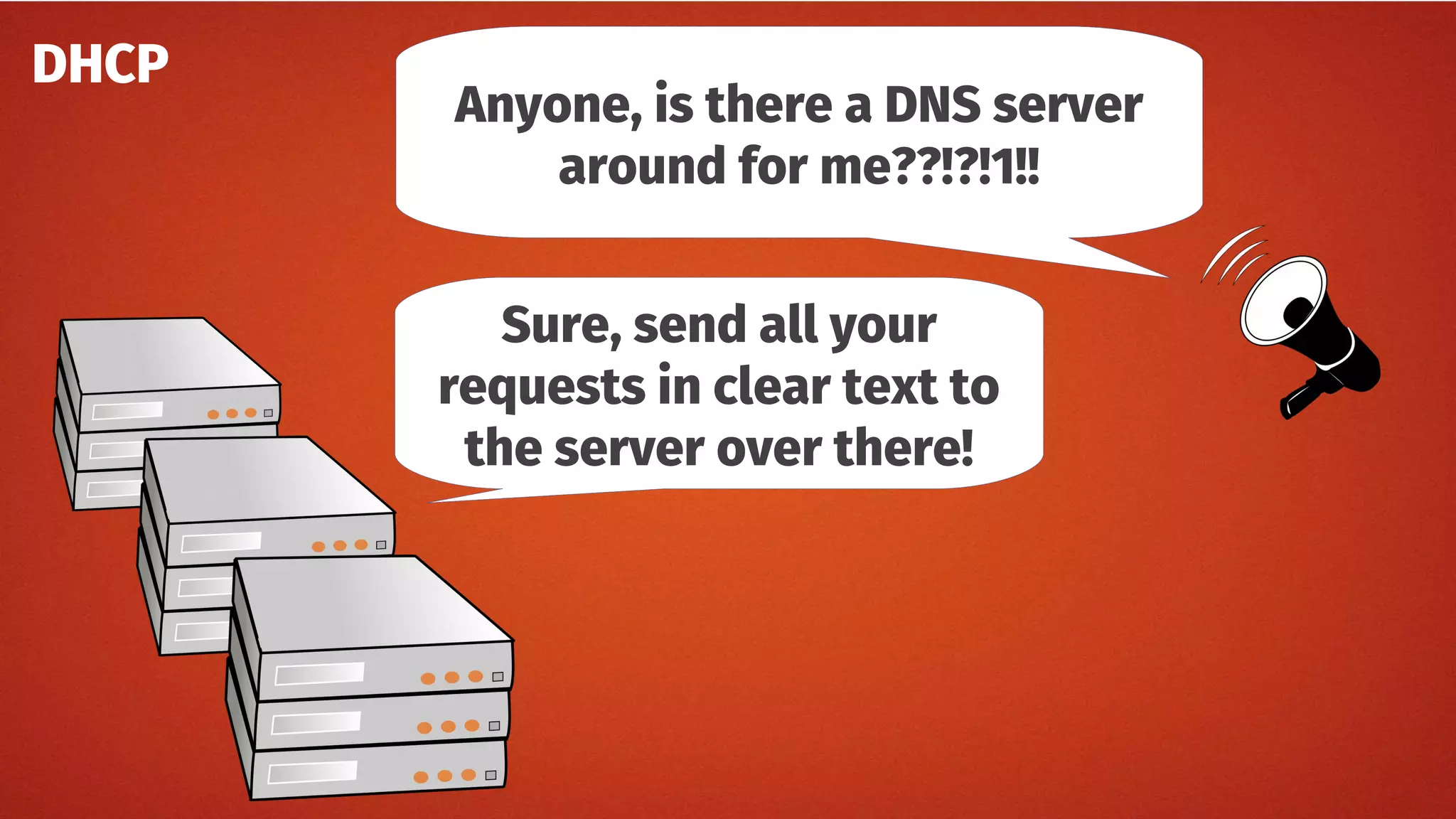
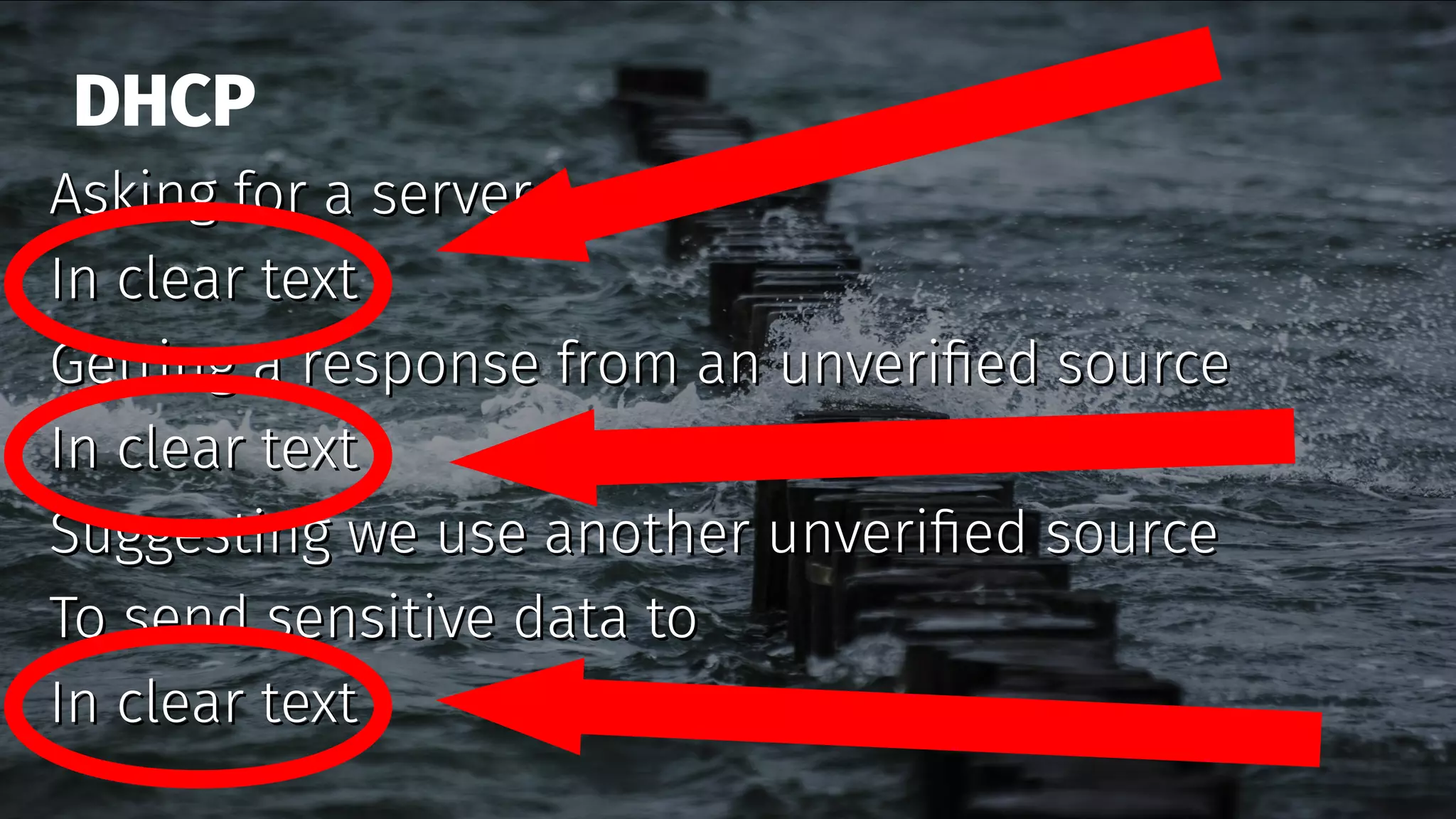
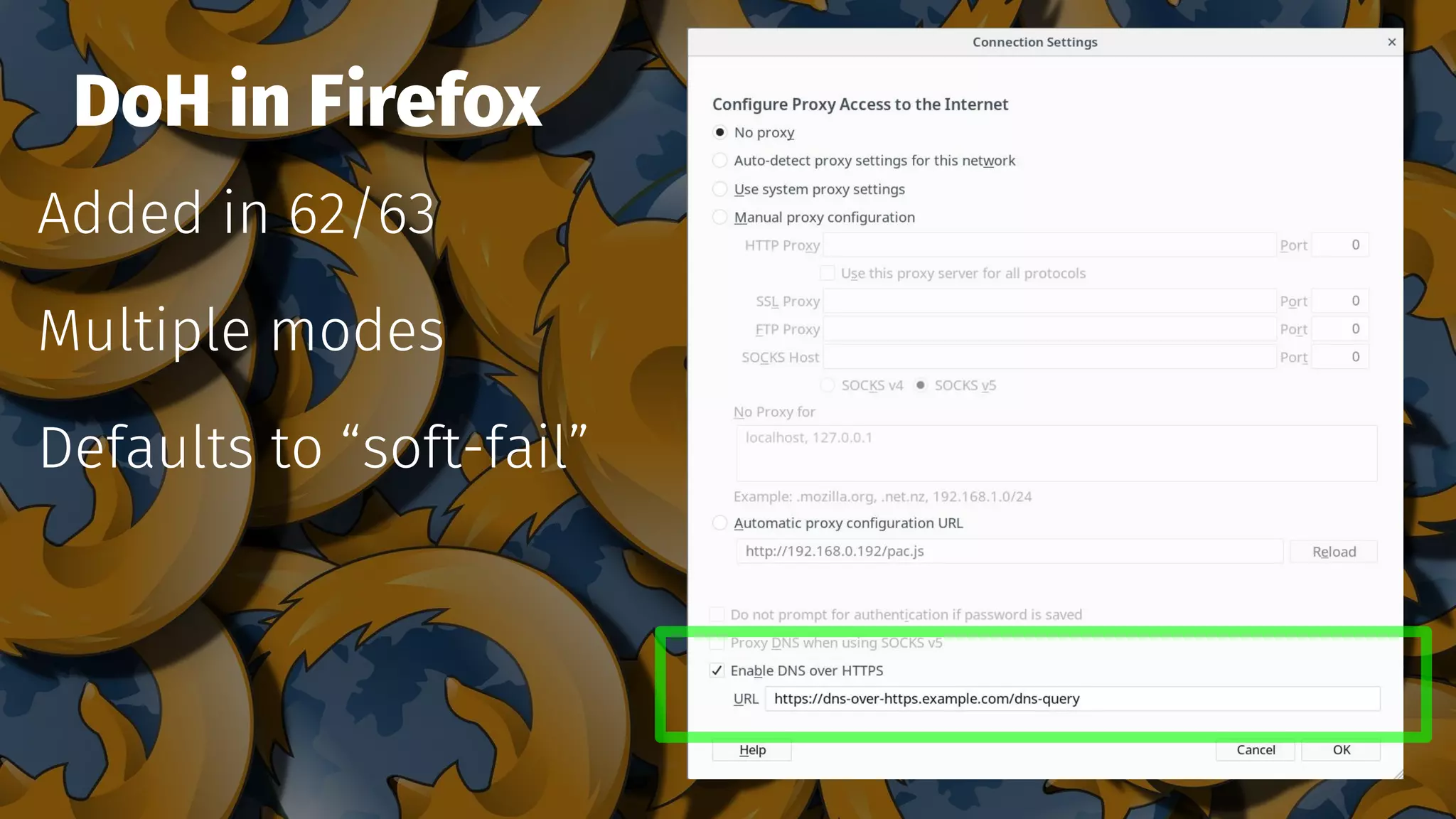
