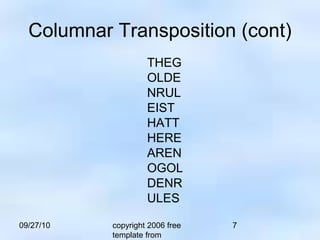
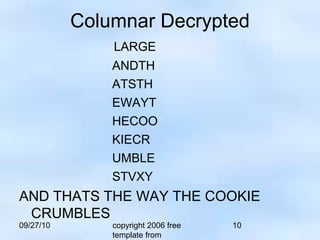
The document discusses transposition ciphers, which encrypt plaintext by rearranging its characters according to a defined system, creating a permutation of the original text. It includes examples like the rail fence and columnar transposition ciphers, demonstrating how messages are encoded and decoded. Through mathematical functions, positions of characters are altered for encryption and then reversed for decryption.