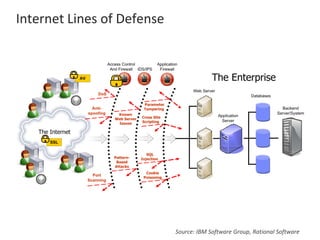
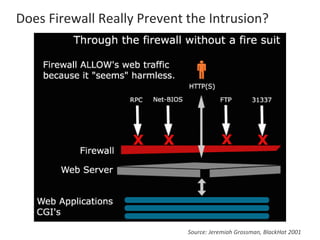
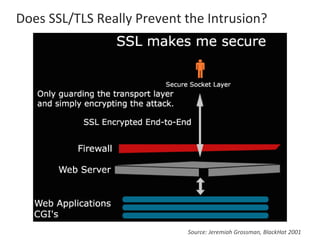
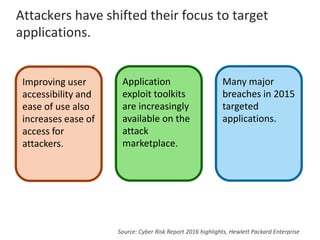
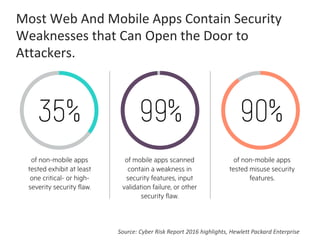
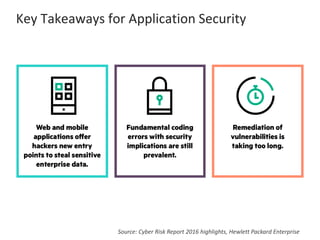
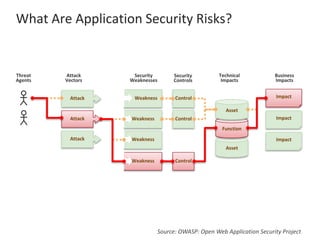
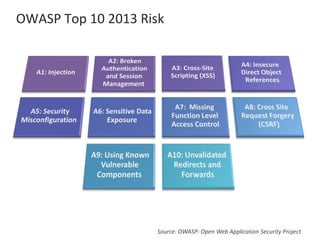
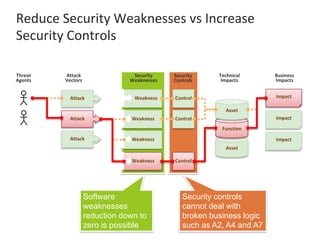
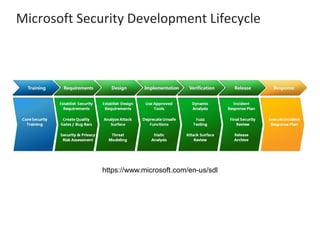
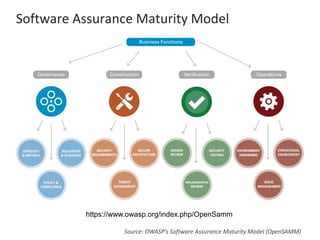
The presentation by Narudom Roongsiriwong at the ASEAN IT Security Conference highlights the shift in attackers' focus towards applications, with increasing availability of exploit toolkits. Major breaches in 2015 targeted applications, revealing security weaknesses in most web and mobile apps. Key takeaways emphasize the importance of implementing proactive application security controls and frameworks, such as the OWASP Top 10 and Microsoft Security Development Lifecycle.