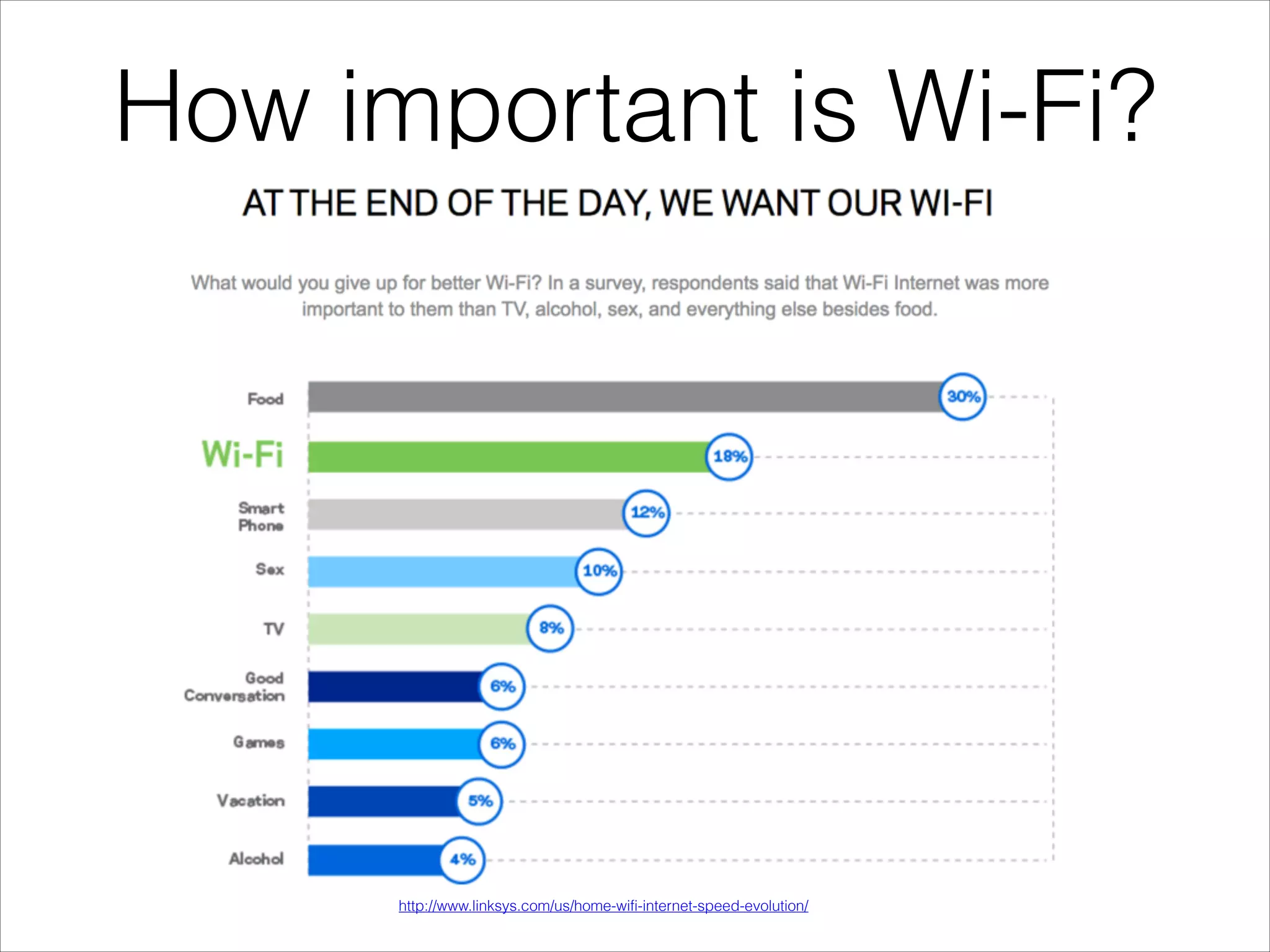
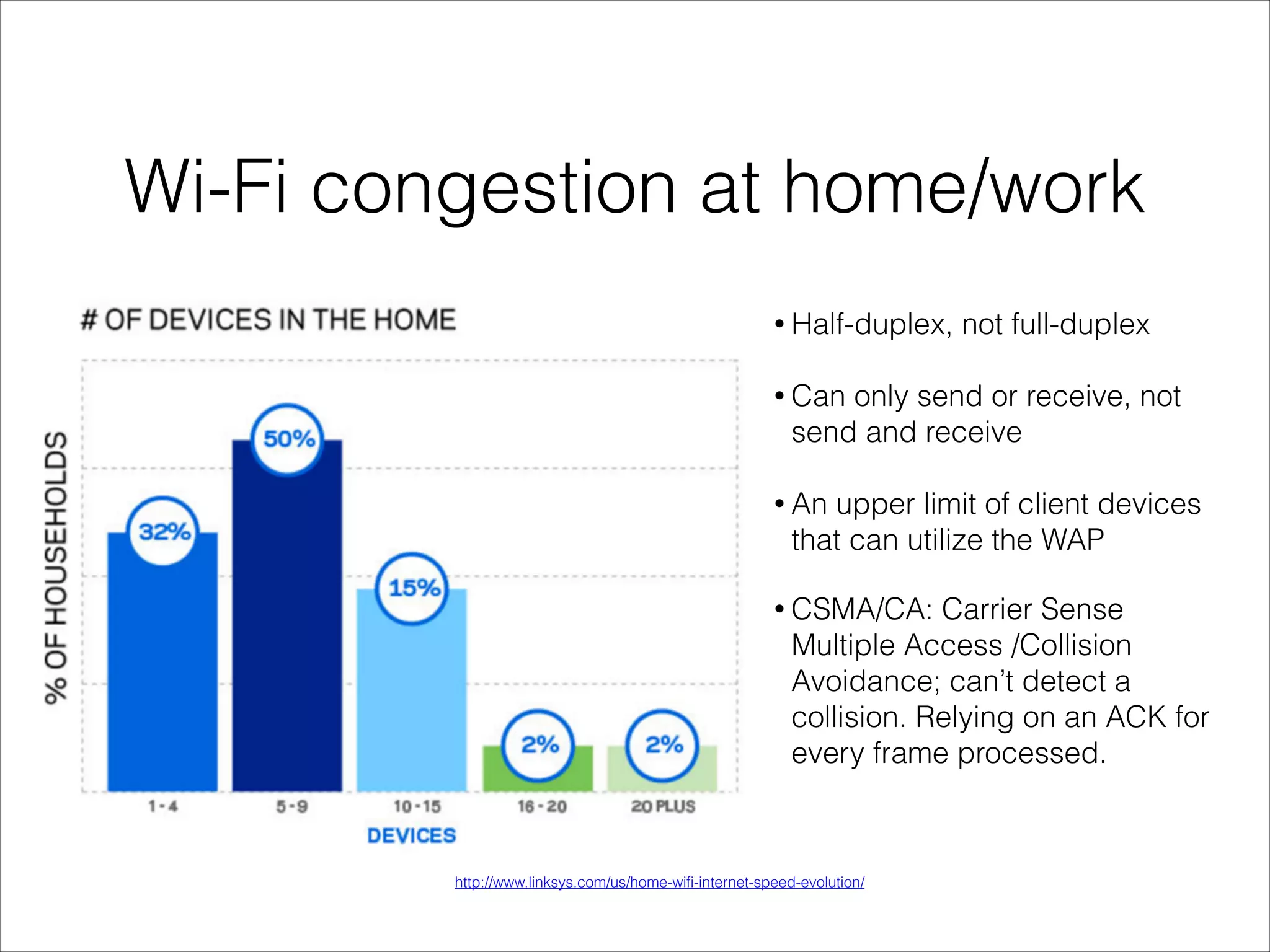
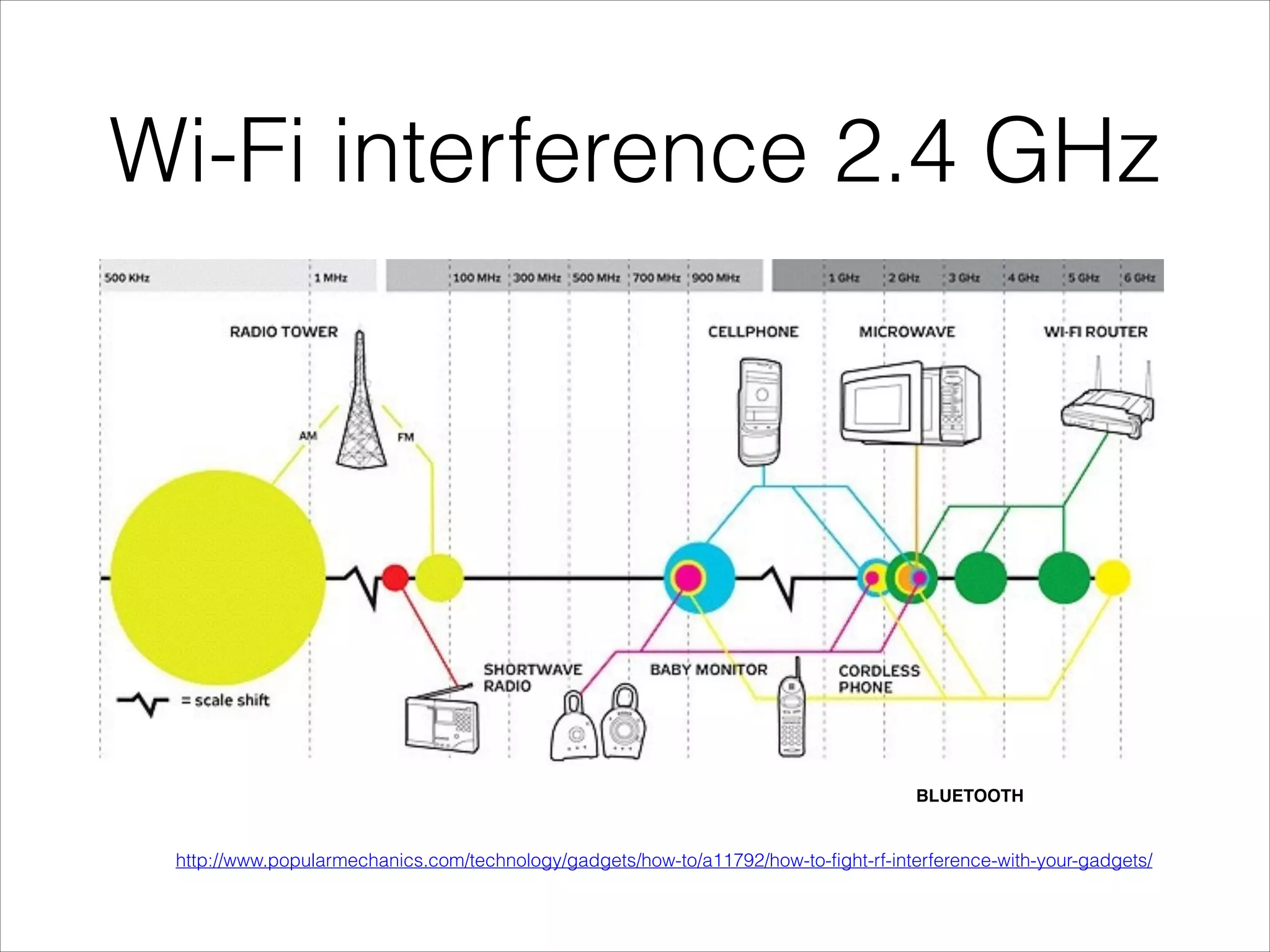
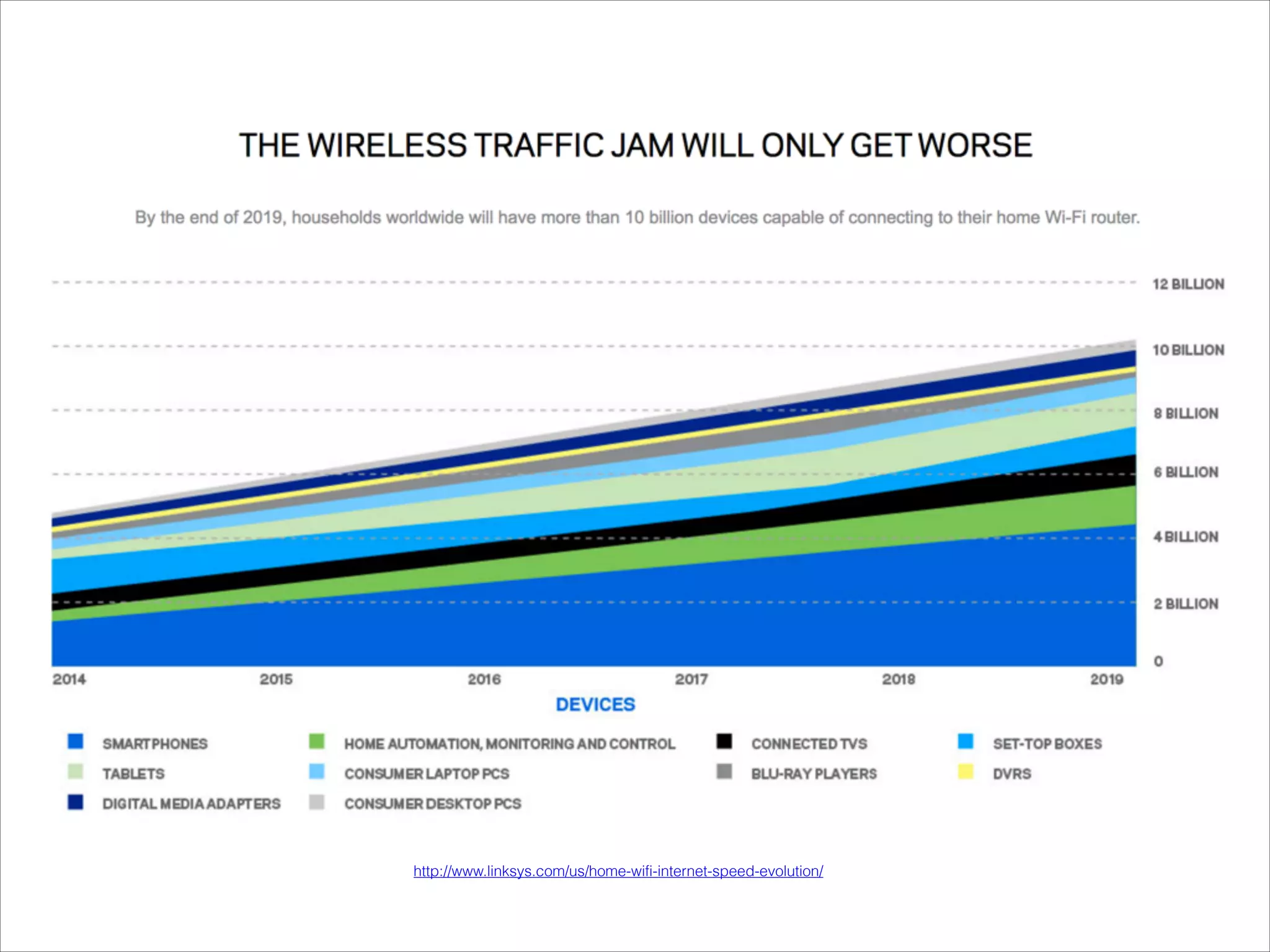
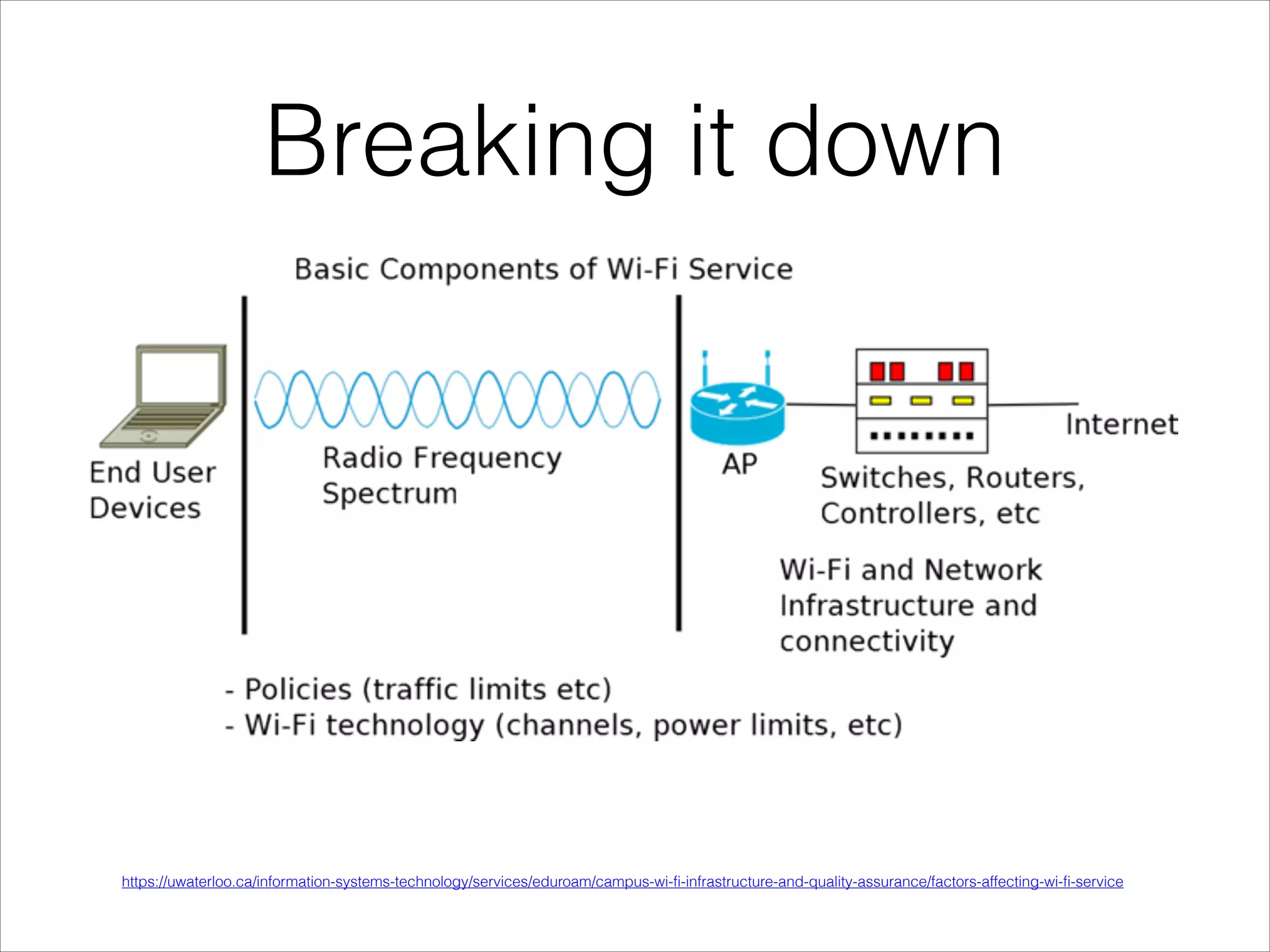
