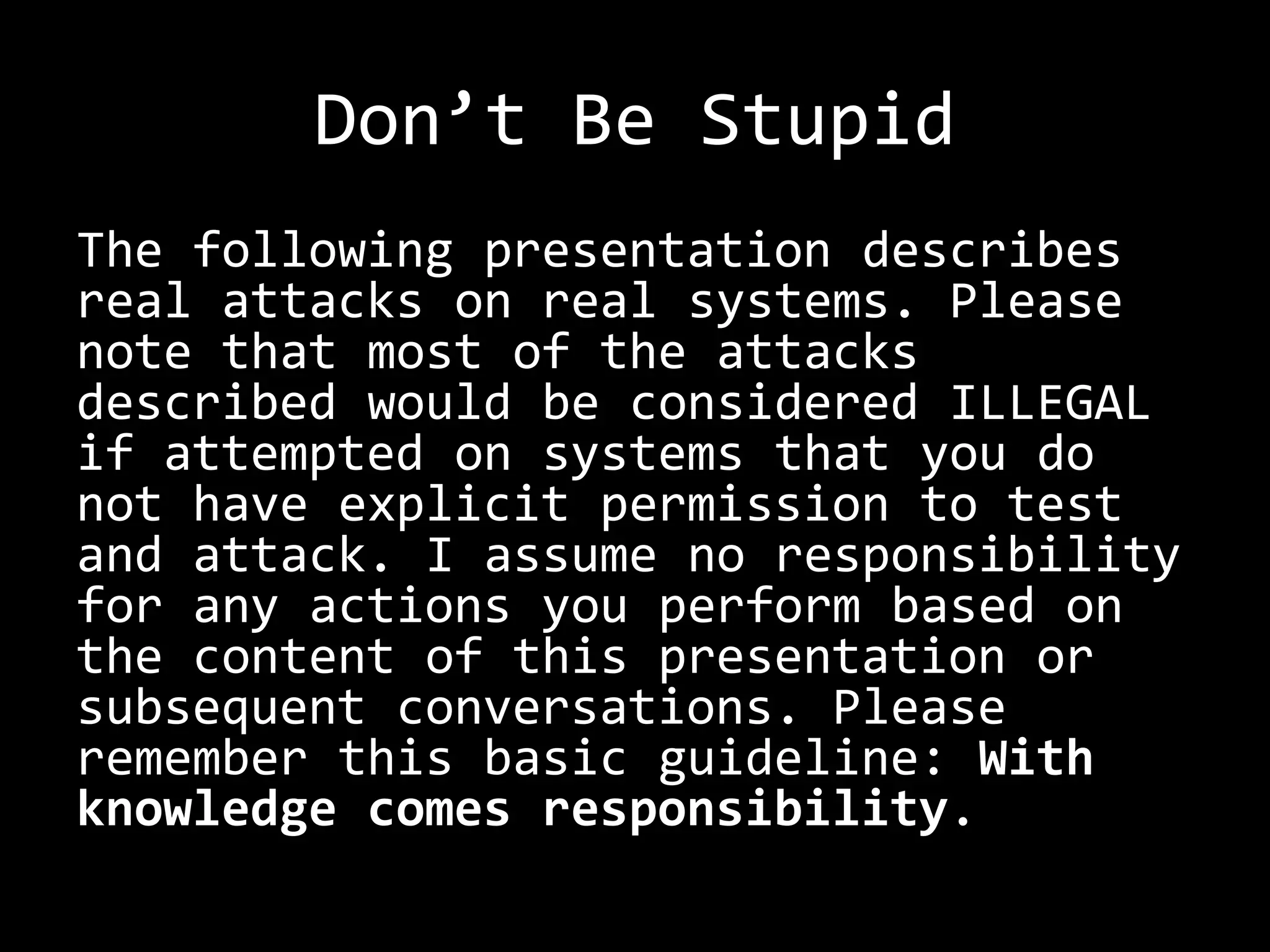
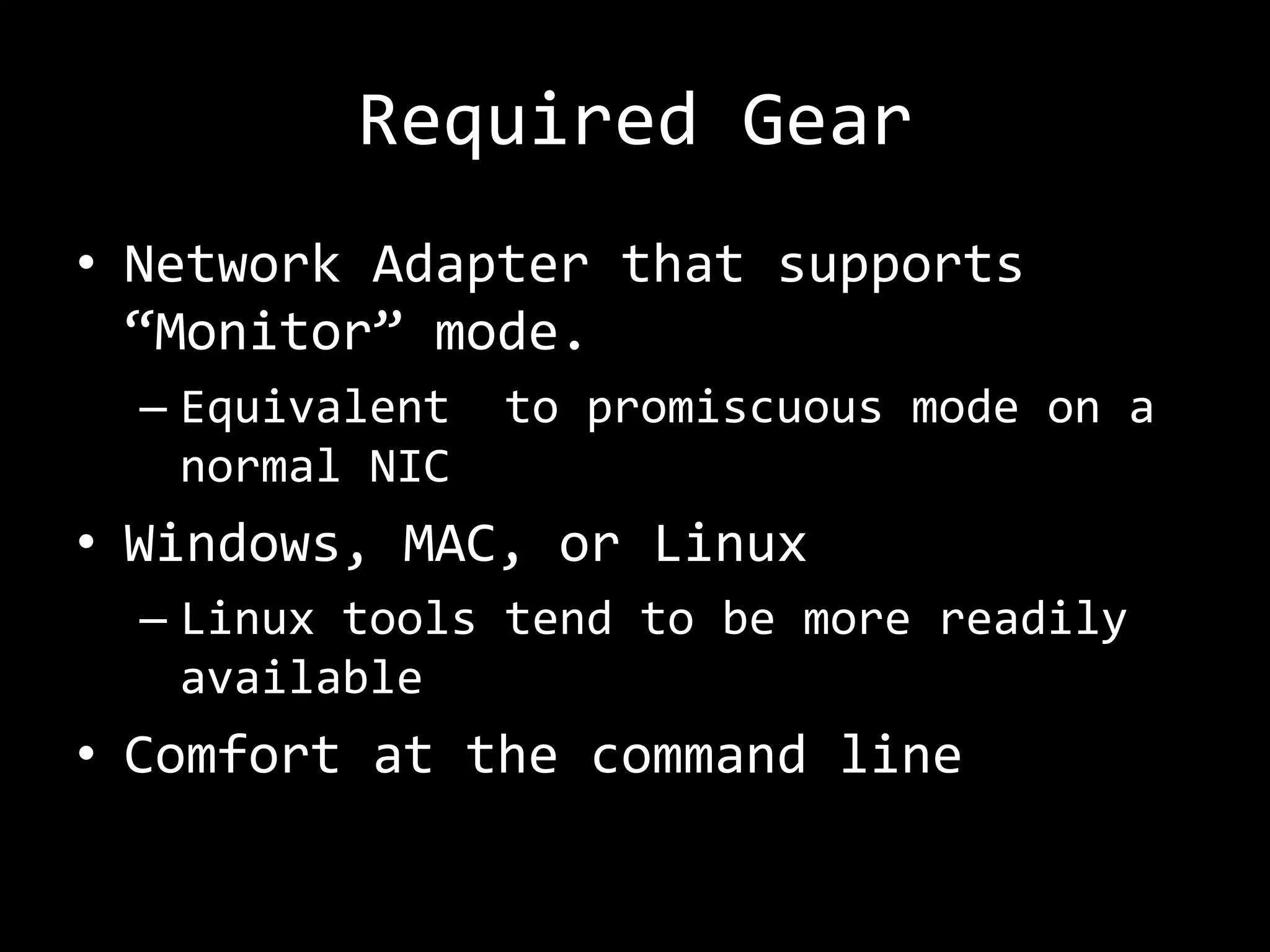
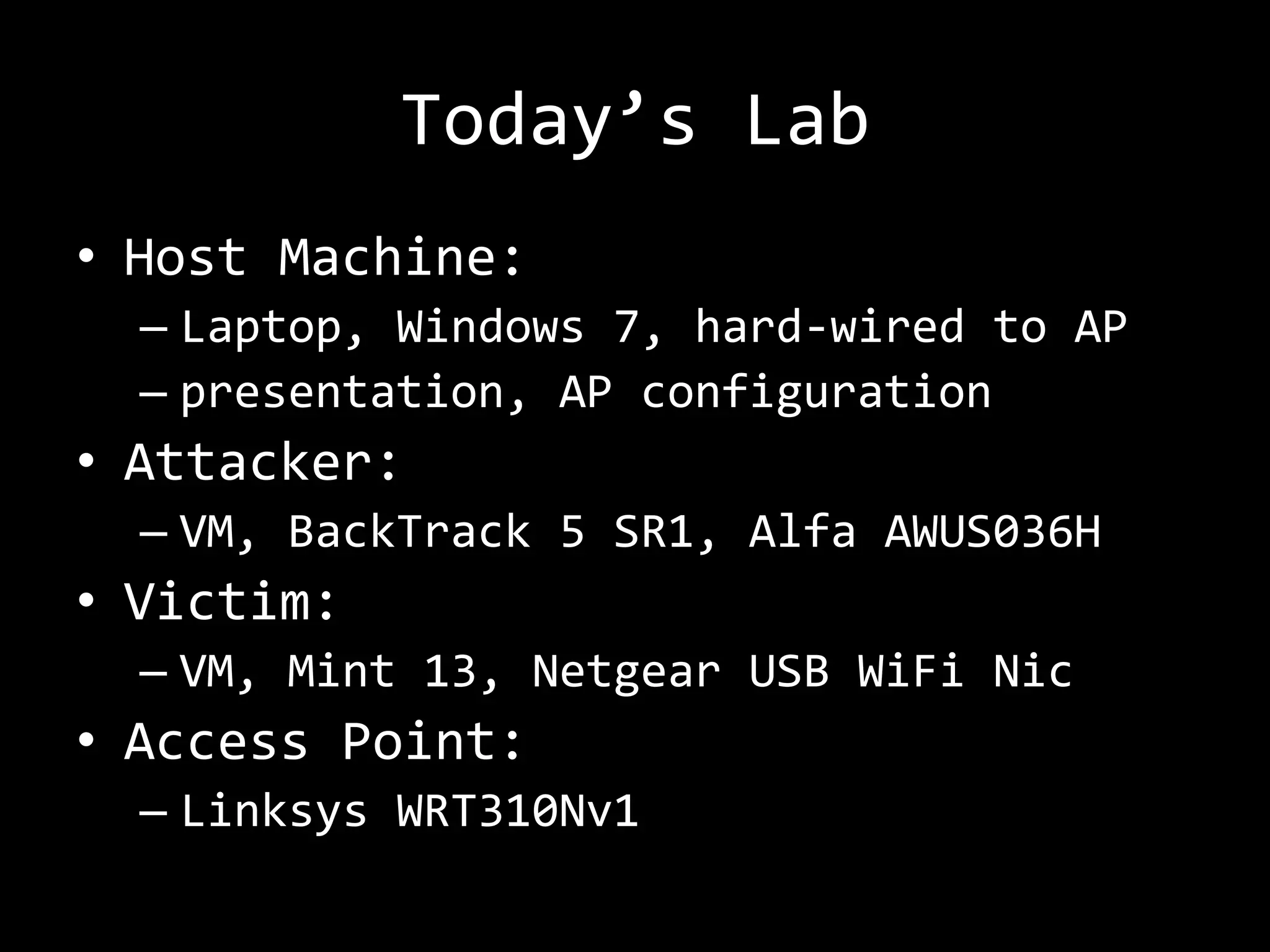
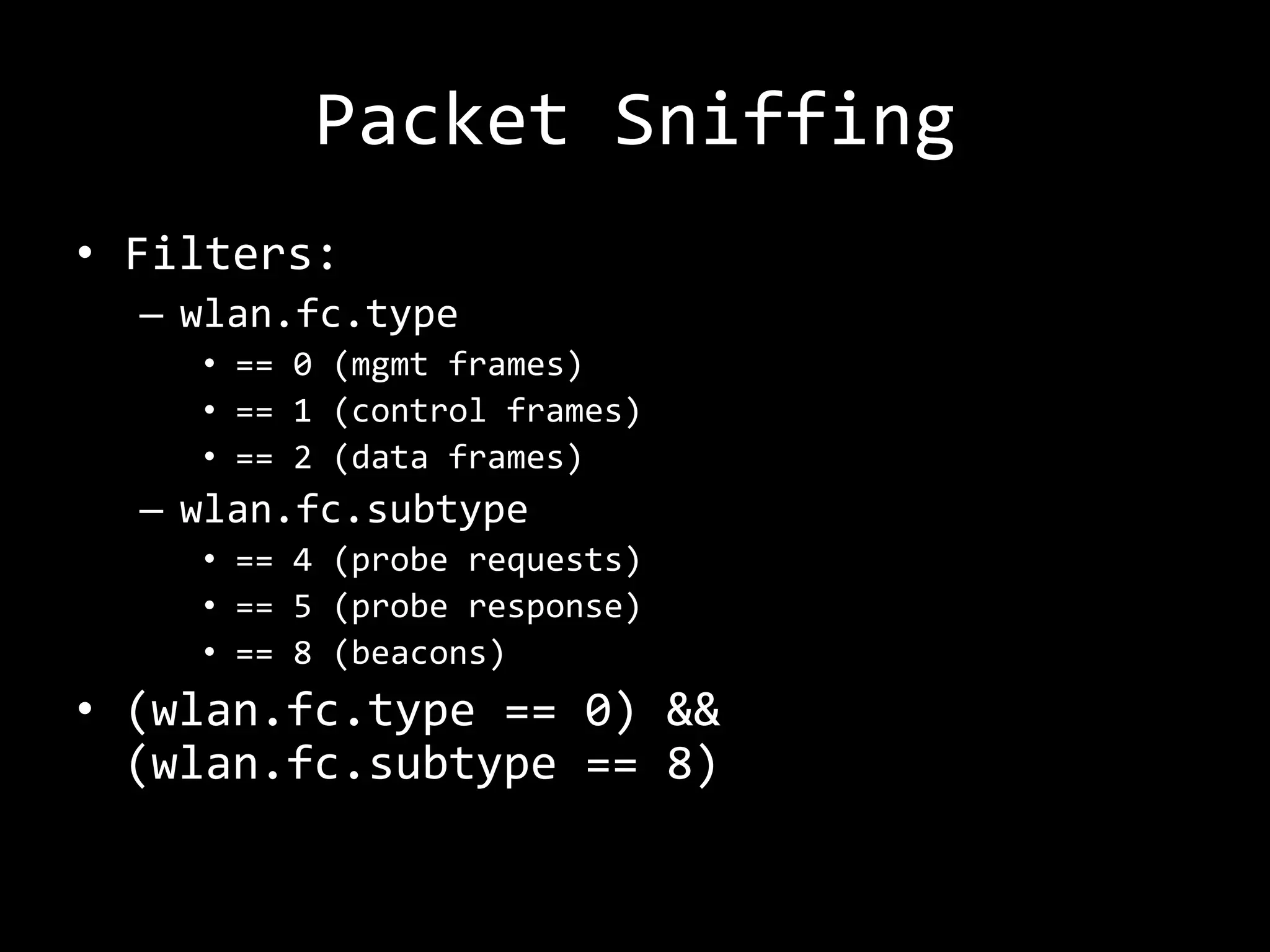
