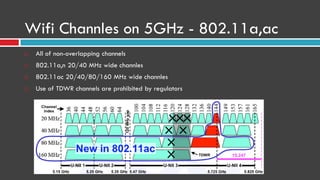
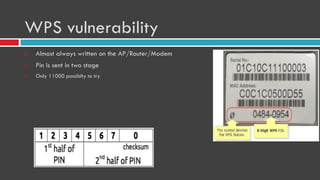
This document provides an overview of wireless networks and security. It discusses the evolution of IEEE 802.11 WiFi standards over time, including vulnerabilities in early versions like WEP. It also covers wireless topics like ISM bands, channel layout, modes, and common attacks against open or weakly encrypted networks. The document demonstrates wireless scanning and attacks. It introduces RF concepts like electromagnetic interference and TEMPEST attacks. Finally, it presents wireless security tools like Ubertooth, RTL-SDR, and HackRF.
























![Tempest
TEMPEST is a National Security Agency specification and NATO certification[1][2] referring to
spying on information systems through
Radio or Electrical signals
Sounds
Vibrations](https://image.slidesharecdn.com/wirelessnetworksandsecurity-150416030018-conversion-gate01/85/Kablosuz-Iletisim-ve-Guvenlik-36-320.jpg)





