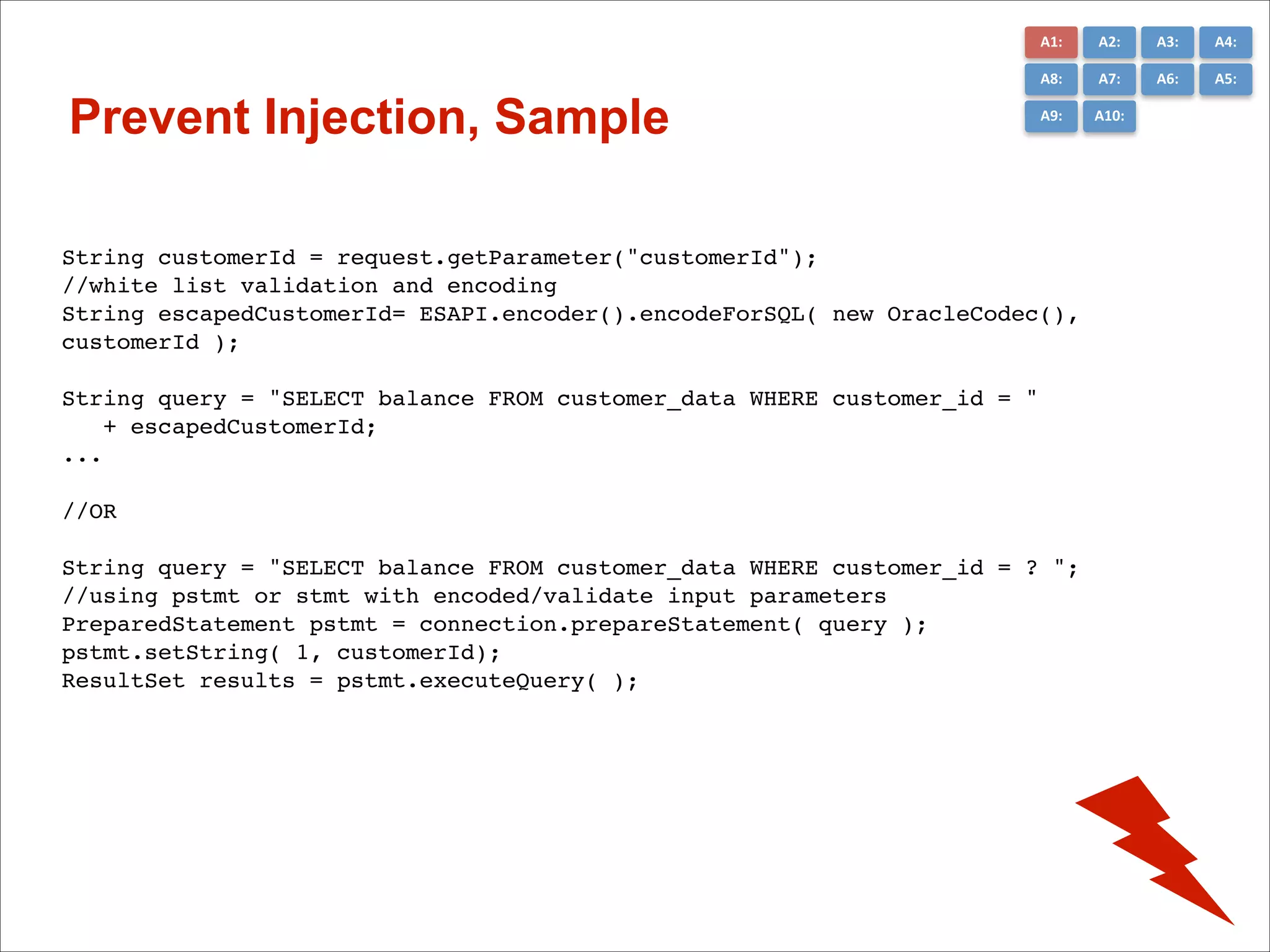
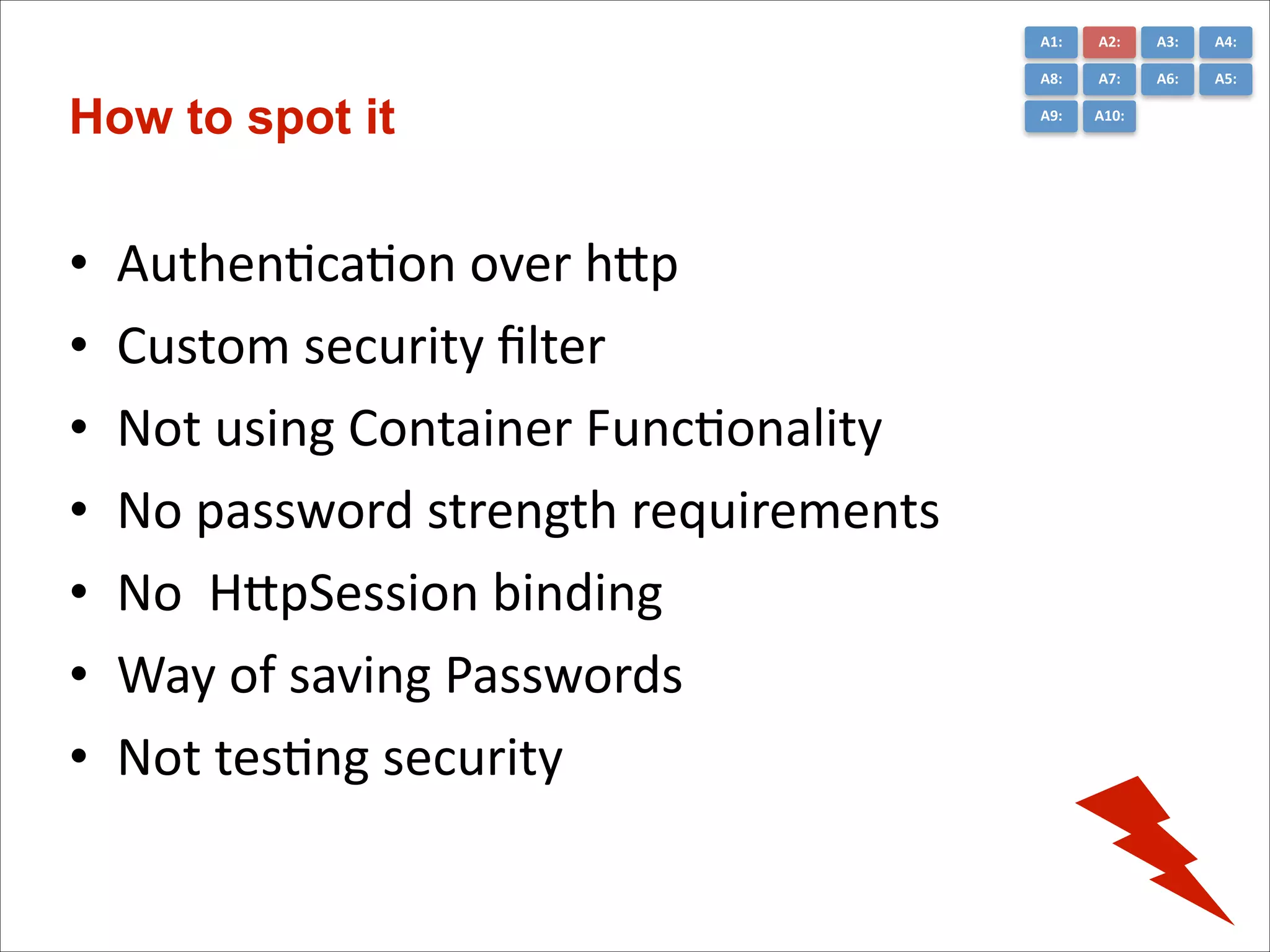