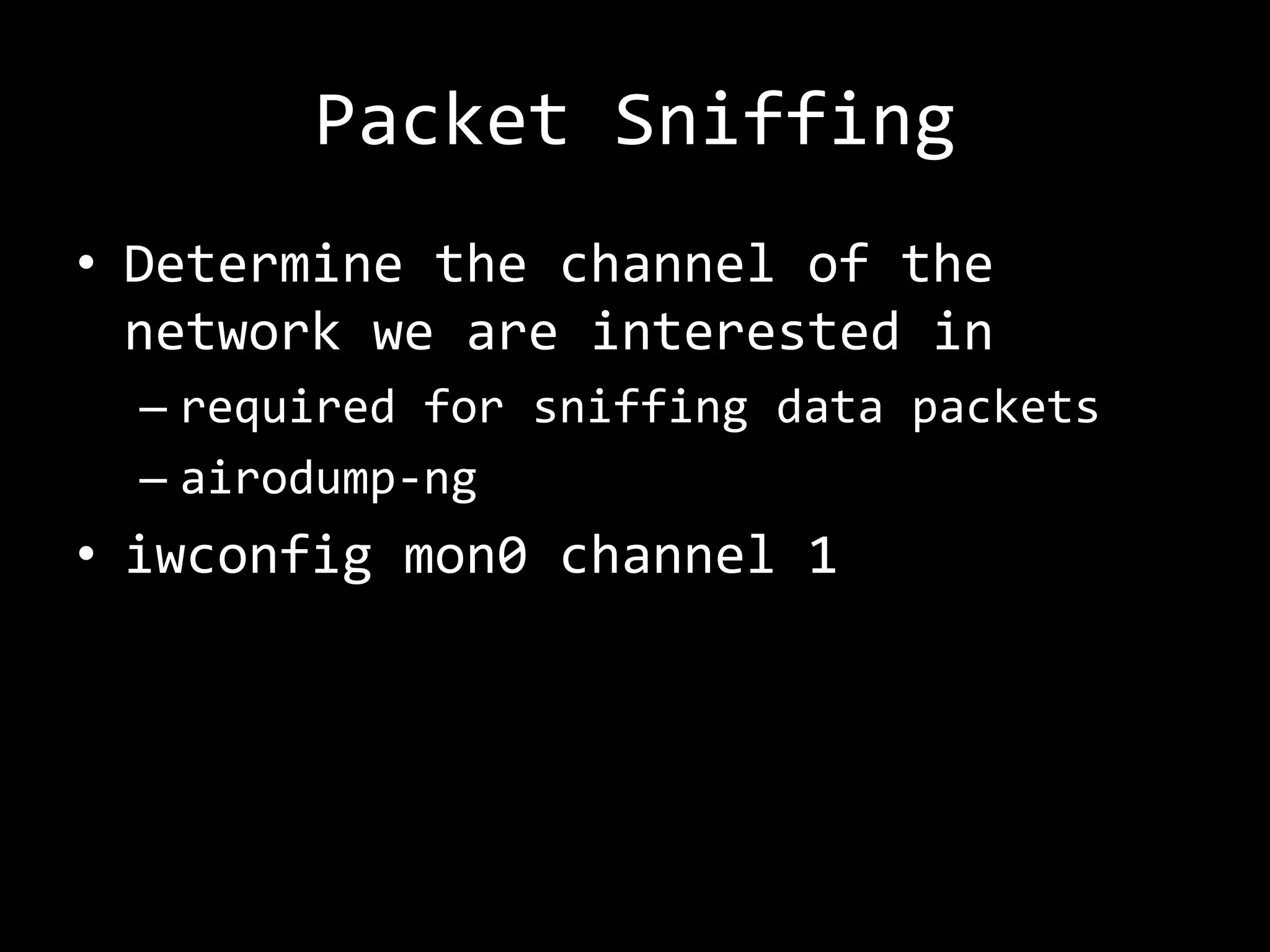
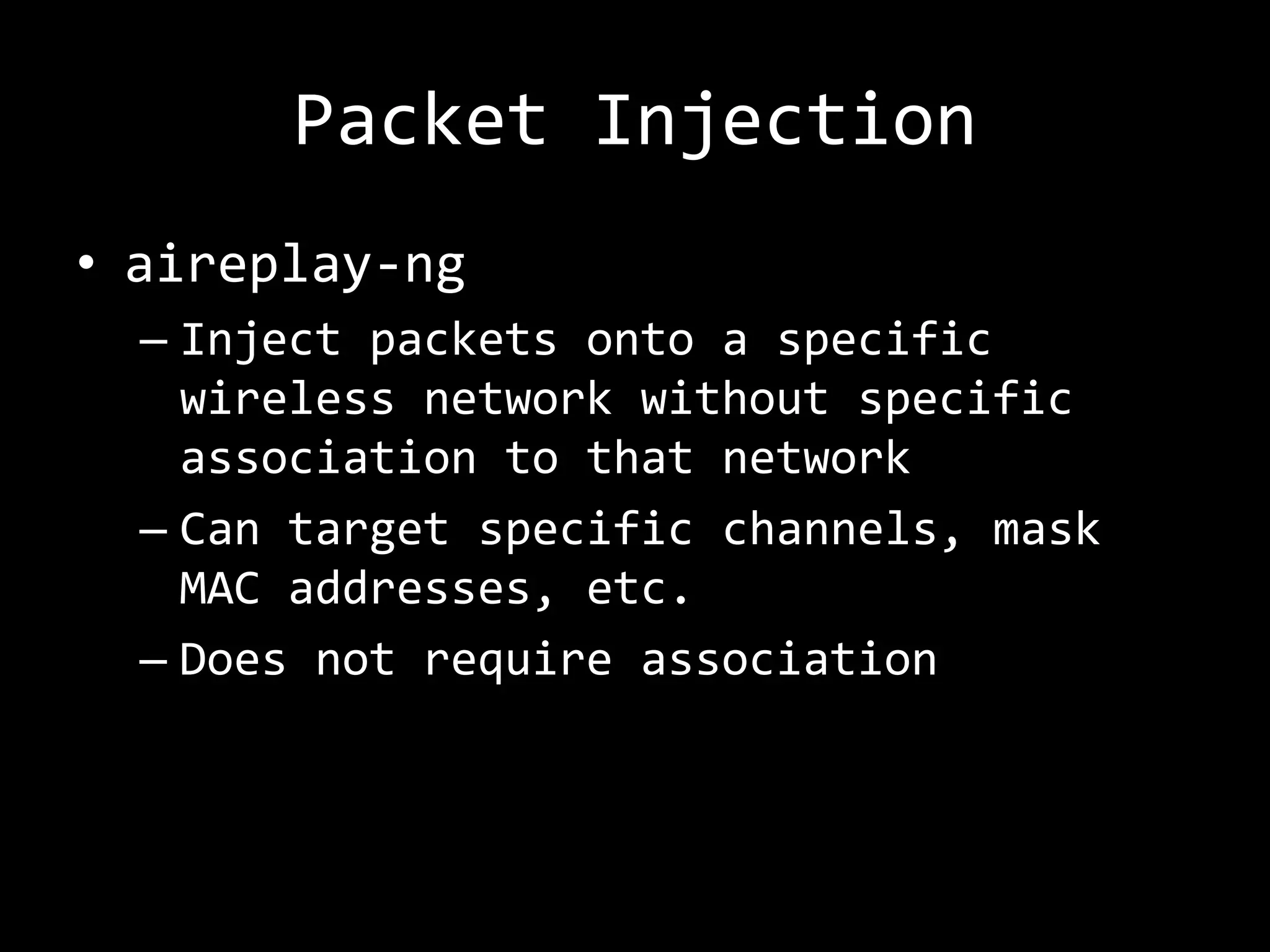
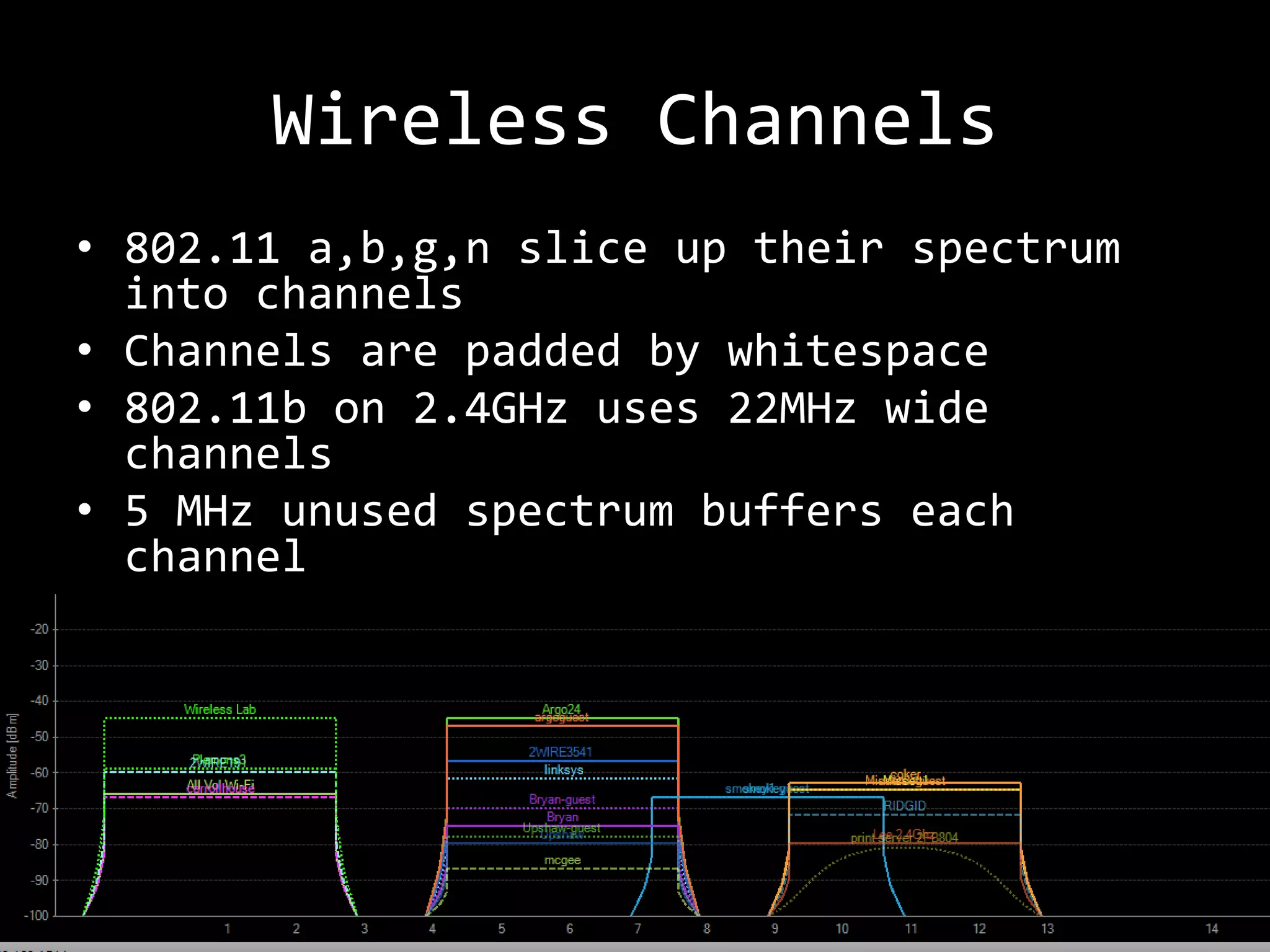
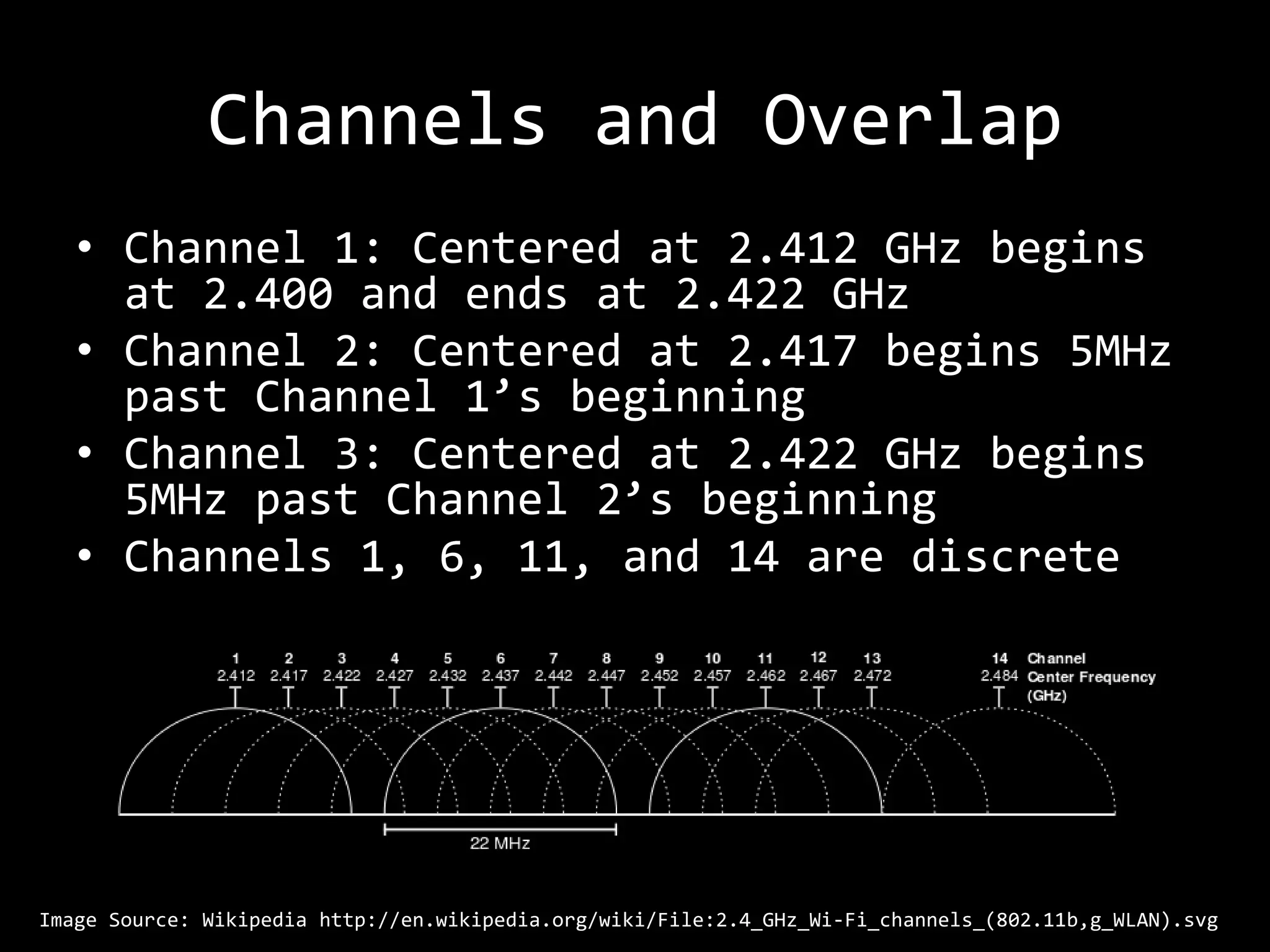
