The document discusses various web security topics such as SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and parameter tampering. It provides examples of these vulnerabilities and methods to prevent them, including input validation, output encoding, anti-forgery tokens, and limiting exposed functionality. The document is intended as an educational guide on common web security issues and best practices.



















![Stored Procedures & ORM
ALTER PROCEDURE dbo.SearchWidgets
@SearchTerm VARCHAR(50)
AS BEGIN
DECLARE @query VARCHAR(100)
SET @query = 'SELECT Id, Name FROM dbo.Widget WHERE Name LIKE ''%'
+ @SearchTerm + '%'''
EXEC(@query)
END
20
var searchTerm = Request.QueryString["SearchTerm"];
var db = new WidgetEntities();
var widgets = db.SearchWidgets(searchTerm);
SELECT Id, Name FROM dbo.Widget WHERE Name LIKE '%Radi' or 1=1;--%'
* Bonus content from: http://www.troyhunt.com/2012/12/stored-procedures-and-orms-wont-save.html](https://image.slidesharecdn.com/7-150523162809-lva1-app6891/85/ASP-NET-Web-Security-20-320.jpg)






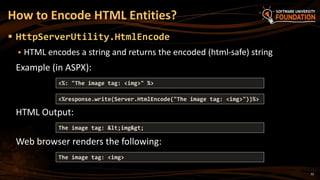
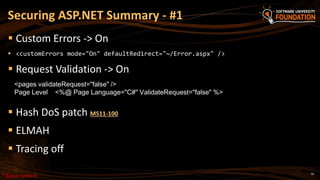
![28
ASP.NET WebForms
Disable the HTTP request validation for all pages in Web.config
(in <system.web>):
ASP.NET MVC
Using the ValidateInput filter we can disable validation for an
action or entire controller
Disable Request Validation
<httpRuntime requestValidationMode="2.0" />
<pages validateRequest="false" />
[ValidateInput(false)]
public ActionResult XssMvc(string someInput) { … }](https://image.slidesharecdn.com/7-150523162809-lva1-app6891/85/ASP-NET-Web-Security-28-320.jpg)




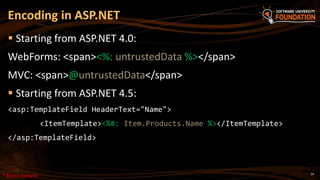





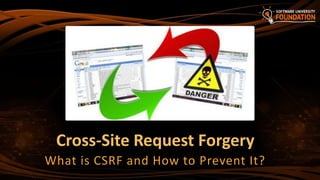





![46
To prevent CSRF attacks in MVC apps use
anti-forgery tokens (aka NONCE token)
Put the anti-CSRF token in the HTML forms:
Verify the anti-CSRF token in each controller action that should be
protected:
Prevent CSRF in ASP.NET MVC
@using (@Html.BeginForm("Action", "Controller"))
{
…
@Html.AntiForgeryToken()
}
[ValidateAntiForgeryToken]
public ActionResult Action(…)
{ … }](https://image.slidesharecdn.com/7-150523162809-lva1-app6891/85/ASP-NET-Web-Security-46-320.jpg)









![57
MVC is stateless – no real protection
WebForms is much better – ViewState & Event Validation
Looking at Request.UrlReferrer is not sufficient!
Parameter encryption
([Bind(Include = "Name, Email, CommentText")] &
[Bind(Exclude)]
Only real solution – validate if the user can retrieve or update
the data – [Authorize] is not enough!
Preventing Parameter Tampering
* Bonus content](https://image.slidesharecdn.com/7-150523162809-lva1-app6891/85/ASP-NET-Web-Security-57-320.jpg)



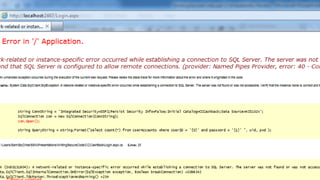








![72
Use IsLocalUrl() on login pages
FormsService.SignIn(model.UserName, model.RememberMe);
if (IsLocalUrl(returnUrl)) {
Use the AntiForgeryToken on every form post to prevent CSRF
attacks
Use ValidateAntiForgeryToken on Controllers
[ValidateAntiForgeryToken] public ViewResult Update()
Validate access to retrieved or edited data
Securing ASP.NET Summary - #3
* Bonus content](https://image.slidesharecdn.com/7-150523162809-lva1-app6891/85/ASP-NET-Web-Security-72-320.jpg)