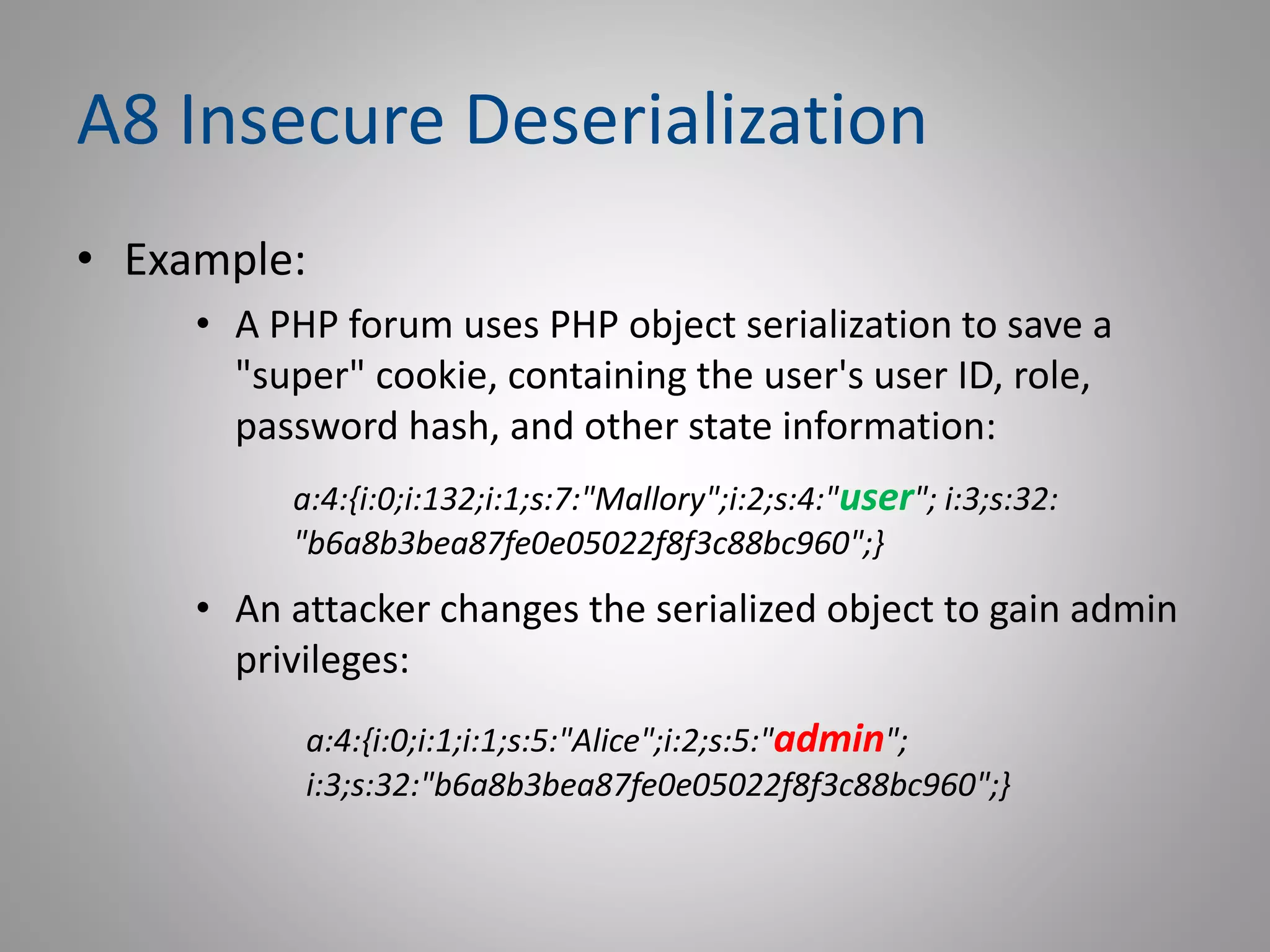
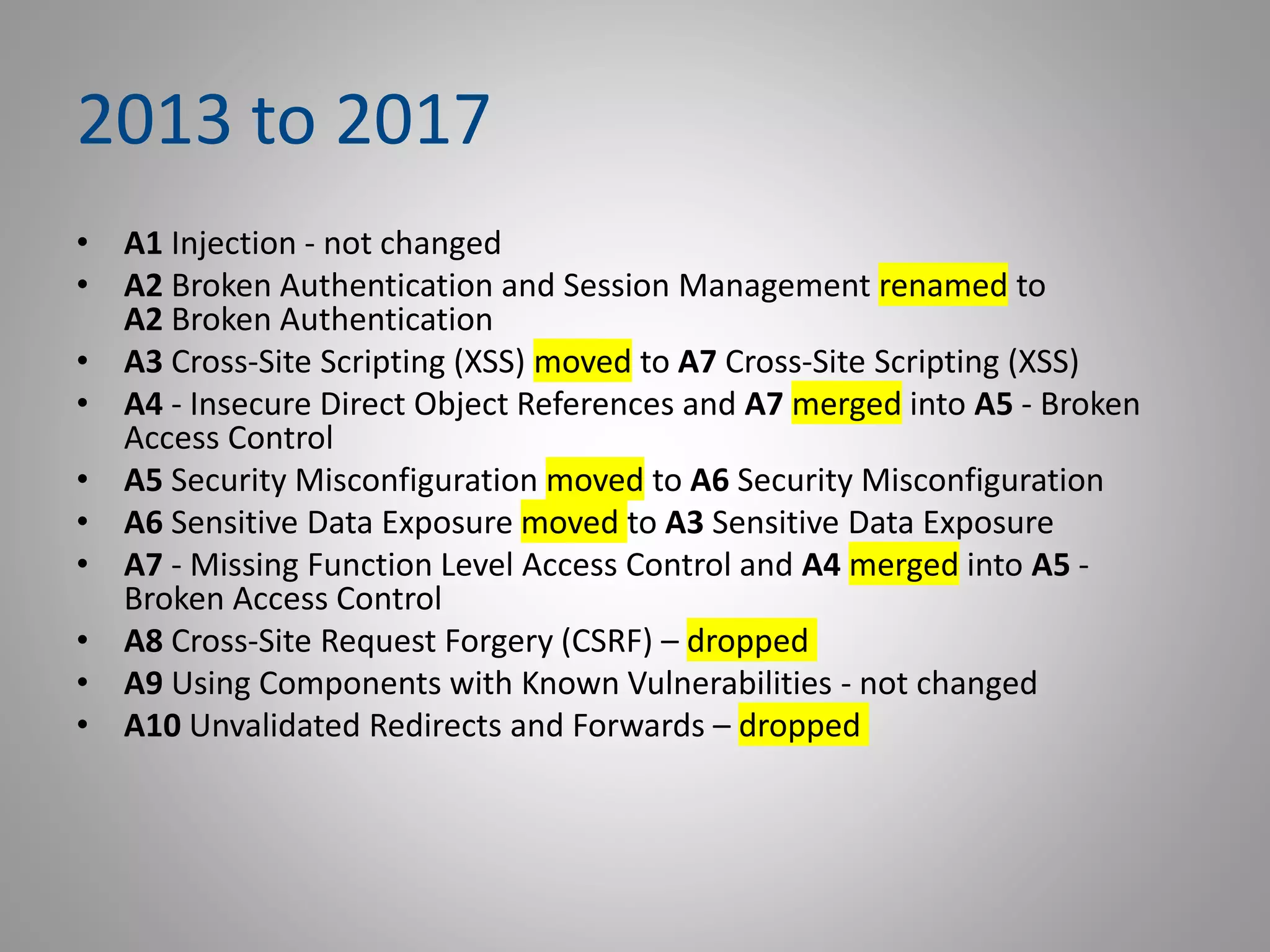
The document discusses the OWASP Top Ten project, which identifies the 10 most critical web application security risks. It provides an overview of OWASP, describes the Top 10 risks from 2013 and 2017, and explains changes between the two versions. For each risk, it gives a brief example and recommendations for prevention. The key topics covered are injection, broken authentication, sensitive data exposure, XML external entities, broken access control, security misconfiguration, cross-site scripting, insecure deserialization, use of vulnerable components, and insufficient logging/monitoring.





















![A4 XML External Entities
• Attackers can exploit vulnerable XML processors if
they can upload XML or include hostile content in an
XML document
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM "file:///etc/passwd" >]>
<foo>&xxe;</foo>](https://image.slidesharecdn.com/owasptopten2017-190127183427/75/OWASP-Top-Ten-2017-23-2048.jpg)