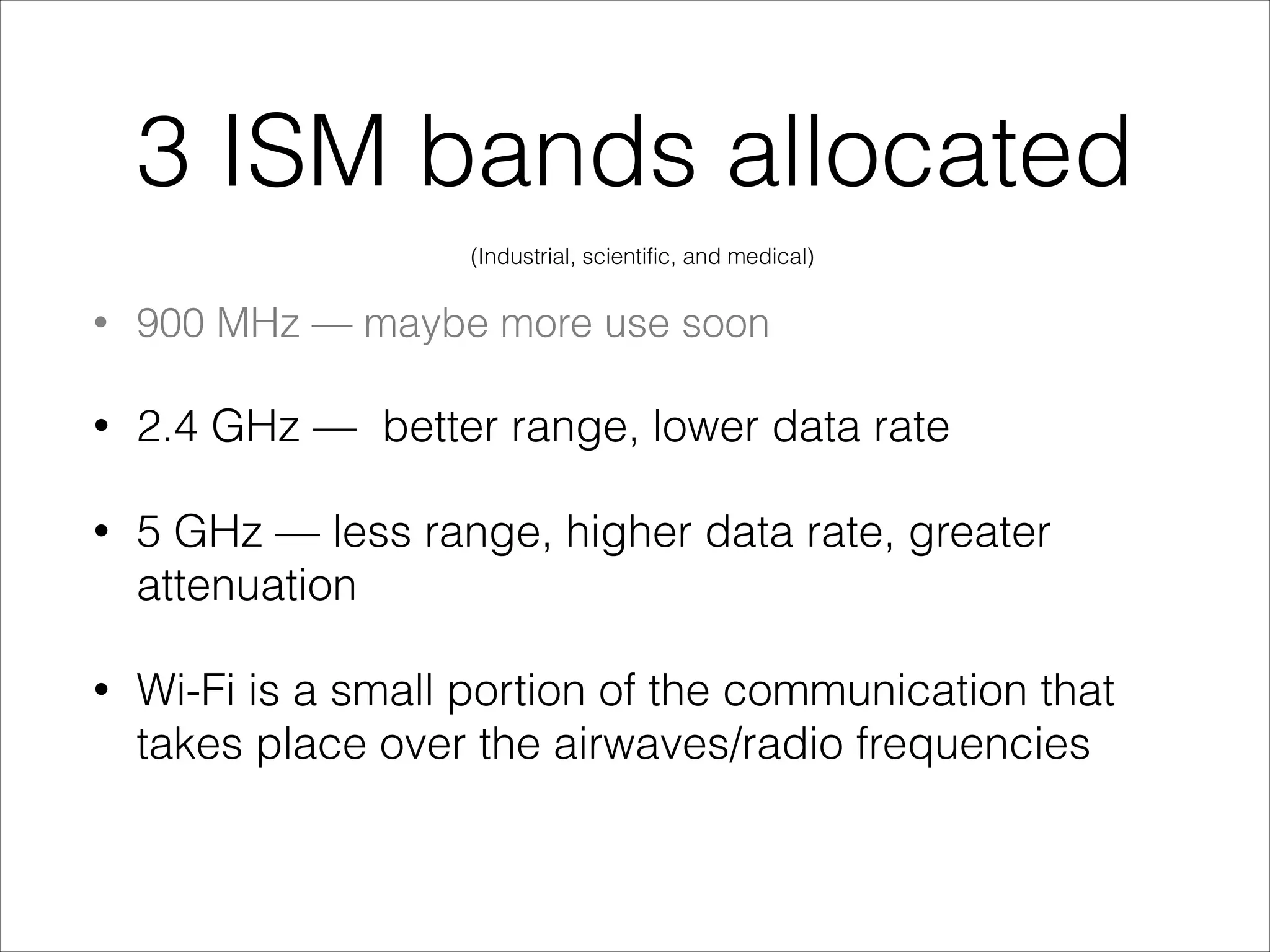
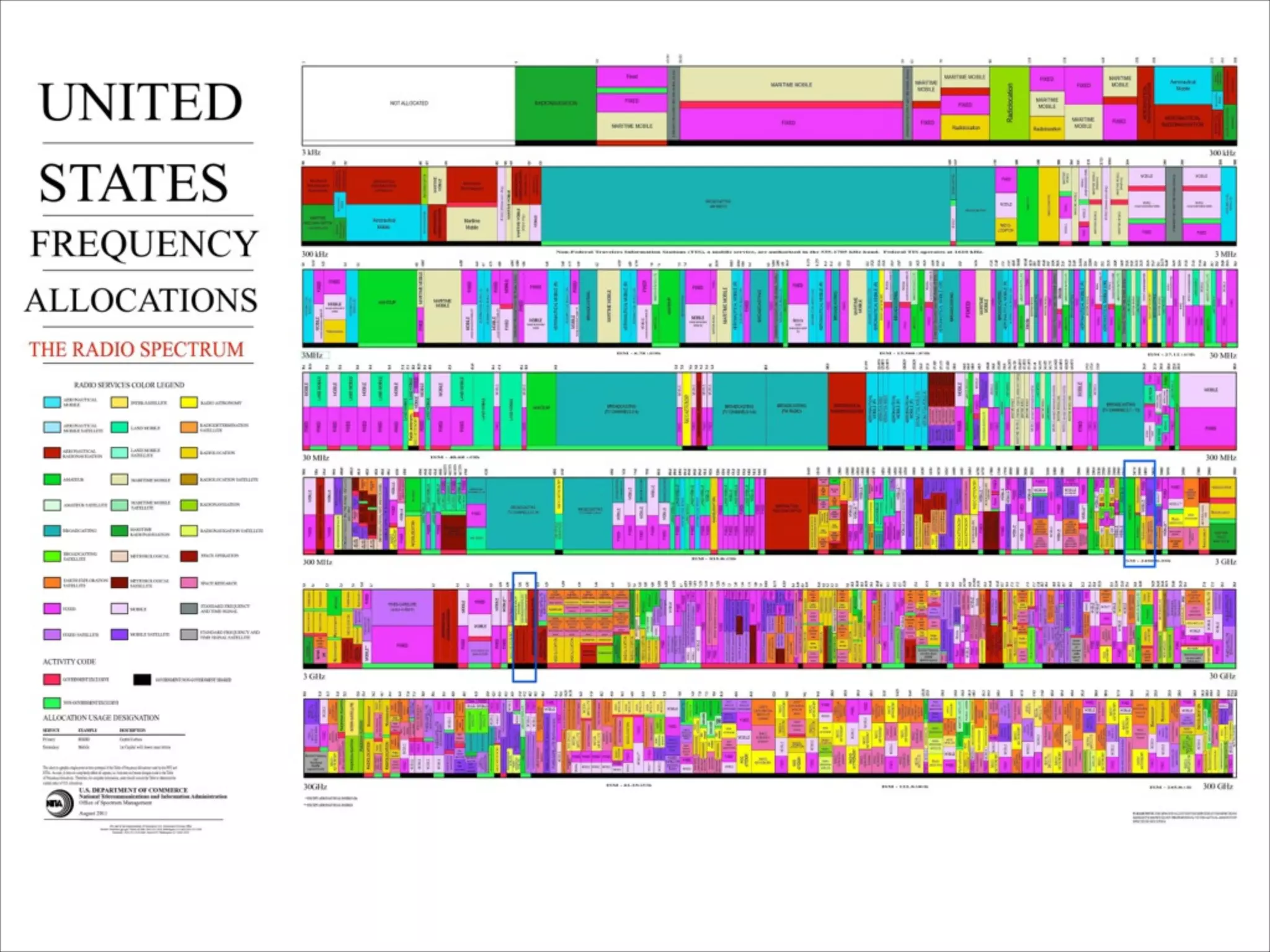
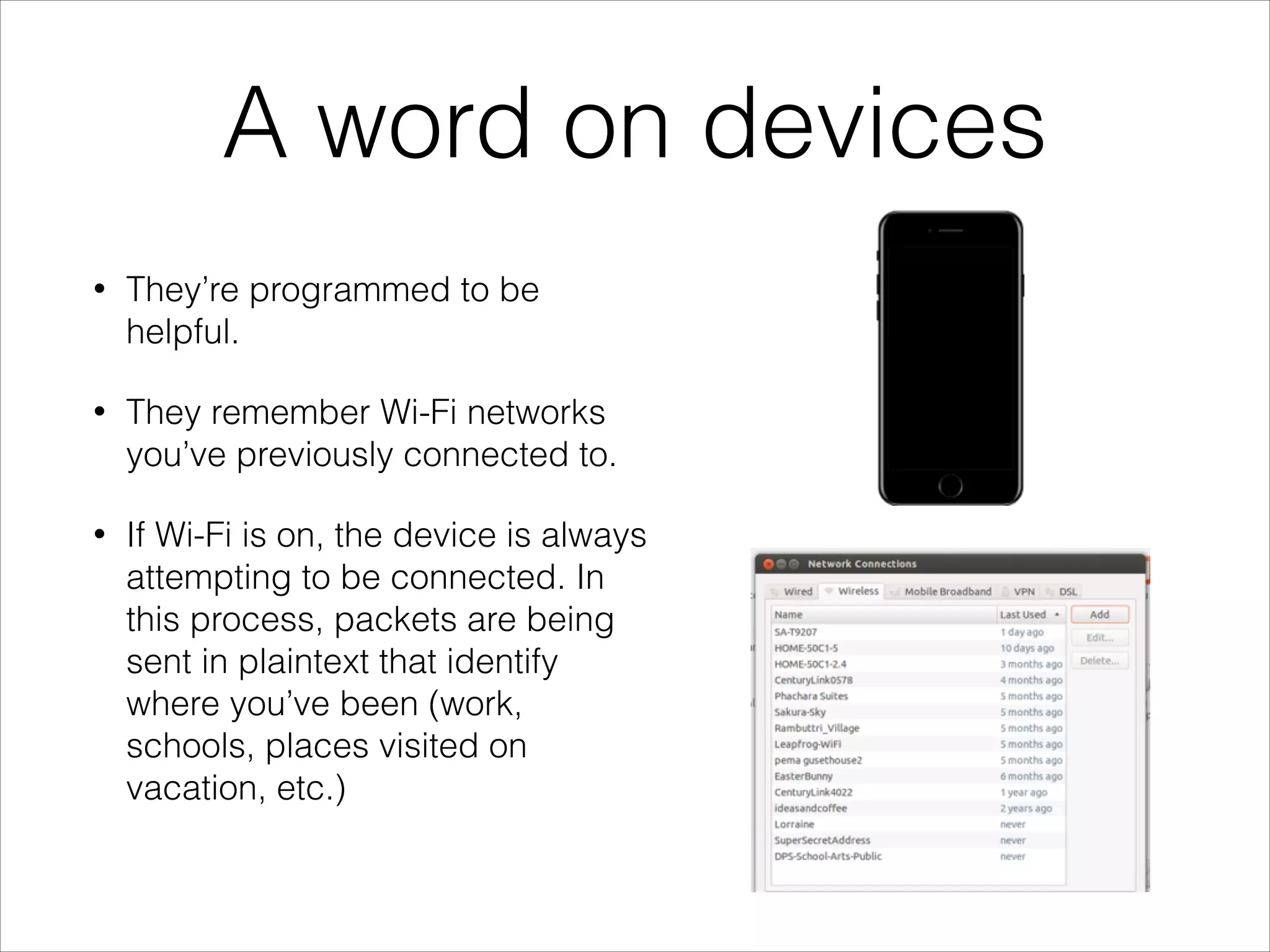
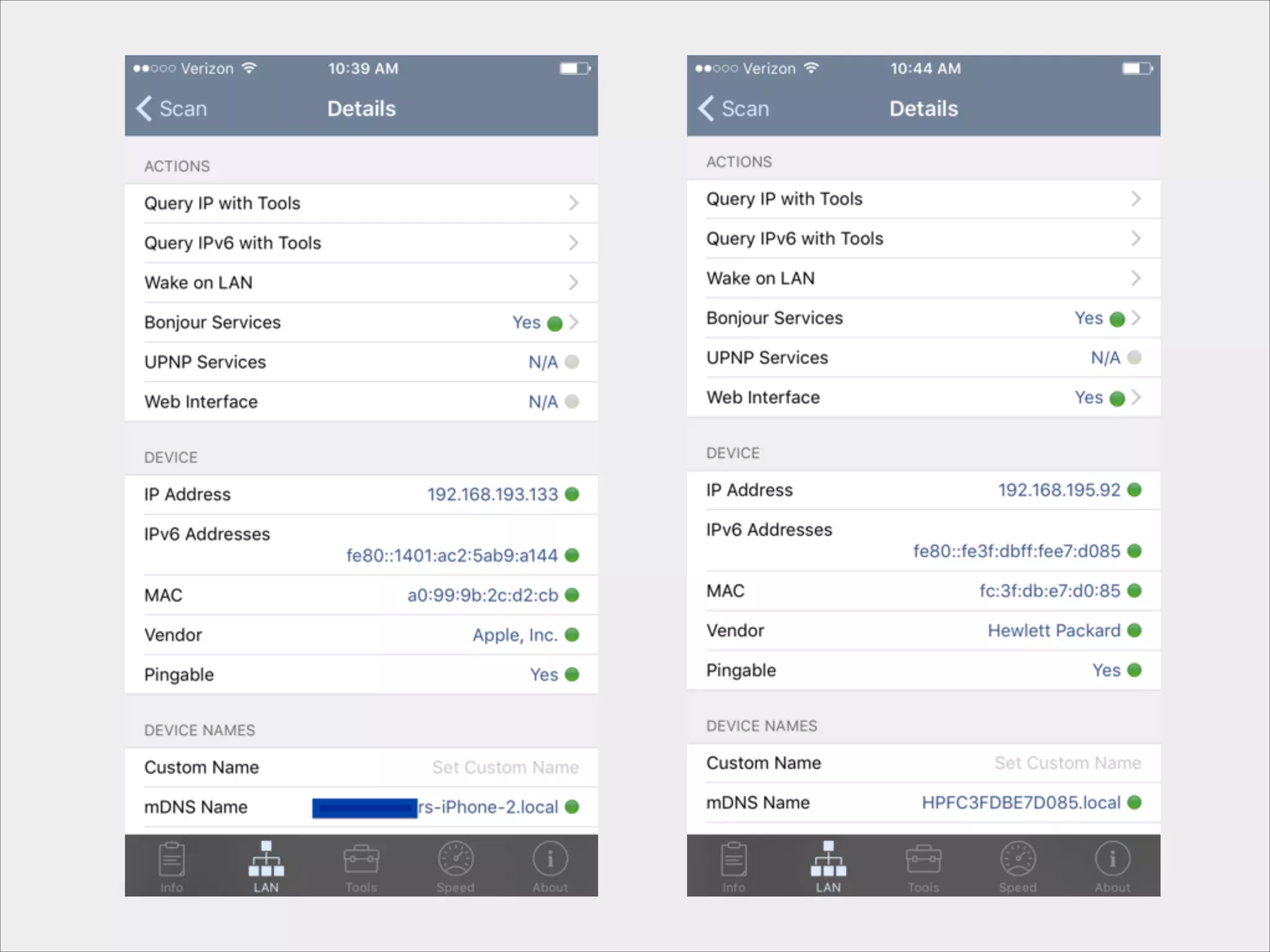
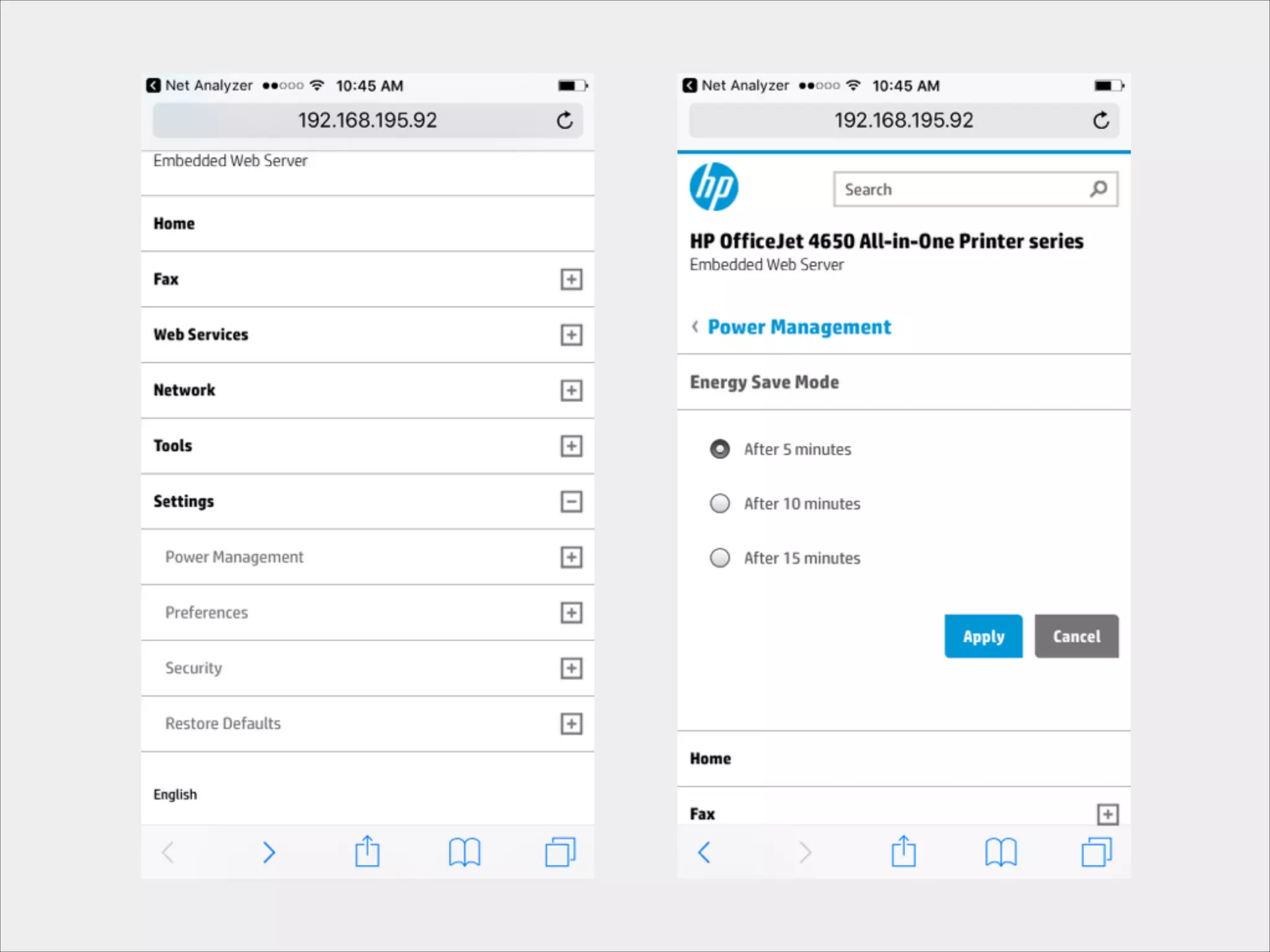
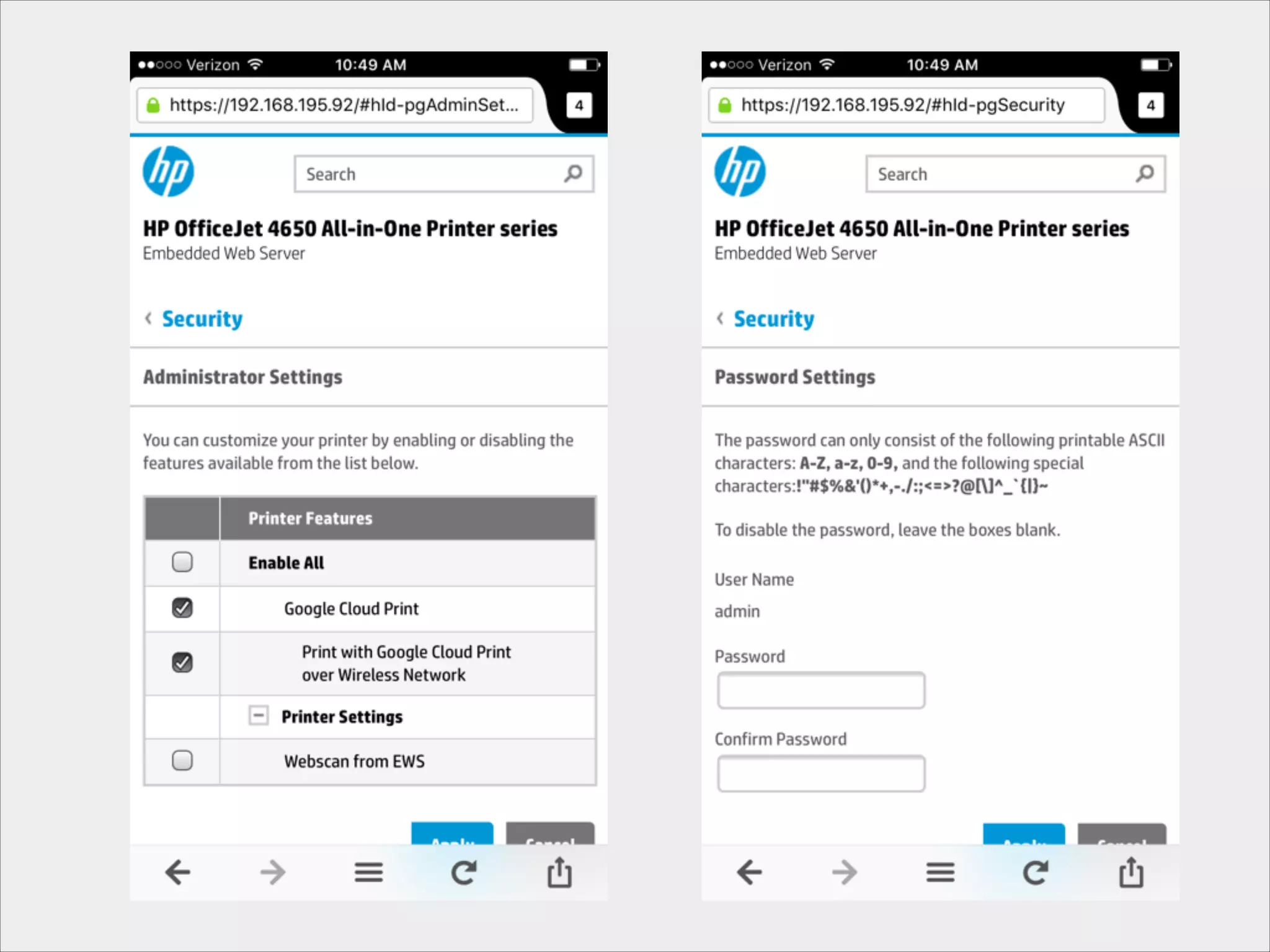
