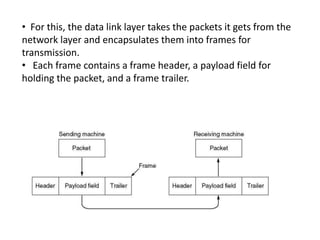
The data link layer is responsible for node-to-node communication and transforming the physical layer into a reliable link. It handles framing, addressing, error control, flow control, and media access. The data link layer provides services like unacknowledged connectionless, acknowledged connectionless, and acknowledged connection-oriented to the network layer. Framing groups the physical layer bit stream into discrete frames using techniques like character counting, flag bytes with stuffing, or encoding violations.