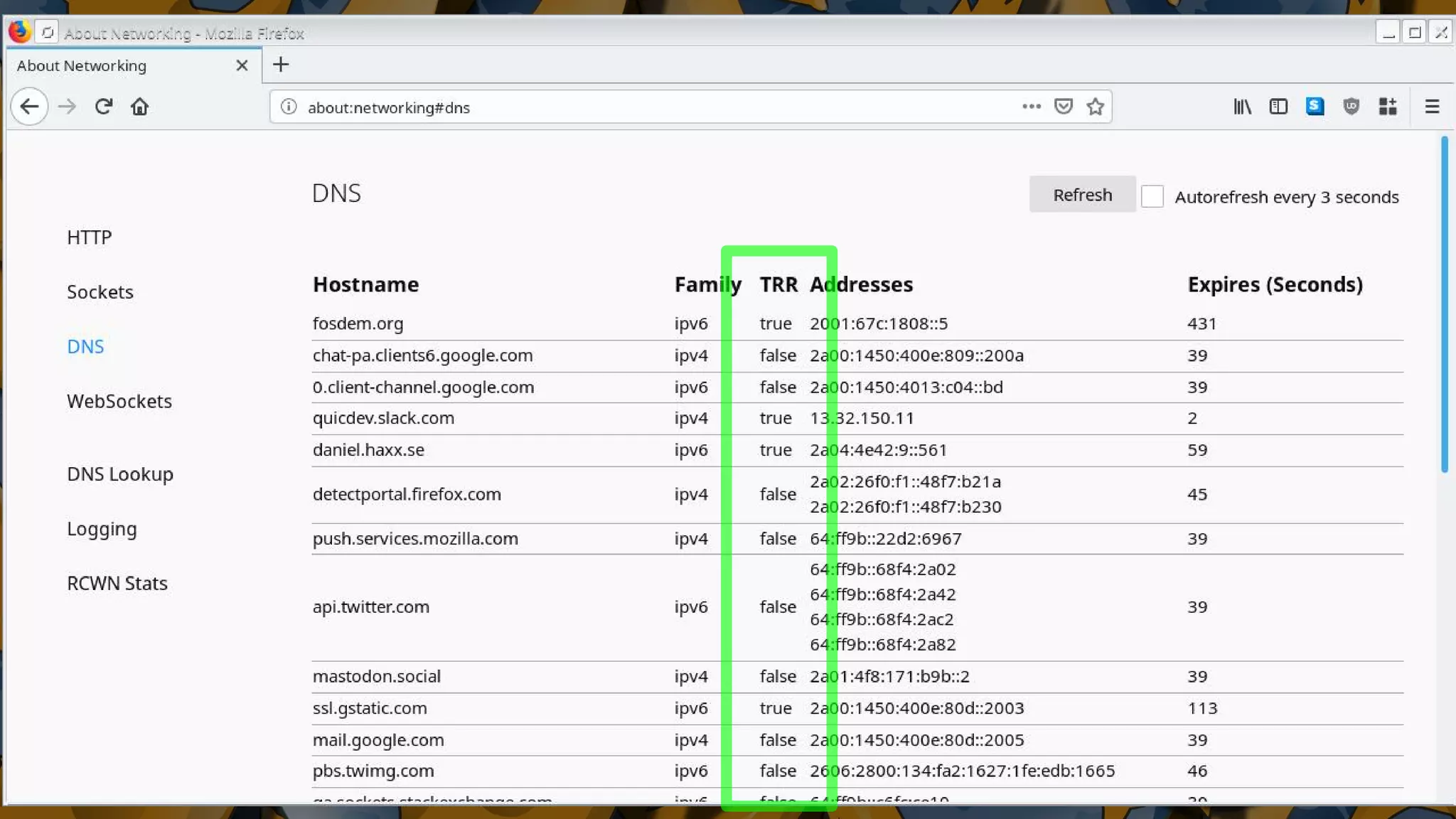
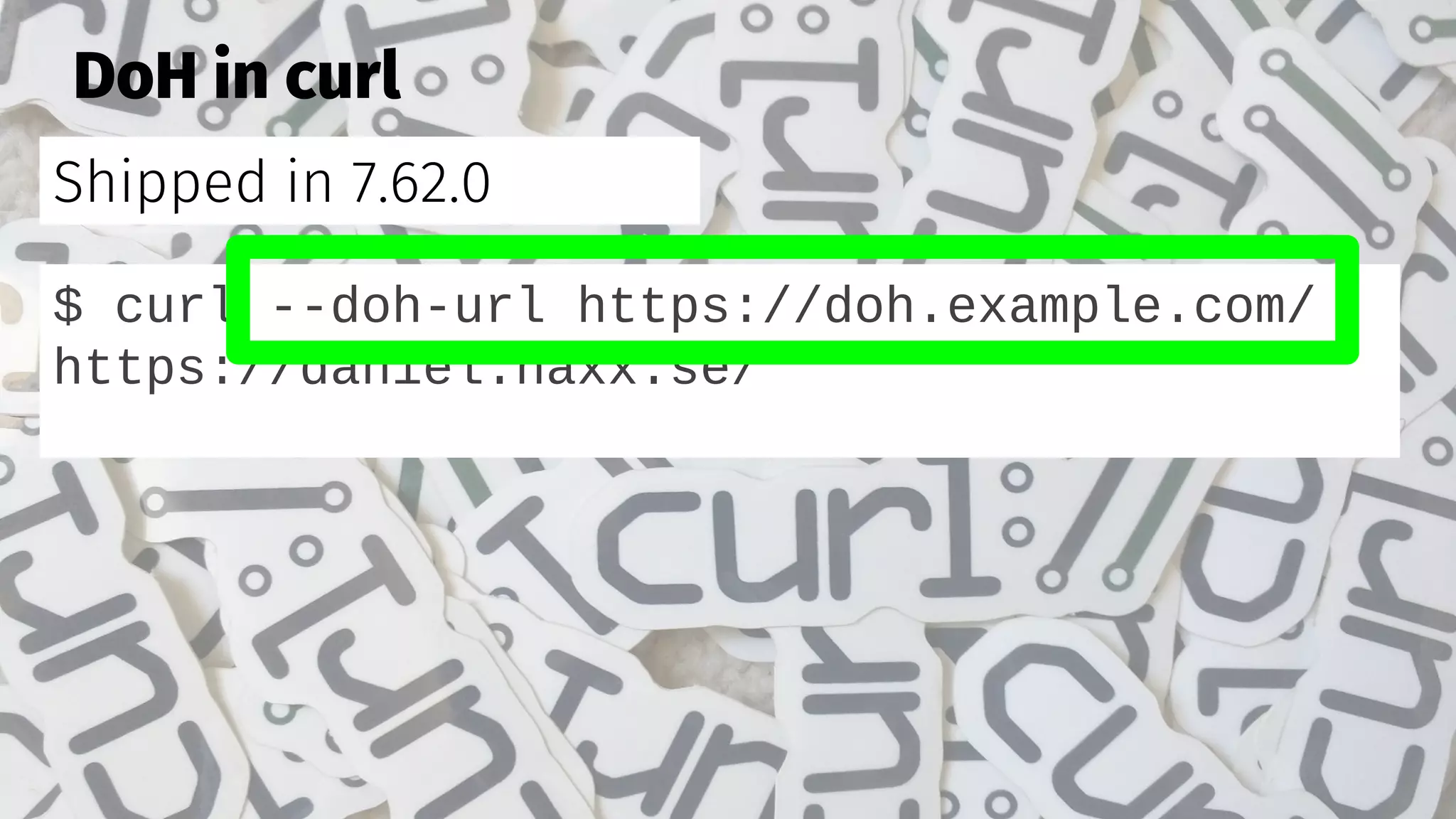
