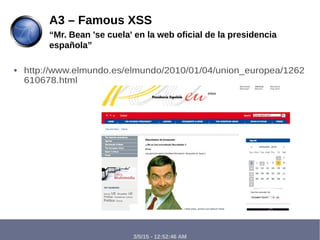
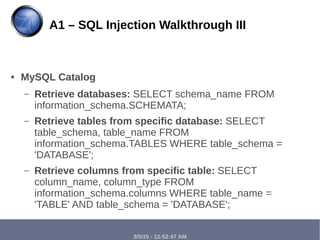
The document discusses the importance of web security for developers, highlighting threats such as spam, phishing, and ransomware. It elaborates on web vulnerabilities, specifically focusing on Cross-Site Scripting (XSS) and SQL injection, including their types, attack methods, and common mitigation strategies. The presentation emphasizes the need for secure coding practices and awareness of user input vulnerabilities.