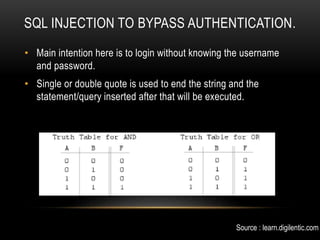
This document provides an overview of website structure, common internet protocols, and some common web vulnerabilities. It defines what a website is and its components. It describes protocols like IP, HTTP, HTTPS and their roles. It explains public vs private IP addresses and HTTP status codes and methods. The document then discusses vulnerabilities like HTML injection, SQL injection, and buffer overflow attacks that can be used to bypass authentication or execute code on a server. It provides examples of how these attacks work at a high level.