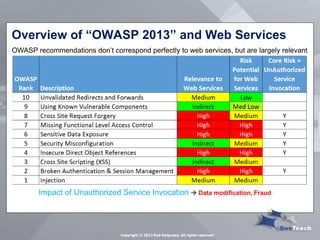
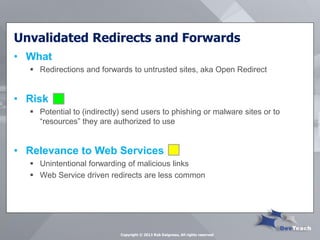
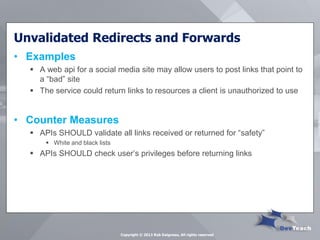
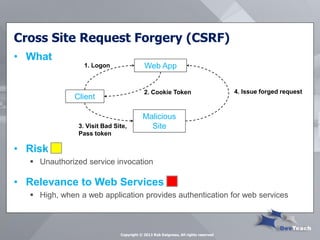
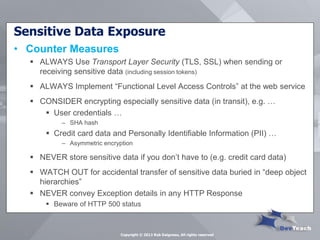
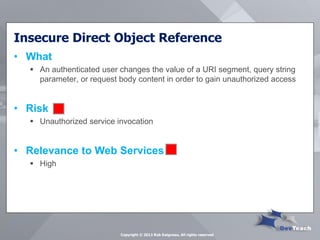
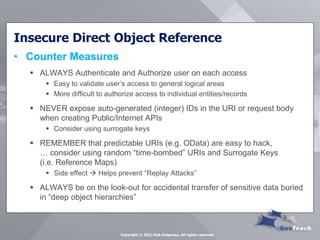
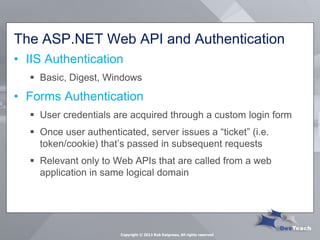
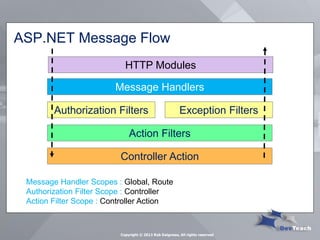
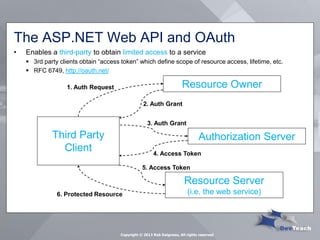
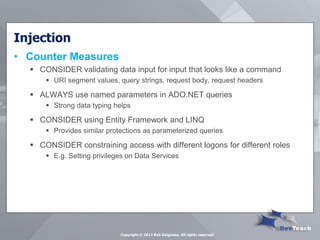
This document summarizes Rob Daigneau's presentation on securing web services. It discusses the OWASP 2013 top 10 security risks and their relevance to web services. For each risk, it provides a brief description, potential impact, and recommendations for mitigation strategies specific to web services, such as implementing access controls, encrypting sensitive data, and validating all user input.