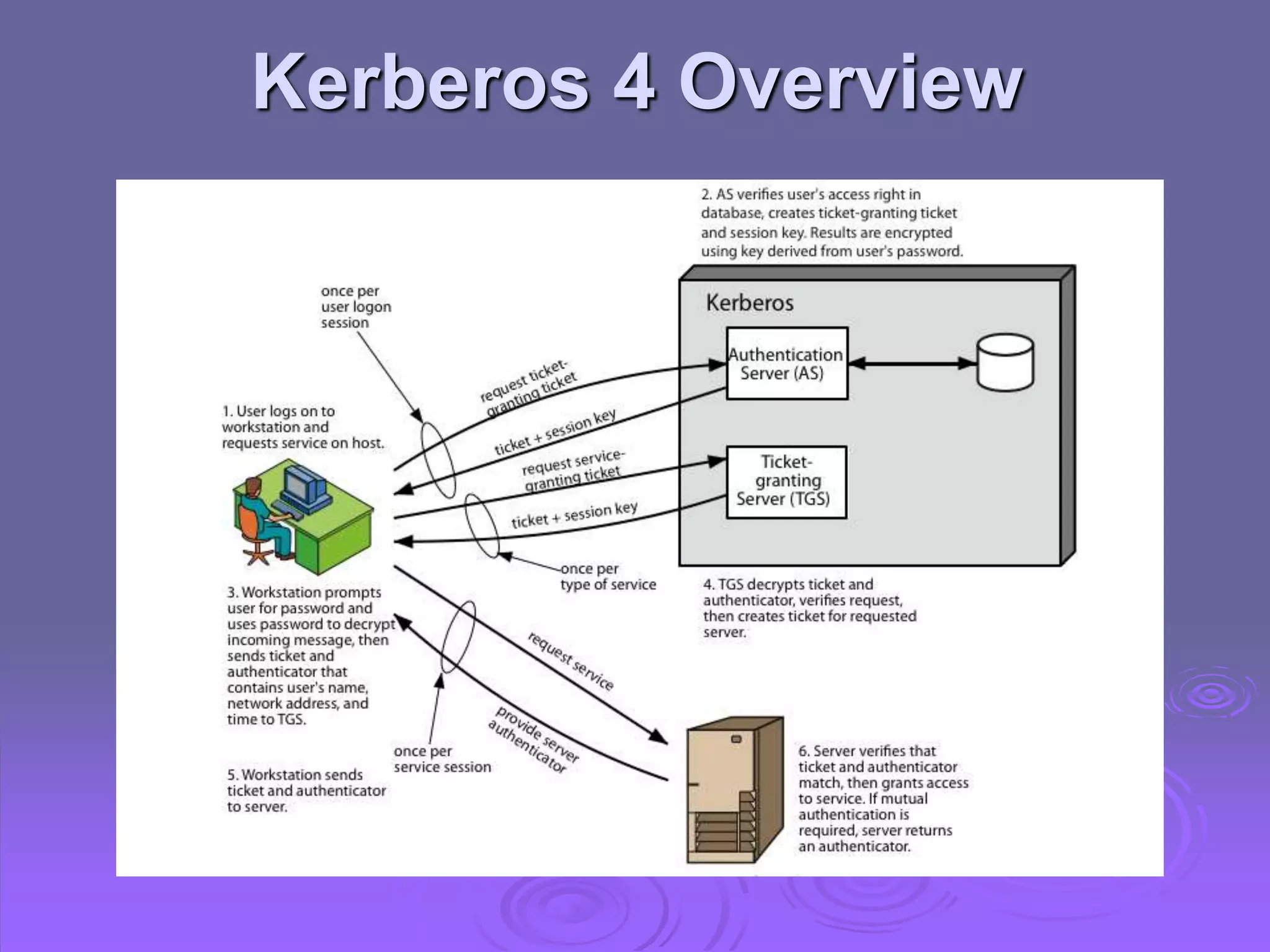
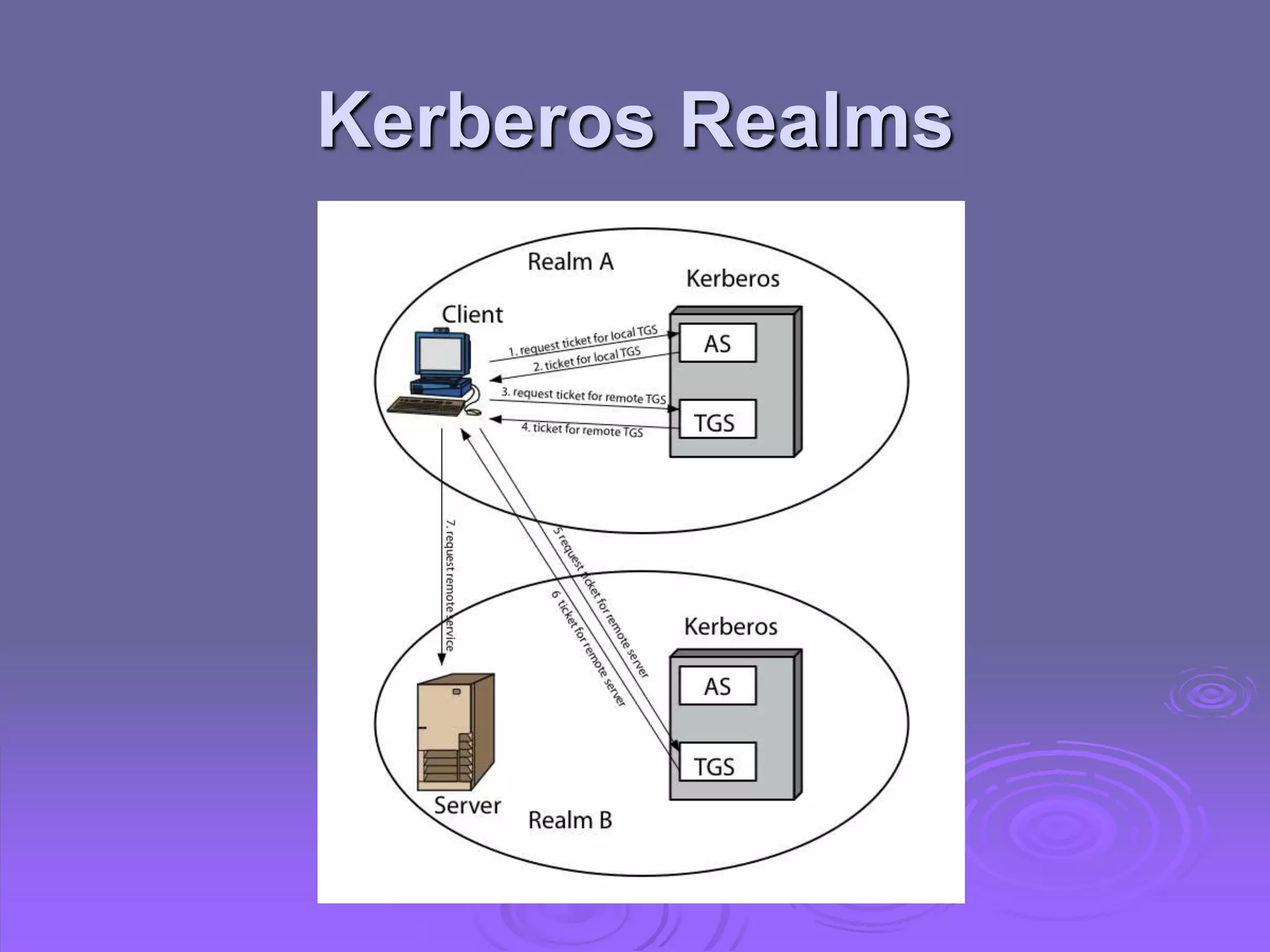
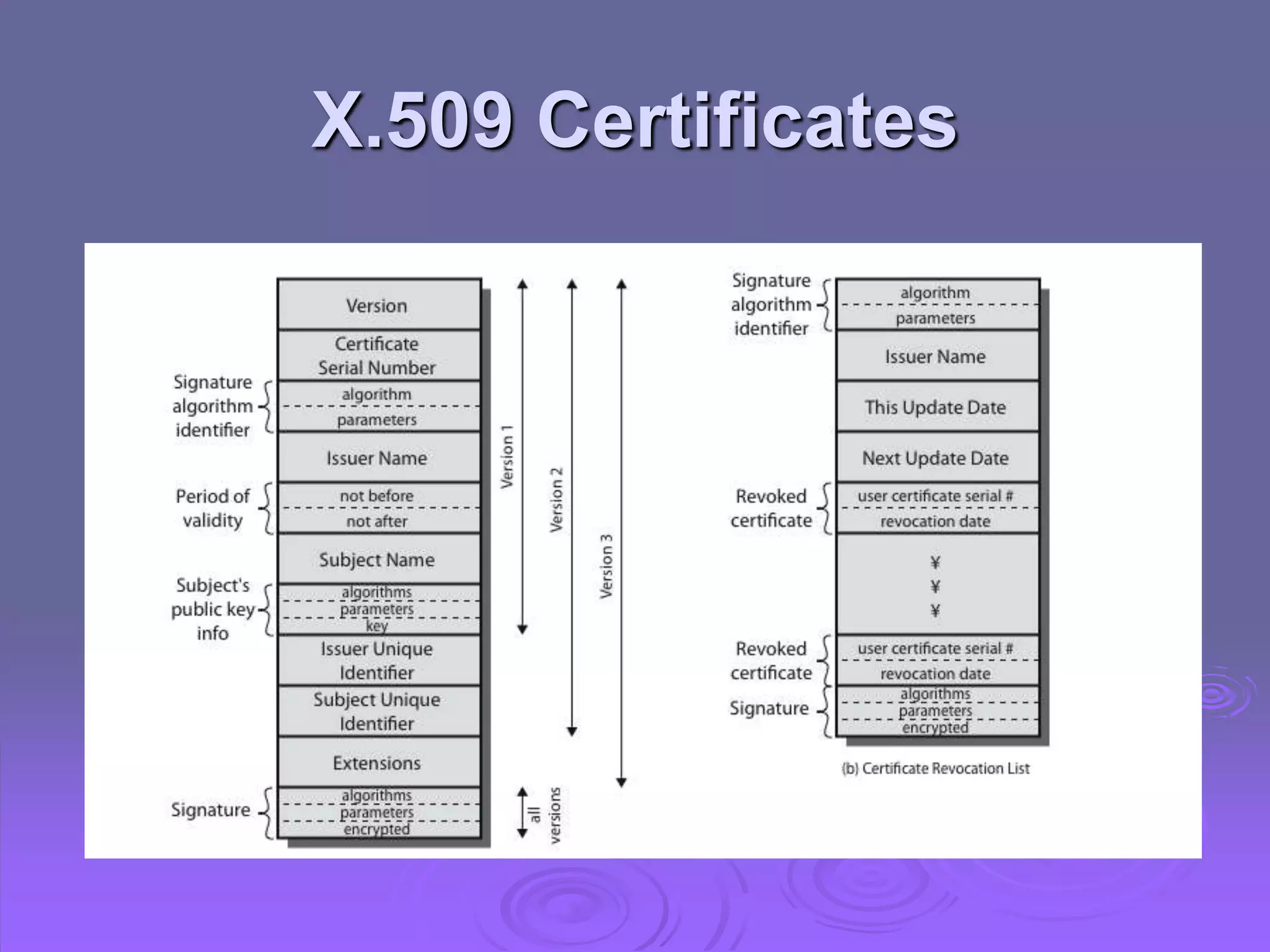
