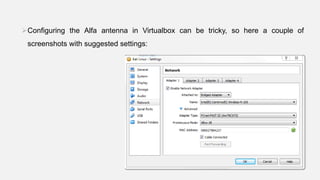
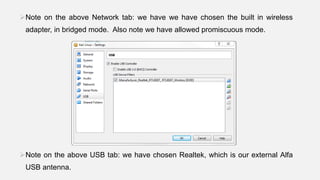
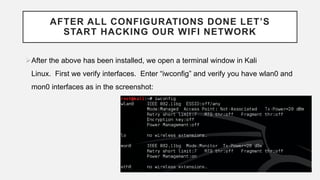
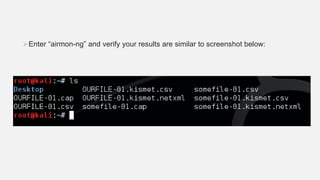
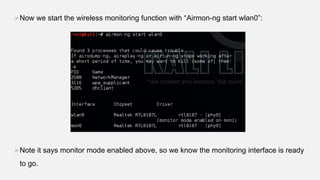
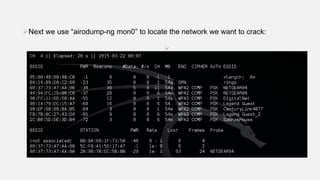
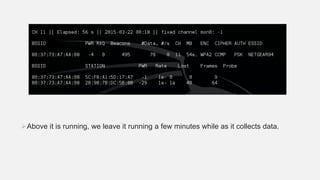
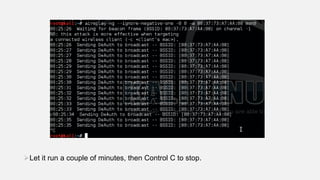
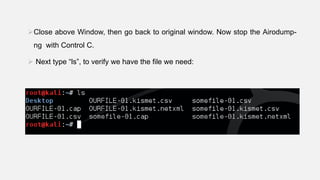
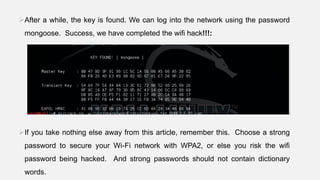
This document provides instructions for hacking WiFi passwords using Kali Linux. It describes downloading and configuring Kali Linux in a virtual machine. An external USB antenna is used to monitor WiFi networks. The airodump-ng tool is used to detect networks and capture data, which is then cracked using a dictionary attack with aircrack-ng. If the network is not busy, deauthentication packets can be sent to force password transmission. Following these steps, the document claims the password for a sample network was successfully cracked.