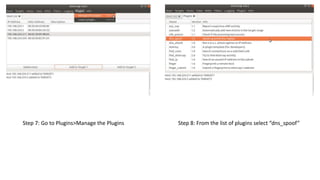
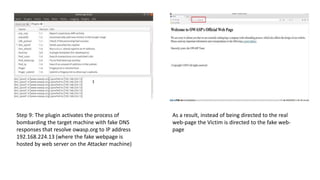
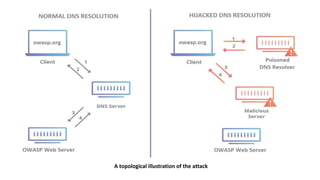
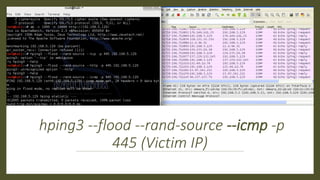
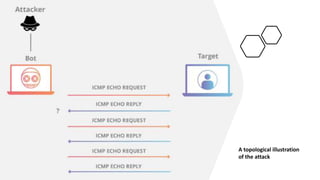
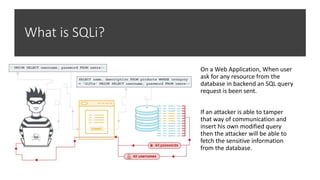
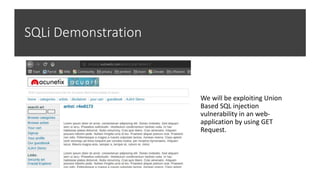
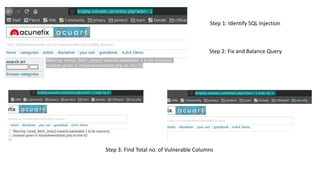
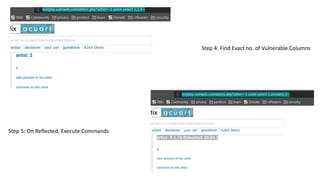
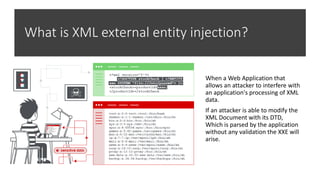
The document discusses various cybersecurity threats, including DNS cache poisoning, ICMP flood attacks, SQL injection, and XML external entity injection. It explains how these attacks occur, provides demonstrations of each, and outlines prevention measures such as using antivirus software, parameterized queries, and disabling dangerous features in XML processing. The document serves as a detailed guide for understanding and mitigating these security risks.