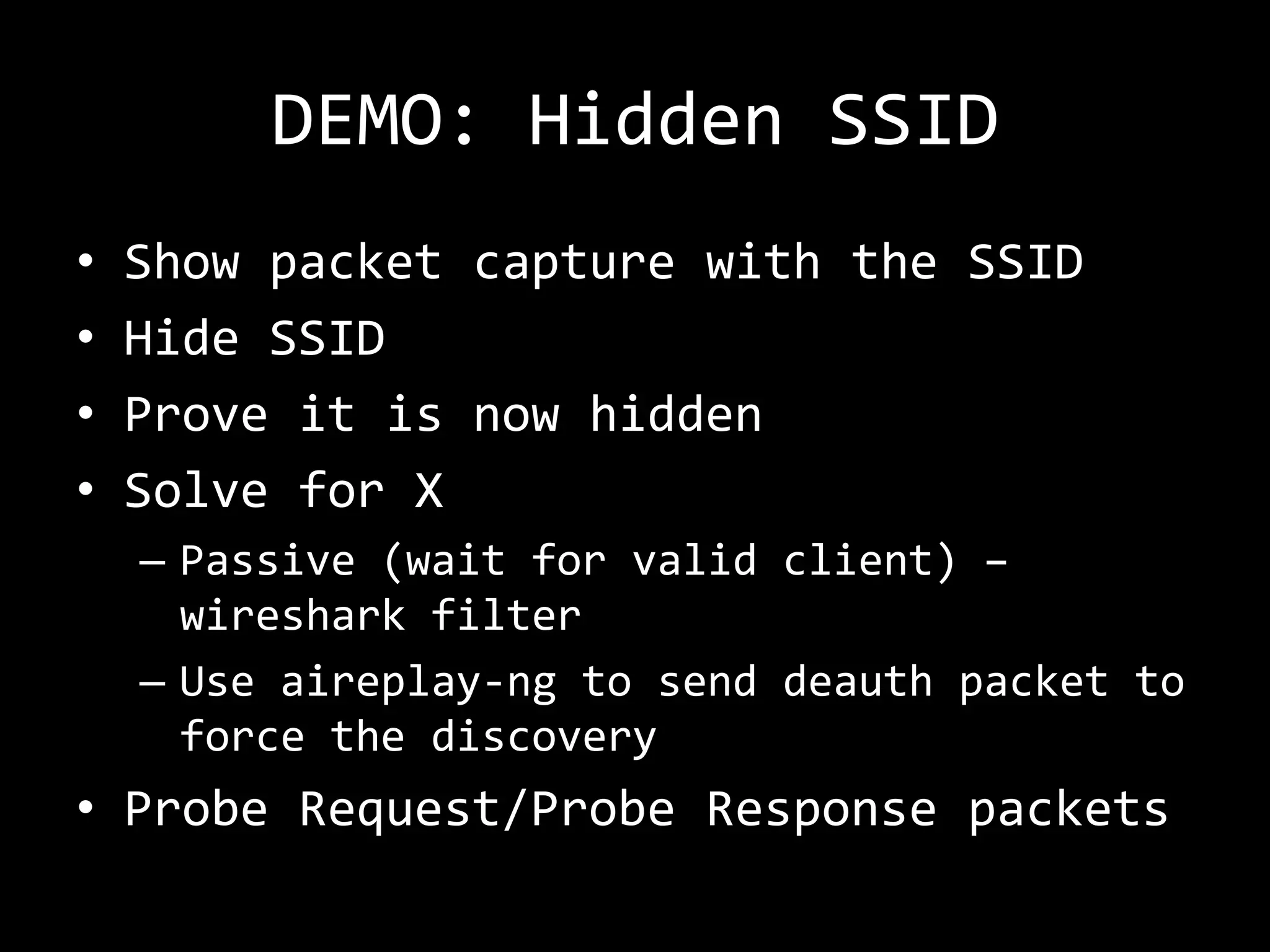
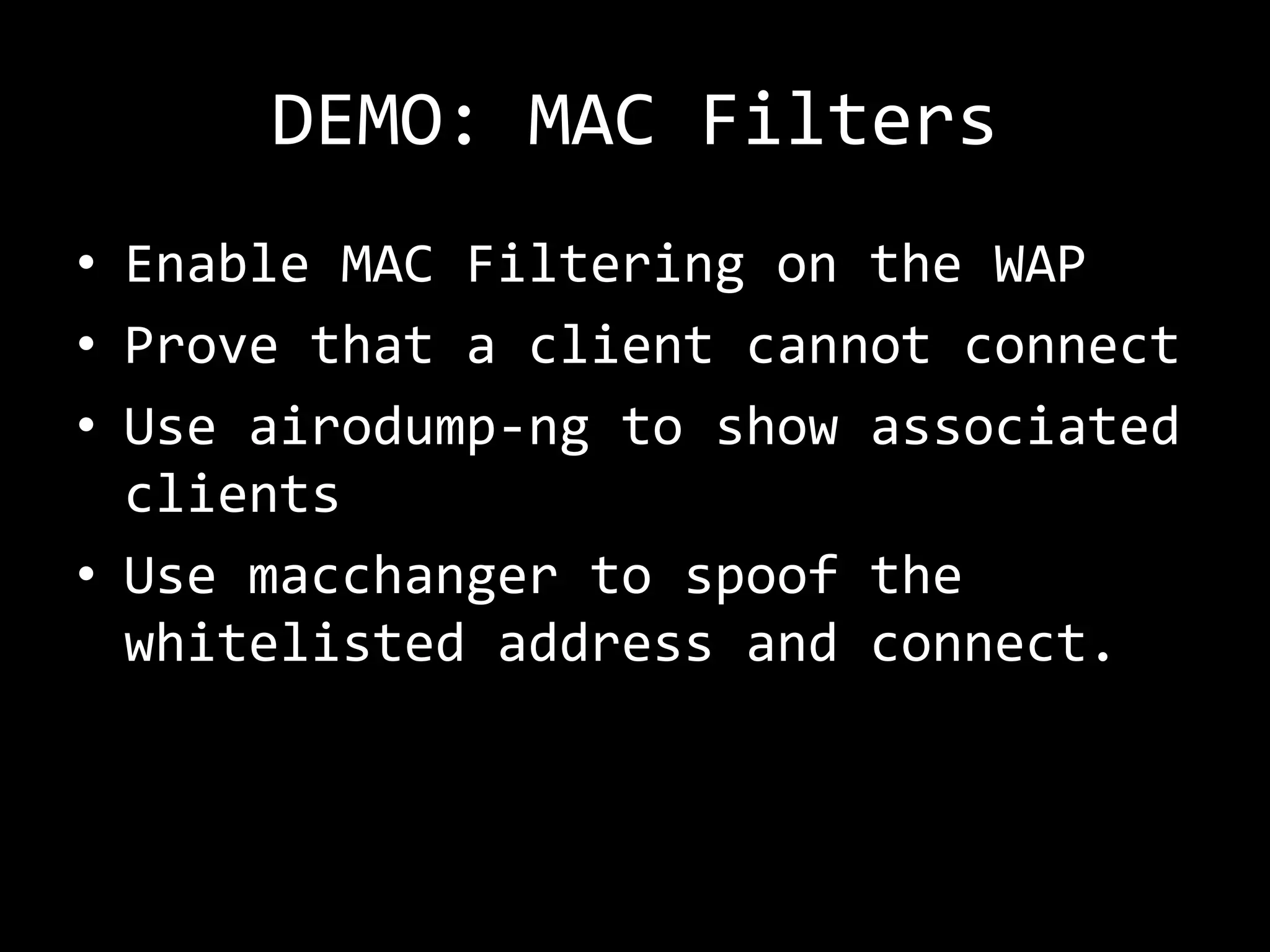
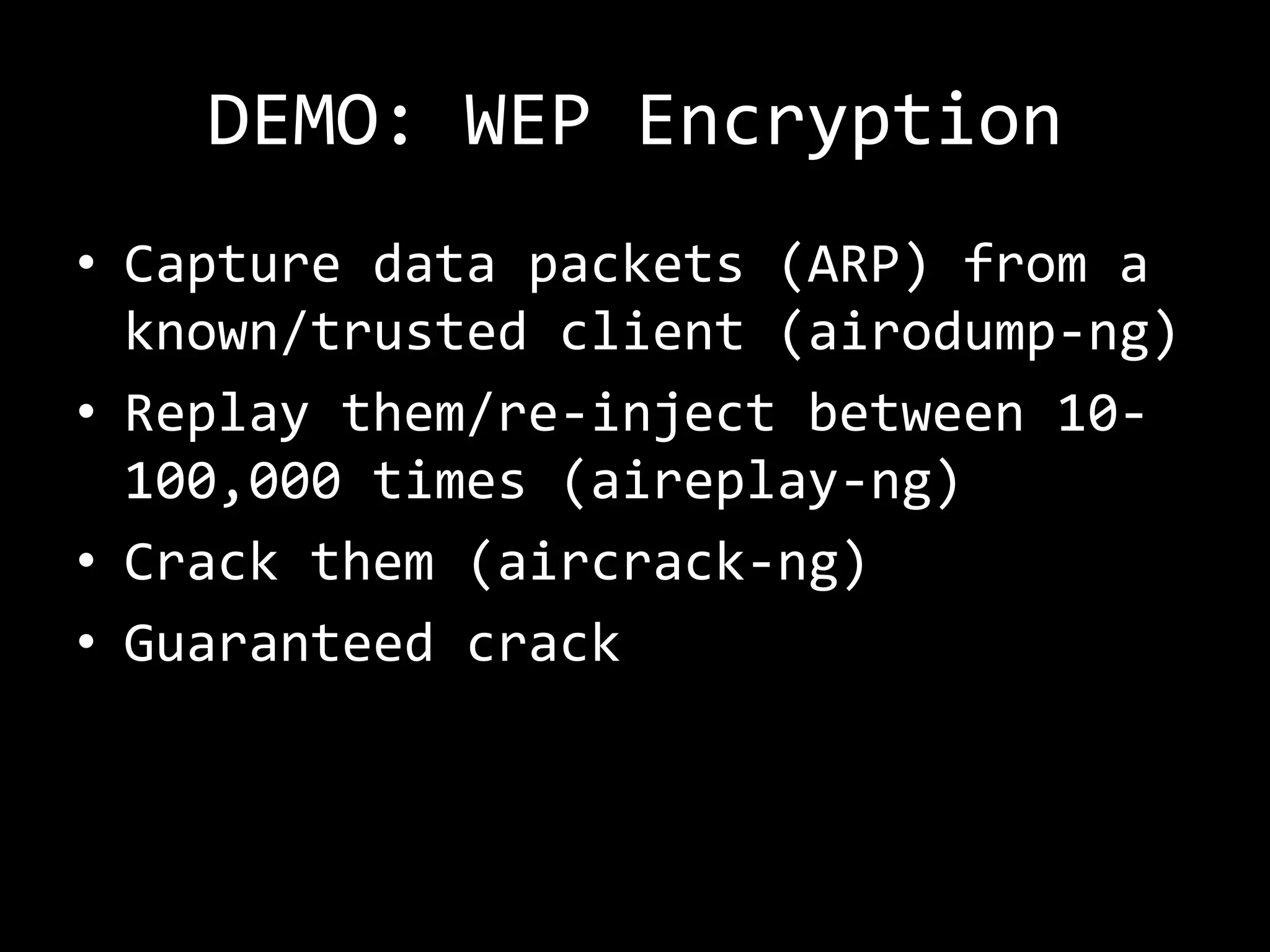
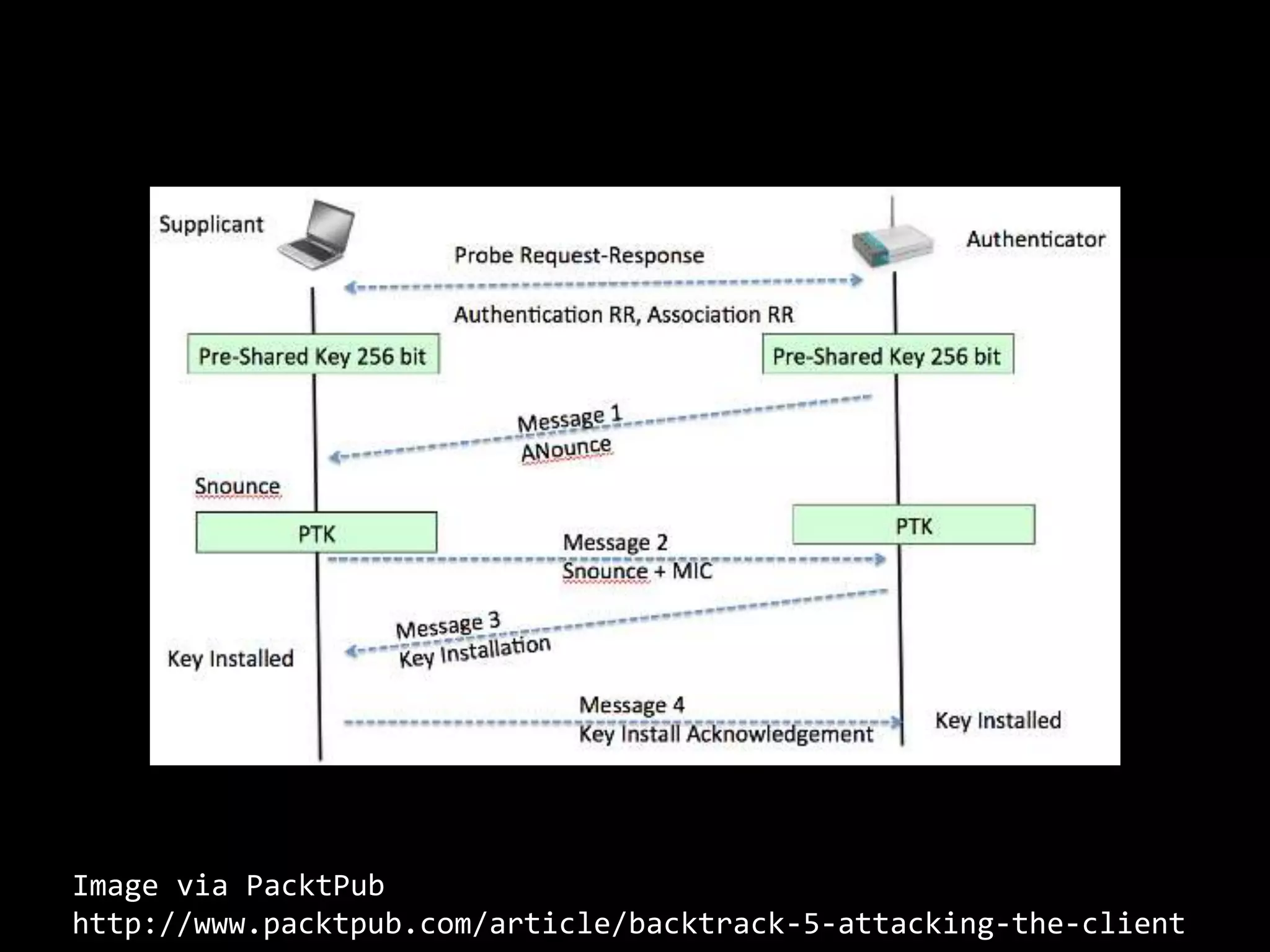
