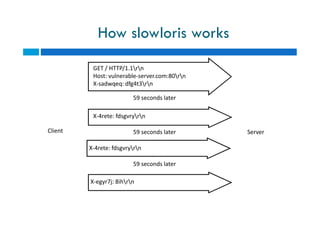
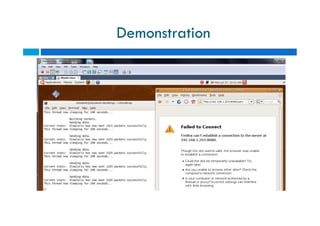
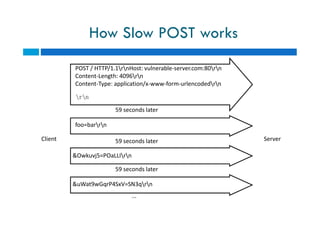
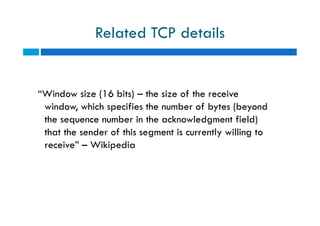
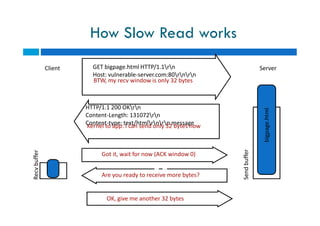
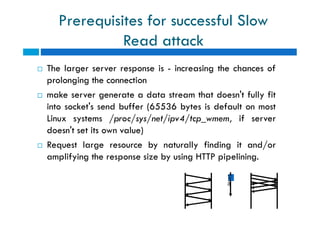
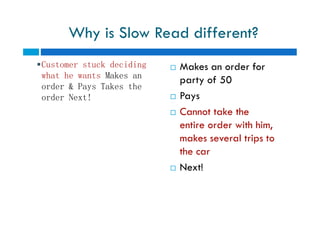
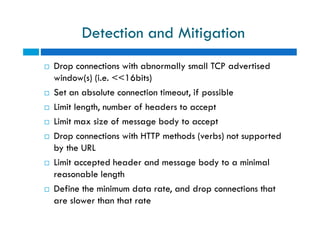
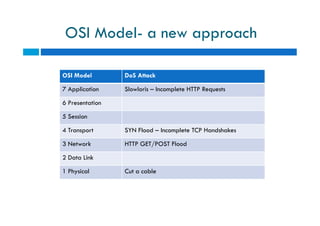
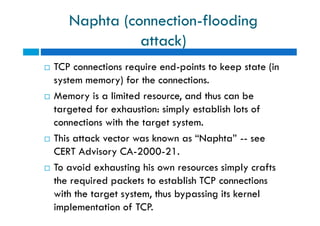
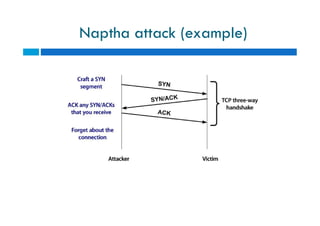
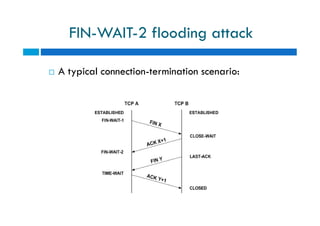
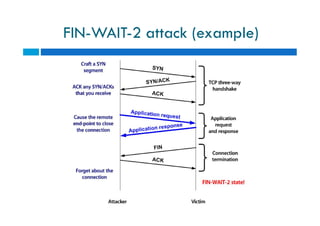
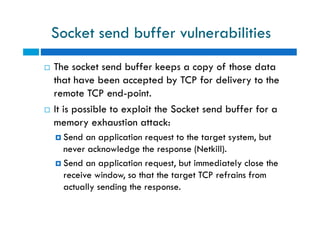
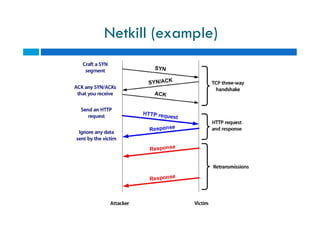
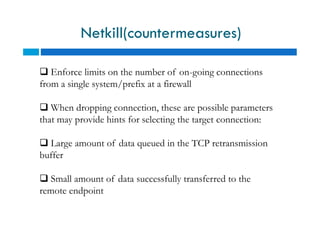
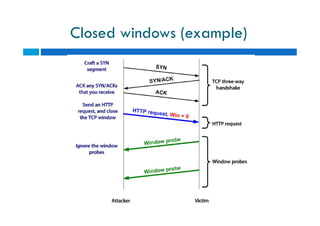
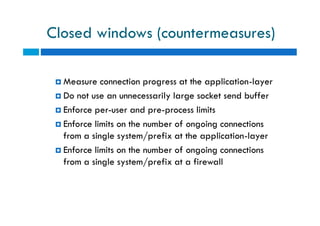
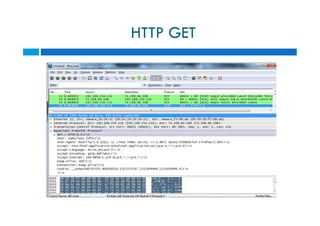
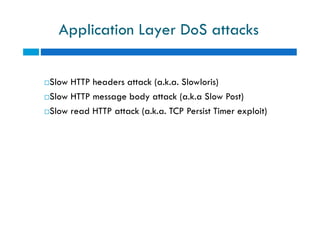
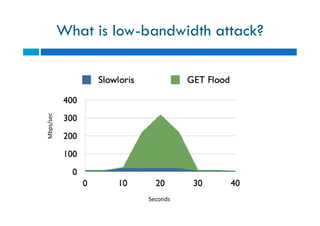
The document discusses different types of denial of service (DoS) attacks against web servers, focusing on Slowloris, Slow Post, and Slow Read attacks. Slowloris keeps connections open by sending partial HTTP requests and headers. Slow Post sends complete headers but an incomplete message body. Slow Read maliciously throttles the receipt of large HTTP responses to tie up server resources. These low-bandwidth attacks can be effective at consuming connection pools and overloading servers. The document provides details on how each attack works and recommendations for detection and mitigation techniques.







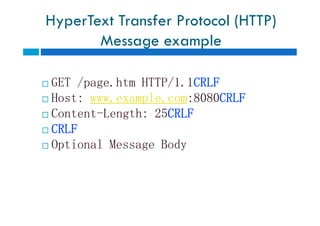
![HyperText Transfer Protocol (HTTP)
Message syntax
Per RFC 2616
generic-message = start-line
*(message-header CRLF)
CRLF
[ message-body ]
start-line = Request-Line | Status-Line
Per RFC 2616
generic-message = start-line
*(message-header CRLF)
CRLF
[ message-body ]
start-line = Request-Line | Status-Line](https://image.slidesharecdn.com/vrtdos-150211004319-conversion-gate01/85/Null-HYD-VRTDOS-12-320.jpg)