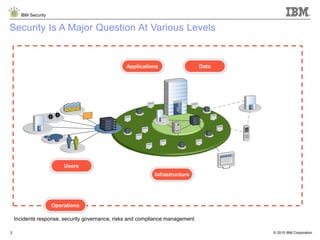
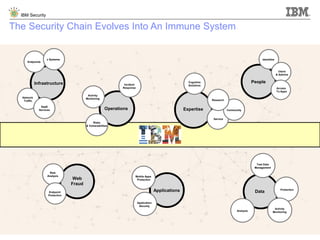
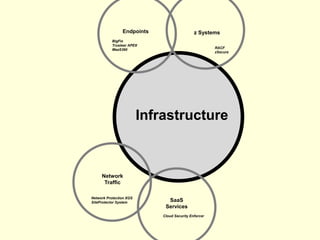
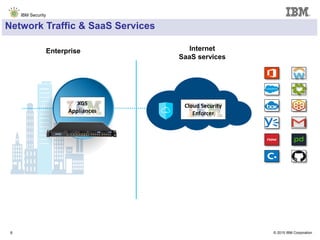
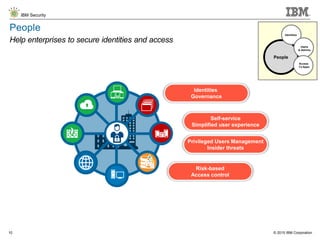
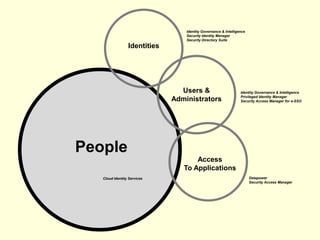
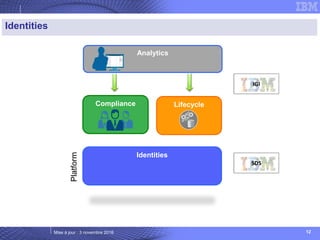
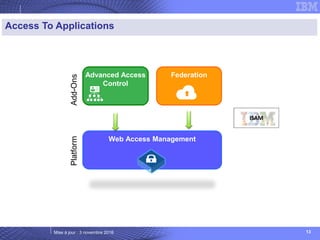
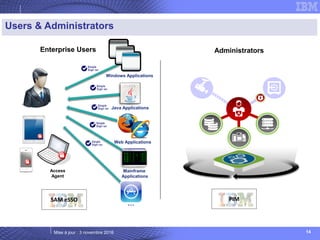
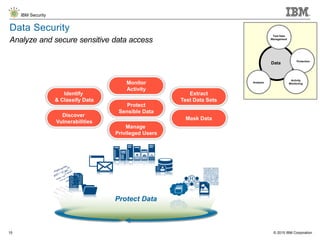
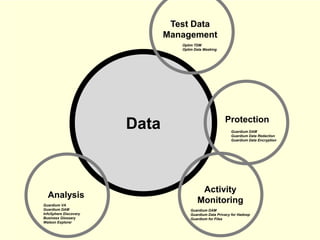
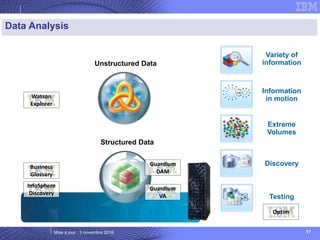
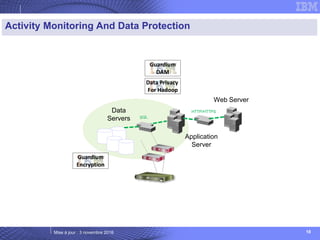
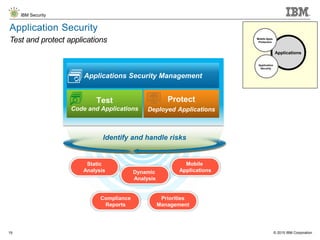
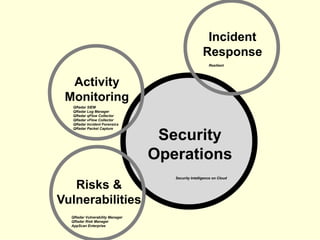
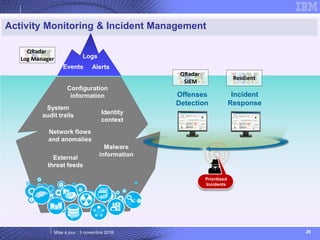
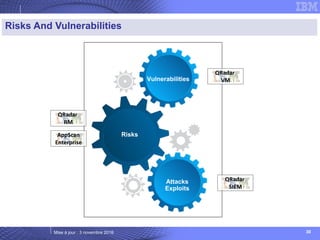
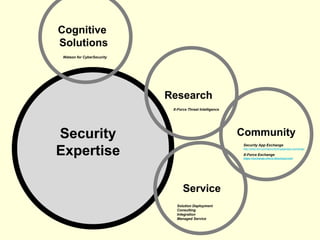
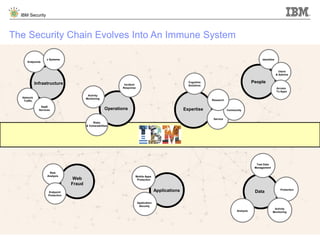
The document details IBM's security software offerings, focusing on integrated solutions for application, data, infrastructure, and endpoint protection designed to support digital transformation. It emphasizes a multi-layered security approach addressing risks, compliance, and incident response across various platforms, including cloud and mobile. Additionally, it mentions the importance of cognitive solutions and threat intelligence in enhancing security measures.