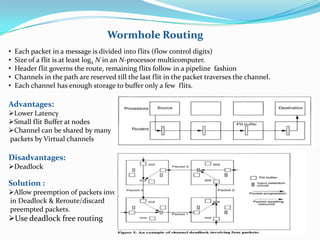
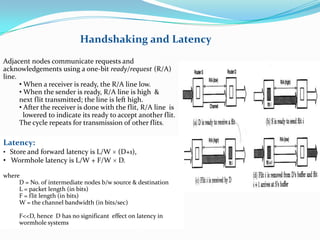
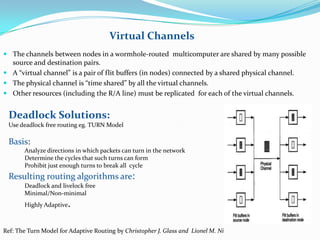
This document discusses wormhole routing in multicomputers. In wormhole routing, packets are divided into fixed-size units called flits. The header flit determines the route and reserves channels as subsequent flits follow in a pipeline. Each channel can buffer only a few flits. Wormhole routing has lower latency than store-and-forward but can cause deadlock. Deadlock is addressed through preemption and rerouting of blocked packets or using deadlock-free routing algorithms like the turn model. Virtual channels allow sharing of physical channels among packets through time-division multiplexing of flit buffers.