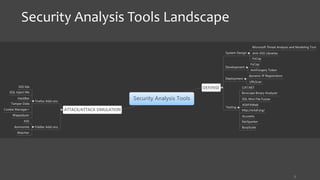
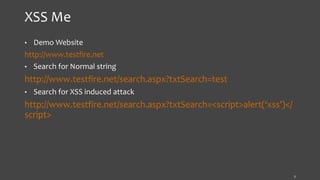
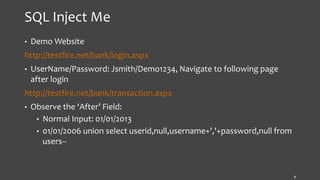
The document presents an overview of application security, highlighting the OWASP top 10 threats and various security analysis tools used for testing and mitigating risks associated with common vulnerabilities such as XSS and SQL injection. It details specific tools like XSS-Me, SQL Inject-Me, HackBar, and various Firefox add-ons, explaining their functionalities and use cases in identifying security flaws. Additionally, it includes references to external resources and licensing information.