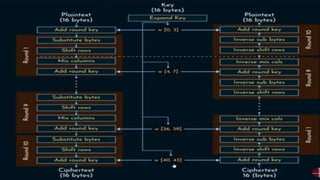
The document discusses the Advanced Encryption Standard (AES) algorithm. It describes AES as a cybersecurity standard for encrypting electronic data using symmetric-key algorithms with key sizes of 128, 192, and 256 bits. The document outlines the key components of AES, including the key expansion, round key addition, byte substitution, row shifting, column mixing, and different numbers of transformation rounds depending on the key size. It also explains the processes of AES encryption and decryption. Finally, it discusses various modes of operation for AES, such as electronic codebook (ECB), cipher block chaining (CBC), cipher feedback (CFM), output feedback (OFM), and counter (CTR) modes.