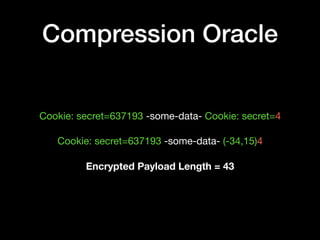
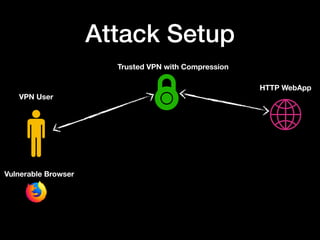
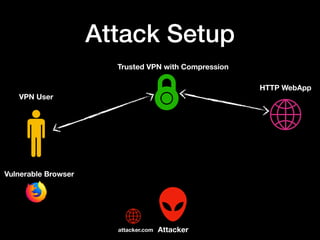
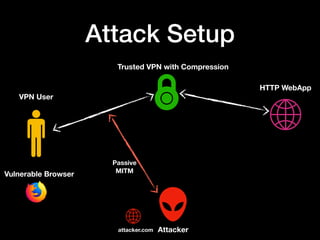
The document discusses the vulnerabilities of VPN networks to compression oracle attacks, highlighting how compression can be exploited by attackers to leak sensitive data. It outlines the history and mechanics of such attacks, particularly focusing on how browsers can play a role in performing these attacks against systems using vulnerable configurations. The author emphasizes the need for VPN services to disable compression for plaintext transactions and suggests a transition to HTTPS for enhanced security.