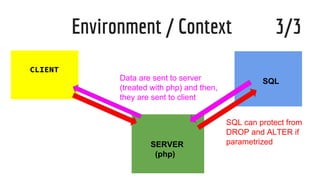
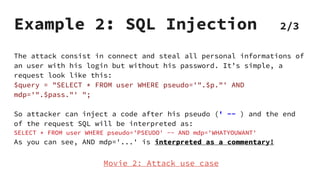
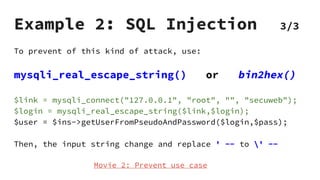
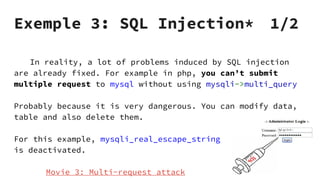
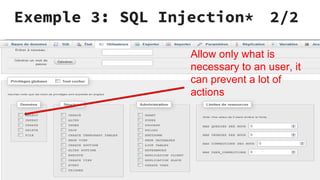
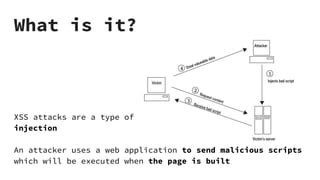
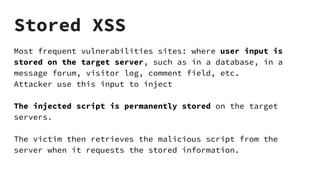
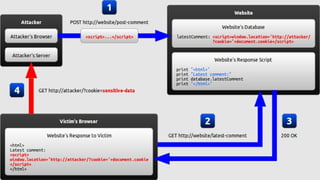
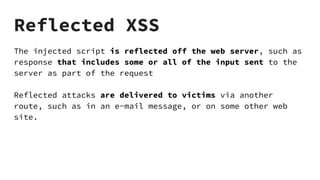
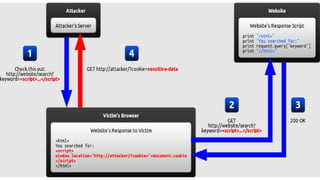
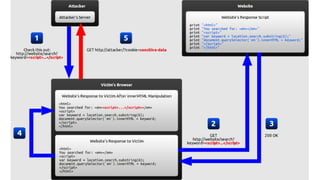
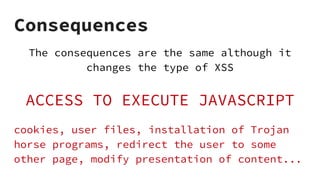
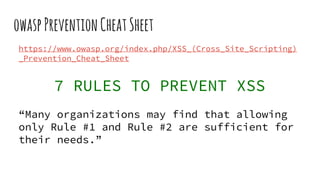
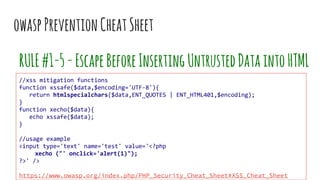
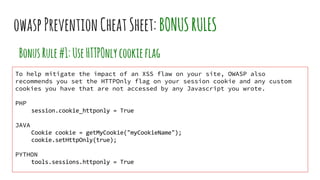
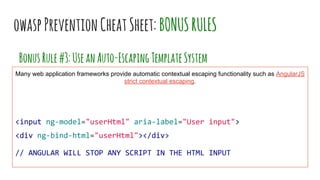
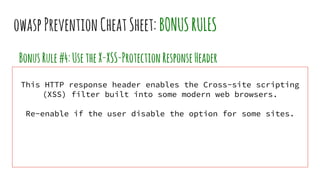
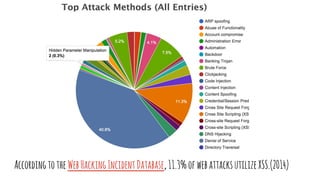
XSS vulnerabilities allow attackers to inject malicious scripts into web pages viewed by other users. There are three main types: stored XSS injects scripts into stored data like forums; reflected XSS uses malicious links; DOM-based XSS modifies the DOM. Successful XSS can steal users' cookies and passwords, hijack sessions, deface websites, and distribute malware. Developers can prevent XSS by escaping untrusted data, using safe templating systems, and implementing a content security policy.