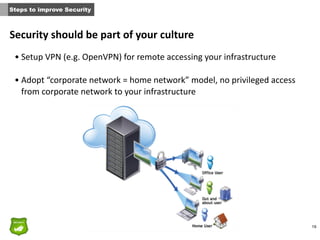
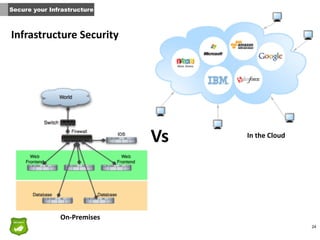
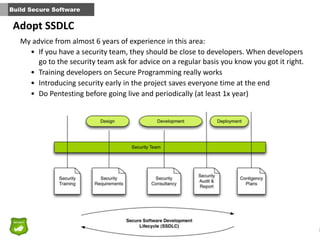
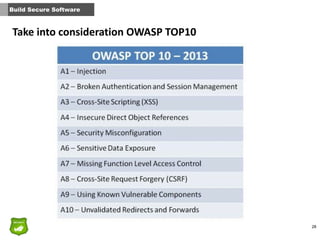
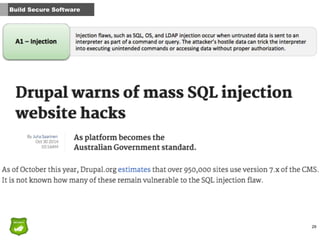
This document provides tips for John, the co-founder of a small startup, on improving security within the organization. It recommends that security should be part of the company culture from the start and promoted through regular security awareness training. It also suggests conducting a basic risk analysis to understand the main assets, threats, and vulnerabilities. Additionally, it offers advice on securing the infrastructure, whether on-premises or in the cloud, as well as adopting secure practices throughout the software development lifecycle. The overall message is that security is important for startups to address from the beginning to prevent potential attacks from putting the company out of business.