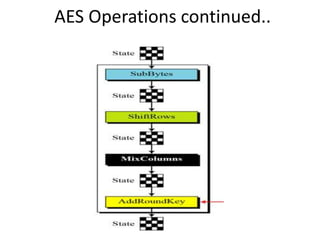
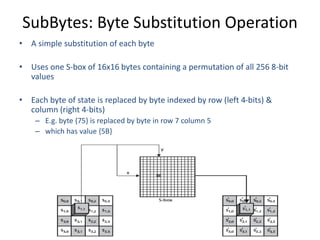
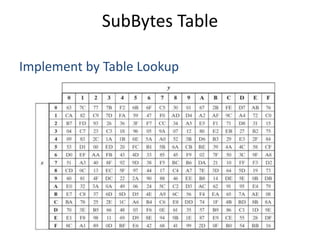
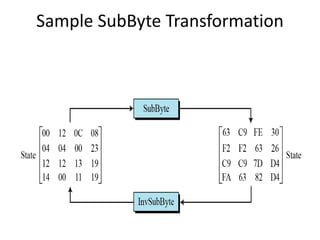
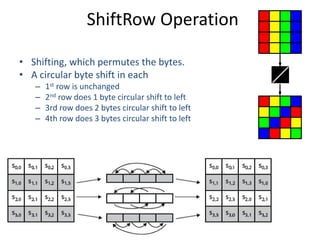
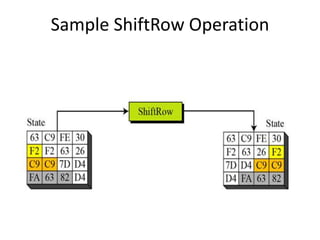
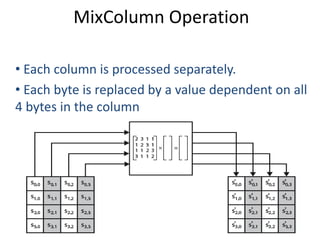
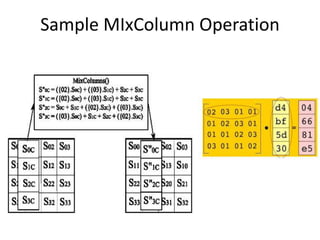
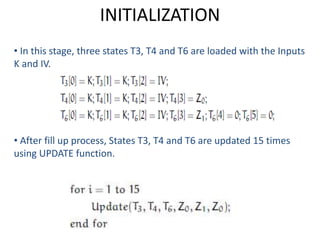
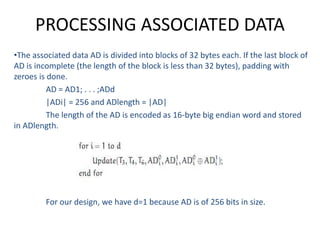
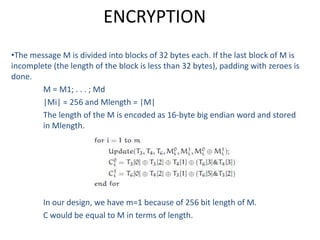
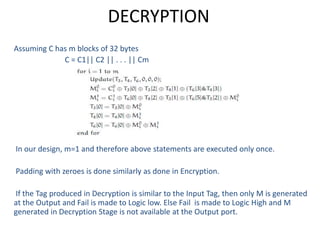
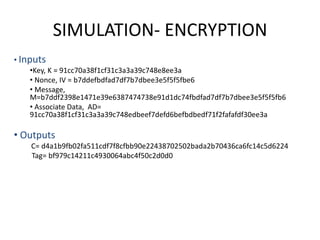
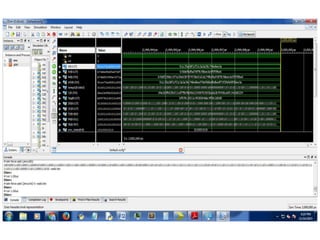
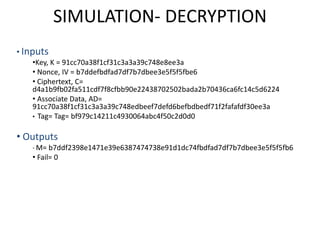
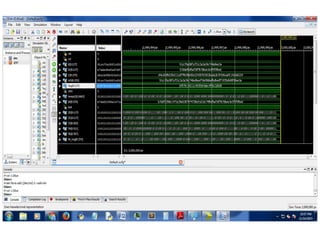
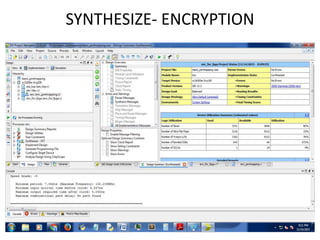
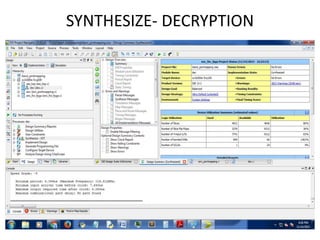
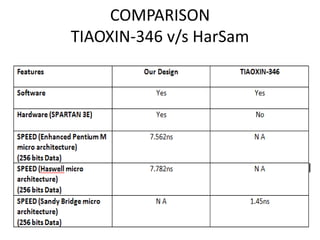
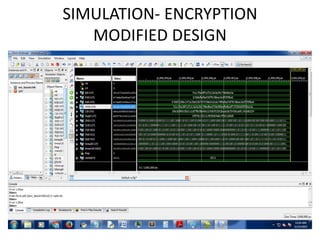
The document presents a project titled Harsam, a hardware implementation of the Tiaoxin-346 design, which focuses on efficient authenticated encryption to enhance data security. Authenticated encryption is introduced as a more reliable method than traditional encryption by requiring both encryption and authentication in a single process. The project details the stages of encryption and decryption processes, alongside simulation results, and outlines future work to improve design performance.