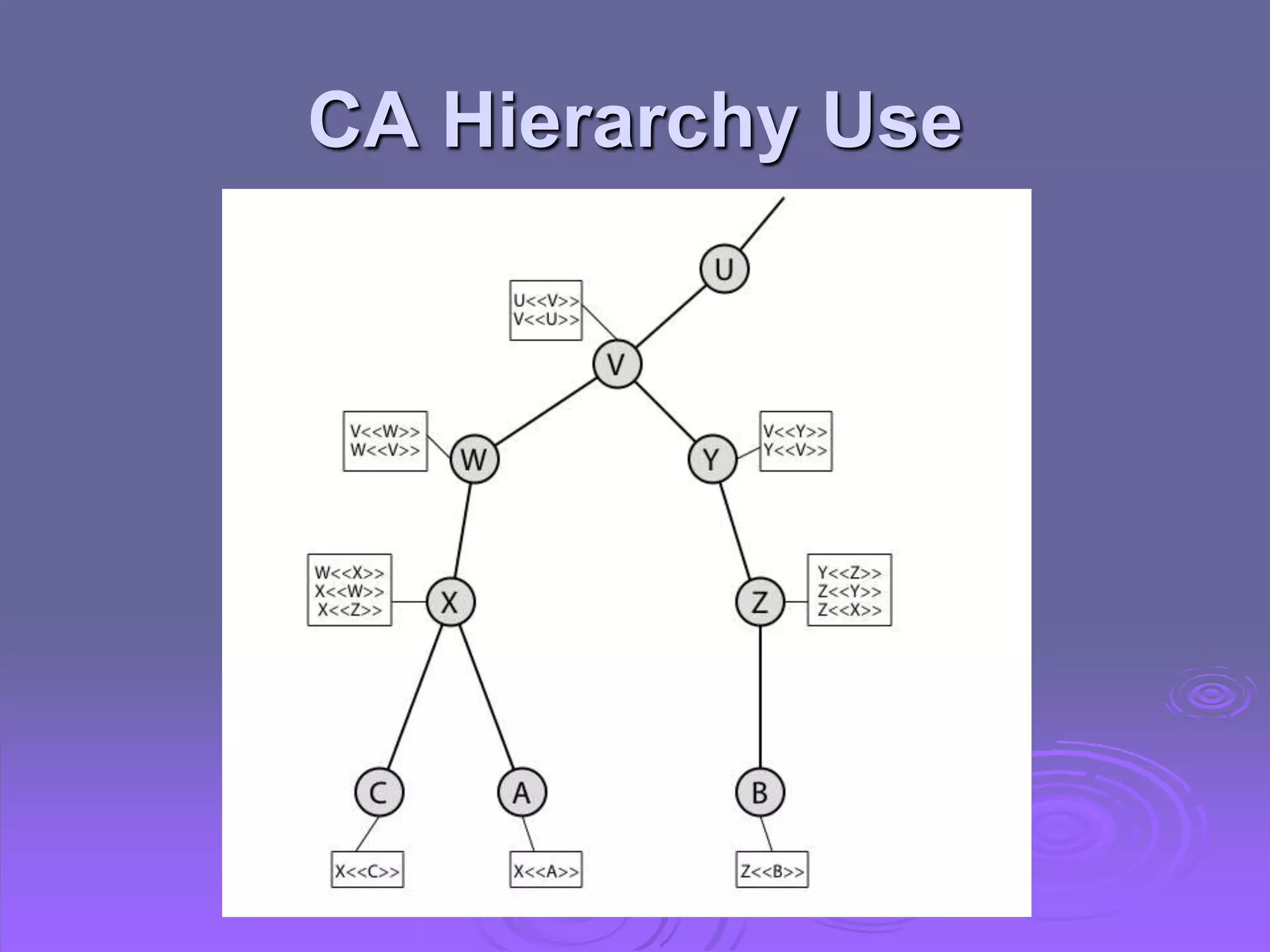
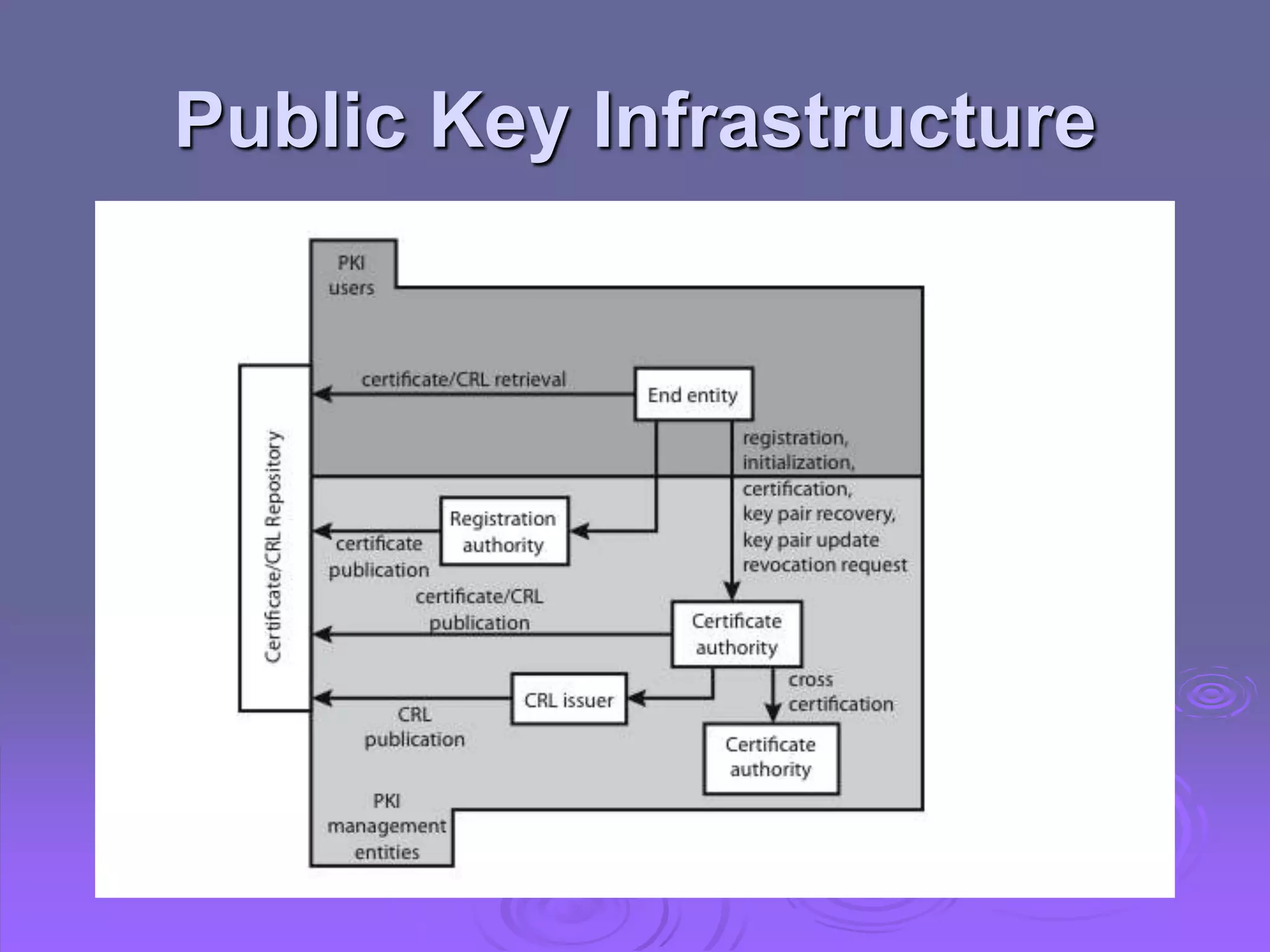
Kerberos is a trusted third-party authentication system that uses tickets and session keys to allow clients access to distributed services on a network. X.509 defines a framework for authentication using public-key cryptography and digital certificates signed by a certification authority. Key features include one-way, two-way, and three-way authentication protocols, certificate extensions, certificate revocation lists, and certificate authority hierarchies.