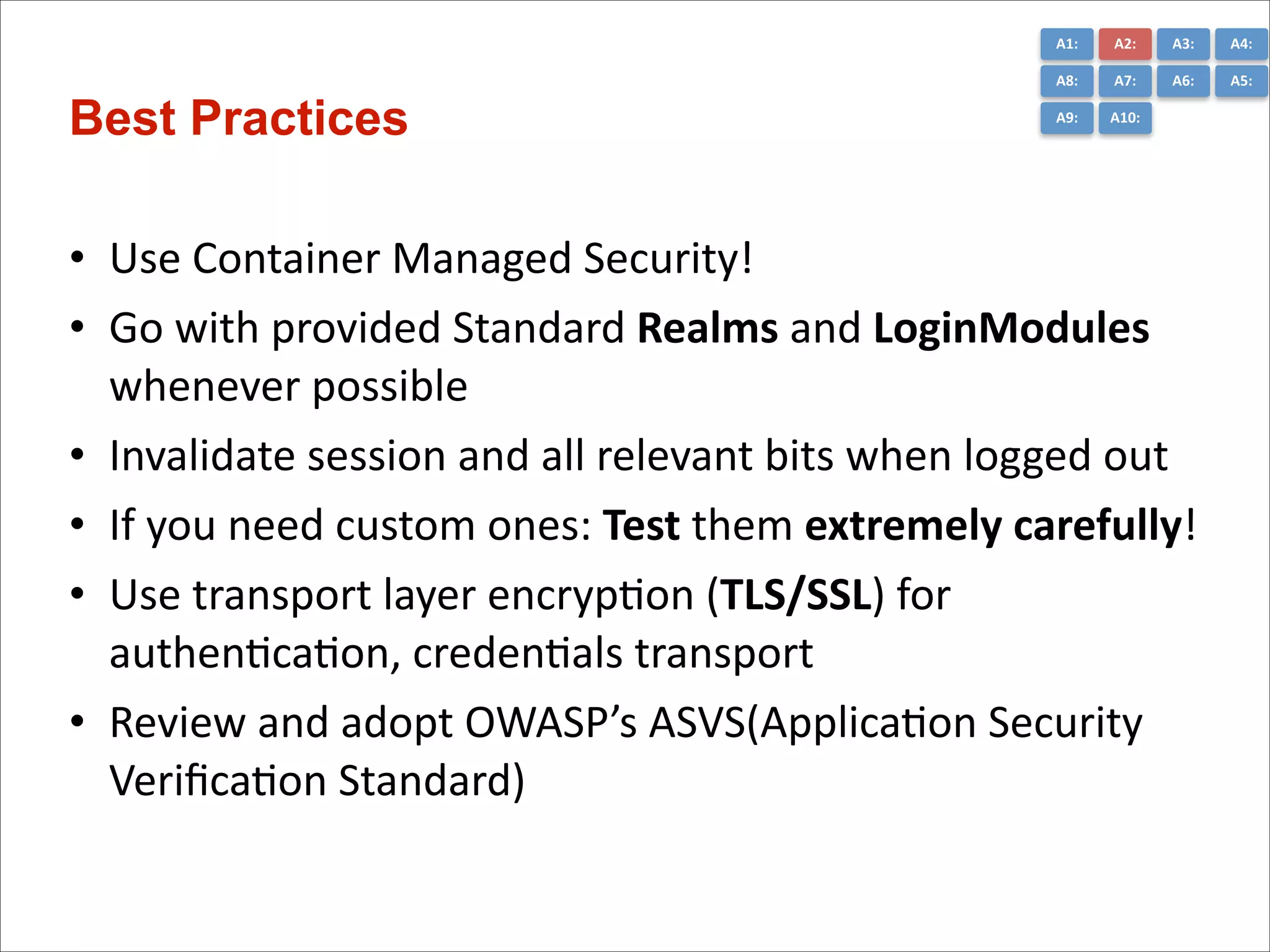
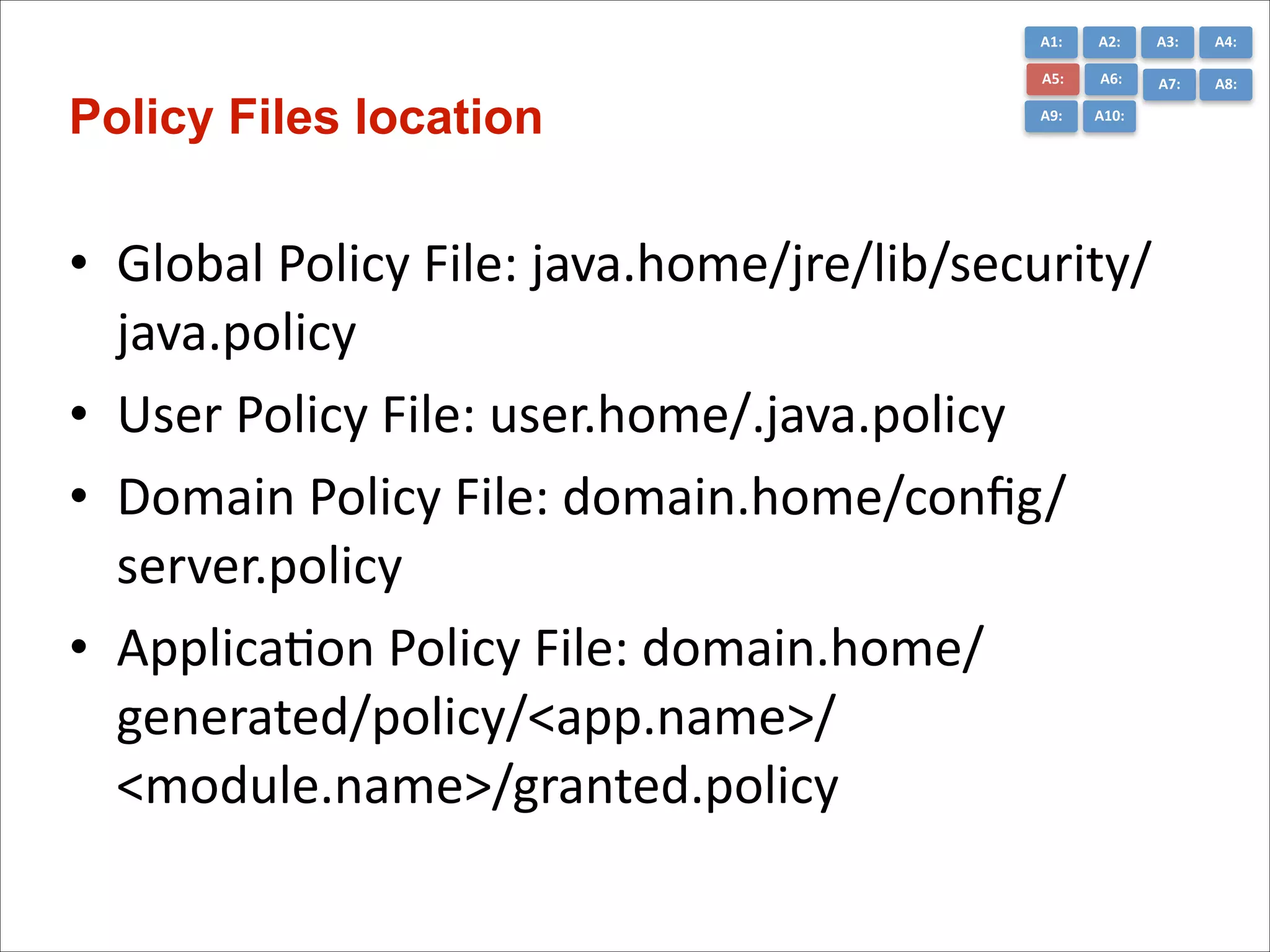
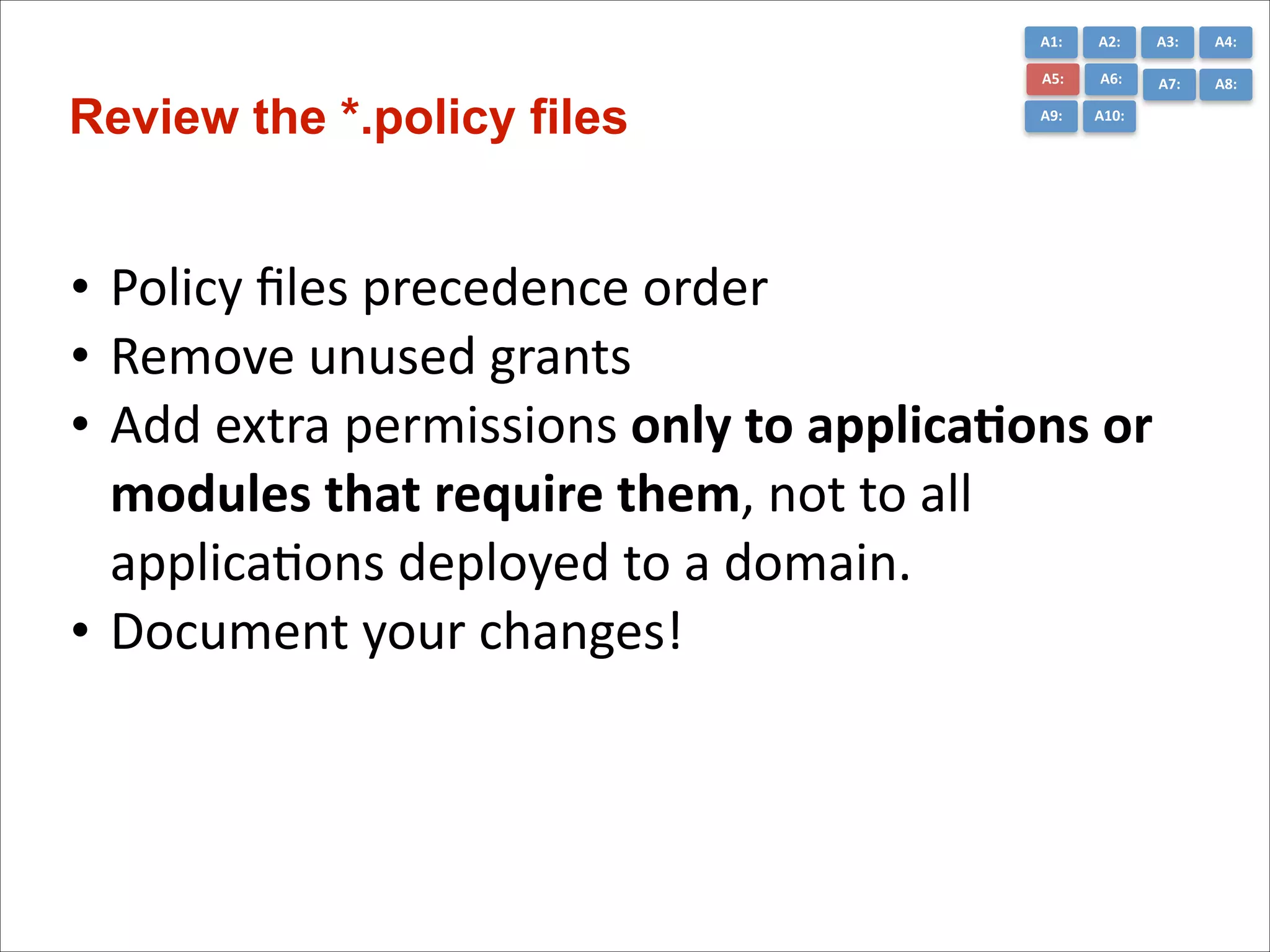
