The document discusses key concepts in cryptographic key management and user authentication:
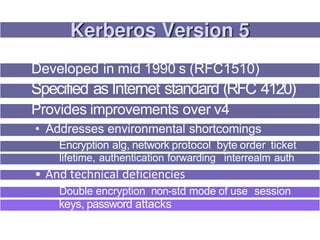
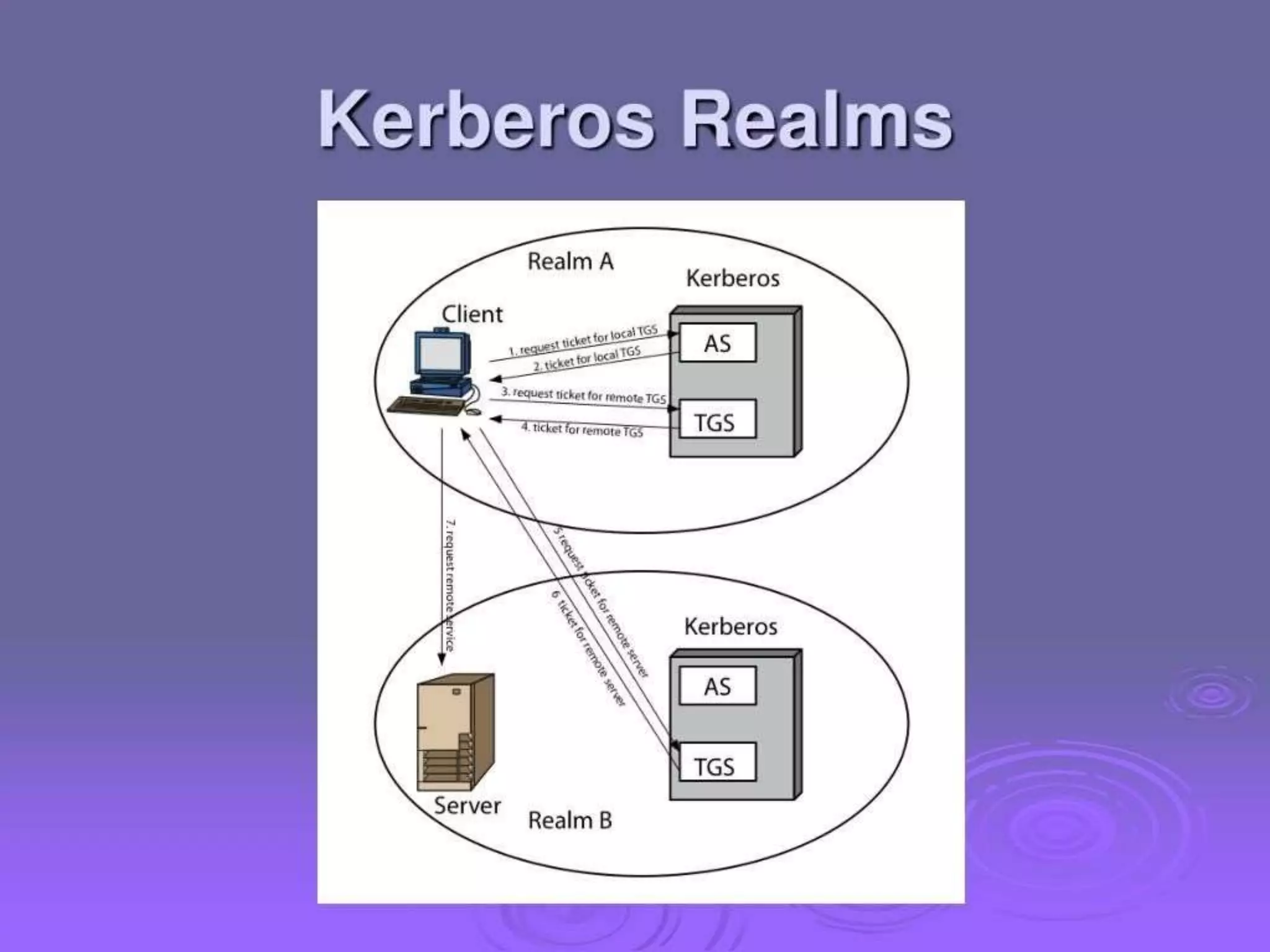
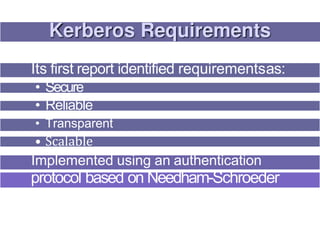
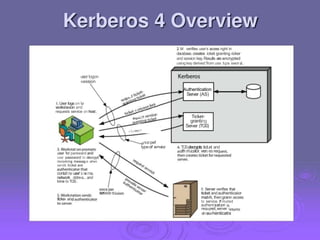
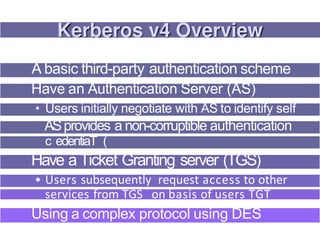
1. Kerberos is a trusted third party authentication protocol that allows clients to obtain service tickets from an authentication server (AS) and ticket granting server (TGS) using encrypted tickets and without transmitting passwords in plaintext.
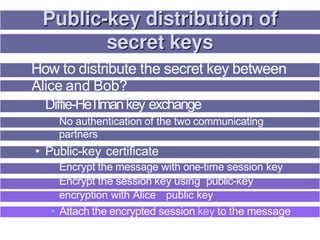
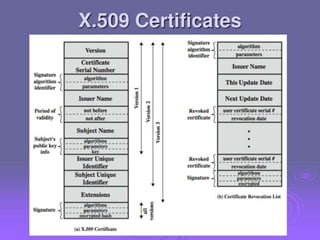
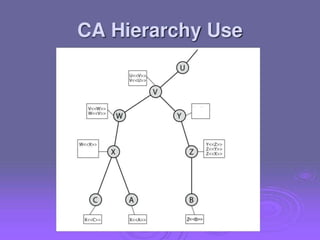
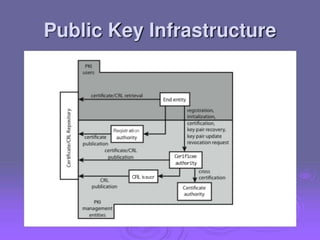
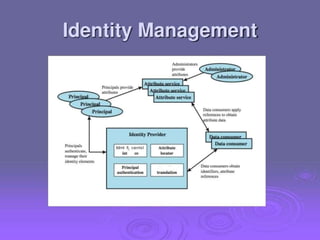
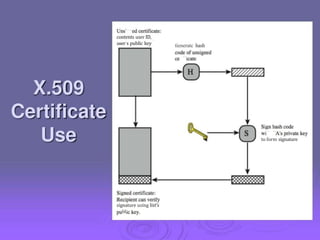
2. Public key certificates bind public keys to user identities through digital signatures by a certification authority (CA). Certificates are distributed through public directory services and can be validated through a hierarchy of CAs.
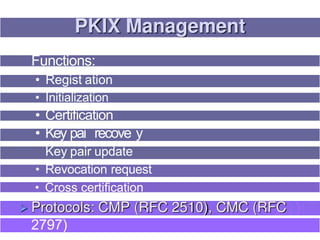
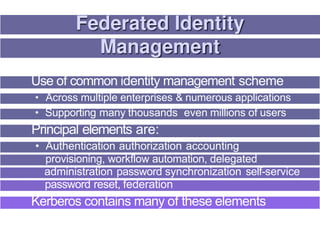
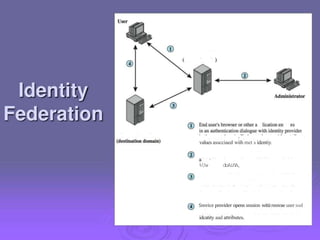
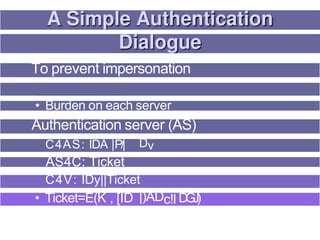
3. Key distribution and user authentication protocols aim to securely distribute secret keys between parties or allow users to authenticate to services while preventing impersonation attacks. Standards like Kerberos, public key infrastructure and Security Assertion Markup Language


