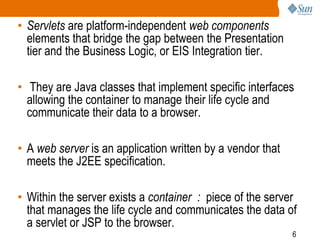
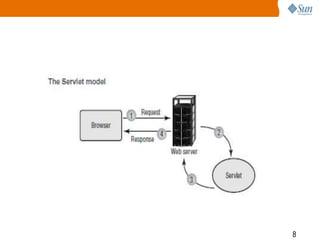
The document provides an overview of the Web Client Model and HTTP requests and responses. It discusses:
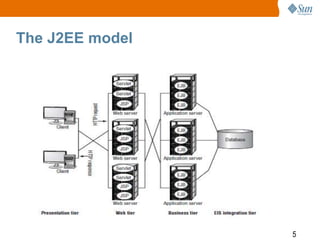
1) The J2EE model and how servlets and JSPs are used.
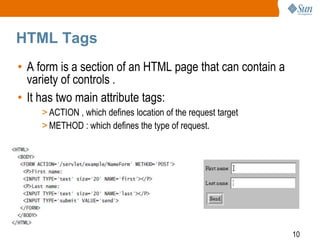
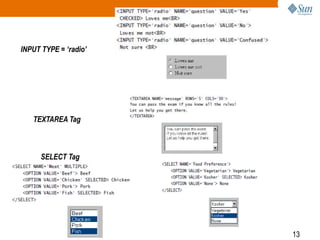
2) HTML tags like forms, inputs, and selects that are used to collect data from users.
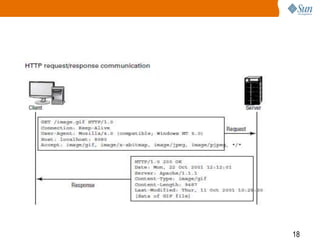
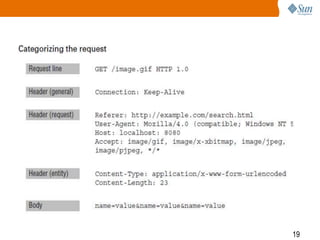
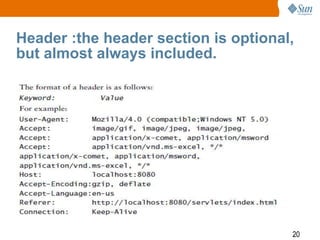
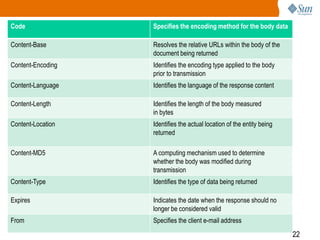
3) How HTTP is used to transfer data, including the different request methods like GET, POST, PUT, and how requests and responses are structured with a start line, headers, and body.






![15
URL
• A Uniform Resource Locator (URL) defines the information the
client needs to make a connection to the server.
• http://book.com:8080/servlet/Registration?
name=Ariela&address=1234+Happy+Street
• The full signature consists of the following:
• <protocol>://<servername>[:port]/<url-path> [?query-string]
• Request address: http://java.sun.com/products/servlet/index.html?id=‘09’
• URL: http://java.sun.com/products/servlet/index.html?id=‘09’
• URI: /products/servlet/index.html](https://image.slidesharecdn.com/thewebclientmodel-1-151128150850-lva1-app6891/85/SCWCD-The-web-client-model-CHAP-1-15-320.jpg)