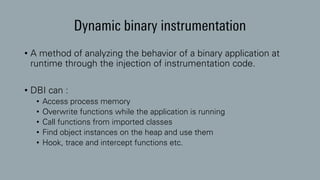
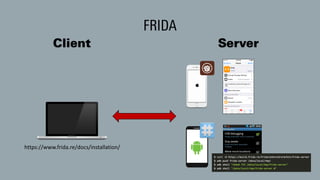
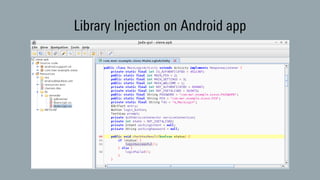
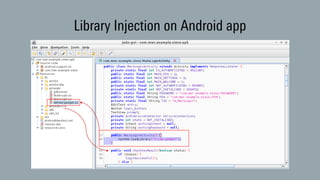
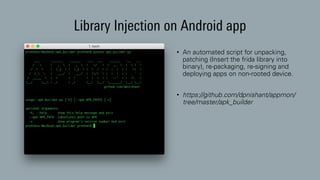
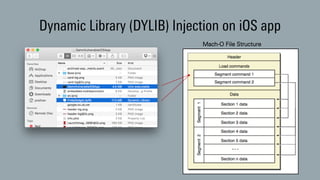
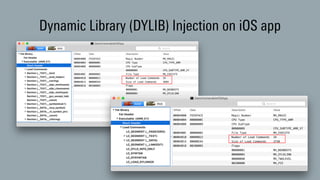
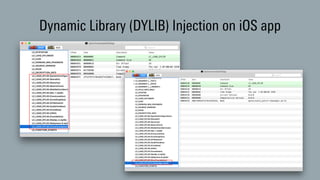
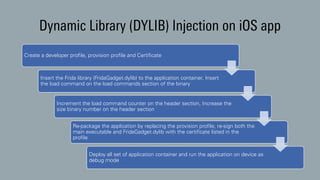
The document discusses dynamic binary instrumentation (DBI) and the use of the Frida toolkit for runtime exploitation without the need for rooting or jailbreaking devices. It highlights methods to bypass security measures such as root detection and SSL pinning, along with case studies and countermeasures for mobile banking applications. Additionally, it provides references and automation scripts for injecting libraries into apps for security analysis.