This document provides an introduction to Wi-Fi networking concepts including:
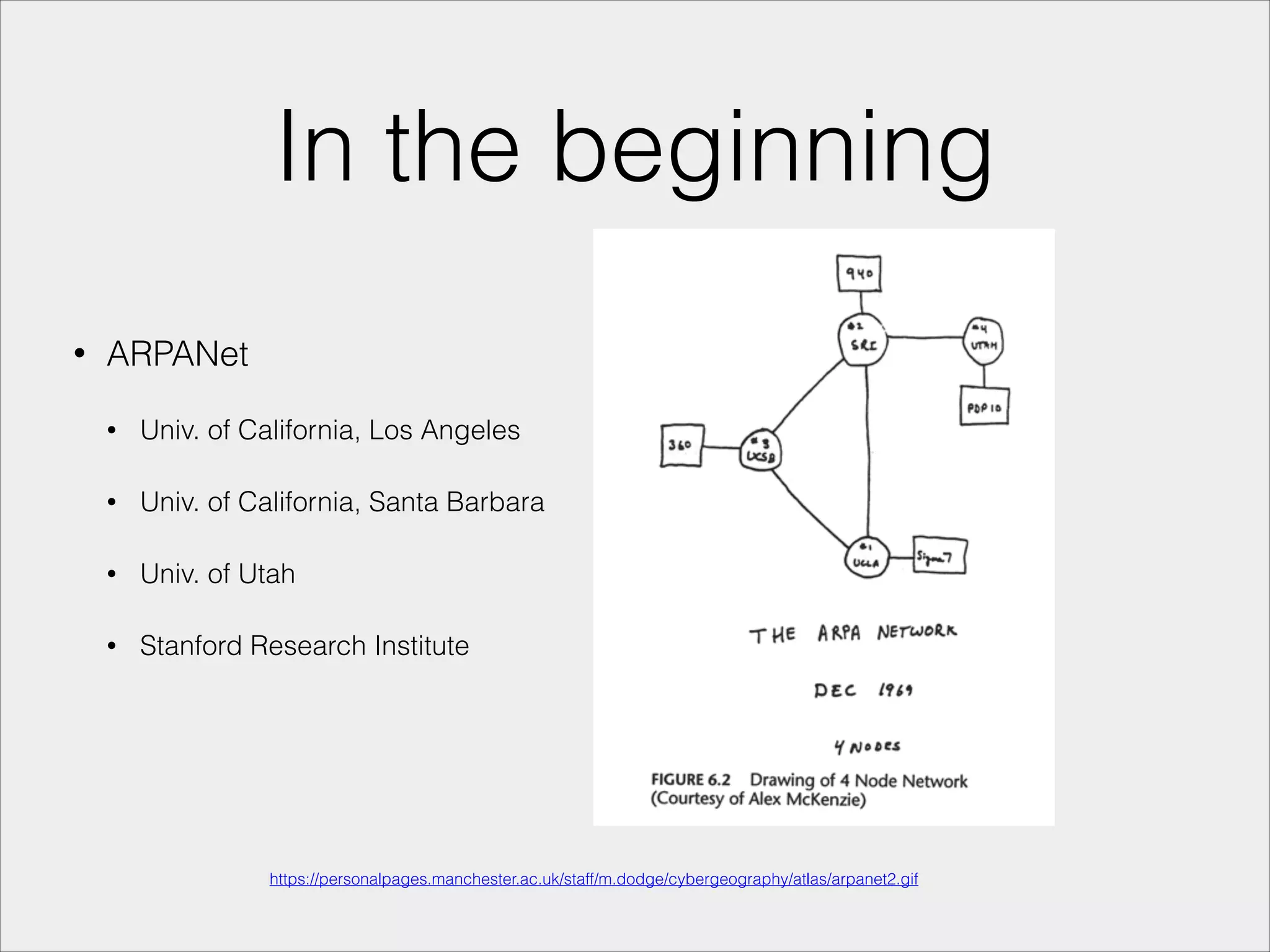
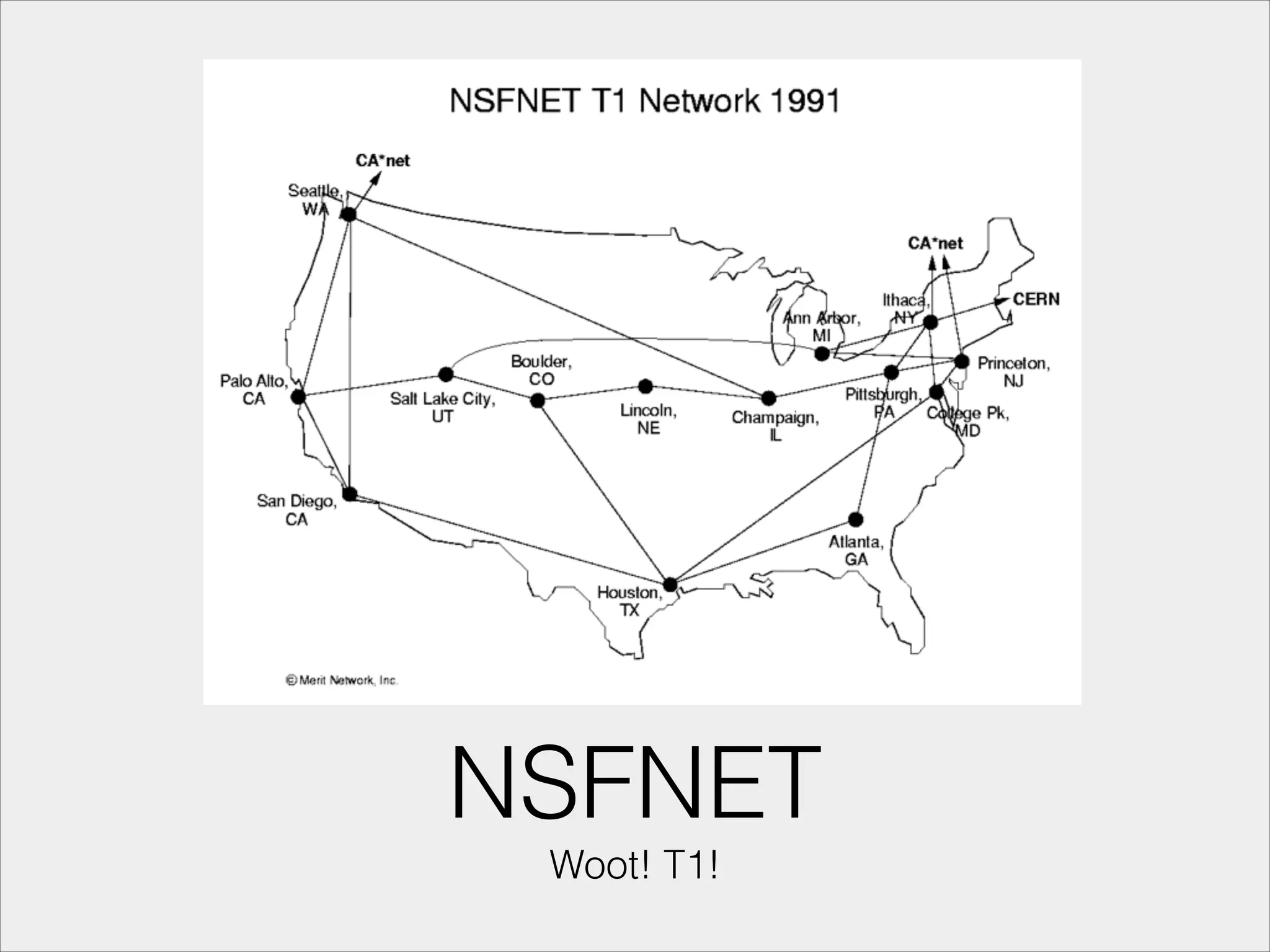
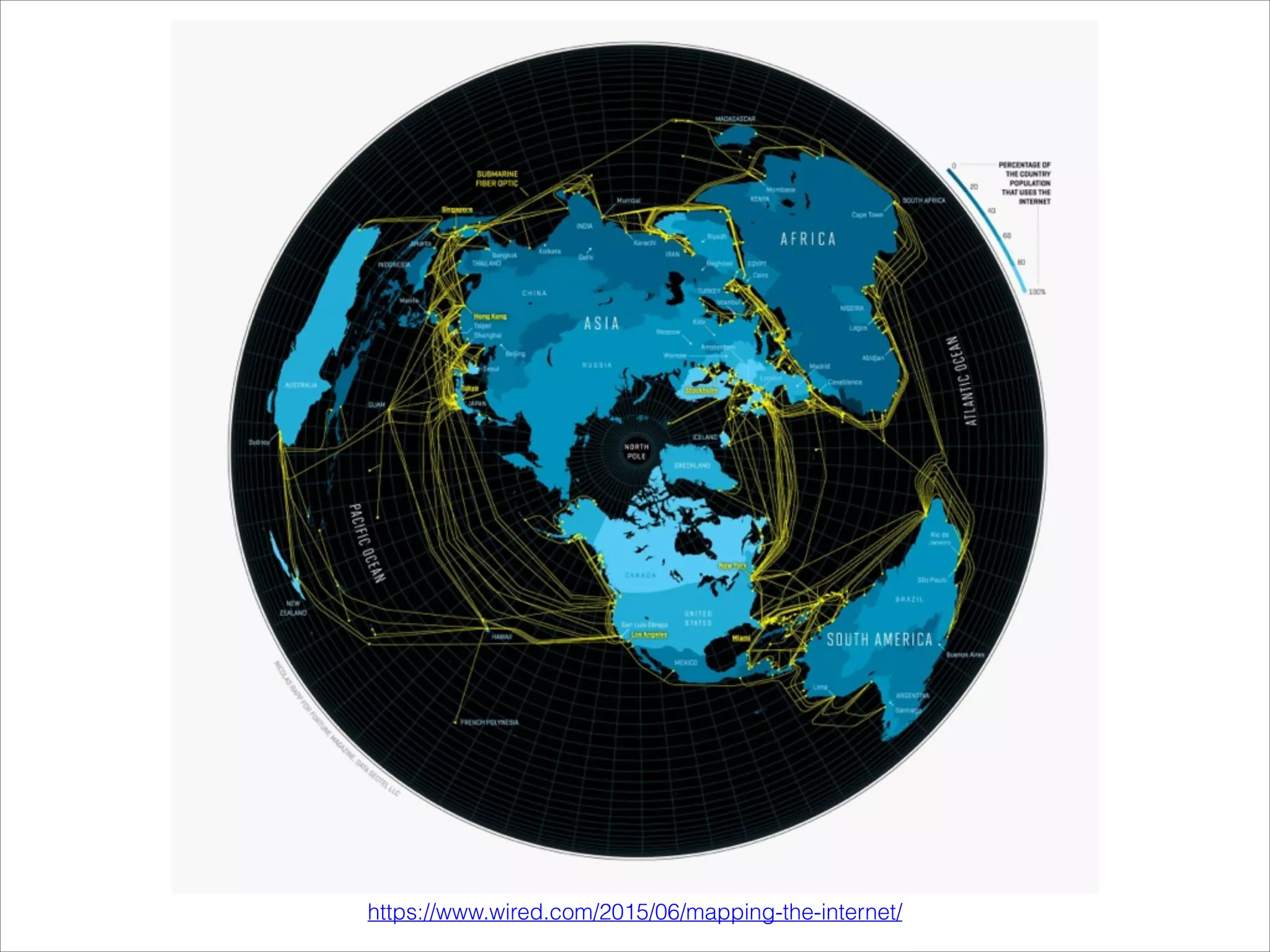
