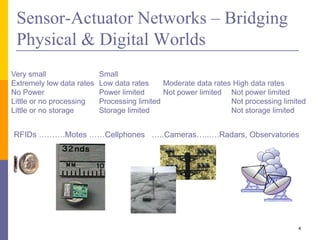
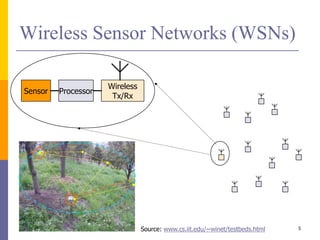
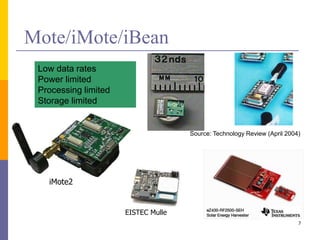
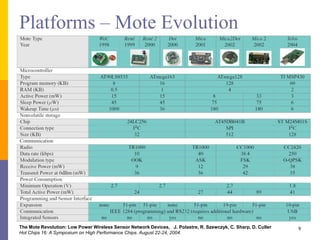
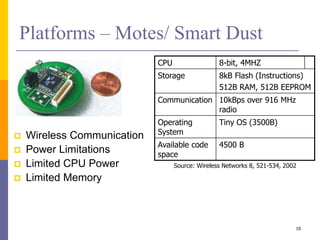
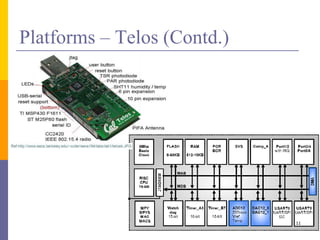
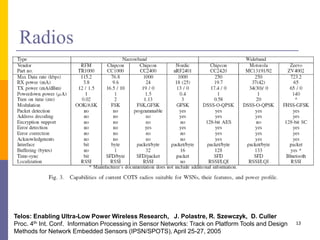
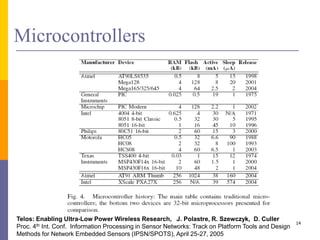
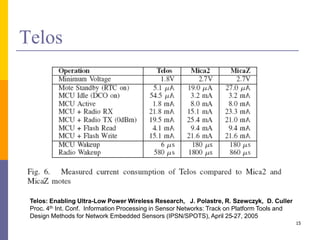
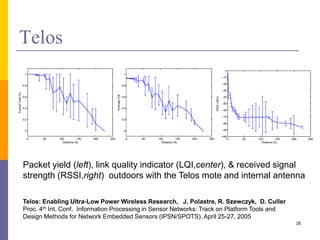
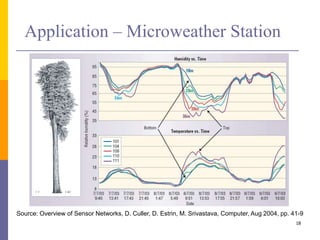
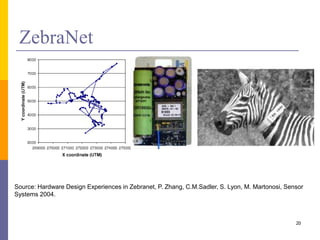
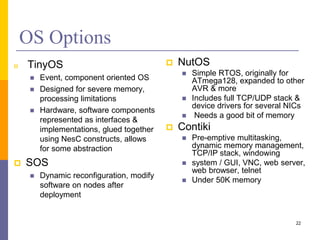
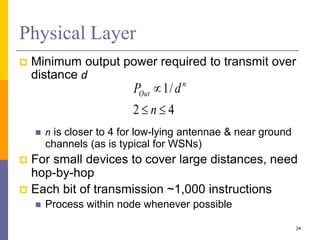
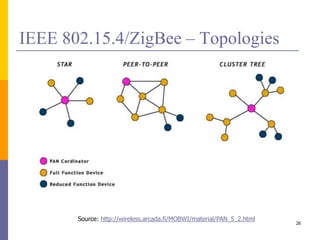
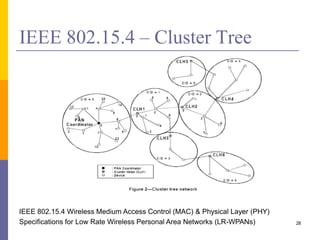
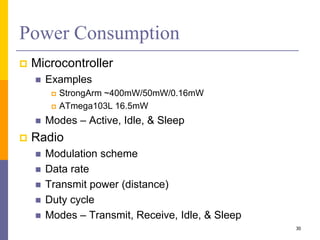
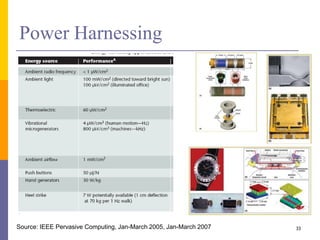
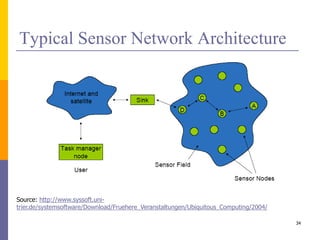
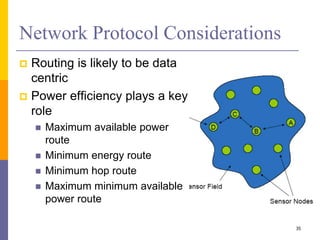
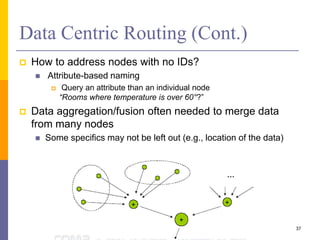
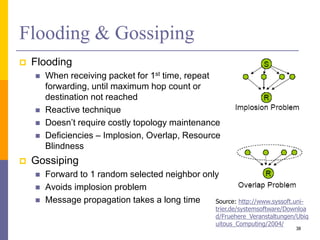
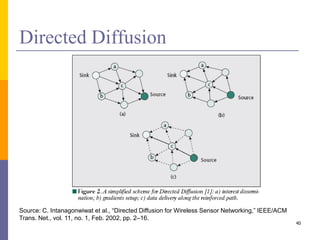
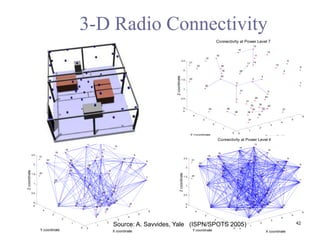
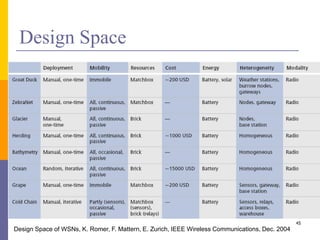
The document provides an overview of wireless sensor networks (WSNs), detailing platforms, protocols, powering methods, and challenges of implementation in an Internet of Things (IoT) context. It discusses the evolution and functionalities of smart devices like motes, the importance of energy efficiency, and various applications including environmental monitoring and livestock management. Additionally, it addresses security and privacy implications associated with deploying these networks.