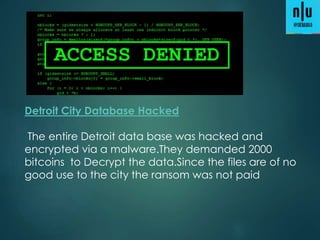
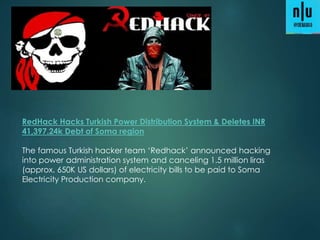
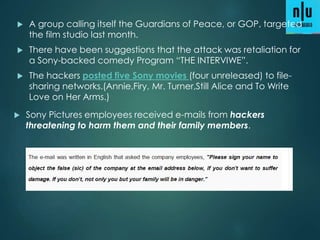
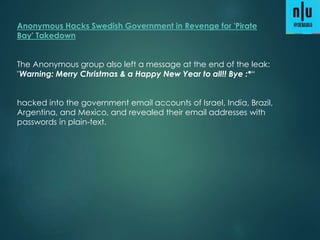
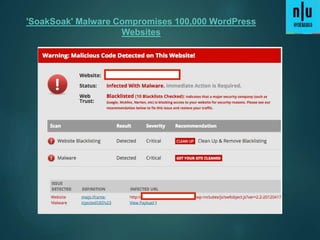
1) 12 million home and office routers are vulnerable to "Misfortune Cookie" attacks that allow hackers to take control over a network by sending a specially crafted HTTP cookie to the public IP address.
2) A critical vulnerability in the Git version control software allows remote code execution when cloning or checking out repositories from a malicious Git server.
3) The global internet authority ICANN was hacked through a spear phishing campaign targeting its staff, allowing hackers to gain administrative access to some of its systems.