- A brief history of internet development leading to Wi-Fi technology.
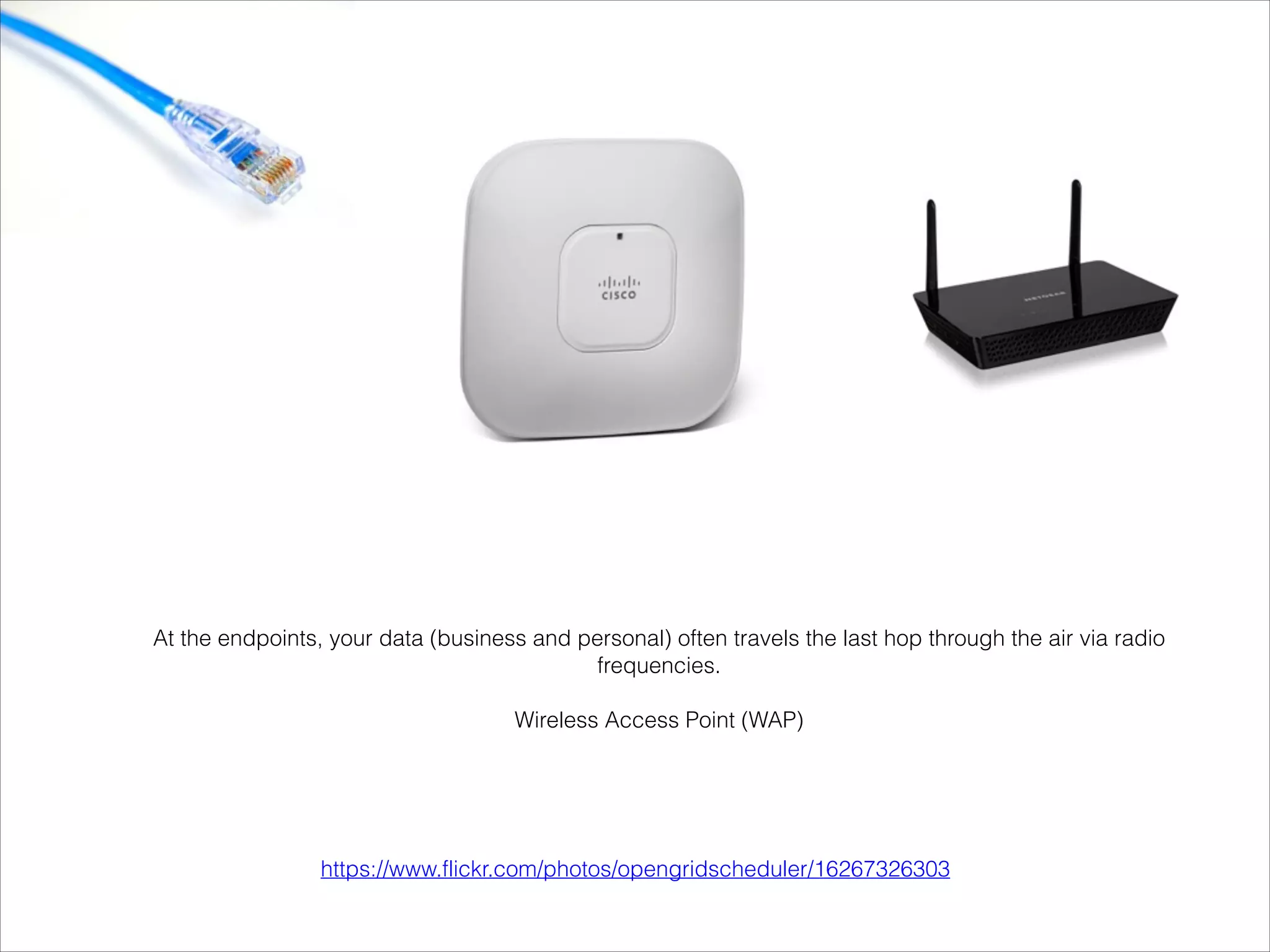
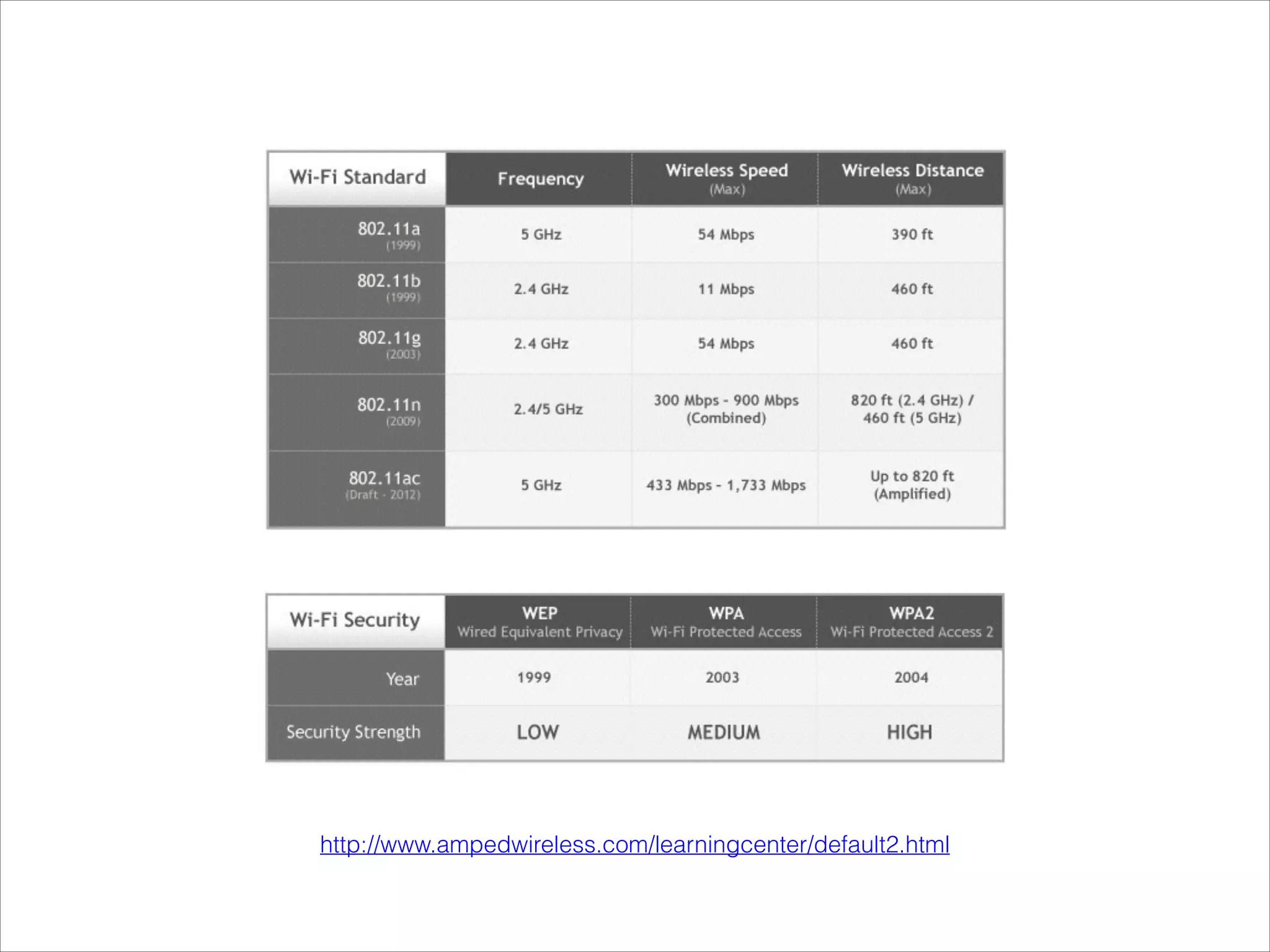
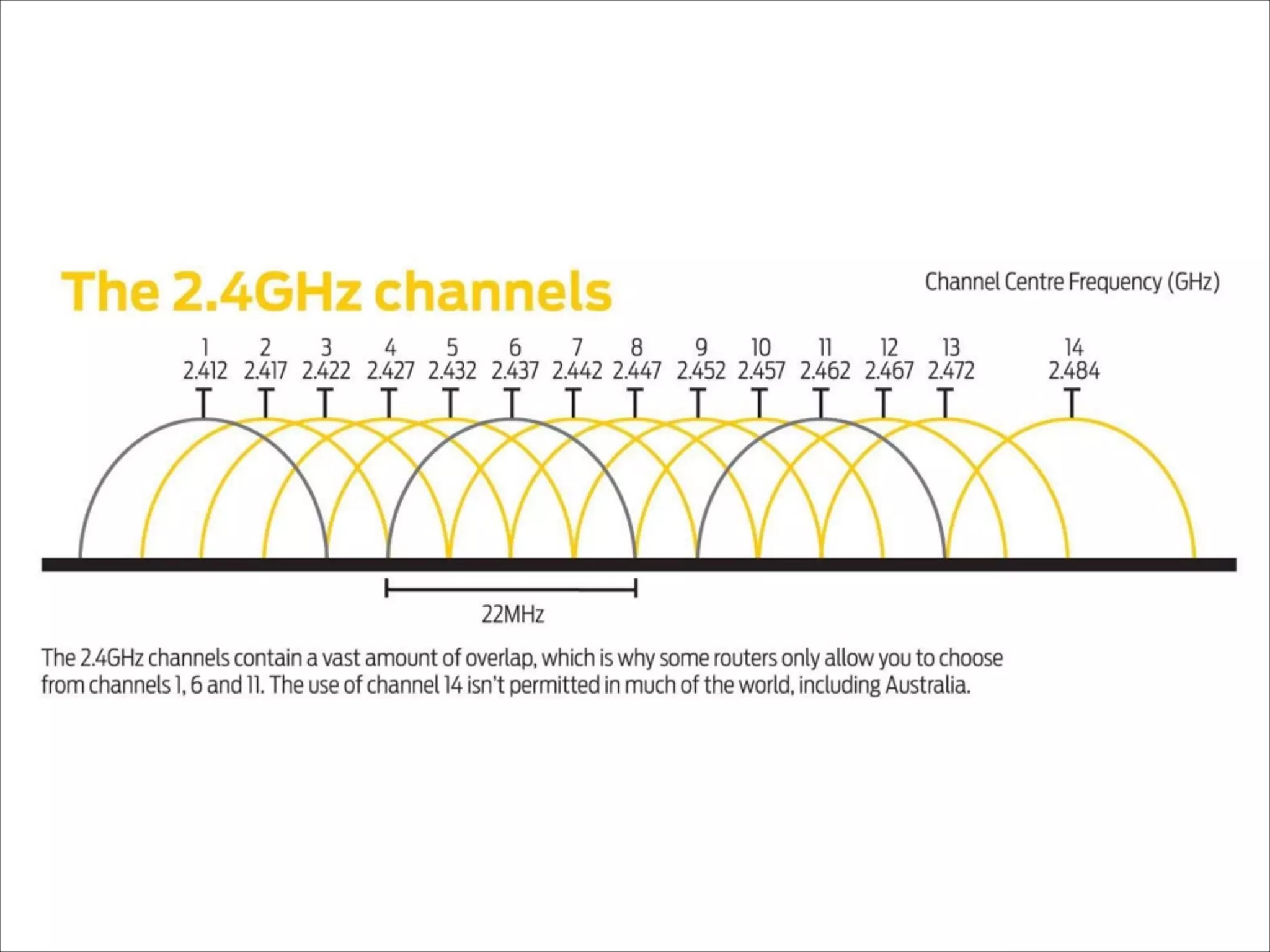
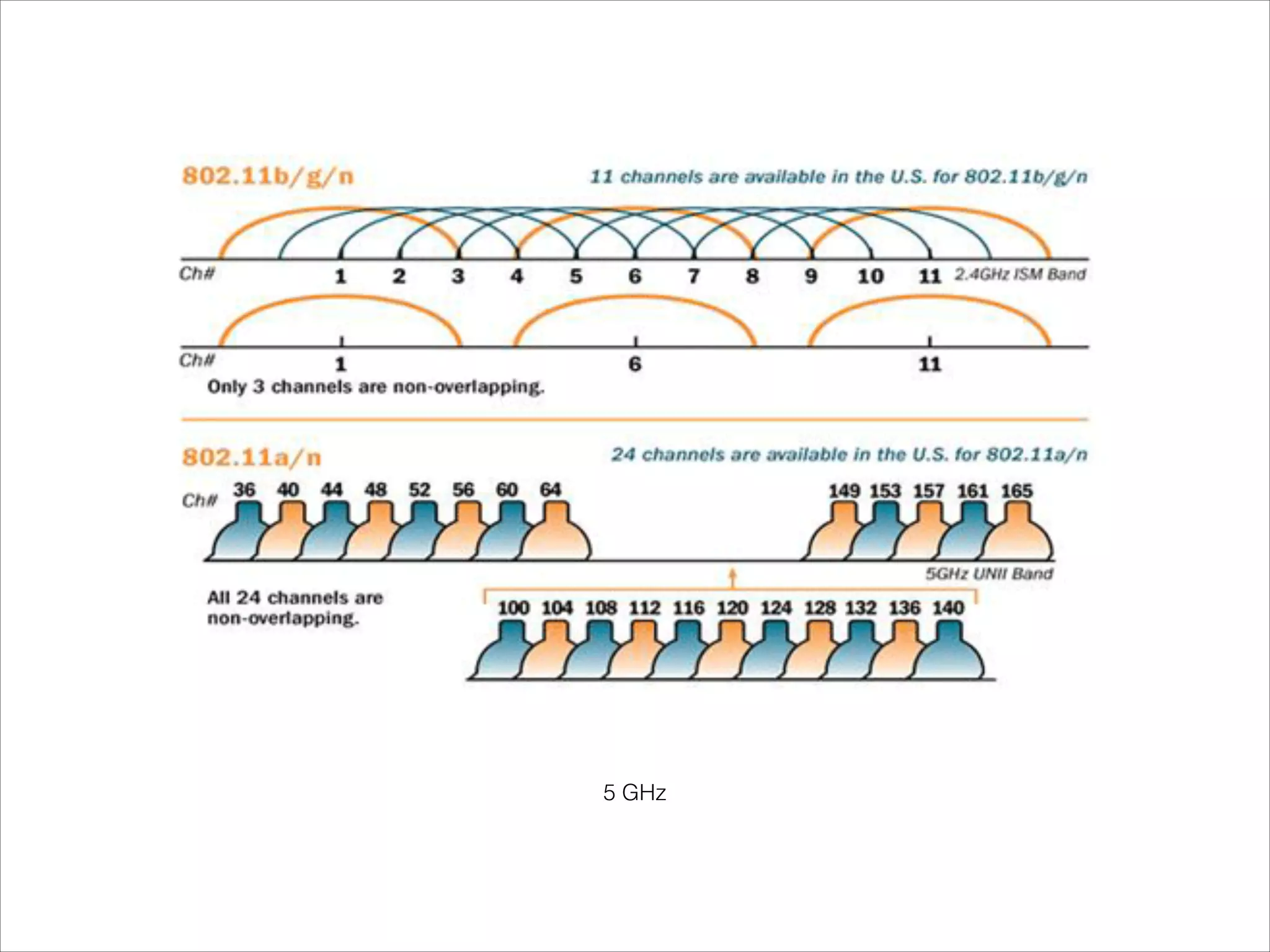