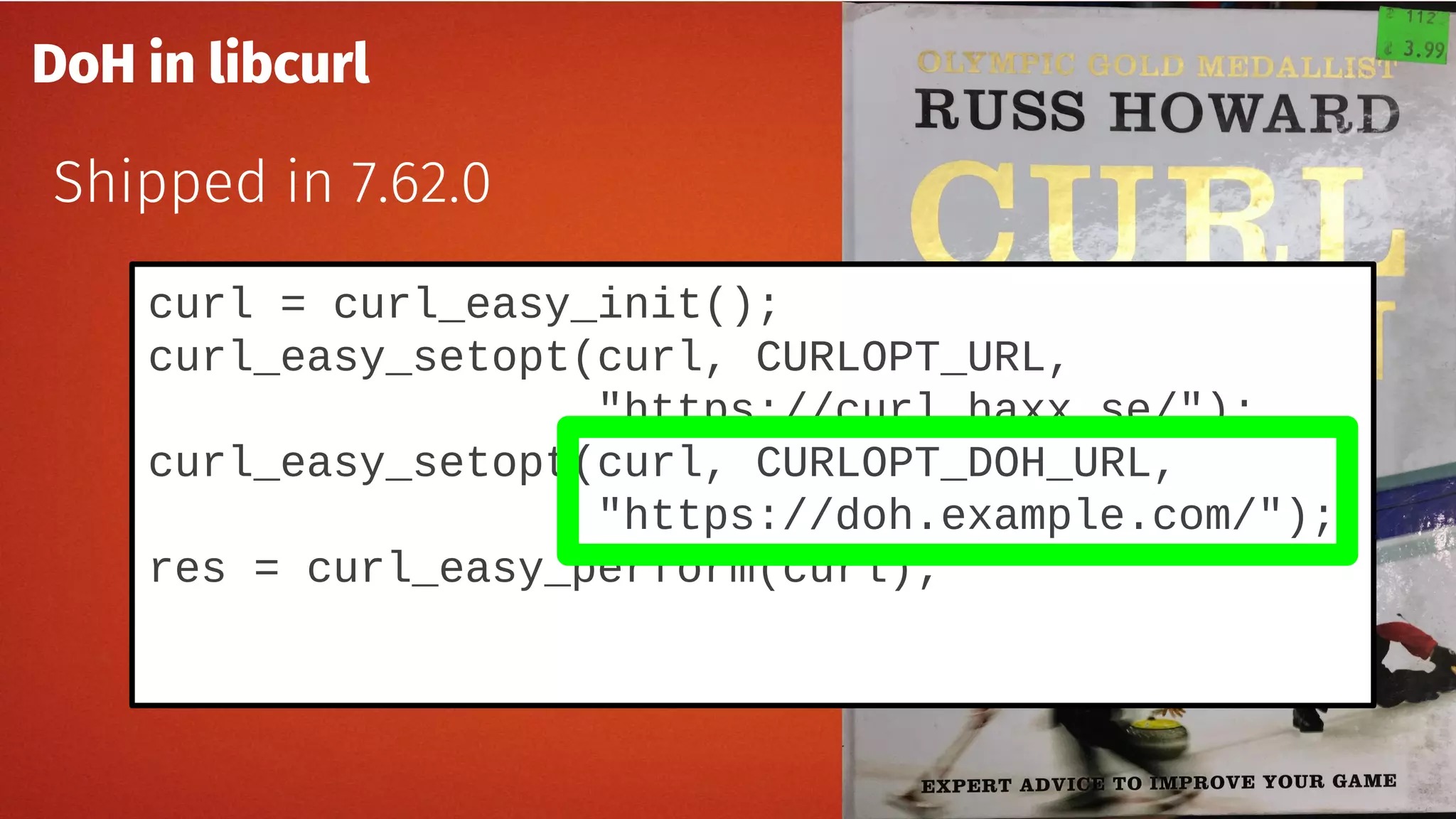
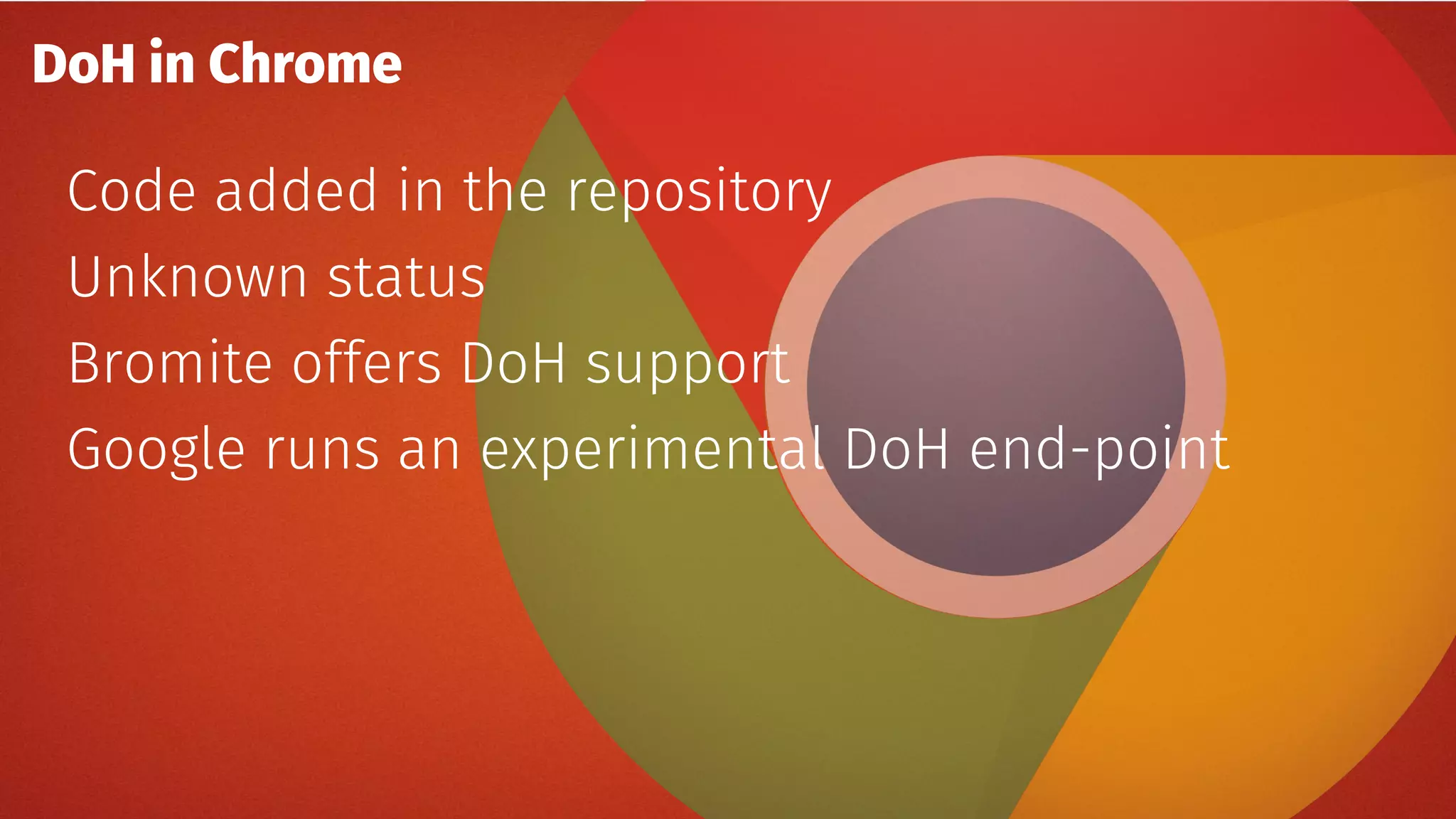
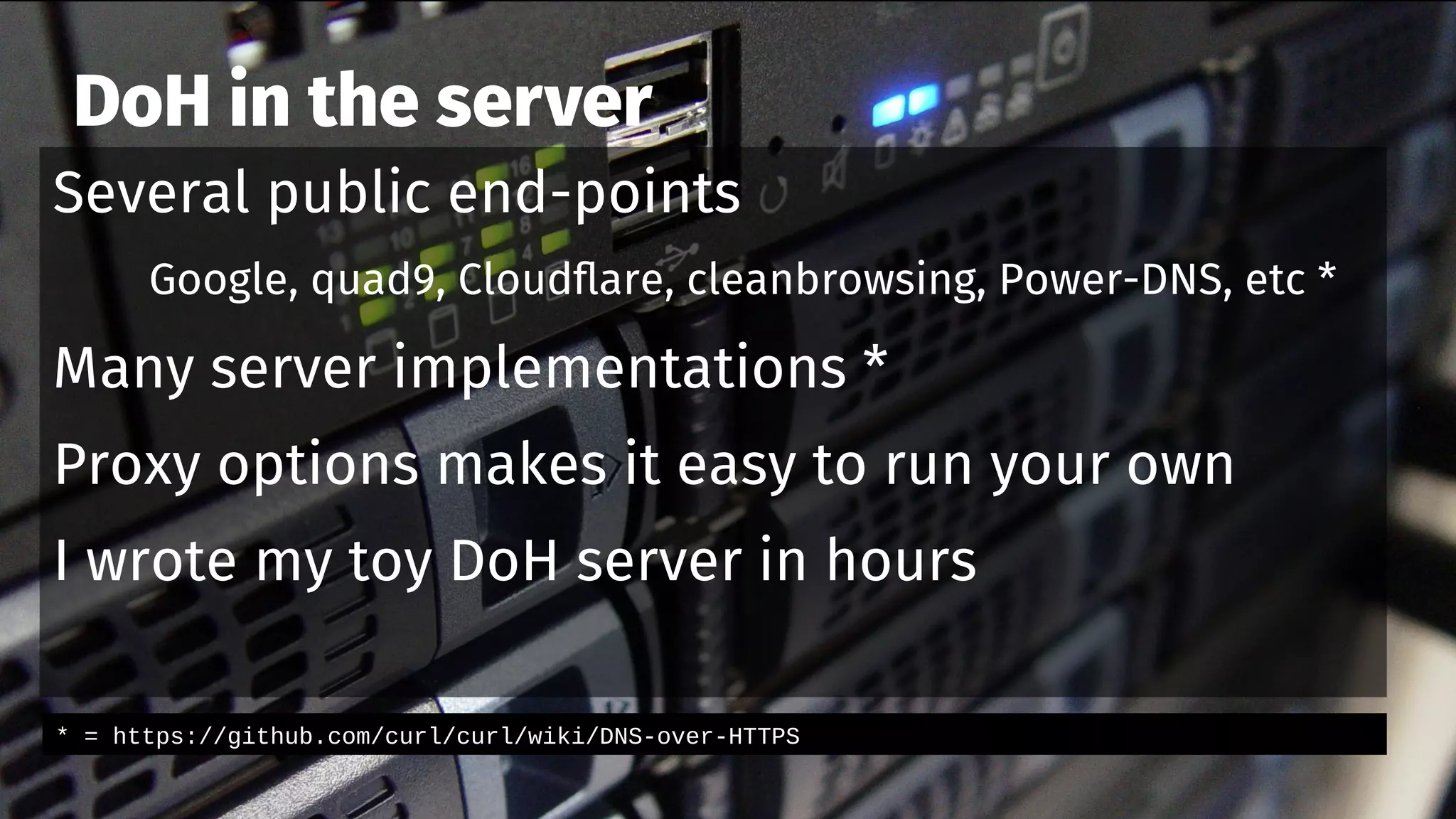