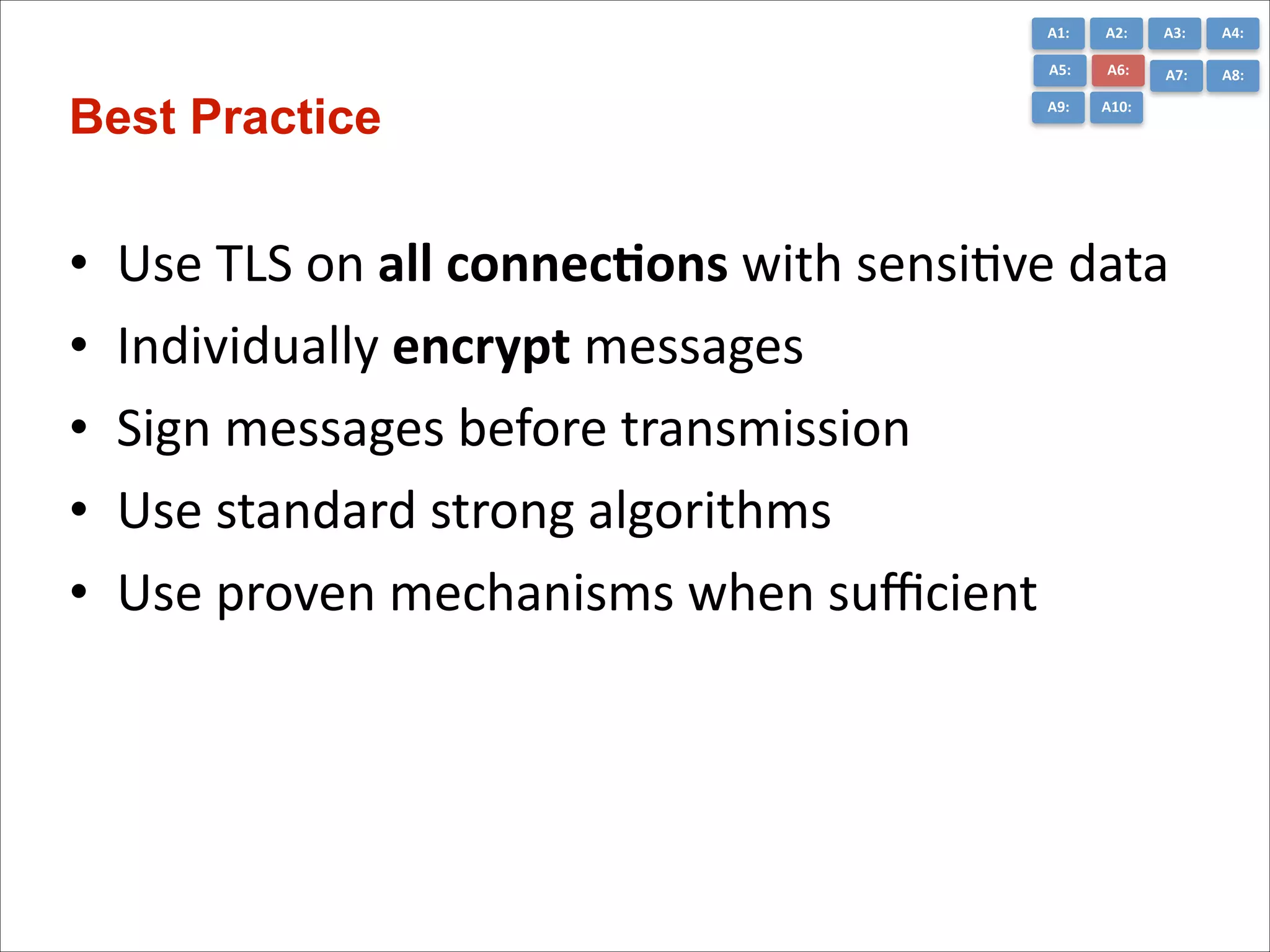
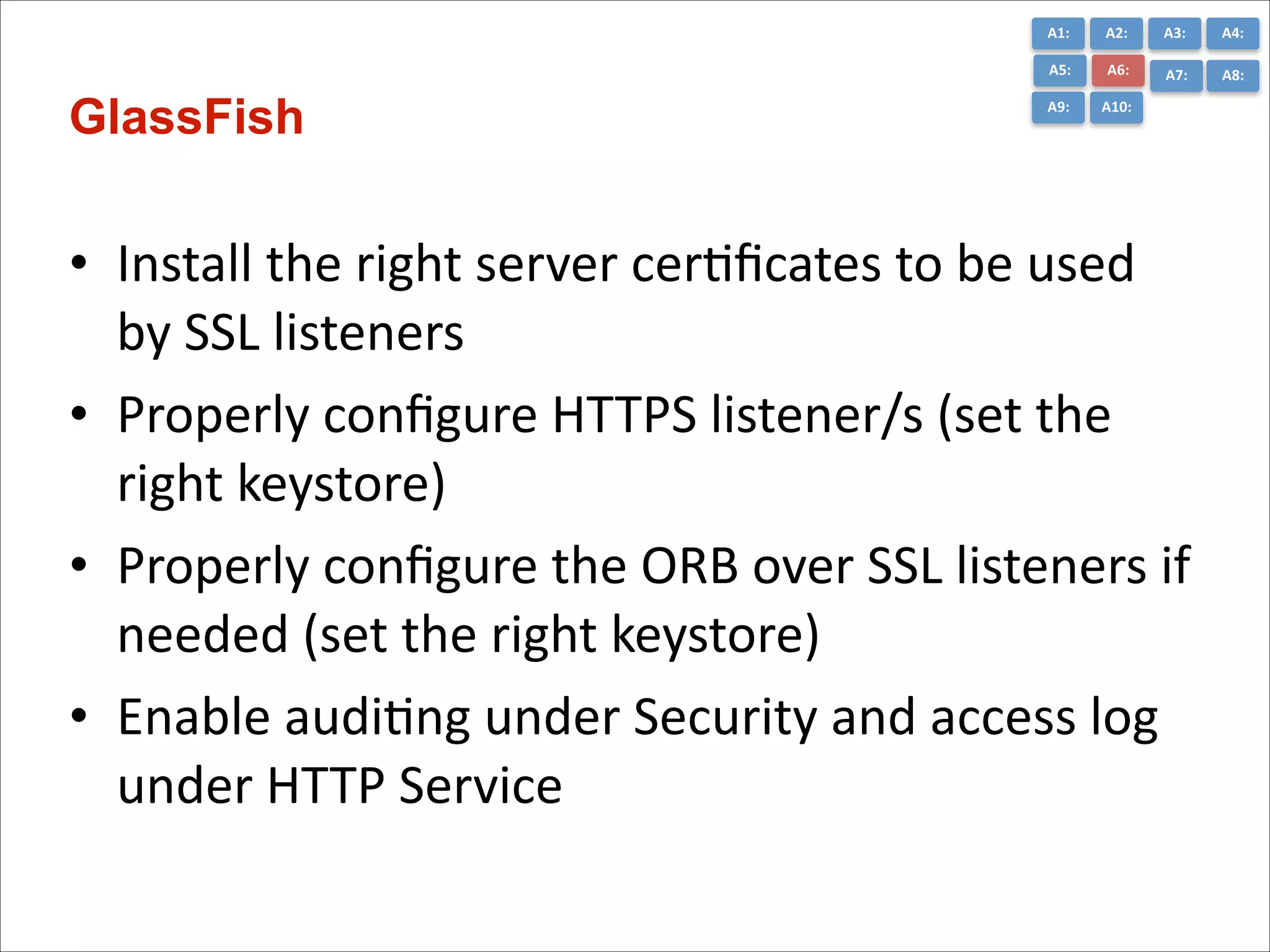
The document presents the top 10 critical web application security risks for Java EE applications, as outlined by Masoud Kalali. It covers issues like injection attacks, broken authentication, cross-site scripting, and security misconfigurations, providing insights into vulnerabilities and recommendations for prevention. The aim is to raise awareness and encourage secure development practices within the Java EE community.