- Explanations of Wi-Fi spectrum bands and wireless networking standards.
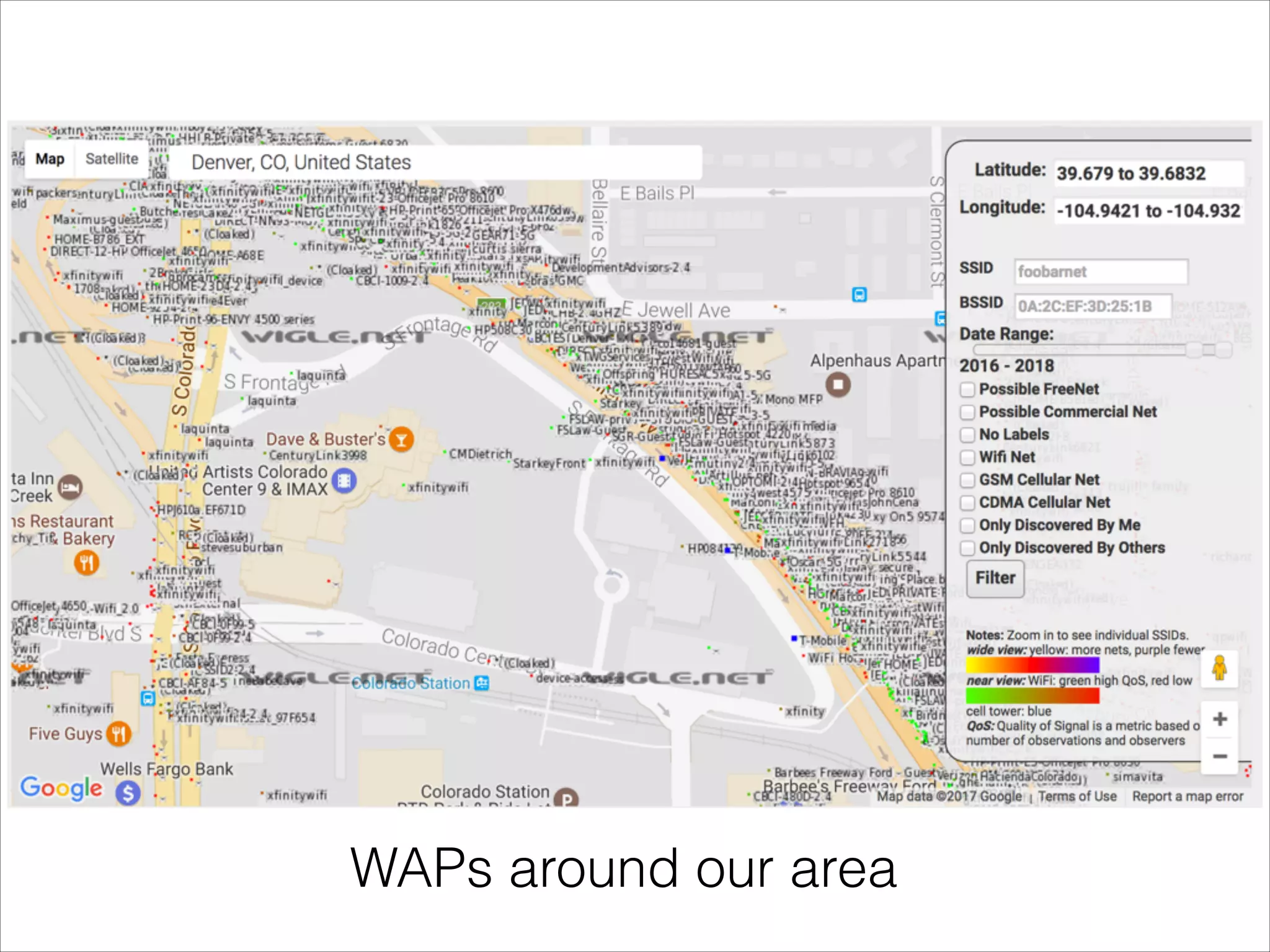
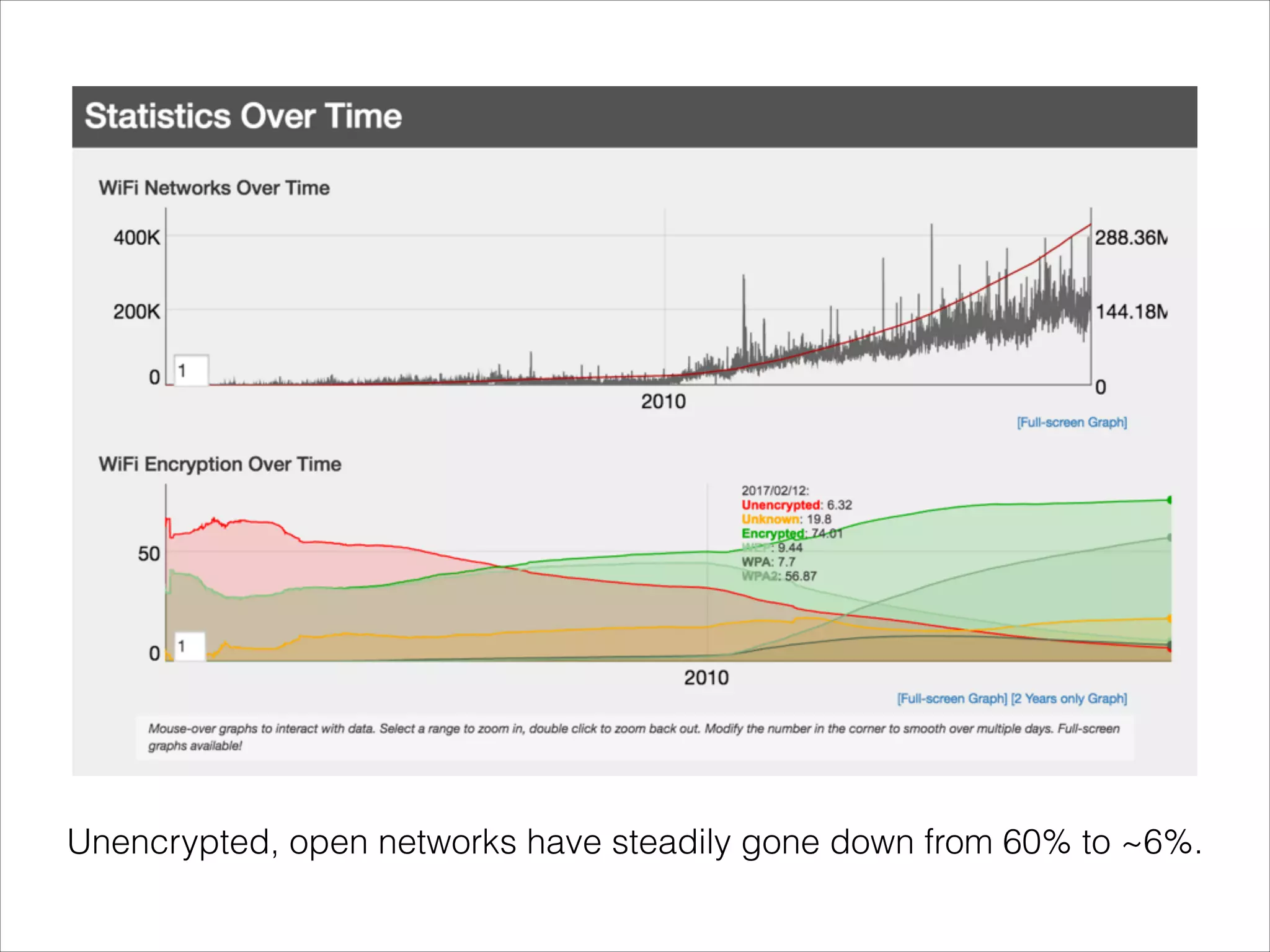
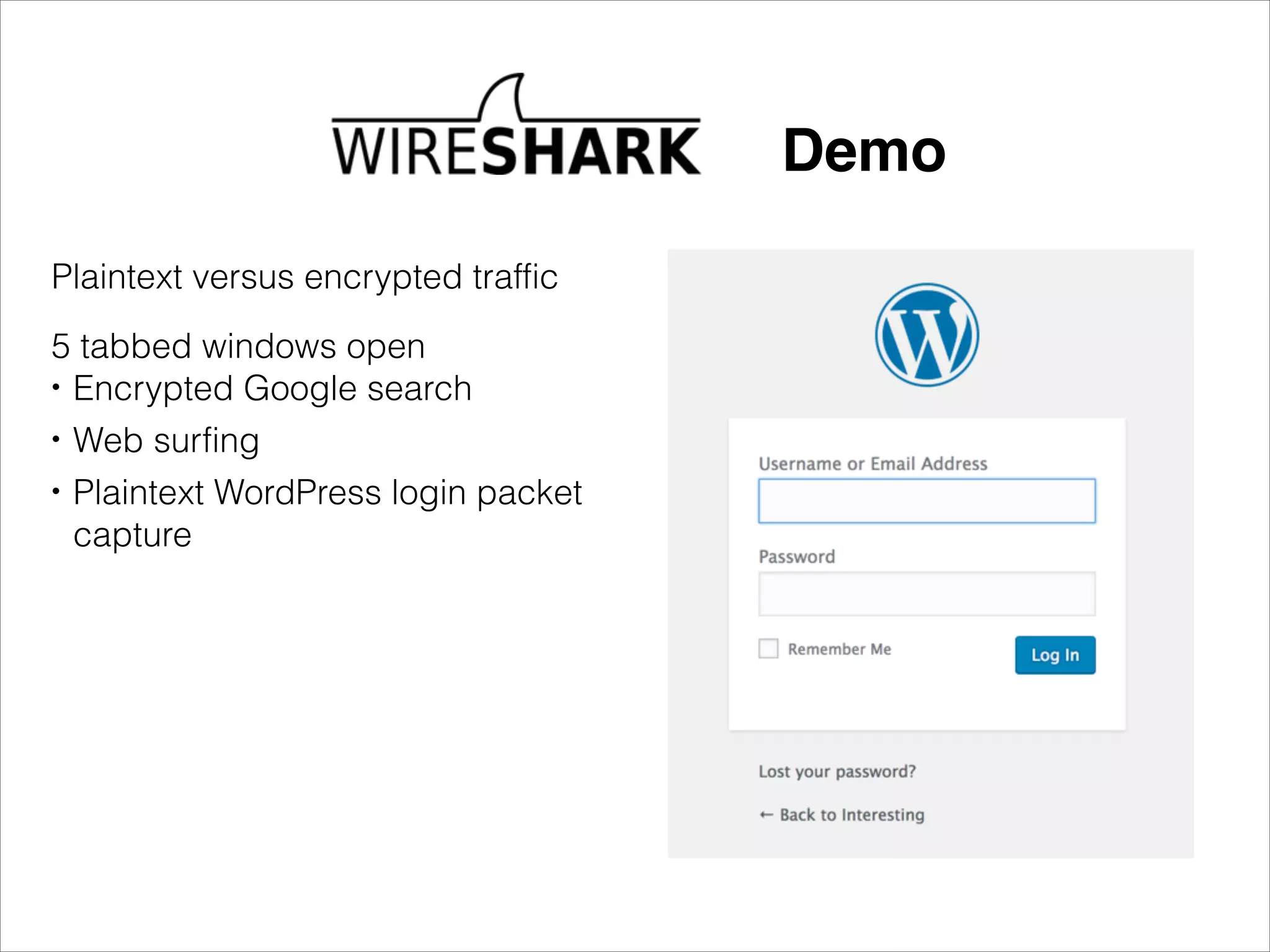