![Client Server Authentication Exchange to
obtain service
C4V: Ticket
V4C: E( [TS +1]) (for mutua!
authentication)
• Ticket —
E( [K
Dcl)ADcÍl D ||TS4||Lifetime4])
• Authenticatorc —
E( cvI D |)ADcÌ)TSs])](https://image.slidesharecdn.com/1165839977-230818130938-348714b2/85/1165839977-pptx-6-320.jpg)







![Authentication service exchange to obtain
ticket-granting ticket
C4AS IDC| D
g TS1
AS4C: E(
[ | D
g TS2|| Lifetime2||Ticketg ])
• Ticket g
s
—E( [
IDC||ADC| D gs TS2||Lifetime2])
[Session key: ]](https://image.slidesharecdn.com/1165839977-230818130938-348714b2/85/1165839977-pptx-21-320.jpg)
![Ticket-granting service exchange to obtain
ticket-granting ticket
C->TGS: IDV| Ticketg
TGS4 C: E( [ ||ID ||TS4||Tickety])
• Ticketg E(
IDA )ADcÌÌ D
g
[
| TS2| Lifetime2])
• Ticket —
E( [
D ))ADcÍl Dvl)TS4||Lifetime4])
[ Dcs)ADcÌ)TS3])
• Authenticatorc —
E(ïï ¿
[Session key: ]](https://image.slidesharecdn.com/1165839977-230818130938-348714b2/85/1165839977-pptx-22-320.jpg)

![# C4ASÎ Dc IDg T
S
C
. AS4 C: E(KC
[ c D g TS2| Lifetime2| Ticket ])
C TGS D m||TiCketgs||Authenticatory
. TGS4C: E(Kgg
8 C >
T Srem•CDVem))Ticketțgsemİ)Authenticatorc
TGSrem’ E(KCtgnem,
[Kcvrem) Dvrem))TS6||Ticketyrem])
8 C
C
V emuTickety em))Authenticator](https://image.slidesharecdn.com/1165839977-230818130938-348714b2/85/1165839977-pptx-24-320.jpg)