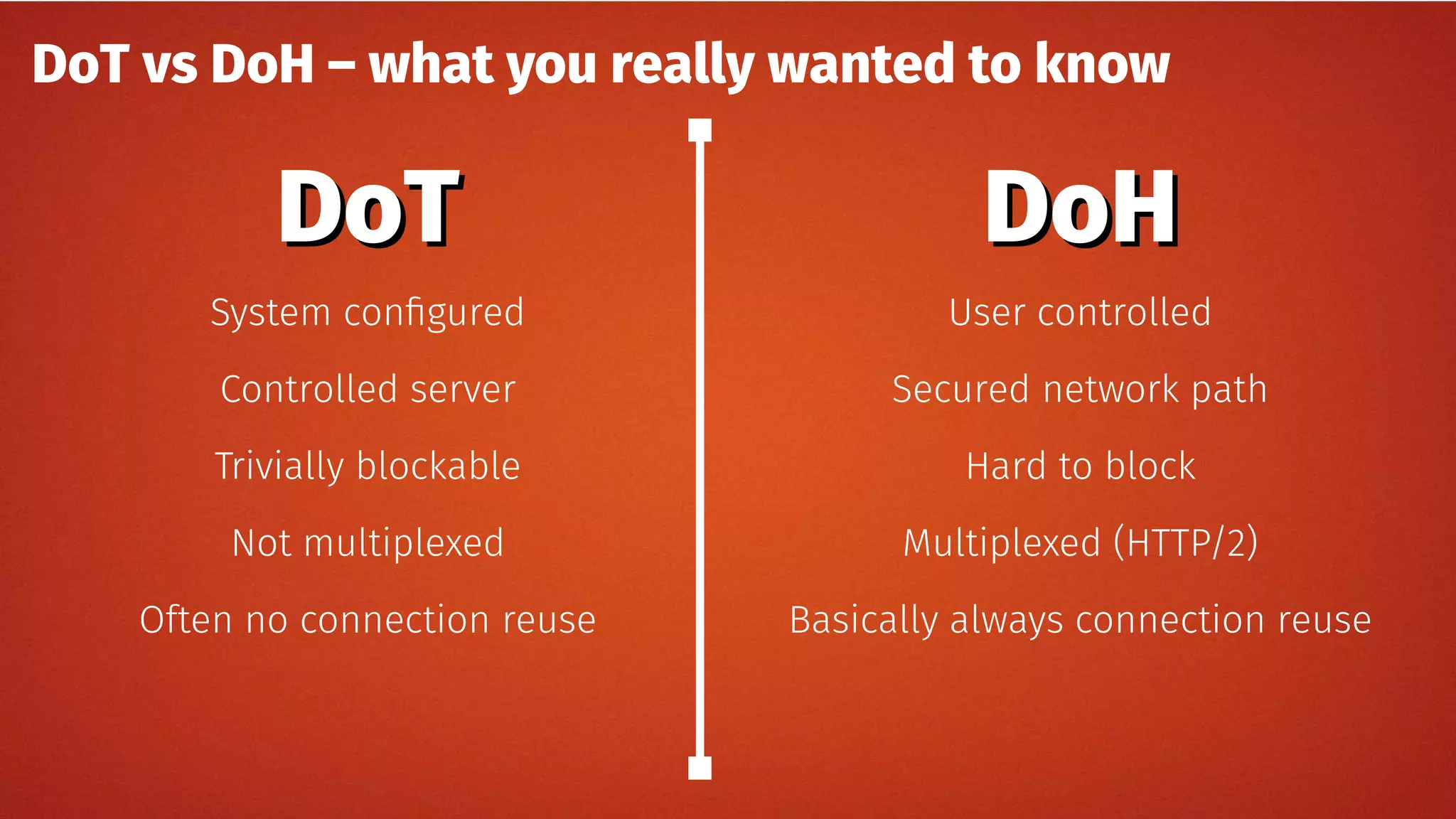
The document discusses the security features and implementation of DNS over HTTPS (DoH), highlighting its advantages over traditional DNS methods that use clear text communication. It covers various aspects such as enabling DoH in different browsers, the challenges related to user configuration, privacy, and centralization of DNS services. Additionally, it addresses other secure DNS protocols like DNS over TLS and their limitations, emphasizing that secure DNS is still an evolving area requiring ongoing exploration.