- Security risks associated with open and unencrypted Wi-Fi networks.
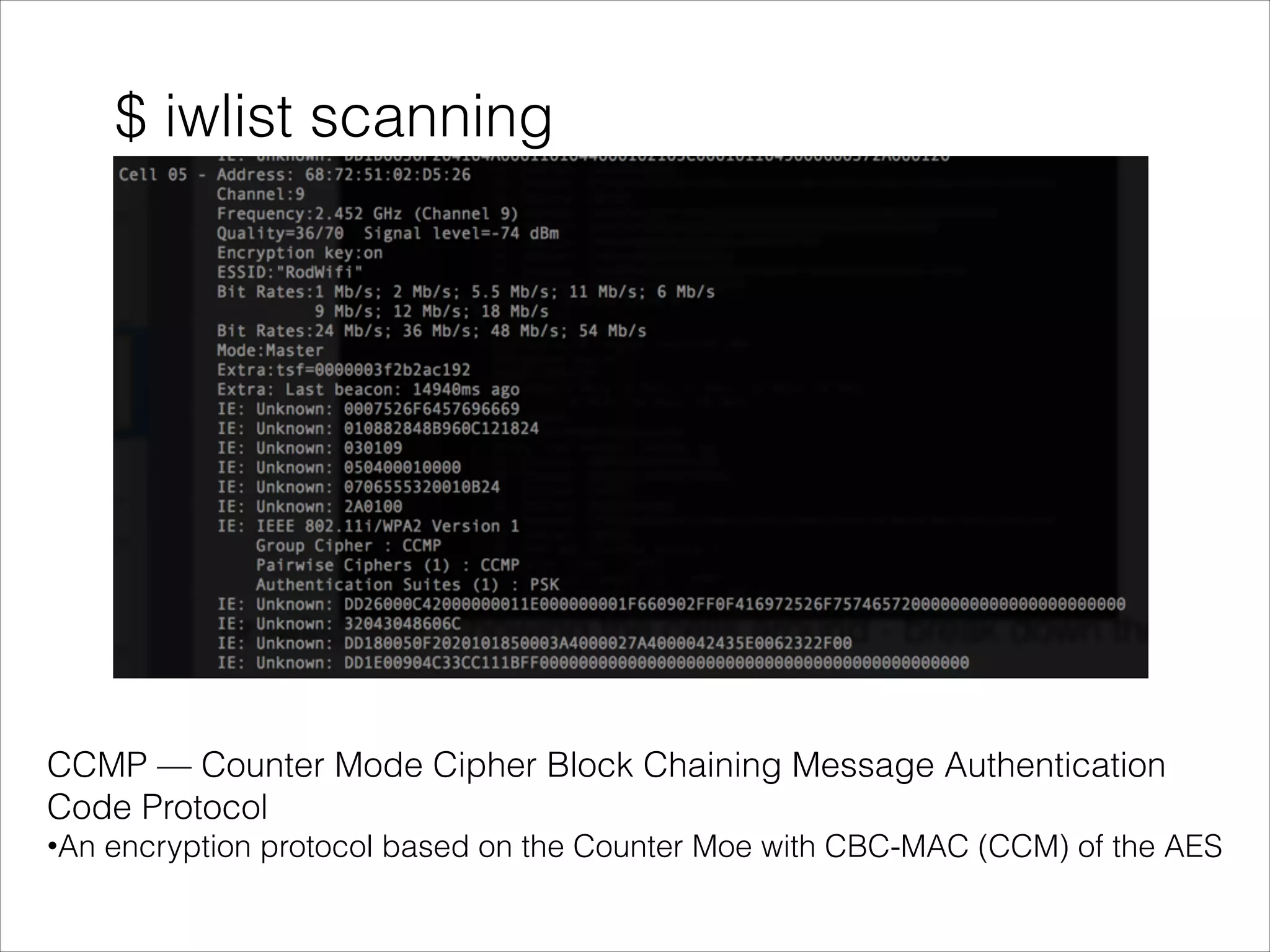
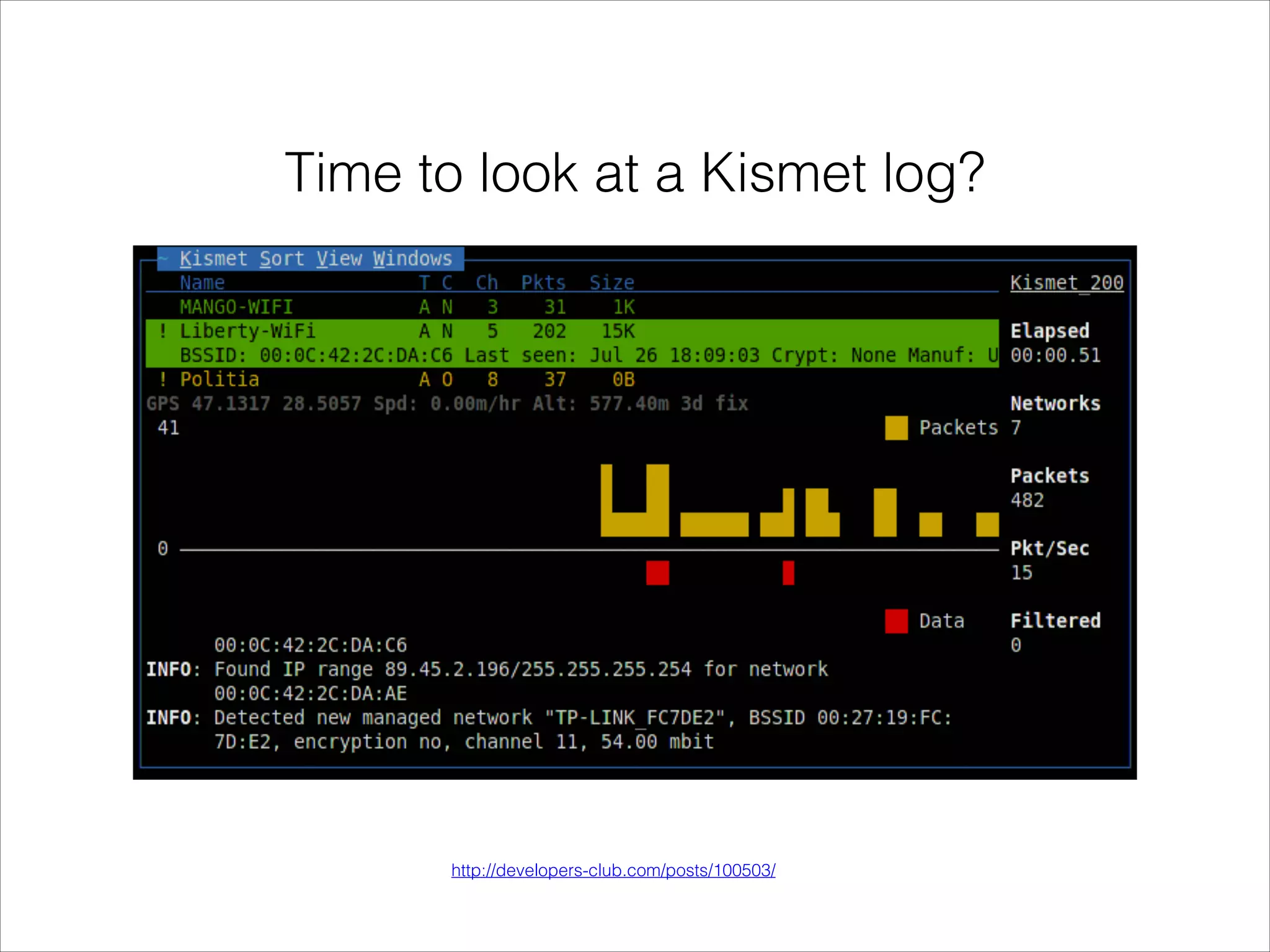
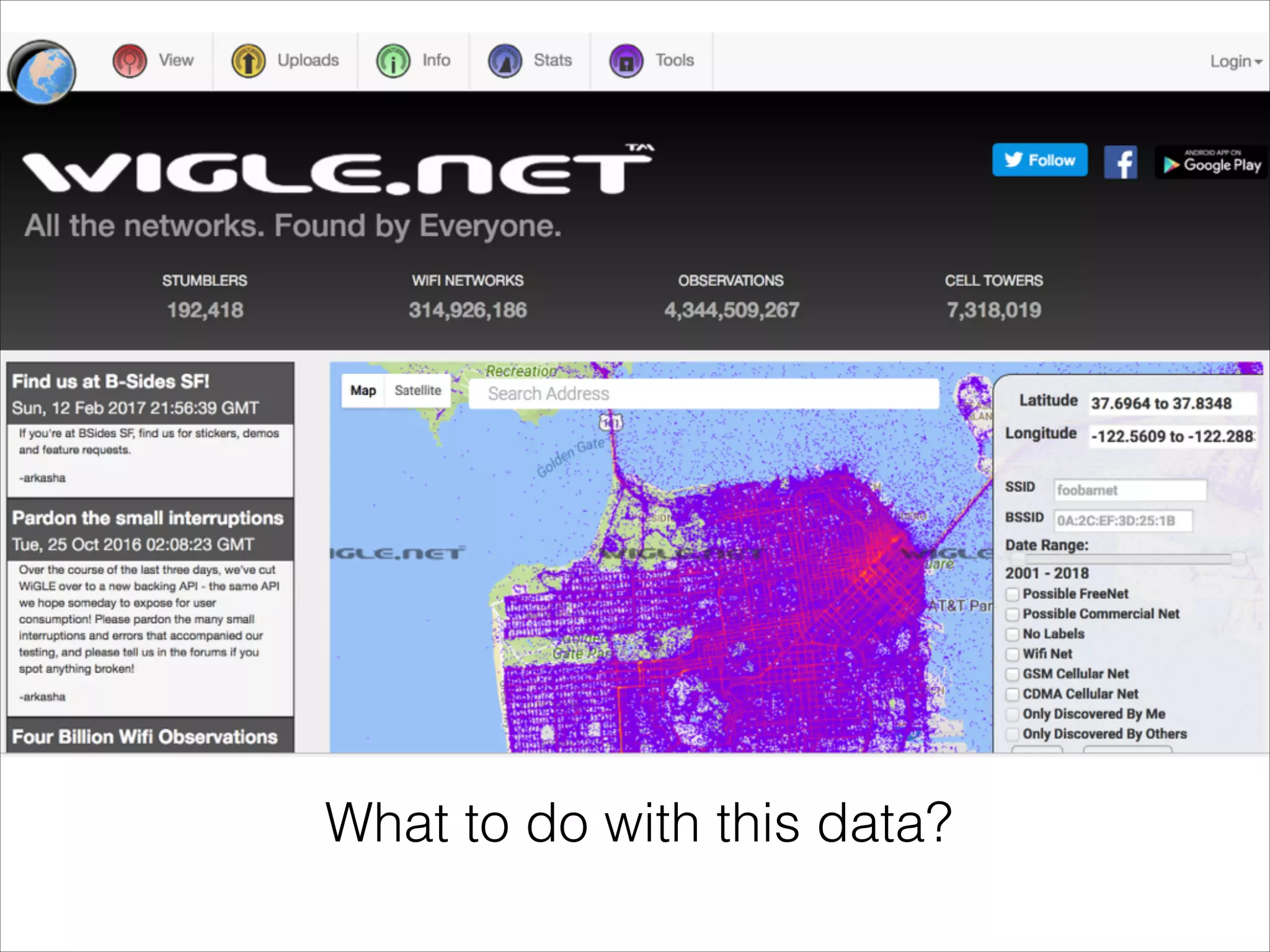
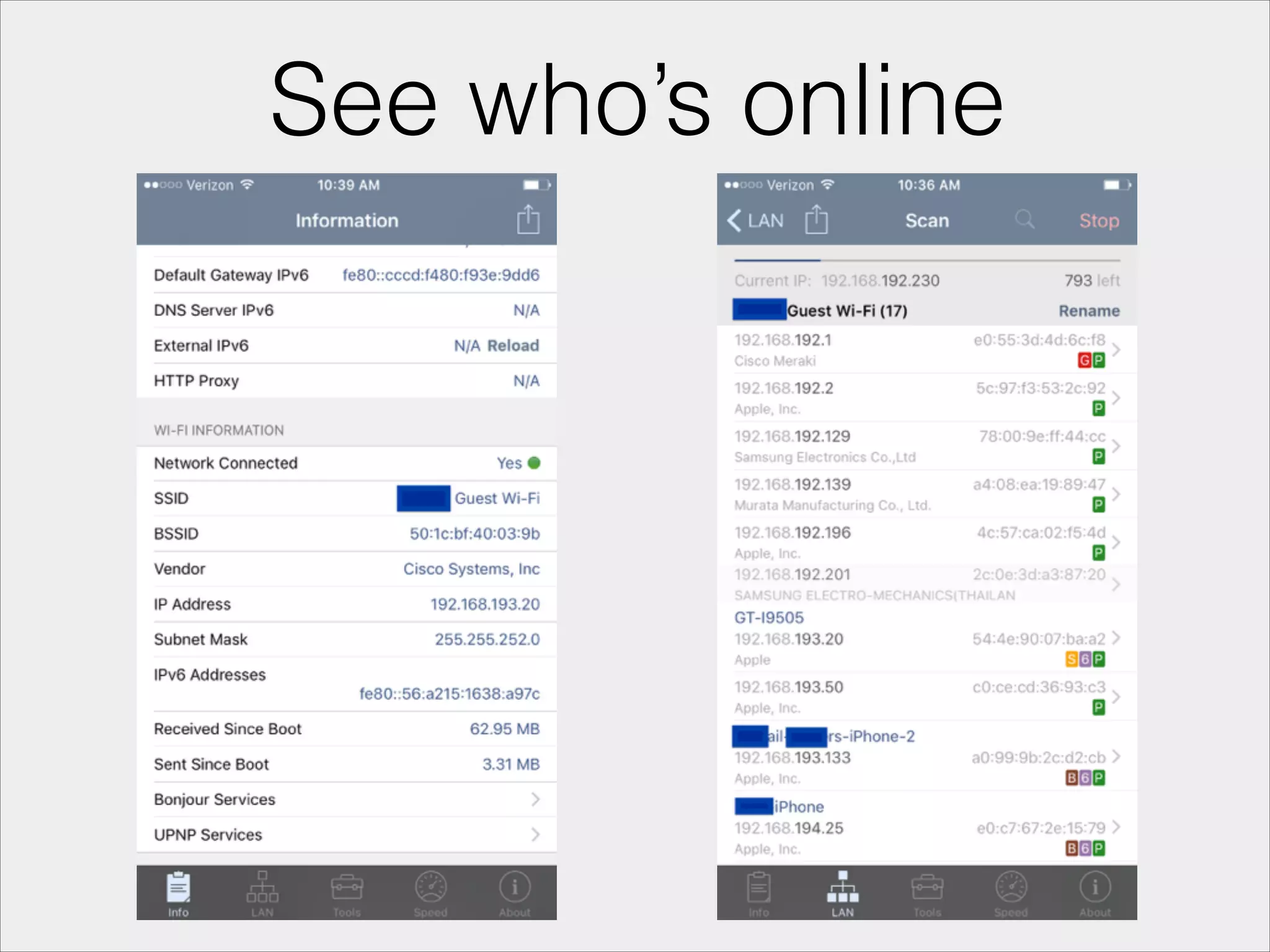