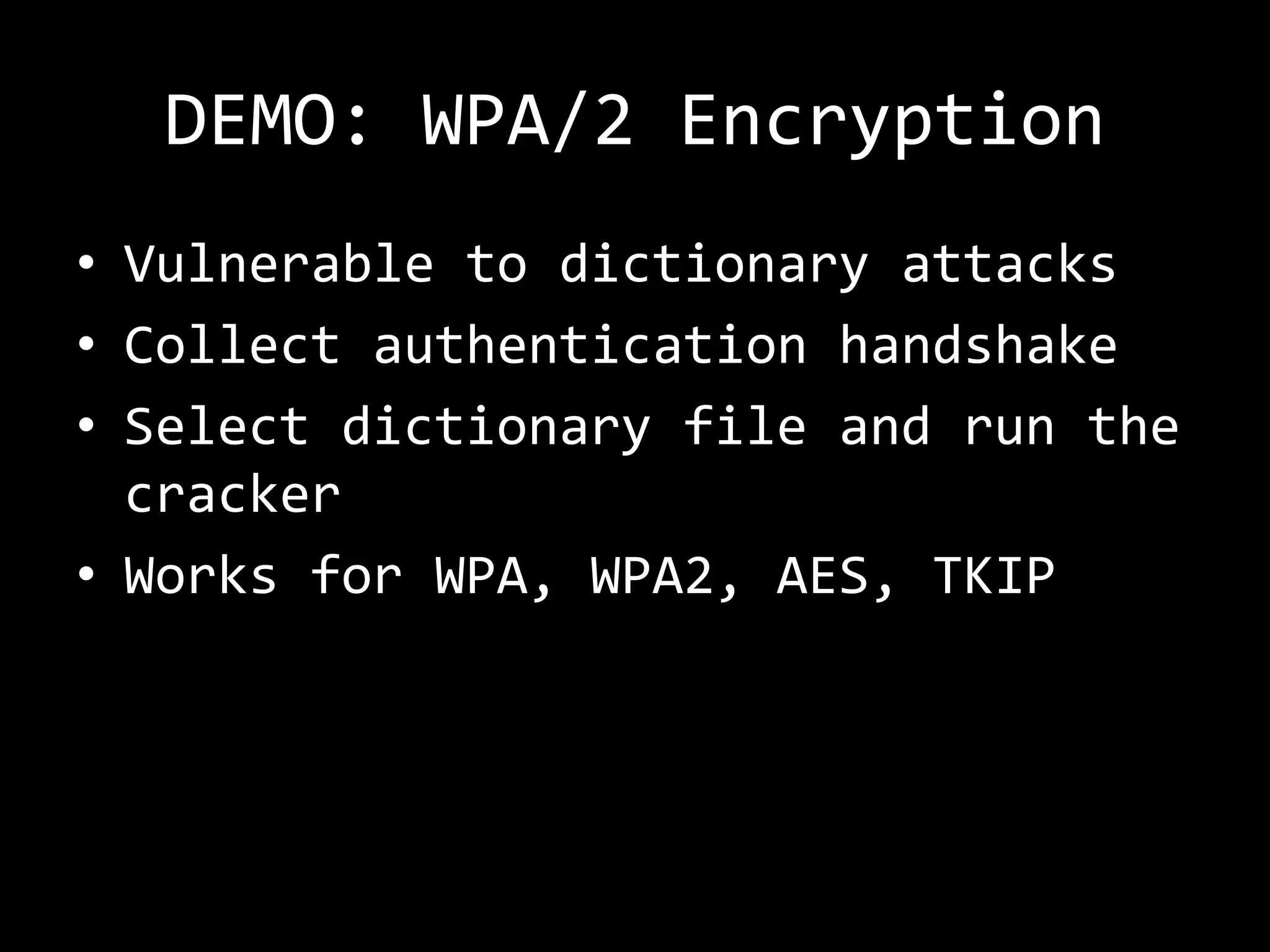
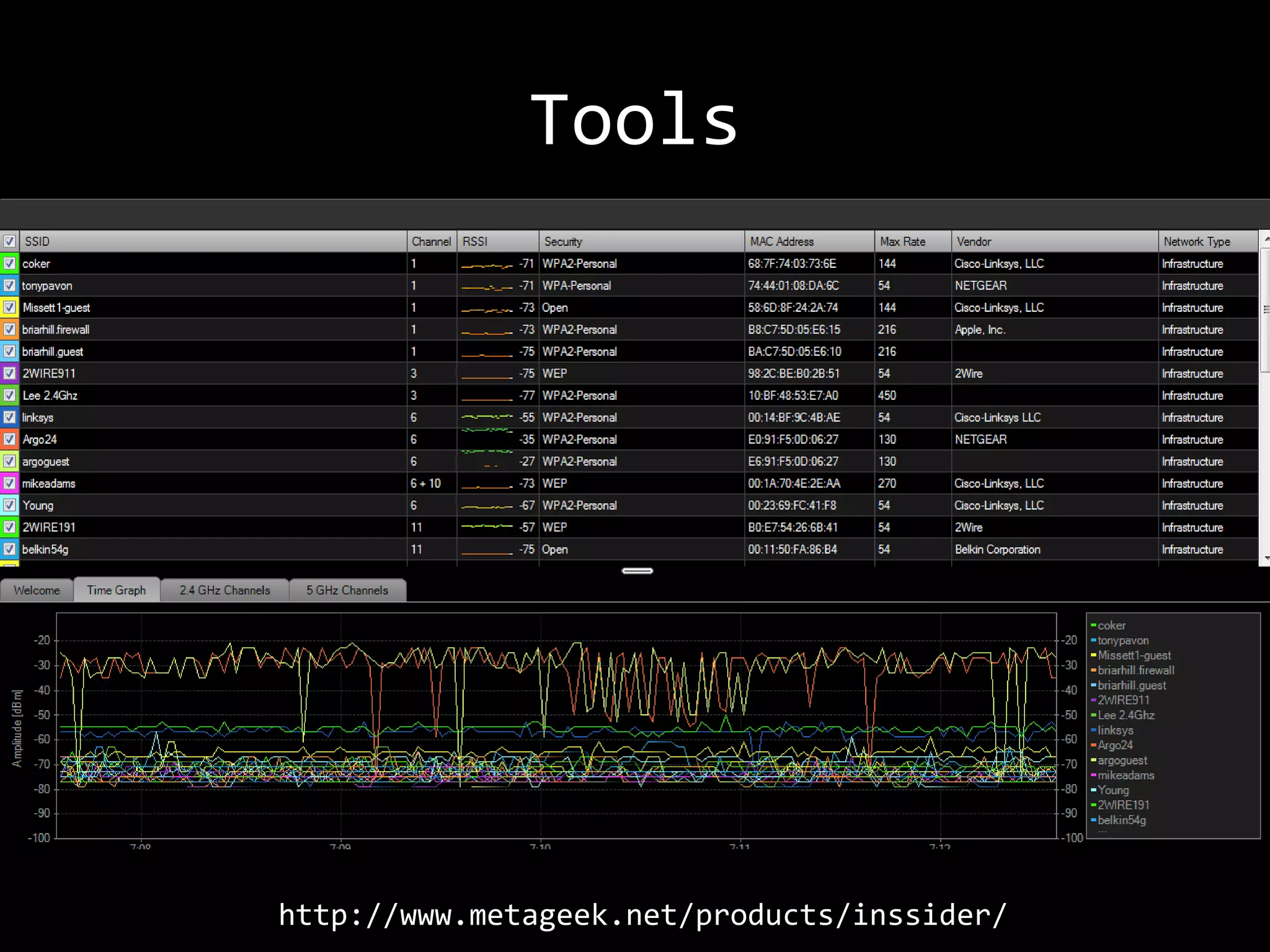
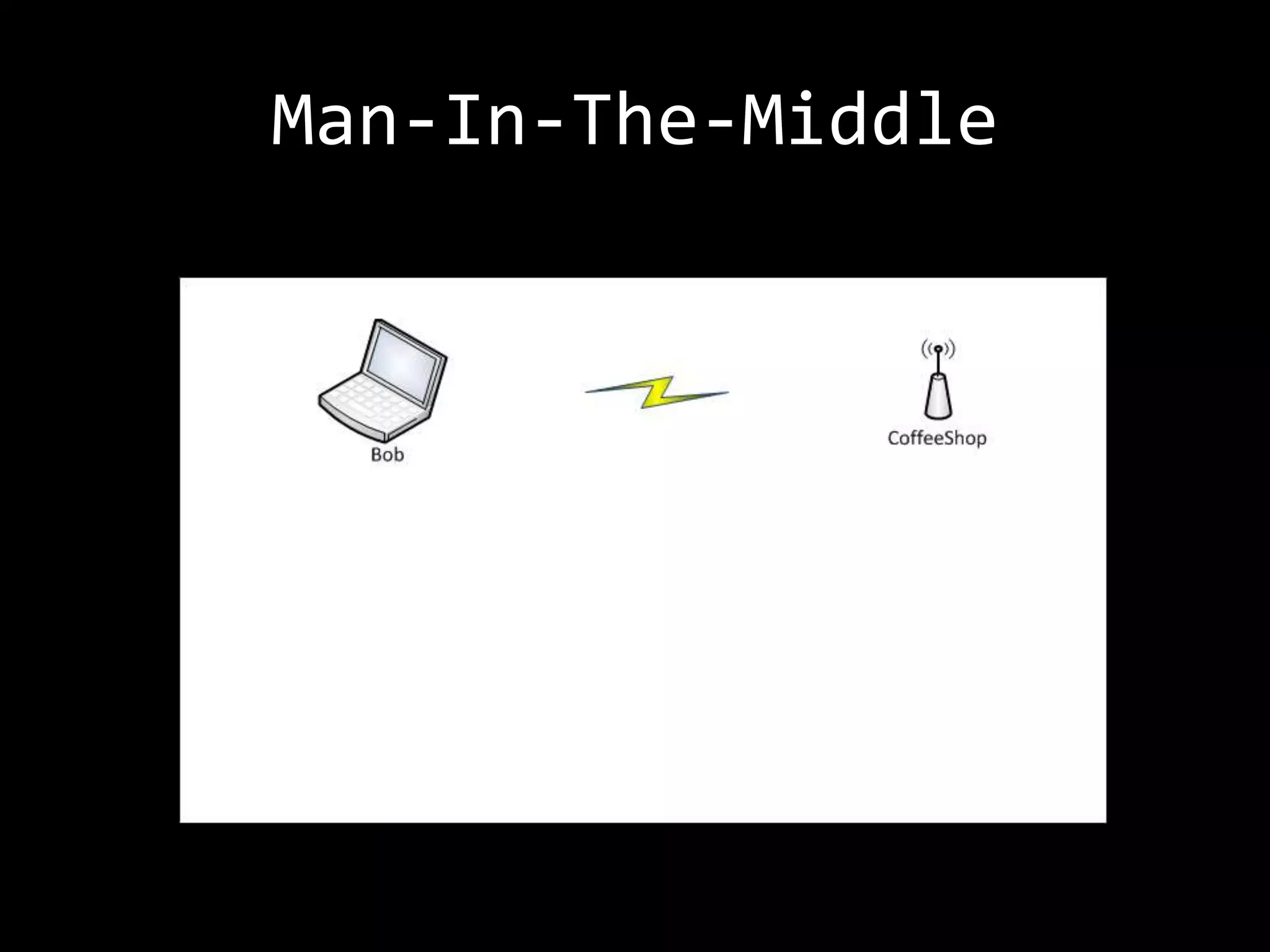
