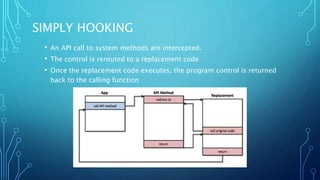
The document discusses runtime analysis of iOS applications, focusing on techniques like hooking to manipulate APIs, bypass security features, and analyze vulnerabilities. It outlines tools and methods used for testing, including Cydia Substrate, Cycript, and Snoop-It, and provides examples of common security issues such as insecure data storage and broken cryptography. Additionally, it compares tools for iOS and Android runtime analysis and emphasizes the importance of understanding application internals for effective black box testing.







![[DEMO] MY CURRENT SETUP
• Hardware
• Jailbroken iPhone 6 (v9.0)
• A RAVPower power bank with a Wifi interface.
• Impactor – an app install modded iOS apps.
• Software
• On computer
• Xcode with iOS Simulator
• IDA Free (or Hopper)
• Burpsuite Pro
• On iOS device
• DamnVulnerableIOSApplication (ref: http://damnvulnerableiosapp.com/#learn)
• Snoop-IT
• cydia](https://image.slidesharecdn.com/runtimeanalysisforiosappsowasp-220222052435/85/Runtime-Analysis-on-Mobile-Applications-February-2017-9-320.jpg)
![[DEMO] INSECURE DATA STORAGE
• Sensitive information is stored locally on the device without proper file
protections.
• PLIST files – unencrypted binary/xml file stored in app sandbox. Generally
used for storing application configuration information.
• Keychains – An encrypted vault which uses iOS’s Secure Enclave
implementation extensively.
• Use kSecAttrAccessibleWhenUnlockedThisDeviceOnly – for sensitive data storage
• CoreData – An SQLite type flat file used for storing iOS application data.
• Tool Used:
• DamnVulnerableIOSApplication
• Snoop-IT – for monitoring iOS application changes at runtime](https://image.slidesharecdn.com/runtimeanalysisforiosappsowasp-220222052435/85/Runtime-Analysis-on-Mobile-Applications-February-2017-10-320.jpg)
![[DEMO] BROKEN CRYPTOGRAPHY
• Insecure encryption/decryption implementation
• Hardcoded Keys
• Depreciated cryptographic algorithms
• Insufficient Key Size
• Tool Used:
• DamnVulnerableIOSApplication
• Snoop-IT – for monitoring iOS application changes at runtime
• IDA Pro – for decompiling the application](https://image.slidesharecdn.com/runtimeanalysisforiosappsowasp-220222052435/85/Runtime-Analysis-on-Mobile-Applications-February-2017-11-320.jpg)
![[DEMO] SENSITIVE INFORMATION IN
MEMORY
• Insecure handling of sensitive information
• Using NSString* to store passwords, credit card numbers etc.,
• NSString is an immutable data type. NSMutableString is a better alternative.
• Not clearing variables used for storing sensitive information, after its use.
• Tool Used:
• DamnVulnerableIOSApplication
• Snoop-IT – for calling Objective-C classes at runtime.
• Cycript - for scripting capabilities](https://image.slidesharecdn.com/runtimeanalysisforiosappsowasp-220222052435/85/Runtime-Analysis-on-Mobile-Applications-February-2017-12-320.jpg)
![[DEMO] BYPASSING CLIENT-SIDE CHECKS
• Runtime manipulation of code to bypass built-in safeguards
• Flawed design/implementation of application logic.
• Only Client-Side check for mission/business critical functionalities
• Tool Used:
• DamnVulnerableIOSApplication
• Snoop-IT – for calling Objective-C classes at runtime.
• Cycript – for scripting capabilities
• Xcode and iOS Simulator – another way of performing runtime analysis](https://image.slidesharecdn.com/runtimeanalysisforiosappsowasp-220222052435/85/Runtime-Analysis-on-Mobile-Applications-February-2017-13-320.jpg)
![[DEMO] JAILBREAK DETECTION BYPASS
• Runtime manipulation of code to bypass jailbreak detection
• Flawed design/implementation of application logic.
• Custom built jailbreak detections are easy to bypass
• Applicability: MDM solutions.
• Tool Used:
• DamnVulnerableIOSApplication
• Snoop-IT – for calling Objective-C classes at runtime.
• Cycript – for scripting capabilities](https://image.slidesharecdn.com/runtimeanalysisforiosappsowasp-220222052435/85/Runtime-Analysis-on-Mobile-Applications-February-2017-14-320.jpg)
![[DEMO] SSL/TLS CERTIFICATE PINNING
• Bypassing SSL/TLS Certificate Pinning at runtime.
• iOS Applications use “NSURLConnection” to trigger an HTTP request
• “NSURLConnection” uses
“connection:willSendRequestForAuthenticationChallenge” to perform
certificate pinning validations
• SSL Kill Switch 2 - a tweak which hooks into ”NSURLConnection”, and accepts
all certificates.
• Tool Used:
• DamnVulnerableIOSApplication
• Burpsuite Pro
• SSL Kill Switch 2
• https://github.com/nabla-c0d3/ssl-kill-switch2](https://image.slidesharecdn.com/runtimeanalysisforiosappsowasp-220222052435/85/Runtime-Analysis-on-Mobile-Applications-February-2017-15-320.jpg)