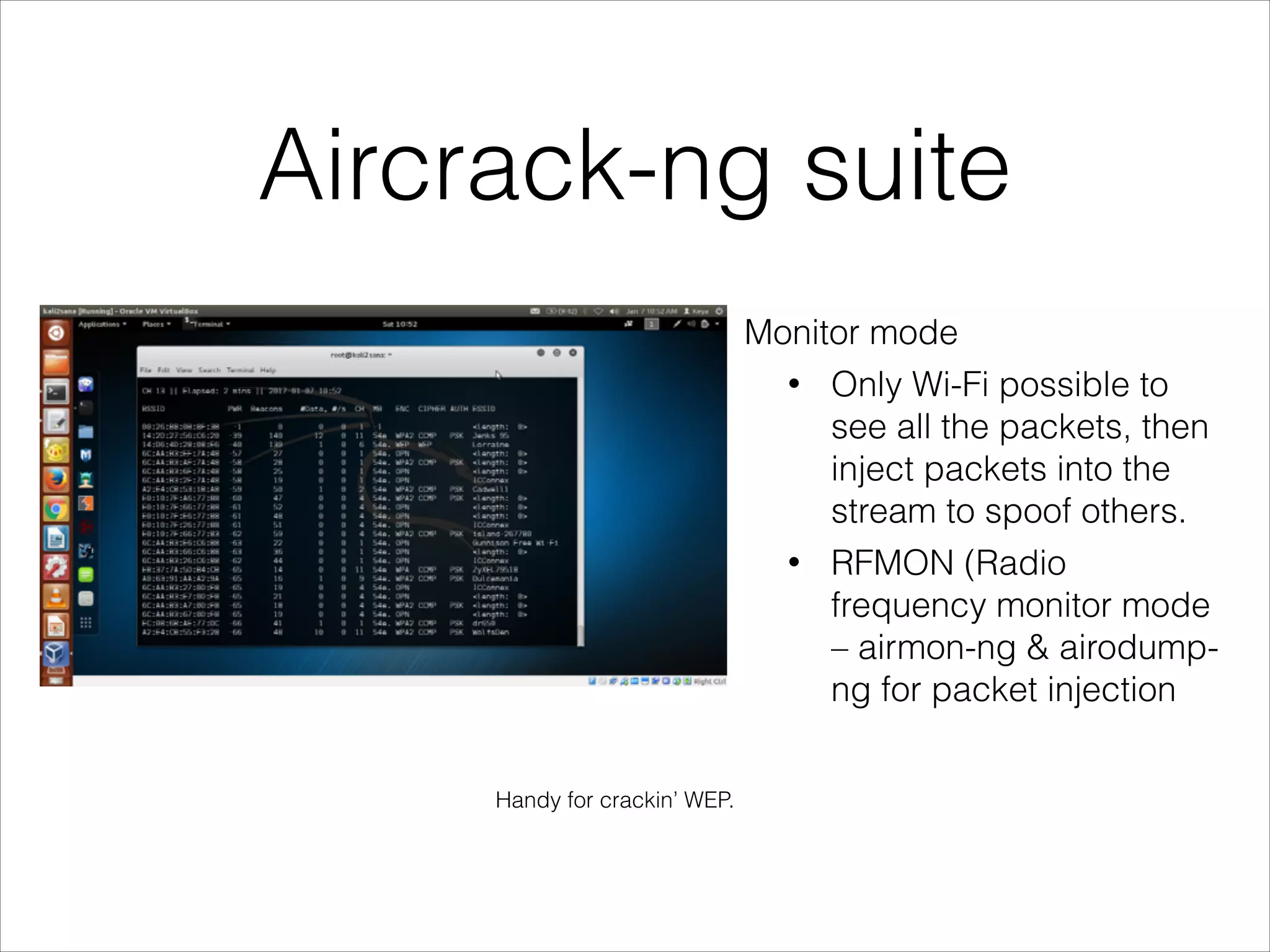
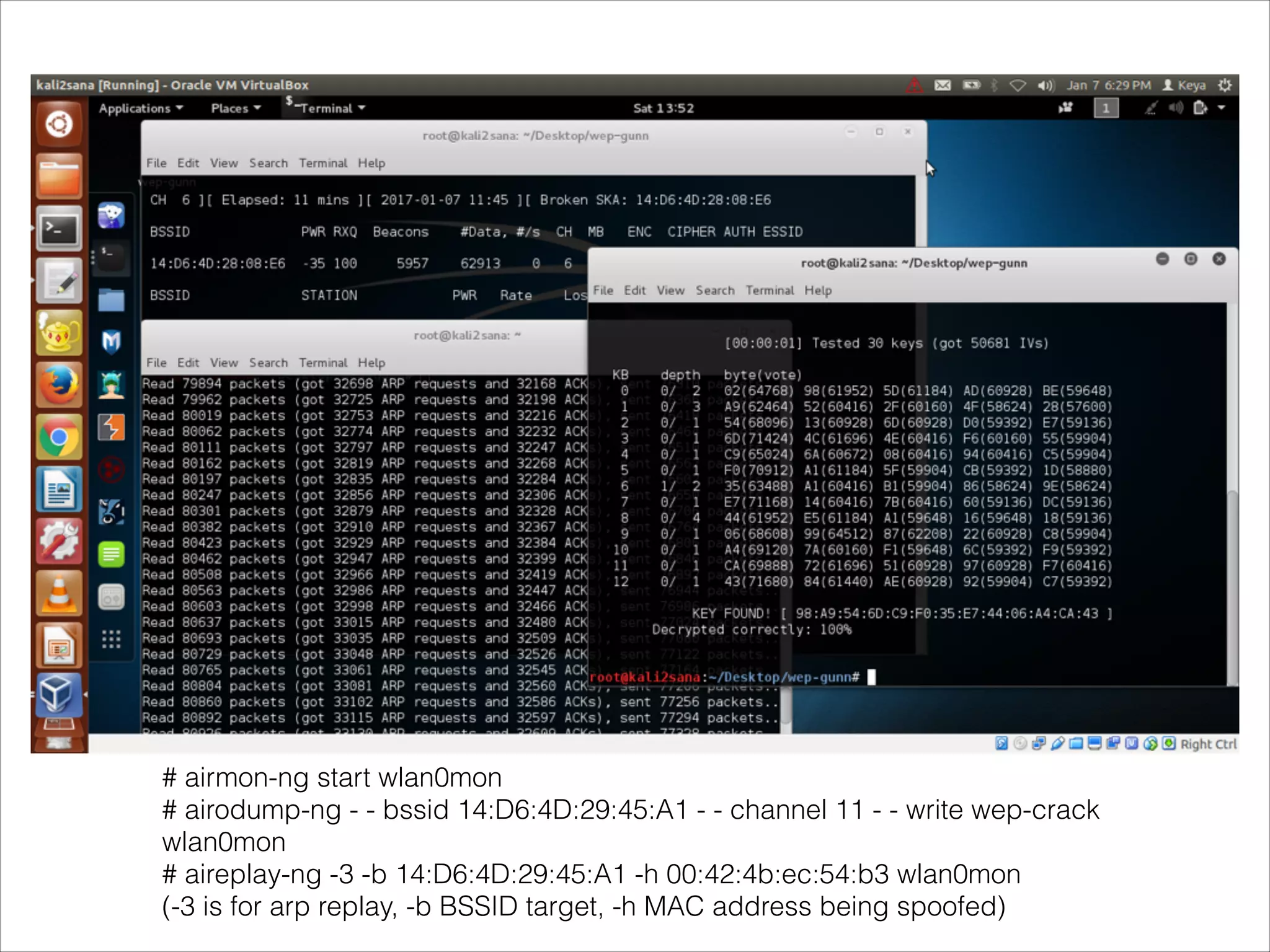
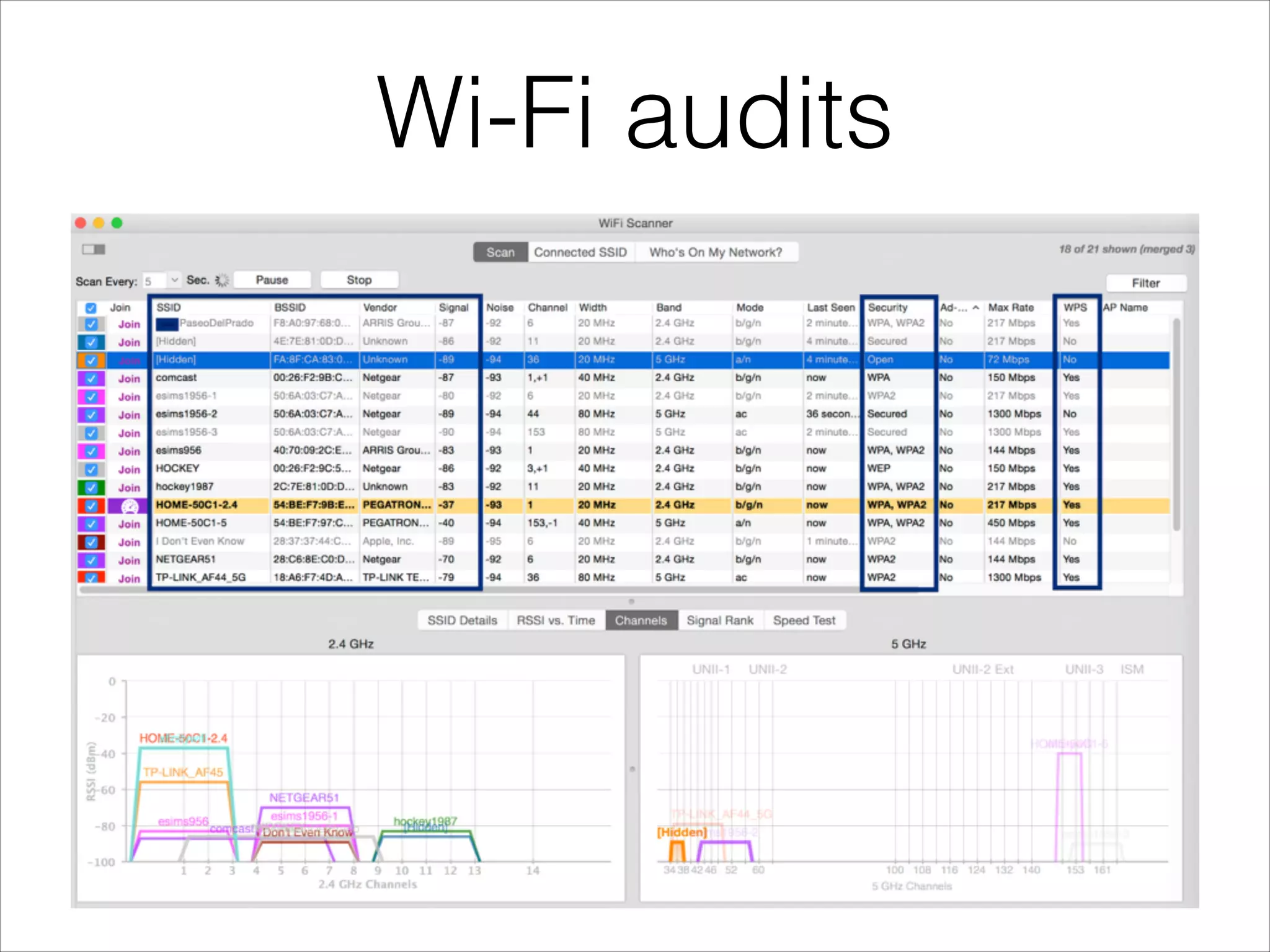
- Tools that can be used to analyze wireless network traffic and identify vulnerabilities.