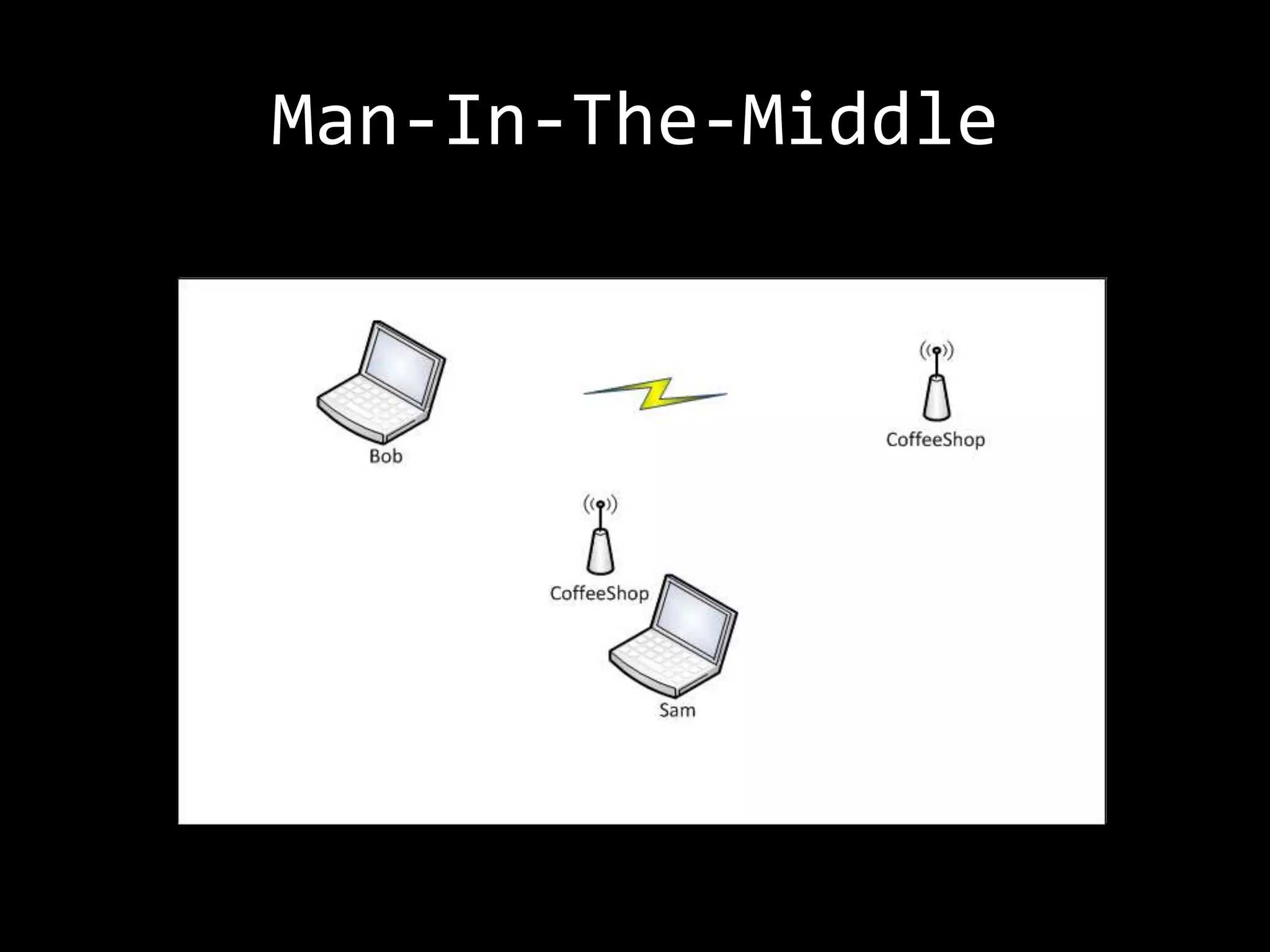
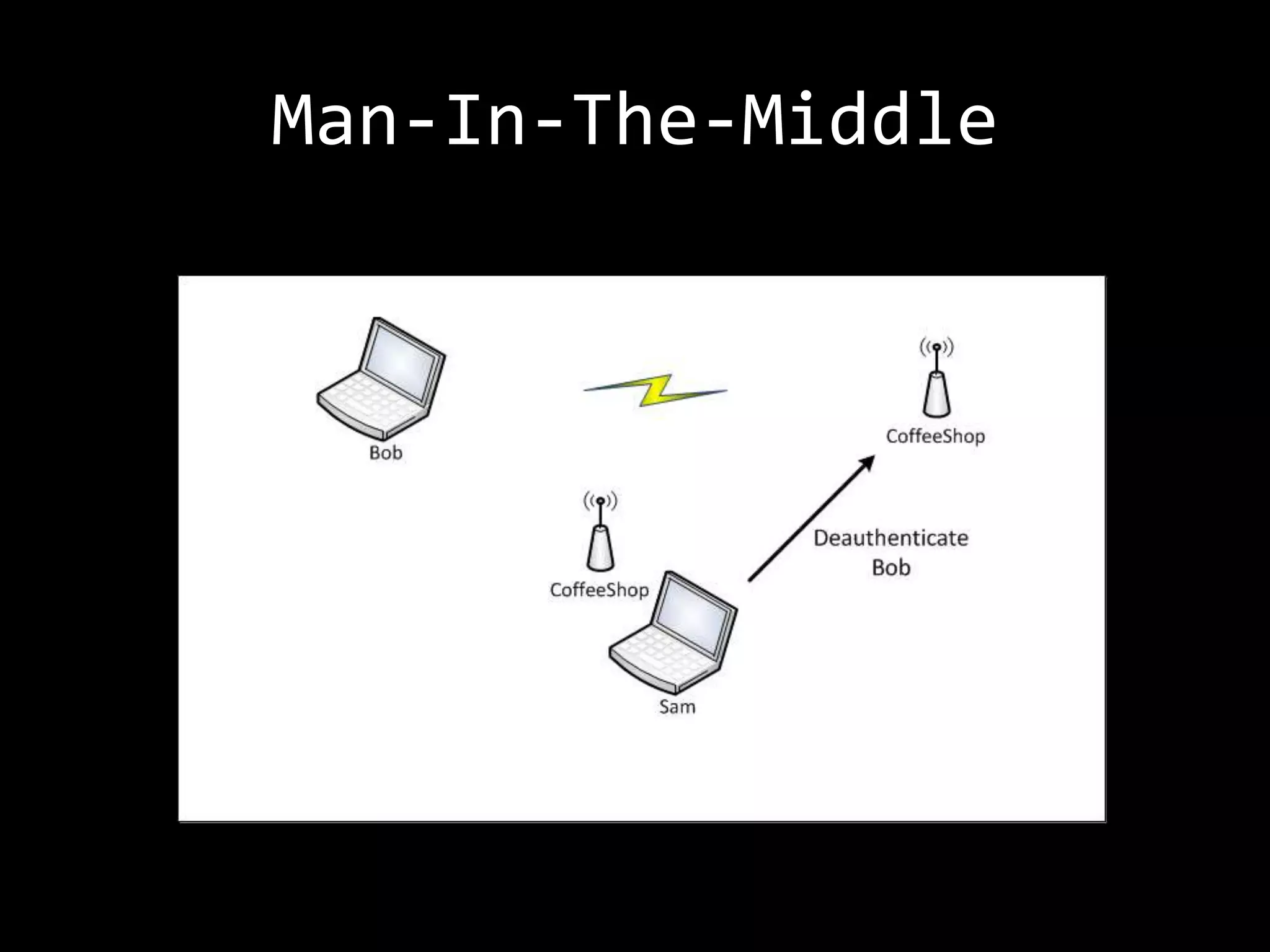
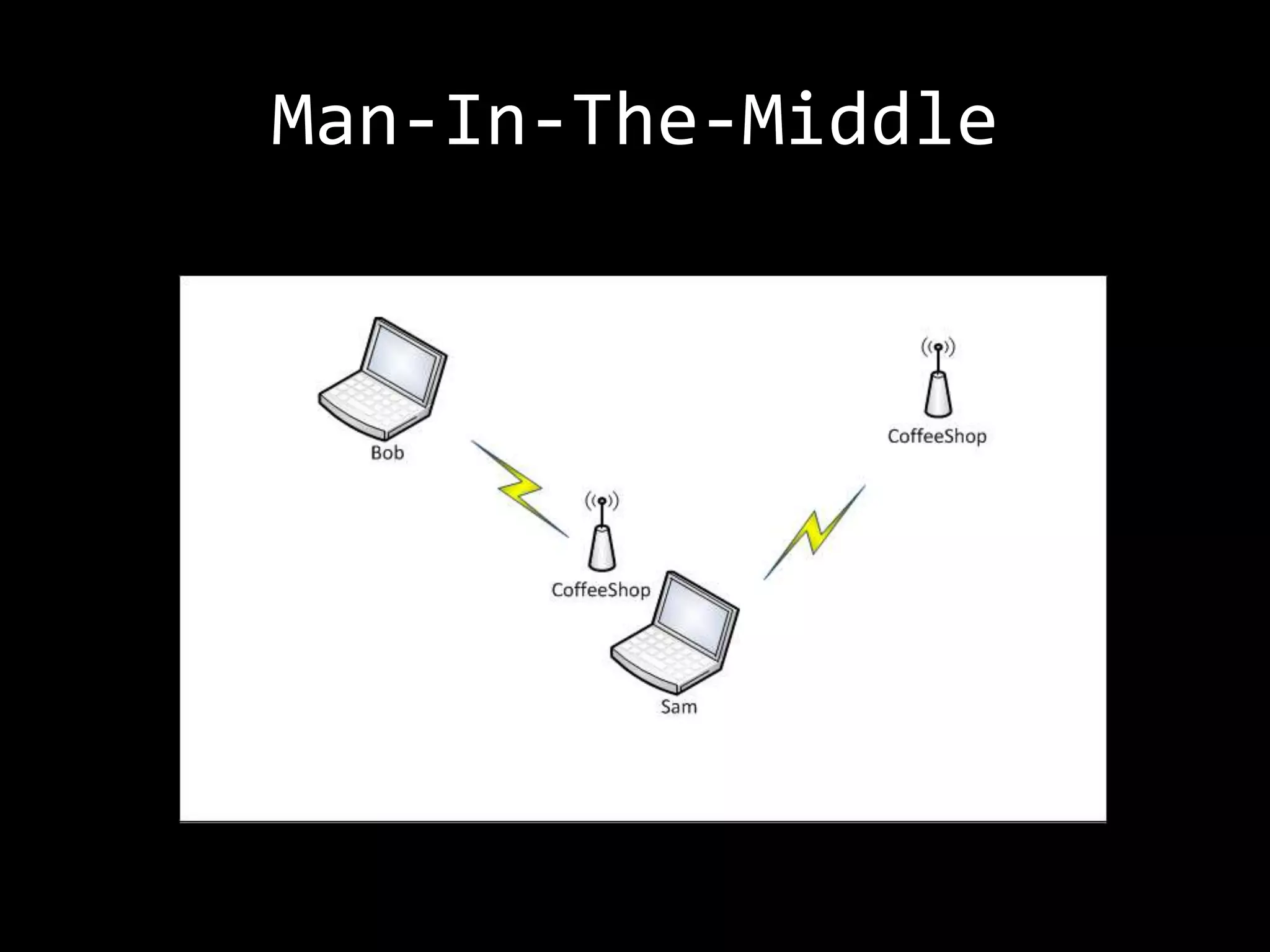
The document discusses attacks on WiFi networks and provides an overview of wireless security testing tools and techniques. It notes that most attacks described would be illegal without permission and assumes no responsibility. It then covers wireless packet frames, packet sniffing filters, packet injection, wireless channels, hidden SSIDs, MAC filters, WEP cracking, WPA/WPA2 cracking using dictionaries, wireless security testing tools like Pineapple and Reaver, and recommendations for more secure wireless practices.