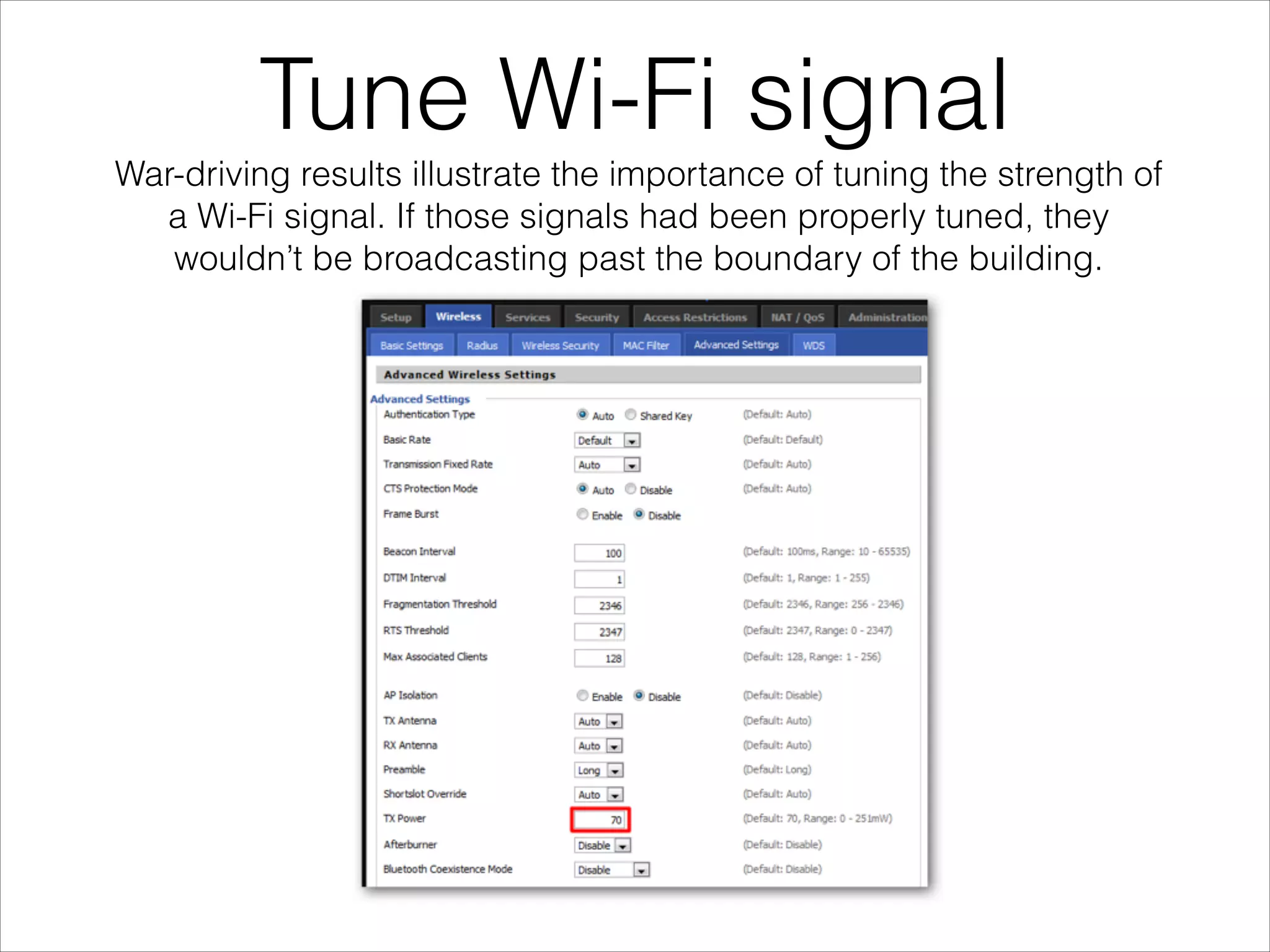
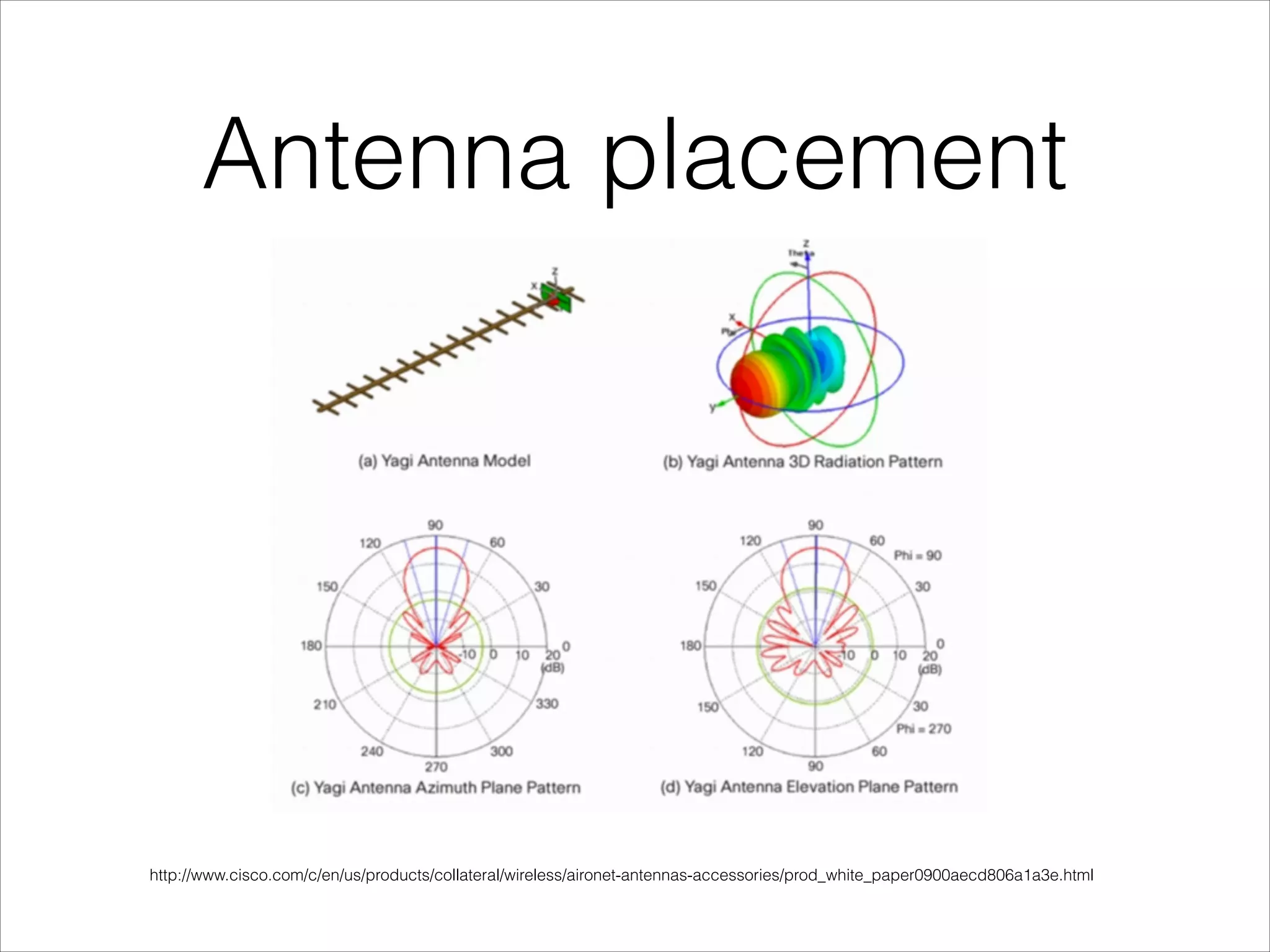
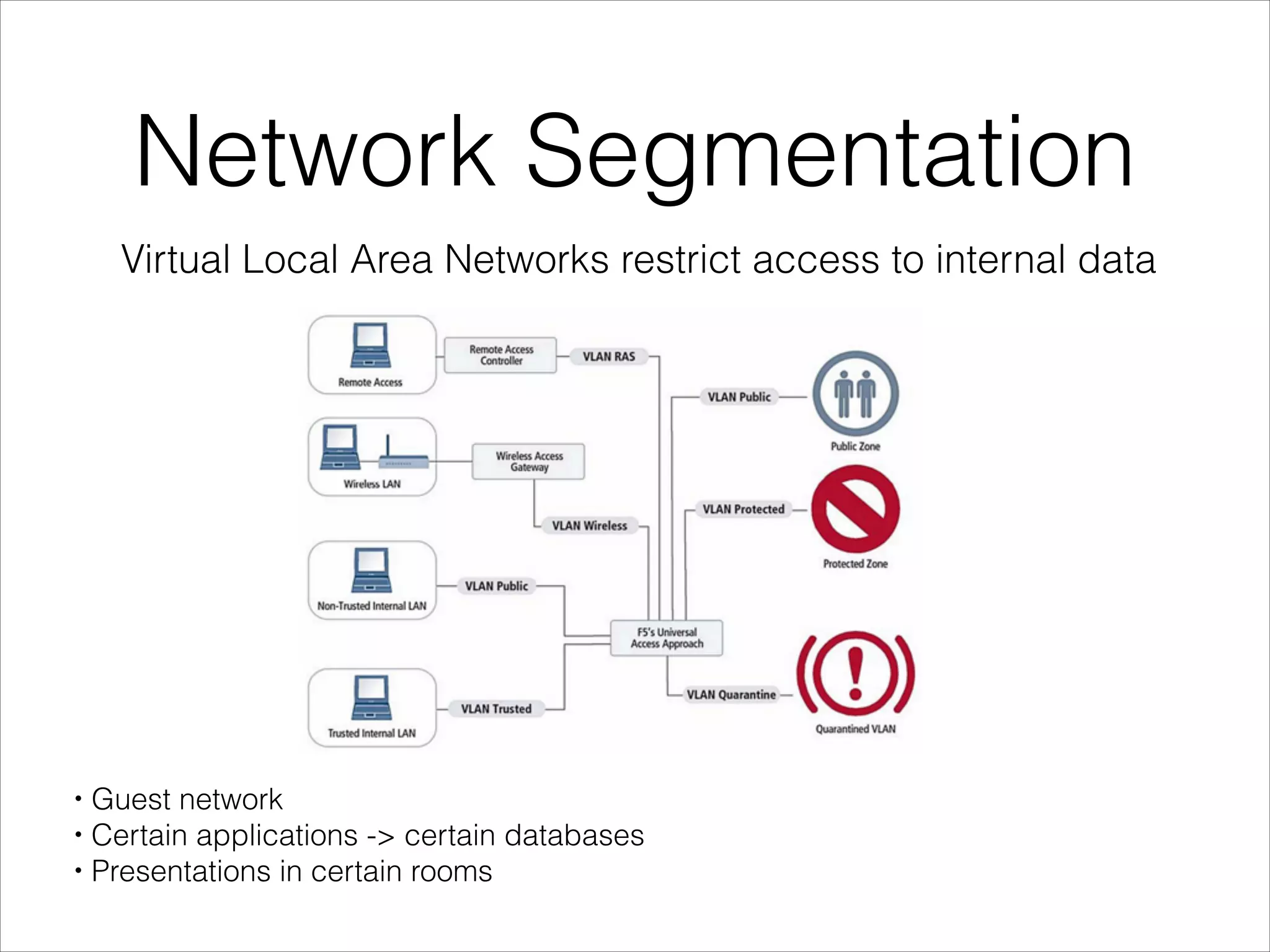
- Best practices for securing wireless networks through encryption, segmentation, and other methods.